MySQL Security & GDPR
- 6. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | GDPR – Who’s affected • GDPR applies to ‘controllers’ and ‘processors’ of personal EU data • From 25th May 2018 – – €20million or 4% of annual turnover – Stop orders – Temporary & Permanent – DPO must be in place if required NIS Directive (also known as the New EU Cybersecurity Directive) • Operational Essential services and Digital Service providers • Member states to decide level of fines – expected to be similar to GDPR Risks organisations face 6 OES’s • Energy • Transport • Water • Banking and financial market infrastructures • Healthcare • Digital infrastructure DSP’s • Search Engines • Cloud Computing Services • Online market Places
- 7. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Complexity grows Risk Grows 7
- 8. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Security (GDPR) and MySQL • We can’t be entirely prescriptive • We have many things that can be applied towards attaining compliance – Products – Features – Best Practices – Documents – Integrations 8
- 9. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | 9 Enterprise Security Architecture ¡ Workbench •Model •Data •Audit Data •User Management ¡ ¡ Enterprise Monitor •Identifies Vulnerabilities •Security hardening policies •Monitoring & Alerting •User Monitoring •Password Monitoring •Schema Change Monitoring •Backup Monitoring ¡Data Encryption •TDE •Encryption •PKI ¡ Firewall ¡ Key Vault ¡ Enterprise Authentication •SSO - LDAP, AD, PAM ¡ Network Encryption ¡ Enterprise Audit •Powerful Rules Engine ¡ Audit Vault ¡ Strong Authentication ¡ Access Controls ¡ Assess ¡ Prevent ¡ Detect ¡ Recover ¡ Enterprise Backup •Encrypted ¡ HA •Innodb Cluster ¡Thread Pool •Attack minimization
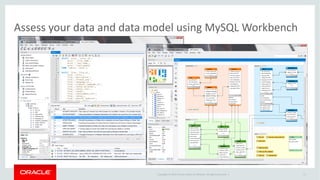
- 11. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Assess - MySQL Enterprise Features and GDPR • Assess Risks (Articles 35, 90, 91) – MySQL Enterprise Monitor • Account assessment and reporting • Identifies Security Vulnerabilities – discover security holes, advises remediating actions – Advisors provide rules designed to enforce security best practices and alert upon discovering vulnerabilities – MySQL Workbench EE • Discover tables and columns containing “Personal Data” • Data Modeling tool - Reverse Engineering of Data Model to review data stored in the database • Schema Inspector, Table Inspectors – for schema assessment, grant inspection – MySQL Security Best Practices Guidelines 11
- 12. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Enterprise Monitor • Enforce MySQL Security Best Practices – Identifies Vulnerabilities – Assesses current setup against security hardening policies • Monitoring & Alerting – User Monitoring – Password Monitoring – Schema Change Monitoring – Backup Monitoring – Configuration Management – Configuration Tuning Advice • Centralized User Management 12 "I definitely recommend the MySQL Enterprise Monitor to DBAs who don't have a ton of MySQL experience. It makes monitoring MySQL security, performance and availability very easy to understand and to act on.” Sandi Barr Sr. Software Engineer Schneider Electric
- 13. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Assess MySQL Authorization • Administrative Privileges • Database Privileges • Session Limits and Object Privileges • User privileges – Creating, altering and deleting databases – Creating, altering and deleting tables – Execute INSERT, SELECT, UPDATE, DELETE queries – Create, execute, or delete stored procedures and with what rights – Create or delete indexes 13 Security Privilege Management in MySQL Workbench
- 14. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Enterprise Authentication 14 • Integrate with Centralized Authentication Infrastructure – Centralized Account Management – Password Policy Management – Groups & Roles • PAM (Pluggable Authentication Modules) – Standard interface (Unix, LDAP, Kerberos, others) – Windows • Access native Windows service - Use to Authenticate users using Windows Active Directory or to a native host Integrates MySQL with existing security infrastructures
- 15. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Enterprise Authentication: PAM • Standard Interface – LDAP – Unix/Linux • Proxy Users 15
- 18. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Prevent - MySQL Enterprise Features and GDPR • Prevent Attacks (Articles 32, 83, 28, 26, 5, 20, 27, 30, 64) – MySQL Enterprise Security – Transparent Data Encryption • Includes Key Management • Protects Tablespace via Encryption, Keys via Key Manager/Vault integration – MySQL Enterprise Security – Firewall • MySQL Firewall Statement/User/IP Whitelists, Rules – MySQL Enterprise Authentication – DBA configurable IP whitelisting, Connection Limits, … • Via server level and via per Account IP/Hostname Controls, Account resource limits, – In transit data encryption - • Full support for TLS 1.2 - X509, Certificate Authorities, Exclude Lists, etc. – Granular access controls • Table Grants, Database Views, Stored Procedures, Functions 18
