Optimizing On Demand Weight -Based Clustering Using Trust Model for Mobile Ad Hoc Networks
- 1. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 DOI : 10.5121/ijasuc.2010.1408 81 Optimizing On Demand Weight -Based Clustering Using Trust Model for Mobile Ad Hoc Networks 1 V.G.Rani and 2 Dr.M.Punithavelli 1 Research and Development Center Bharathiar University, Coimbatore, India. [email protected] 2 Director, Department of Computer Science, Sri Ramakrishna College of Arts and Science for women, Coimbatore, India. [email protected] Abstract: Mobile ad hoc networks are growing in popularity due to the explosive growth of modern devices with wireless capability such as laptop, mobile phones, PDA, etc., makes the application more challenging. The mobile nodes are vulnerable to security attacks. To protect the ad hoc network it is essential to evaluate the trust worthiness. The proposed TWCA is similar to WCA in terms of cluster formation and cluster head election. However, in WCA security features are not included. The proposed TWCA is a cluster based trust evaluation, in which the mobile nodes are grouped into clusters with one cluster head. It establishes trust relationship for the cluster based on the previous transaction result. The simulation result confirms the efficiency of our scheme than the WCA and SEMC. Keywords: Ad Hoc networks, Clustering, Security, Trust. 1. Introduction Hand held devices have faster processing power and consumes less energy. Most of the technologies available today for mobile communication are based on existing cellular communication architecture, eg., Cellular Digital Packet Data(CDPD) for connection to packet- switched network [3], and Global System for Mobiles (GSM) [17] for connection to circuit switched networks. For the Internet, Mobile IP [20] provides a one hop wireless connection of mobile computers to the fixed network. Mobile ad hoc network is such type of network which is a collection of wireless communication nodes that are dynamically self configure to form a network without any fixed infrastructure or centralized administration. Their life duration is generally short. Each node in a MANET is free to move independently in any direction, and will therefore frequent change of topology is unavoidable. Earlier this type of network was used only in military purpose, now the need of wireless and easy installation is most wanted in the civilian applications also. Applications of ad-hoc networks range from military tactical application to civil rapid deployment such as emergency search and rescue missions, data collection sensor networks and instantaneous class room and meeting room application. Routing is a fundamental issue is MANET. There are no one-for-all schemes that work well for different network sizes, traffic overheads, and node mobility patterns. The routing schemes in dynamic environment must consider the topology changes while the packets are being routed. When a source node is unable to send a message directly to the destination node due to the limited transmission range, it uses the intermediate nodes to forward the message. Each node must forward traffic unrelated to its own use, and therefore be routers.
- 2. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 82 Routing in MANET are classified in to four major groups namely, flooding, proactive, reactive and hybrid. Flooding is a distributed process in which node transmit control message to all its neighbors consequently until the message has been send to the entire network. This type of routing is simple but it generates a huge amount of traffic. In proactive routing, every node in the network will maintain the valid rout. These type of routing is mostly applied for small network because of increasing overhead when the network size increase. Reactive routing performs well for small scale network but it does not support for large scale networks due to the increasing in high load. The best way to solve the problem of scalability and efficient solution is hybrid routing, which is based on implementation of a hierarchical approach called clustering. In the following section II give a brief overview of the security and the existing techniques I mobile ad hoc networks. In section III we describe the new security concept is described. Our work result is discussed in section IV and compared with the well popular algorithms. Finally Section V concludes the paper and gives the future work. 2. Security of Mobile Ad Hoc Network Mobile wireless networks are more prone to security threads than the wired network. Due to the dynamic and cooperative nature of the network it is very difficult to manage the security. Unlike wired network where an adversary must gain physical access to the network. Ad hoc networks experience common security vulnerabilities that cause attacks such as denial of service attack, intruding, spoofing, eavesdropping and signal jamming. Attacks in ad hoc network can be divided into two classes, passive attack and active attacks. Detection of passive attacks is very difficult since the operation of the network itself does not get affected. Active attacks can be classified into two classes, external and internal attack. External attack is carried out by the nodes that are not belonging to the network. Internal attack are carried out by the compromised nodes in the network. Researchers have already proposed a number of security solutions. Looking from the current research, many of them are trying to give better security solution based on hierarchical mechanism. In [1], [2] cluster based distribution authentication were proposed to detect the compromising nodes. In [3],[4] the distributed clustering algorithm used the trust level and mobility metrics for the cluster head election .the more value of reputation the node has, the better the node is. Several public key management protocols have been proposed for ad hoc networks. PKI (Public Key Infrastructure) use digitally signed certificate to verify the identity of the owner. In this method each user has to receive a digitally signed certificate from the certificate authority (CA). Popular network authentication architecture include X.509 standard [5] and Kerberos [6]. Traditional CA based solution does not meet the requirements of the mobile ad hoc network due to the absence of infrastructure and lack of centralized network. Partially Distributed certificate authority [7] which uses threshold (k,n) schemes for distributing the certificate authority to a set specialized node. The self-issued certificate proposed [8] which is similar to PGP in the sense that public key certificate are issued by user. Therefore, our design aims to optimize the WCA well-known weight clustering algorithm in terms of security. In our model the trust was adopted from the Chen and Yang [9]. Proposed model is divided into network model and trusted model.
