Open Source Security and ChatGPT-Published.pdf
- 1. Open Source Security and ChatGPT: Navigating Concerns while Enhancing Development with Javier Perez
- 2. Chief Evangelist & Sr. Director of Product Management javierperez.mozello.com www.linkedin.com/in/javierperez Tech Evangelist | Open Source Advocate | OSS Program Leader | Product Management Product Marketing | App Security | Speaker | Blogger | Startups | Ex-Red Hat | Ex-IBM Javier Perez Perforce Software
- 3. 2.6M + 720 packages/day 575K + 182 packages/day 384K + 86 packages/day 475K + 211 packages/day 379K + 161 packages/day 178K + 12 packages/day Source: Nov 16, 2023 www.modulecounts.com
- 4. 350+ Projects 850+ Projects 157+ Projects 418+ Projects 30+ Projects Source: 2022 Foundation annual reports
- 5. Source code is publicly available Open to collaboration Source code available with a license that permits users to freely run, study, modify and redistribute Freedom to deploy anywhere Open Source Software Source: AI-generated with DALL-E
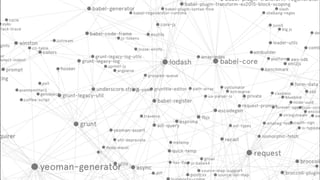
- 6. Open source libraries are reused by other open source Libraries can have up to 1000s of dependencies Same issue with proprietary software since they are all using OSS Source: AI-generated with DALL-E
- 7. Example: Apache Commons IO Library Used by: 26,486 artifacts Apache Commons Lang 27,309 AssertJ 16,216 Spring Web 8,400 Apache Log4j 10,205 Fastjson 6,347 Snake YAML Hadoop Common Zoo Keeper Selenium Java * Source: MavenRepository.com (Nov 16, 2023) * Sources: graphcommons.com
- 8. Example: Apache Commons IO Library Used by: 26,486 artifacts Apache Commons Lang 27,309 AssertJ 16,216 Spring Web 8,400 Apache Log4j 10,205 Fastjson 6,347 Snake YAML Hadoop Common Zoo Keeper Selenium Java * Source: MavenRepository.com (Nov 16, 2023) * Sources: graphcommons.com
- 9. It’s about Vulnerabilities Common Vulnerability and Exposures (CVE) Common Vulnerability Score System (CVSS) Vulnerabilities outside CVE and NVD Open Source Software Security Source: AI-generated with DALL-E
- 10. New vulnerabilities are constantly being discovered The smart way to make them public is when you have a fix (public disclosure) More than 95% of public vulnerabilities have a fix, but you must keep up with the latest releases/patches Source: AI-generated with DALL-E
- 11. OpenAI’s ChatGPT took the world by storm, over 100 million users in the first two months after its public launch
- 12. ChatGPT or other AI-based tools allow developers to produce code more quickly and more efficiently
- 13. Validity of the Code Without context the validity of the code can be questioned. Are developers going to relay entirely on ChatGPT-generated code? Developers don’t take ChatGPT’s output as the final word. AI-generated code is should be just the baseline. Just like using code from Stack Overflow, GitHub, NPM, etc. C O N C E R N 1 R E S P O N S E
- 14. Training Data ML/DL model training must be fair, robust and explainable. Where is the data coming from? Garbage in, garbage out. ChatGPT’s code outputs are not guaranteed to be perfect. But ChatGPT can explain new or existing code, it can also effectively provide unit tests for code, which will help with writing better software faster. C O N C E R N 2 R E S P O N S E
- 15. Ownership Can I use and distribute AI-generated code? What about license compliance? The code that ChatGPT outputs should not be considered in a final state or copyrightable. AI-generated code is not supposed to be identical to other code, if it is, Microsoft cover legal challenges related to copyright grounds (paid version) C O N C E R N 3 R E S P O N S E
- 16. Job Displacement AI tools and ChatGPT are going to make developer jobs redundant. Deeper testing shows inaccuracies, unreliable code, and content. ChatGPT won’t immediately create new or different jobs. Encourage developers and open source developers to embrace ChatGPT, GitHub Copilot and other tools to explore possibilities. C O N C E R N 4 R E S P O N S E
- 17. Security AI-generated code is going to introduce vulnerabilities. It’s the developer’s responsibility to use code ethically and safely. It’s also important to carefully review any code generated by ChatGPT and ensure that it doesn’t introduce vulnerabilities. Same as it’s done today from other sources. C O N C E R N 5 R E S P O N S E
- 18. ChatGPT has already proven to be an effective educational tool. Consider asking for book recommendations about programming languages and coding; it delivers short descriptions for each book. Prompt it for the top takeaways from one specific book. Translate code from one programming language to another.
- 19. Other Security Concerns • Phishing attacks: ChatGPT affords bad foreign actor to near fluency in English • Malicious code: AI is programmed not to generate code that it deems to be malicious. Code generation can still be manipulated and updated to create malicious code, same as any other source of code. Source: AI-generated with DALL-E
- 20. If ChatGPT can assist bad actors, remember that this same power is equally available to good actors. Source: AI-generated with DALL-E
- 21. Dev Security Education • Security Champions Needed • Knowledge of OWASP Top Ten Many Contributors “Given enough eyeballs, all bugs are shallow” – Linus’ Law Vulnerabilities in Open Source Source: AI-generated with DALL-E
- 22. OWASP Top 10 Vulnerabilities • Broken Access Control • Cryptographic Failures (sensitive data exposure) • Injection (SQL, NoSQL, OS, LDAP, Cross-site scripting) • Insecure Design • Security Misconfiguration • Vulnerable and Outdated Components (CVEs and EOL software) • Identification and Authentication Failures • Software and Data Integrity Failures • Security Logging & Monitoring Failures • Server-Side Request Forgery (SSRF) Top 10
- 23. • Identify open source libraries, generate software bill of materials (SBOMs) • Identify vulnerabilities and severity on libraries and dependencies • Prioritization, alerts, and security policies • Integrate with build environment (CI pipeline) Vulnerabilities Scanners Source: AI-generated with DALL-E
- 24. • OWASP Dependency-Checker • NPM audit • GitHub vulnerability alerts • GitLab dependency scanning • SAP code vulnerability analyzer Open Source or Free Scanners Source: AI-generated with DALL-E
- 25. SBOMs Generation • OWASP Dependency-Track • SBOM Tool (Microsoft) • Syft and Grype • CycloneDx-CLI • OSV-Scanner Source: AI-generated with DALL-E
- 26. Public Vulnerability Databases National Vulnerability Database nvd.nist.gov GitHub Advisory Database github.com/advisories Mend Vulnerability Database mend.io/vulnerability-database NPM Security Advisory npmjs.com/advisories Sonatype OSS Index ossindex.sonatype.org VulDB vuldb.com Metasploit rapid7.com/db Source: AI-generated with DALL-E
- 27. “Open Source Security is about visibility of vulnerabilities, apply patches, avoid EOL versions, and making scans part of SDLC.”
- 28. “Whether it’s reviewing code, pair programming or learning from fellow developers, humans will not be replaced by generative AI, only enhanced.”
- 29. “Take advantage of the new tools and treat AI-generated code as any other code: with bugs and vulnerabilities.”
- 30. Chief Evangelist & Sr. Director of Product Management javierperez.mozello.com www.linkedin.com/in/javierperez Javier Perez Perforce Software Thank You! Images generated with OpenAI’s DALL-E via Microsoft Bing Image Creator Article à