OpenID Connect - a simple[sic] single sign-on & identity layer on top of OAuth 2.0
- 1. OpenID Connect a simple[sic] single sign-on & identity layer on top of OAuth 2.0 Brian Campbell @__b_c Copyright © 2014 Brian Campbell. All rights reserved.
- 2. Copyright © 2014 Brian Campbell. All rights reserved. 2 Agenda • Introductions • Framing the Problem • OpenID Connect as an Emergent Solution • Nuts & Bolts: The Basic Client Profile • Random Thoughts
- 3. Copyright © 2014 Brian Campbell. All rights reserved. 3 Who Dat? Brian Campbell Some Meaningless Title & 10+ years @ Used to write a lot of code Now active in standards development Identity is ubiquitous. Regardless of the kind of applications you develop you will, at some point, almost certainly have to deal with identifying users of the app. Yet it's seldom a central part of the app’s value proposition and rarely a core competency for developers. Wouldn’t it be nice to outsource user authentication and free yourself from the liability and complexity of storing and managing passwords? OpenID Connect, just ratified earlier this year and backed by some big industry names, is emerging as the go to standard way to do exactly that. Connect allows you to easily and securely get an answer to the question: “What is the identity of the person currently using this browser or native app?” Unlike some of it’s predecessors, however, Connect has roots spanning the consumer, SaaS and enterprise space and is better suited to serve a diverse set of deployments. Come find out more about Connect in this talk from a seasoned veteran of the prestigious basement conference rooms at GlueCon. Cardboard box
- 4. Copyright © 2014 Brian Campbell. All rights reserved. 4 Speaker Credentials
- 5. Copyright © 2014 Brian Campbell. All rights reserved. 5 Speaker Credentials
- 6. Copyright © 2014 Brian Campbell. All rights reserved. 6 Speaker Credentials Prominently mentioned on the second to last page that nobody will ever read just before the copyright notices
- 7. Copyright © 2014 Brian Campbell. All rights reserved. 7 Agenda • Introductions • Framing the Problem • OpenID Connect as an Emergent Solution • Nuts & Bolts: The Basic Client Profile • Random Thoughts
- 8. Copyright © 2014 Brian Campbell. All rights reserved. 8 Passwords are Broken For Users Death by a Thousand Passwords true story: “holyfucknotanotherfuckingpassword1”
- 9. Copyright © 2014 Brian Campbell. All rights reserved. 9 Passwords are Broken For Users What? A Well Regarded Fortune 500 Financial Services Company
- 10. Copyright © 2014 Brian Campbell. All rights reserved. 10 Passwords also Broken for Service Providers • Hell on user registration conversion rates • Managing passwords is hard – Just ask Adobe or LinkedIn or Kickstarter or…
- 11. Copyright © 2014 Brian Campbell. All rights reserved. 11 Agenda • Introductions • Framing the Problem • OpenID Connect as an Emergent Solution • Nuts & Bolts: The Basic Client Profile • Random Thoughts
- 12. Copyright © 2014 Brian Campbell. All rights reserved. 12 Introducing OpenID Connect • Easily and securely get an answer to the question: “What is the identity of the person currently using this browser or native app?” – Without taking on the responsibility of storing and managing passwords, which is nice • Built on top of OAuth 2.0 using familiar and widely available stuff like JSON and HTTP • Adds an ID Token (JWT) for user authentication to the client • API access and SSO together
- 13. Copyright © 2014 Brian Campbell. All rights reserved. 13 Unlike Predecessors
- 14. Copyright © 2014 Brian Campbell. All rights reserved. 14 OAuth 2.0 In A Nutshell Client Resource Server Authorization Server Authorization Endpoint Token Endpoint Important Stuff Where the magic happens
- 15. Copyright © 2014 Brian Campbell. All rights reserved. 15 OAuth 2.0 JOSE WebFinger OpenID Connect
- 16. Copyright © 2014 Brian Campbell. All rights reserved. 16 OpenID Connect is built on OAuth 2.0 Discovery Client Relying Party Resource Server Authorization Server Identity Provider or IDP or OpenID Provider or OP Authorization Endpoint Token Endpoint Important Stuff Userinfo Endpoint Registration Endpoint JWKS Endpoint JWKS Endpoint Validate (JWT) ID Token /.well-known /webfinger /openid-configuration Check Session IFrame End Session Endpoint
- 17. Copyright © 2014 Brian Campbell. All rights reserved. 17 Didn’t Someone Say “Simple”? • It wasn’t me • It’s not simple, it’s complicated • But the burden of complexity has been shifted to the Identity Provider, where it’s more appropriate • Many deployments can be à la carte Mr. Boombastic https://www.flickr.com/photos/67589493@N00/166195826 (cropped) https://creativecommons.org/licenses/by/2.0/
- 18. Copyright © 2014 Brian Campbell. All rights reserved. 18 Agenda • Introductions • Framing the Problem • OpenID Connect as an Emergent Solution • Nuts & Bolts: The Basic Client Profile • Random Thoughts
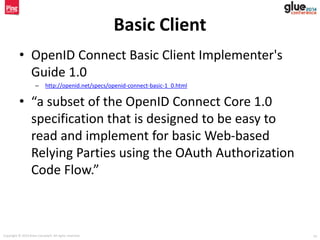
- 19. Copyright © 2014 Brian Campbell. All rights reserved. 19 Basic Client • OpenID Connect Basic Client Implementer's Guide 1.0 – http://openid.net/specs/openid-connect-basic-1_0.html • “a subset of the OpenID Connect Core 1.0 specification that is designed to be easy to read and implement for basic Web-based Relying Parties using the OAuth Authorization Code Flow.”