- 3. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 83 3. Clustering in Ad Hoc Network MANET with the plane structure will increase routing control overhead and the scalability problem. Clustering the mobile node helps to reduce network traffic, because each node has only the information of the nodes which belong to the same group. Choosing the optimal clustering assignment is an NP-hard problem [1].Clustering algorithm will help to construct the hierarchical topology which will solve the above problem. Clustering has five outstanding advantages over other protocols. First, multiple channels are used efficiently and also it improves system capacity [26, 28, 29, 30, and 31]. Second, the exchange of control overhead is reduced and strengthens node management [27, 28, 29, 30, 31, and 32].Third, easy to implement local synchronization of network [28, 31, and 33]. Fourth, quality of service routing for multimedia services efficiently [30, 31, 33, and 34]. Finally, it supports large no of nodes [32, 35]. a. Overview of existing clustering Algorithms: There are several studies regarding clustering algorithm for Ad hoc networks are carried out, LCA[2] (Link Clustering Algorithm) which creates bigger clusters and requires less frequent cluster reorganizations. Lowest Identity [10] (LID), cluster head election is based on lowest identity based node among the neighbors, the system performance is better that the HID in terms of throughput. Least Cluster head Change (LCC) [8] .Maximum Connectivity Clustering (MCC) [7] is based on the degree of connectivity. a node is elected as cluster head if it is the highest connected node. Mobility Metric Based Algorithm (MOBIC) [9], where received signal strength is the key parameter to measure the relative mobility. The weaknesses of the algorithm, large cluster setup time and high reaffiliation rate increases computation and communication overhead. On demand Weight based clustering algorithm (WCA) [18] which elect lowest weighted node and weight is calculated by considering various factors like degree of the node, mobility, battery power and transmission power. Strength of this algorithm is stability and very low reaffiliation which reduce the overhead. b. Cluster structure and Cluster formation The nodes in the network are subdivided into groups called cluster. A node may hold one of the three stages namely cluster head, gateway node, and member node. One node is elected with some criteria as cluster head and others will be the members of the cluster and can communicate with the cluster head and vice versa. Each cluster has exactly one cluster head which is one hop away from its entire cluster member. Each cluster member belongs to one cluster only and the set of cluster head is known as a dominant set. The elected cluster head takes the responsibility for forwarding the information as well as the membership management. Electing of cluster head and clusters are formed by the cluster formation algorithm and then maintained by the cluster maintenance algorithm. Initially all nodes will be in undecided status, which means that a node is still in search of its cluster. Cluster head consumes more battery power than an ordinary node since it has an extra responsibility than the other nodes in the cluster. Due to the dynamic nature of the mobile node the cluster heads are constantly changing and creating a large overhead, minimizing the number of cluster head becomes essential. During the cluster formation, nodes that are within the transmission range of 2 cluster head are called gateway nodes and these types of nodes will take care of intra cluster communication.
