Nmap scripting engine
- 2. 3 Sections Todays Agenda – NSE 1. Nmap Overview - 10 Mins Nmap ? Basic Scan Options 2. NSE Overview – 20 Mins Existing Categories How to use these available scripts ? Use of 2 sample scripts 3. How to write your own NSE script ?- 20 Mins Baiscs on writing NSE Script Write a script to find website title “Null” PwC 2
- 4. Nmap (Network Mapper) – Overview Was written 15 years back as a port scanner by Gordon Lyon (Fyodor) Port Scanner : Used to discover hosts and services on a computer network by sending specially crafted packets to the target host and then analyzes the responses. Current Stable release : version 6.40 (Free) Have CLI and GUI interfaces. GUI called Zenmap/NmapFE/Xnmap(Mac) Linux, Mac OS X, Windows, Solaris, Free/Net/OpenBSD are supported. Why Nmap? – Fast, free, easy to use, flexible in scan options, portable with multiple OS, large community support and neat documentation. PwC 4
- 5. How to use Nmap ? (As port scanner) How to start with nmap ? Single Host # nmap 220.220.220.2xx # nmap Target.Nmaptest.com What i plan to scan ? IP Address : 220.220.220.2xx Subnet : /24 Host Name : Target.Nmaptest.com Subnet # nmap 220.220.220.2xx Mulitple Targets # nmap 220.220.220.2x1 220.220.220.2x5 IP Address Range # nmap 220.220.220.2x1-100 Random Ip Address (Make a list in text file - list.txt) # nmap -sL list.txt Sepcific ports # nmap -p21,23,80,443 220.220.220.2xx PwC 5
- 6. Nmap Basic Scan Output PwC 6
- 7. Nmap Switches Scan Options : -sS/sT/sA: TCP SYN/Connect()/ACK/ -sU: UDP Scan -sN/sF/sX: TCP Null, FIN, and Xmas Specify Ports : -p <port ranges>: scan specified ports Eg: -p22; -p1-65535; -p U:53,111,137, -F: Fast mode - Scan fewer ports -r: Scan ports consecutively --top-ports <number>:Scancommon ports OS Detection : -O: Enable OS detection Host Discovery : -sL: List Scan - simply list targets to scan -sn: Ping Scan - disable port scan -Pn: Treat hosts as online, skip H discovery Time Change : -T<0-5>: Set timing template (higher is faster) IP version 6 scan : -6 : Enable IPv6 scanning Output: -oN : Output scan in normal, -oX : Output scan XML How to use them together , just chain them : # nmap [ <Scan Type> ...] [ <Options> ] { <target specification> } e.g. # nmap –sS –sU -T4 -A -v -Pn 220.220.220.211 #namp –T4 –randomize-host –iL list.txt –oX scanresults.xml Cheet Sheet : http://pentestlab.wordpress.com/2012/08/17/nmap-cheat-sheet/ PwC 7
- 9. Nmap Scripting Engine (NSE) – Introduction Nmap Scripting Engine (NSE) allows users to write simple scripts to automate networking and pentesting tasks. NSE include network discovery, sophisticated version detection, vulnerability detection and even for vulnerability exploitation. Uses Lua programming. Lua also used in Wireshark, snort and some Web App. F/W. Current download of nmap comes with 437 scripts. Scrips are categratized into various caterogies based on the usage. Every script needs to be identified by a category. E.g. categories = {"intrusive", "auth"} Nmap.org also provides libary details for writting your own scripts. NSE Docuemntation : http://nmap.org/nsedoc/ PwC 9
- 10. NSE Script Categories auth These scripts deal with authentication credentials (or bypassing them) on the target system. E.g. ftp-anon, oracle-enum-users broadcast Scripts in this category typically do discovery of hosts not listed on the command line by broadcasting on the local network. E.g. newtargets brute Use brute force attacks to guess authentication credentials of a remote server. E.g. http-brute, oracle-brute, snmp-brute default - A option with namp E.g. http-auth, ftp-anon discovery try to actively discover more about the network by querying public registries, SNMP-enabled devices, directory services, and similar. E.g. html-title, smb-enum-shares dos Denial of service scripts. E.g. broadcast-avahi-dos Exploit Scripts aim to actively exploit some vulnerability. E.g. http-fileuploadexploiter external Connects to 3rd party database to get info. E.g. Whois fuzzer Designed to fuzz. E.g. dns-fuzz PwC 10
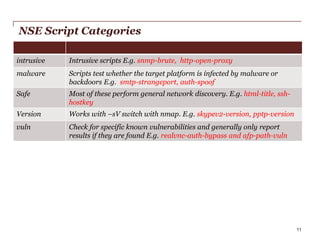
- 11. NSE Script Categories intrusive Intrusive scripts E.g. snmp-brute, http-open-proxy malware Scripts test whether the target platform is infected by malware or backdoors E.g. smtp-strangeport, auth-spoof Safe Most of these perform general network discovery. E.g. html-title, sshhostkey Version Works with –sV switch with nmap. E.g. skypev2-version, pptp-version vuln Check for specific known vulnerabilities and generally only report results if they are found E.g. realvnc-auth-bypass and afp-path-vuln PwC 11