- 20. Copyright © 2014 Brian Campbell. All rights reserved. 20 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request
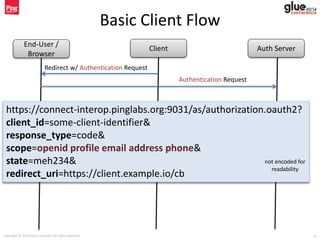
- 21. Copyright © 2014 Brian Campbell. All rights reserved. 21 Basic Client Flow End-User / Browser Client Auth Server https://connect-interop.pinglabs.org:9031/as/authorization.oauth2? client_id=some-client-identifier& response_type=code& scope=openid profile email address phone& state=meh234& redirect_uri=https://client.example.io/cb Redirect w/ Authentication Request Authentication Request not encoded for readability
- 22. Copyright © 2014 Brian Campbell. All rights reserved. 22 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User
- 23. Copyright © 2014 Brian Campbell. All rights reserved. 23 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User
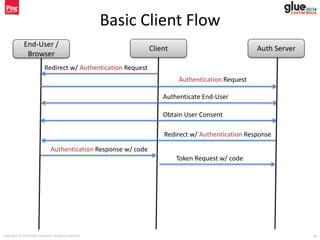
- 24. Copyright © 2014 Brian Campbell. All rights reserved. 24 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent
- 25. Copyright © 2014 Brian Campbell. All rights reserved. 25 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent
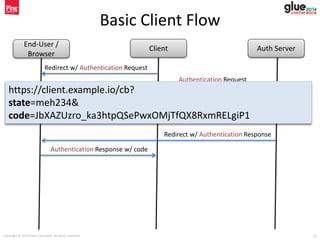
- 26. Copyright © 2014 Brian Campbell. All rights reserved. 26 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code
- 27. Copyright © 2014 Brian Campbell. All rights reserved. 27 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code https://client.example.io/cb? state=meh234& code=JbXAZUzro_ka3htpQSePwxOMjTfQX8RxmRELgiP1
- 28. Copyright © 2014 Brian Campbell. All rights reserved. 28 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code
- 29. Copyright © 2014 Brian Campbell. All rights reserved. 29 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code POST /as/token.oauth2 HTTP/1.1 Host: connect-interop.pinglabs.org:9031 Content-Length: 185 Content-Type: application/x-www-form-urlencoded client_id=some-client-identifier& grant_type=authorization_code& client_secret=super-duper-password& redirect_uri=https://client.example.io/cb& code=JbXAZUzro_ka3htpQSePwxOMjTfQX8RxmRELgiP1 not encoded for readability
- 30. Copyright © 2014 Brian Campbell. All rights reserved. 30 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code Token Response w/ access & ID token
- 31. Copyright © 2014 Brian Campbell. All rights reserved. 31 Basic Client Flow End-User / Browser Token Response w/ access & ID token Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code HTTP/1.1 200 OK Date: Tue, 13 May 2014 15:43:14 GMT Cache-Control: no-cache, no-store Pragma: no-cache max-age: Thu, 01 Jan 1970 00:00:00 GMT Content-Type: application/json;charset=UTF-8 Expires: Thu, 01 Jan 1970 00:00:00 GMT Transfer-Encoding: chunked {"token_type":"Bearer", "expires_in":600, "id_token":"eyJhbGciOiJub25lIn0.eyJzdWIiOiIxMDAxIiwiYXVkIjoic 29tZS1jbGllbnQtaWRlbnRpZmllciIsImp0aSI6Ijc2UnJHdkM1bDNRT 1BPMDVwTGpVdmEiLCJpc3MiOiJodHRwczpcL1wvY29ubmVjdC1p bnRlcm9wLnBpbmdsYWJzLm9yZzo5MDMxIiwiaWF0IjoxMzk5OTk 1Nzg1LCJleHAiOjEzOTk5OTYzODV9.", "access_token":"zfrQZYtamGHS6ZYXdSV4Yo"}
