netfilter and iptables
- 6. …
- 8. ● ● ○ ○
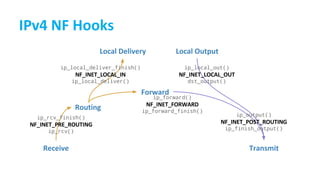
- 11. /* * Main IP Receive routine. */ int ip_rcv(struct sk_buff *skb, struct net_device *dev, struct packet_type *pt, struct net_device *orig) { ... return NF_HOOK(NFPROTO_IPV4, NF_INET_PRE_ROUTING, net, NULL, skb, dev, NULL, ip_rcv_finish); }
- 12. /* Activate hook; either okfn or kfree_skb called, unless a hook returns NF_STOLEN (in which case, it's up to the hook to deal with the consequences). Returns -ERRNO if packet dropped. Zero means queued, stolen or accepted. */ static inline int NF_HOOK_THRESH(uint8_t pf, unsigned int hook, struct net *net, struct sock *sk, struct sk_buff *skb, struct net_device *in, struct net_device *out, int (*okfn)(struct net *, struct sock *, struct sk_buff *), int thresh) { int ret = nf_hook_thresh(pf, hook, net, sk, skb, in, out, okfn, thresh); if (ret == 1) ret = okfn(net, sk, skb); return ret; }
- 13. int nf_register_net_hook(struct net *net, const struct nf_hook_ops *ops); int nf_register_net_hooks(struct net *net, const struct nf_hook_ops *reg, unsigned int n); int nf_register_hook(struct nf_hook_ops *reg); int nf_register_hooks(struct nf_hook_ops *reg, unsigned int n);
- 14. static struct nf_hook_ops ipv4_synproxy_ops[] = { { .hook = ipv4_synproxy_hook, .pf = NFPROTO_IPV4, .hooknum = NF_INET_LOCAL_IN, .priority = NF_IP_PRI_CONNTRACK_CONFIRM - 1, .priv = NULL, }, { .hook = ipv4_synproxy_hook, .pf = NFPROTO_IPV4, .hooknum = NF_INET_POST_ROUTING, .priority = NF_IP_PRI_CONNTRACK_CONFIRM - 1, .priv = NULL, }, };
- 15. static unsigned int ipv4_synproxy_hook(void *priv, struct sk_buff *skb, const struct nf_hook_state *nhs) { if (...) return NF_ACCEPT; ... if (...) return NF_DROP; return NF_ACCEPT; }
- 16. ● ● ● ● ●
- 17. enum { NFPROTO_UNSPEC = 0, NFPROTO_INET = 1, NFPROTO_IPV4 = 2, NFPROTO_ARP = 3, NFPROTO_NETDEV = 5, NFPROTO_BRIDGE = 7, NFPROTO_IPV6 = 10, NFPROTO_DECNET = 12, NFPROTO_NUMPROTO, };
- 19. ● ● ● ● ○ ●
- 21. ● ●
- 24. # iptables -t filter -P INPUT DROP # iptables -P OUTPUT ACCEPT # iptables -A INPUT -i lo -j ACCEPT # iptables -A INPUT -p tcp --dport 443 -j ACCEPT # iptables -A INPUT -s 40.5.6.7 -p tcp --dport 22 -j ACCEPT # iptables -A INPUT -m mark --mark 0xE -j ACCEPT
- 25. # iptables -t mangle -A PREROUTING -p tcp --dport 22 -j MARK --set-mark 2 # iptables -t mangle -A POSTROUTING -p tcp --tcp-flags SYN,RST SYN -o eth0 -j TCPMSS --set-mss 1420 # iptables -t mangle -A OUTPUT -p TCP --dport 22 -j TOS --set-tos 0x10
- 26. # iptables -t nat -A POSTROUTING -o eth0 -s 192.168.1.0/24 -j SNAT --to-source 2.55.4.8-2.55.4.9 192.168.1.10 192.168.1.11 192.168.1.12 192.168.1.13 2.55.4.8 2.55.4.9
- 27. # iptables -t nat -A POSTROUTING -o eth0 -s 192.168.1.0/24 -j MASQUERADE 192.168.1.10 192.168.1.11 192.168.1.12 192.168.1.13 2.55.4.9
- 28. # iptables -t nat -A PREROUTING -d 2.55.4.8 -p tcp --dport 80 -j DNAT --to-destination 192.168.1.10 192.168.1.10 192.168.1.11 192.168.1.12 192.168.1.13 2.55.4.8 :80 2.55.4.9
- 30. ● ● ○ ○ ●
- 31. # iptables -t filter -P INPUT DROP # iptables -P OUTPUT ACCEPT # iptables -A INPUT -i lo -j ACCEPT # iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT # iptables -A INPUT -p tcp --dport 443 -m conntrack --ctstate NEW -j ACCEPT
- 33. ● # iptables -A PREROUTING -m addrtype --dst-type MULTICAST -j DROP # iptables -A PREROUTING -m addrtype ! --dst-type LOCAL -j MARK --set-mark 2 ● # iptables -A FORWARD -m devgroup --src-group 27 -j ACCEPT ● # iptables -A FORWARD -m mark --mark 0x3/0x7 -j ACCEPT
- 34. ● // match IP packets with total length >= 256 -m u32 --u32 "0 & 0xFFFF = 0x100:0xFFFF" // TCP payload bytes 8-12 is any of 1, 2, 5 or 8 "6 & 0xFF = 6 && 0 >> 22 & 0x3C @ 12 >> 26 & 0x3C @ 8 = 1,2,5,8" ● -m bpf --bytecode '4,48 0 0 9,21 0 1 6,6 0 0 1,6 0 0 0'
- 35. ● ● ● ● ● …
- 36. ● ● ● ●
- 37. ● ● ● ● …
- 38. # iptables -t filter -N NO-PRIVATE # iptables -A NO-PRIVATE -s 10.0.0.0/8 -j DROP # iptables -A NO-PRIVATE -s 172.16.0.0/12 -j DROP # iptables -A NO-PRIVATE -s 192.168.0.0/16 -j DROP # iptables -A INPUT -i eth0 -j NO-PRIVATE # iptables -A FORWARD -i eth0 -j NO-PRIVATE
- 39. // Calls the specified chain, continue processing in current chain if no match # iptables -A INPUT ... -j MY-CHAIN // Continue processing in the specified chain. return will not continue in current chain, but in the previous calling chain # iptables -A INPUT ... -g MY-CHAIN // Stop traversing, resume at the next rule in the previous calling chain # iptables -A MY-CHAIN ... -j RETURN
- 40. ● ● ●
- 44. ● ● ● ● ●













![static struct nf_hook_ops ipv4_synproxy_ops[] = {
{
.hook = ipv4_synproxy_hook,
.pf = NFPROTO_IPV4,
.hooknum = NF_INET_LOCAL_IN,
.priority = NF_IP_PRI_CONNTRACK_CONFIRM - 1,
.priv = NULL,
},
{
.hook = ipv4_synproxy_hook,
.pf = NFPROTO_IPV4,
.hooknum = NF_INET_POST_ROUTING,
.priority = NF_IP_PRI_CONNTRACK_CONFIRM - 1,
.priv = NULL,
},
};](https://image.slidesharecdn.com/ladkani-netfilter-iptables-2017-170809143646/85/netfilter-and-iptables-14-320.jpg)