- 12. How to use existing NSE scripts? Existing 437 scripts with v6.40 Every Script will have category defined by the author, this will also be used to use the script with nmap scanning. E.g. domino-enum-users Usage : # nmap –sC (equivalent to --script=default; sC == script) e.g #nmap x.x.x.x –sC # nmap --script <filename>|<category>|<directory>|<expression> e.g # nmap --script all x.x.x.x (Runs all avalable Scripts on ip x.x.x.x) # namp –script safe,external, http-auth x.x.x.x # nmap --script <scriptname> --script-args <args> e.g. nmap --script snmp-sysdescr --script-args snmpcommunity=admin example.com #nmap --script-help <scriptname > ( provides help on the script) e.g. #nmap --script-help http-auth 12 PwC
- 13. Sample Nmap NSE Scan Output PwC January 2010 13
- 14. How to write your own NSE script ? 20 Mins PwC 14
- 15. Writing your own NSE script !! Writing NSE script is simple !!! You write them in Lua Pretty set structure for the script. PwC 15
- 16. HR Portal Script (Oracle_Fussion.nse) 1. description Field : The description field describes what a script is testing for and any important notes the user should be aware of. description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] PwC 16
- 17. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] 2. author Field : The author field contains the script authors' names and can also contain contact information author = “Sudhir Babu B <[email protected] >" PwC 17
- 18. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ 3. categories Field : The categories field defines one or more categories to which a script belongs. categories = {"default", "discovery", "safe"} PwC 18
- 19. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ categories = {"default", "discovery", "safe"} 4. license Field (Optional) – Provide appropriate licence. license = "Same as Nmap--See http://nmap.org/book/man-legal.html”" PwC 19
- 20. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“ categories = {"default", "discovery", "safe“} ----------------------------------------------------------------5. As it’s http app. we need the follwoing libary : require “shortport” --- ??? require “hhtp” Why we need short port ? “portrule” defines when nmap when to trigger the script. “shortport” module simplify the this process as common use for portrule 6. Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”}) PwC 20
- 21. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“ categories = {"default", "discovery", "safe“} require “shortport” require “hhtp” Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”}) 7. Action funtion, what to do when portrule triggers. action = function(host, port) -- Define action end PwC 21
- 22. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“ categories = {"default", "discovery", "safe“} require “shortport” require “hhtp” Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”}) action = function(host, port) -- just checking if the directory exist with 200 OK response local stats = http.get (host, port, ‘/Oracle_Fusion/’).status end PwC 22
- 23. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“ categories = {"default", "discovery", "safe“} require “shortport” require “hhtp” Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”}) action = function(host, port) -- just checking if the directory exist with 200 OK response local stats = http.get (host, port, ‘/Oracle_Fusion/’).status Need to add response : what if ? if stats == 200 then return “Internal HR Portal Found” end end PwC 23
- 24. HR Portal Script (Oracle_Fussion.nse) description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App. ]] author = “Sudhir Babu B <[email protected] >“ license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“ categories = {"default", "discovery", "safe“} require “shortport” require “hhtp” Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”}) action = function(host, port) local stats = http.get (host, port, ‘/Oracle_Fusion/’).status if stats == 200 then return “Internal HR Portal Found” end end PwC 24
- 25. Thanks for your time & patience [email protected] PwC 25
- 26. NSE – Example Y ?? Slide 10 PwC 26







![Nmap Switches
Scan Options :
-sS/sT/sA: TCP SYN/Connect()/ACK/
-sU: UDP Scan
-sN/sF/sX: TCP Null, FIN, and Xmas
Specify Ports :
-p <port ranges>: scan specified ports
Eg: -p22; -p1-65535; -p U:53,111,137,
-F: Fast mode - Scan fewer ports
-r: Scan ports consecutively
--top-ports <number>:Scancommon ports
OS Detection :
-O: Enable OS detection
Host Discovery :
-sL: List Scan - simply list targets to scan
-sn: Ping Scan - disable port scan
-Pn: Treat hosts as online, skip H discovery
Time Change :
-T<0-5>: Set timing template (higher is faster)
IP version 6 scan :
-6 : Enable IPv6 scanning
Output:
-oN : Output scan in normal,
-oX : Output scan XML
How to use them together , just chain them :
# nmap [ <Scan Type> ...] [ <Options> ] { <target specification> }
e.g.