- 19. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Enterprise Firewall: Overview 19 Inbound SQL Traffic Web Applications SQL Injection Attack Via Brower ALLOW BLOCK DETECT 1 2 3 Instance MySQL Enterprise FirewallInternet
- 20. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Enterprise Firewall • Block SQL Injection Attacks – Allow: SQL Statements that match Whitelist – Block: SQL statements that are not on Whitelist • Intrusion Detection System – Detect: SQL statements that are not on Whitelist • SQL Statements execute and alert administrators 20 Select * from employee where id=22 Select * from employee where id=22 or 1=1 Block✖ Allow✔ White List Applications Detect & Alert Intrusion Detection
- 21. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Enterprise Firewall • Real Time Protection – Queries analyzed and matched against White List • Blocks SQL Injection Attacks – Positive Security Model • Block Suspicious Traffic – Out of Policy Transactions detected & blocked • Learns White List – Automated creation of approved list of SQL command patterns on a per user basis • Transparent – No changes to application required 21 MySQL Enterprise Firewall monitoring
- 22. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Key Vault High-Level Architecture Standby Administration Console, Alerts, Reports Secure Backups = Credential Files/Other Wallets = Password/phrases Keystores = Certificates Databases Servers Middleware 22
- 23. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Database Encrypted Tablespace Files Protected Key Hacker / Dishonest OS User Accesses Files Directly Information Access Blocked By Encryption MySQL TDE – Protects against Attacks on Database Files
- 24. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Key Vault MySQL Enterprise Transparent Data Encryption 2 Tier Architecture MySQL Database Tablespace Keys MySQL Server Plugin & Services Infrastructure InnoDB Client Keyring plugins • Master Key • Stored outside the database • Oracle Key Vault • SafeNet KeySecure • KMIP 1.1 Compliant Key Vault • Tablespace Key • Protected by master key Master Key Plain Text Encrypted 2 Encrypted 1
- 25. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Detect - MySQL Enterprise Features and GDPR – 1 of 2 • Detect (Articles 30, 82, 33) – MySQL Enterprise Security – Audit • Policy-based auditing solution – gather audit log of activity • Use to spot database misuse • Use to prove compliance to GDPR – MySQL Enterprise Security – Firewall • Real-time protection against database specific attacks • Use to alert and/or block nefarious activity – such as personal data leakage 25
- 26. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Focus on MySQL EE Audit • GDPR – Mandates recording or auditing of the activities on the Personal Data – Recommends records must be maintained centrally • Under the responsibility of the Controller. – Processors and third-parties must not be able to tamper or destroy the audit records. – In addition to book-keeping, auditing helps in forensic analysis in case of a breach. • MySQL Enterprise Audit Audit data can be – Maintained in Oracle Audit Value – certified – Outputs standard XML or JSON that easily integrate with various 3rd party solutions – Supports encryption (MySQL 5.7.18+) – Can direct security logs to write-once storage 26
- 28. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Detect - MySQL Enterprise Features and GDPR – 2 of 2 – MySQL Workbench EE • Security related – – Inspect Audit Data – Configure Firewall – Manage Users – MySQL Enterprise Monitor • Monitor/Alert on Firewall, Audit, Backups and more • Detect configuration changes 28
- 29. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Additional Security Controls Hashing, Signing, Encryption Functions – Symmetric Encryption – AES – Hashing – SHA-2, SHA-1 – Asymmetric Public Key Encryption (RSA) – Asymmetric Private Key Decryption (RSA) – Generate Public/Private Key (RSA, DSA, DH) – Derive Symmetric Keys from Public and Private Key pairs (DH) – Digitally Sign Data (RSA, DSA) – Verify Data Signature (RSA, DSA) – Validation Data Authenticity (RSA, DSA) Confidential – Oracle Internal 29
- 30. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | Additional Security Controls • HA – Traditional Replication – MySQL InnoDB Cluster • Disaster Recovery – Traditional Replication – MySQL InnoDB Cluster • Backup – MySQL Enterprise Backup • Includes encryption • Support for MySQL TDE Confidential – Oracle Internal 30
- 31. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | MySQL Cloud Service • Designed for security • MySQL Enterprise Features • Backup & Recovery – Based on MySQL Enterprise Backup • Support (with consultative support) Confidential – Oracle Internal 31Confidential – Oracle Internal 31 + MySQL Enterprise Edition
- 32. Copyright © 2014 Oracle and/or its affiliates. All rights reserved. | References Confidential – Oracle Internal 32 • Home page EU GDPR – http://www.eugdpr.org/ • MySQL Enterprise – https://www.mysql.com/products/enterprise/ • MySQL PCI DSS – https://www.mysql.com/it/why-mysql/white-papers/mysql-pci-data-security- compliance/ • MySQL Security Best Practices – https://www.mysql.com/it/why-mysql/presentations/mysql-security-best-practices/