- 32. Copyright © 2014 Brian Campbell. All rights reserved. 32 Token Response w/ access & ID token Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code eyJhbGciOiJub25lIn0. eyJzdWIiOiIxMDAxIiwiYXVkIjoic29tZS1jbGllbnQtaWRlbnRpZmllciI sImp0aSI6Ijc2UnJHdkM1bDNRT1BPMDVwTGpVdmEiLCJpc3MiOiJ odHRwczpcL1wvY29ubmVjdC1pbnRlcm9wLnBpbmdsYWJzLm9yZ zo5MDMxIiwiaWF0IjoxMzk5OTk1Nzg1LCJleHAiOjEzOTk5OTYzOD V9. {"alg":"none”} {"sub":"1001", "aud":"some-client-identifier", "jti":"76RrGvC5l3QOPO05pLjUva", "iss":"https://connect-interop.pinglabs.org:9031", "iat":1399995785, "exp":1399996385}
- 33. Copyright © 2014 Brian Campbell. All rights reserved. 33 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code Token Response w/ access & ID token User Info Request w/ access token
- 34. Copyright © 2014 Brian Campbell. All rights reserved. 34 Token Response w/ access & ID token Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code GET /idp/userinfo.openid HTTP/1.1 Host: connect-interop.pinglabs.org:9031 Accept: */* Authorization: Bearer zfrQZYtamGHS6ZYXdSV4Yo User Info Request w/ access token
- 35. Copyright © 2014 Brian Campbell. All rights reserved. 35 Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code Token Response w/ access & ID token User Info Response User Info Request w/ access token
- 36. Copyright © 2014 Brian Campbell. All rights reserved. 36 User Info Request w/ access token Token Response w/ access & ID token Basic Client Flow End-User / Browser Client Auth Server Redirect w/ Authentication Request Authentication Request Authenticate End-User Obtain User Consent Redirect w/ Authentication Response Authentication Response w/ code Token Request w/ code User Info Response HTTP/1.1 200 OK Date: Tue, 13 May 2014 15:44:13 GMT Content-Type: application/json;charset=UTF-8 {"sub": "1001", "name": "Joe Doe", "given_name": "Joe", "family_name": "Doe", "preferred_username": "joe", "email": "[email protected]", "picture": "http://farm8.staticflickr.com/7224/7395022014_1f6f3b33c8_m.jpg", "address":{"formatted":"1234 South North Street, Amherst, MA 01002"}, "phone_number":"+1 (413) 867-5309"}
- 37. Copyright © 2014 Brian Campbell. All rights reserved. 37 That was Simple? • There are a lot of lines… • But from the Client’s perspective – Send the user off somewhere – Wait for them to show up on a callback – Make two simple HTTPS calls and validate some data – Done
- 38. Copyright © 2014 Brian Campbell. All rights reserved. 38 Agenda • Introductions • Framing the Problem • OpenID Connect as an Emergent Solution • Nuts & Bolts: The Basic Client Profile • Random Thoughts
- 39. Copyright © 2014 Brian Campbell. All rights reserved. 39 It’s Not All Rainbows & Unicorns • SAML’s IDP initiated POST is easily the most successful SSO deployment for the enterprise market • Some impedance mismatch as Connect doesn’t have straightforward equivalents
- 40. Copyright © 2014 Brian Campbell. All rights reserved. 40 Tweet Bait https://twitter.com/cloud_opinion/status/459481058480648193 one picture of a goat
- 41. Copyright © 2014 Brian Campbell. All rights reserved. 41 I’m Done.

![OpenID Connect
a simple[sic] single sign-on & identity
layer on top of OAuth 2.0
Brian Campbell
@__b_c
Copyright © 2014 Brian Campbell. All rights reserved.](https://image.slidesharecdn.com/gluecon2014-oidc-140521065808-phpapp01/85/OpenID-Connect-a-simple-sic-single-sign-on-identity-layer-on-top-of-OAuth-2-0-1-320.jpg)