# nmap –sS –sU -T4 -A -v -Pn 220.220.220.211
#namp –T4 –randomize-host –iL list.txt –oX scanresults.xml
Cheet Sheet : http://pentestlab.wordpress.com/2012/08/17/nmap-cheat-sheet/
PwC
7](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-7-320.jpg)







![HR Portal Script (Oracle_Fussion.nse)
1.
description Field : The description field describes what a script is testing for and
any important notes the user should be aware of.
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
PwC
16](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-16-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
2. author Field : The author field contains the script authors' names and can also
contain contact information
author = “Sudhir Babu B <sudhir@securitytest.com >"
PwC
17](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-17-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
3. categories Field : The categories field defines one or more categories to which a
script belongs.
categories = {"default", "discovery", "safe"}
PwC
18](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-18-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
categories = {"default", "discovery", "safe"}
4. license Field (Optional) – Provide appropriate licence.
license = "Same as Nmap--See http://nmap.org/book/man-legal.html”"
PwC
19](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-19-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“
categories = {"default", "discovery", "safe“}
----------------------------------------------------------------5. As it’s http app. we need the follwoing libary :
require “shortport” --- ???
require “hhtp”
Why we need short port ?
“portrule” defines when nmap when to trigger the script.
“shortport” module simplify the this process as common use for portrule
6. Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”})
PwC
20](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-20-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“
categories = {"default", "discovery", "safe“}
require “shortport”
require “hhtp”
Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”})
7. Action funtion, what to do when portrule triggers.
action = function(host, port)
-- Define action
end
PwC
21](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-21-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“
categories = {"default", "discovery", "safe“}
require “shortport”
require “hhtp”
Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”})
action = function(host, port)
-- just checking if the directory exist with 200 OK response
local stats = http.get (host, port, ‘/Oracle_Fusion/’).status
end
PwC
22](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-22-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“
categories = {"default", "discovery", "safe“}
require “shortport”
require “hhtp”
Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”})
action = function(host, port)
-- just checking if the directory exist with 200 OK response
local stats = http.get (host, port, ‘/Oracle_Fusion/’).status
Need to add response : what if ?
if stats == 200 then
return “Internal HR Portal Found”
end
end
PwC
23](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-23-320.jpg)
![HR Portal Script (Oracle_Fussion.nse)
description = [[Attempts to retrieve HR Potral hosted on Oracle Fussion App.
]]
author = “Sudhir Babu B <sudhir@securitytest.com >“
license = "Same as Nmap--See http://nmap.org/book/man-legal.html”“
categories = {"default", "discovery", "safe“}
require “shortport”
require “hhtp”
Portrule = shortport.port_or_service({80, 443, 8081},{“http”,”https”})
action = function(host, port)
local stats = http.get (host, port, ‘/Oracle_Fusion/’).status
if stats == 200 then
return “Internal HR Portal Found”
end
end
PwC
24](https://image.slidesharecdn.com/nmapscriptingengine-131020235307-phpapp02/85/Nmap-scripting-engine-24-320.jpg)