- 4. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 84 Every node should broadcast a HELLO message regularly. Cluster member adds it IP address into its HELLO message and a cluster head adds the IP address of its cluster member into its HELLO message. During the cluster head discover process, cluster member keeps the IP address of other cluster head that can hear. When the former cluster head moves away or a cluster member does not receive three HELLO packets continuously from its cluster head, it considers that the wireless link between them is broken. Thus, a cluster member chooses the latest cluster head in the routing table as its new cluster head, which is one hop from it, or becomes itself a cluster head if it cannot hear any existing cluster head. After broadcasting its HELLO right next packet, the selected cluster head is informed that a new cluster member has joined its group. The cluster member will obtain the confirmation of its new cluster head when it receives the HELLO packet that carries its IP address. 4. Trust in Ad Hoc Network To improve security in MANET is to develop mechanisms that allow a node to evaluate trustworthiness of other nodes. In ad hoc network the trust relationship can be established in two ways: Direct observation and recommendation. In the first case the node directly observe the other nodes behavior, such as packet dropping etc. In the second way trust of one node is taken from the recommendation of another node. In this work the trust concept was same as the trust model [9].Trust can be discrete and continuous. Discrete values are easy to represent and classify but it will not suite for ad hoc network. Ad hoc network is dynamic in nature due to the mobility of the nodes. In our trust model, the trust has continuous range form 0 to +1 representing the trust level from complete distrust to most trust. Trust model evaluation for mobile ad hoc networks has been studied for several research efforts. Trust is calculated in two ways as direct trust which calculates by tacking the direct information between two nodes. The result of the previous transaction is classified as success and failure. 5. Models a. Network Model Clustering is proved in optimizing the use of network bandwidth and minimizing the amount of storage of communication information [10]. The clustering schemes of MANET can be classified according to different criteria as Mobility based clustering [11-13].which takes the mobility of the mobile nodes into consideration. Movement of mobile node will cause the topology changes frequently. In this type of clustering the nodes are grouped according to the speed of the node. Energy efficient based clustering [14-16], these type of clustering balance energy consumption among different mobile nodes, so as to prolong the life time of the network. Load balancing clustering [14, 17] here the number of nodes in each clusters will have similar size. Thus, the load of the network will be equally distributed. Combined weight based clustering [18] usually consider multiple metrics, such as node degreoe, cluster size, mobility speed, and battery energy for cluster configuration and especially for the election of clusterhead. The weighting factor can be adjusted to different application scenario. Chatterjee et al. in [18] propose a weighted clustering mechanism called WCA (Weight clustering Algorithm). Four parameters are consider in the weight computation, namely the node degree, the battery power, the mobility and the transmission power are consider for the selection of cluster head election. The combined weight associated to a node v is defined as
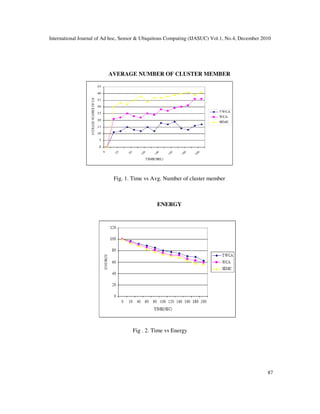
- 5. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 85 W v = w 1 ∆ v + w 2 D v + w 3 M v + w 4 P v , Where, Mv is the measure of mobility taken by computing the running average speed of every node during a specified time T. ∆v is the degree difference obtained by first calculating the number of neighbors of each node. To ensure the load balancing the degree difference is calculated as |d v -δ| for every node v. the parameter D v is defined as sum of distance from a given node to its entire neighbor. The parameter Pv is the cumulative time of a node being a cluster head. Pv is measured of how much battery power has been consumed. Interesting work presented in which WCA is optimized by advanced computational methods such as genetic algorithm [19], simulated annealing [20] and particle swarm optimization [21]. In this work we have proposed a method to optimize the WCA in terms of security. As mentioned in [21, 22, 23], security problem must be taken into consideration in all schemes devoted to ad hoc network. b. Trust model Direct trust computation: Direct trust between two nodes N i and N j . node N i takes into account the individual experience of the past transaction with N j . If N i and N j have n times transaction with m times success, the direct value is calculated as: 0λ0,nm,, λn λ/2m Tij D >≥ + + = (1) The direct trust value is taken as 0.5 if there is no previous interaction between Ni and Nj. If the first interaction is success, the direct trust value increases rapidly. On the contrary, it is decreases rapidly. Recommendation trust computation: recommendation trust is calculated to the unknown or unfamiliar nodes. Cluster head calculates the recommendation trust for every node in the cluster. .,T/T.TT hi D 1 hi D ij D 1 hi D ij R jiHwhereT n i n i ≠>= ∑∑ == (2) Where, n is the number of nodes in the current cluster, the aggregation weight is the direct trust value of node Ni by cluster head. The direct trust is the recommendation value given by the cluster head to node NijDTijDTi about the node Nj . cluster head collects the recommendation and calculates the recommendation value of N j by by formula (2). Note that the recommendation trust of cluster head is always 1 in the proposed model. 6. Experimental and Analysis We have implemented our design in the network simulator NS2. We evaluated the performance of our schemes as listed in the table 1.We have taken SEMC where The result of time vs. average number of cluster members is depicted in fig.1 which shows the less members than the other two. Fig 2 in the graph is drawn for energy comparison between WCA, SEMC and
- 6. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 86 TWCA. Here TWCA consumes very lower energy when compared to other Protocols. The power can be saved up to 97.200 joules. When the time increases consumed energy decreases corresponding so that energy is indirectly proportional to the time. In these graph particularly in energy consumption it should be low if it is best protocol. In Fig 3 for a transmission time of 200, number of cluster head is less in TWCA , which was not in the case of WCA and SEMC. The packets delivery ratio in a network is higher than other protocols. It is also fully directly proportional to the time. When time increases packet delivery ratio also increases correspondingly. Fig 5 shows a graph for packets delivery ratio after modification is shown below as, and it results TWCA is performing well than WCA and SEMC. The number of packets received in TWCA is higher when compared to WCA and SEMC. Fig 4 shows a graph for throughput in network. When time increases number of packets received at receiver side also increases correspondingly. It is defined as the number of packets received at destination side at a particular time. The results show that TWCA is performing well than WCA and SEMC. In Fig 5 the number of cluster head is less than the TWCA and SEMC. SIMULATION PARAMETERS Number of Nodes 80 Size of the Network 1300 x1200 Speed of the Node 20 m/s Transmission range 250m Pause Time 10 Broadcast intervals 0.01 Number of members 5 Number of Clusters 16 Simulation time 200 sec
- 7. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 87 AVERAGE NUMBER OF CLUSTER MEMBER Fig. 1. Time vs Avg. Number of cluster member ENERGY Fig . 2. Time vs Energy
- 8. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 88 AVERAGE NUMBER OF CLUSTERHEAD Fig 3. Time vs Avg. Number of Cluster THROUGHPUT Fig 4 : Time Vs Throughput
- 9. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 89 PACKET RECEIVED Fig 5: Time Vs Packet received 7. Conclusion and Future work In this proposed TWCA (Trusted Weight Clustering Algorithm) we have optimized the WCA with a security concept based on trust. WCA is one such algorithm which can dynamically adapt itself with the ever changing topology of ad hoc networks. The proposed model elects the cluster head according to the weight as in WCA. Using the concept of Trust proposed in [25] the WCA was optimized and the result is compared with both WCA and SEMC [26] and the result shows that TWCA achieved significant performance compared to the other two algorithms in term of average number of cluster member, average number of cluster head, energy, throughput and packed received ratio. In future work, we plan to introduce a new trust model which can support more security concepts and we have a plan to evaluate TWCA in Large-sized mobile ad hoc networks in order to measure the performance. References [1] A.Rachedi, A.Benslimane, “Trust and mobility-based clustering algorithm for secure mobile ad hoc networks”,Proceeding of ICSNC’06, IEEE Computer Society Press, Tahiti, 2006, pp.72-77. [2] M.Y.Hsieh, Y.M.Huang, and H.C.Chao, “Adaptive security design with malicious node detection in cluster-based sensor networks”, Computer Communications, Elsevier B.V.,2007, pp.2385-2400.. [3] S.Jin, C.park, D.Choi, K.Chung, and H.Yoon, “Cluster-based trust evaluation schemes in an ad hoc networks”,ETRI Journal, Seoul,2005,pp,465-468.
- 10. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 90 [4] M.E. Elhdhili, L.B Azzouz, and F. Kamoun, “CASAN:Clustering algorithm for security in ad hoc networks”, Computer Communications, Elsevier B.V..,2008,pp.2972-2980. [5] PKIX Workingg Group, “Internet X.509 Public Key Infrastructure,,”draft-ietf-pkix-roadmap- 06.txt,2002. [6] J.Kohl and B.neuman, “The Kerberous nnetwork authentication service(version 5),” RFC-1510,1991. [7] L.Zhon and Z.J.Hass,”Securing Ad Hoc Networks,” IEEE Networks Magazine, Vol.13,Issue 6,pp.24- 30,1999. [8]. J-P. Hubaux, L. Buttyan, and S. Capkun, “The Quest for Security in Mobile Ad Hoc Networks,” Proceedings of the 2001 ACM International Symposium on Mobile ad hoc networking & computing, Long Beach, CA, USA, pp. 146-155, October 4-5 2001. [9].Chen Alguo, XU Guoai, YANG-Yixian, “A Cluster Based Trust Model For Mobile Ad Hoc networks,” Wireless Communication , 2008,WiCOM’08, pp. 1-4. [10].Edith.C.H.Ngai, and Michael R.Lyu, “Trust and Cluster Based Authentication Services in Mobile Ad Hoc Network,” 2 nd international workshop on mobile distributed computing (MDC) ,2004 ,pp.582-587 [11]. A. B. MaDonald and T. F. Znati, “A Mobility-based Frame Work for Adaptive Clustering in Wireless Ad Hoc Networks,” IEEEJSAC, vol. 17, Aug. 1999., pp. 1466–87. [12]. P. Basu, N. Khan, and T. D. C. Little, “A Mobility Based Metric for Clustering in Mobile Ad Hoc Networks,” in Proc. IEEE ICDCSW’01, Apr. 2001, pp. 413–18 [13] A. B. McDonald and T. F. Znati, “Design and Performance of a Distributed Dynamic Clustering Algorithm for Ad-Hoc Networks,” in Proc. 34th Annual Simulation Symp., Apr. 2001, pp. 27–35. [14] A. D. Amis and R. Prakash, “Load-Balancing Clusters in Wireless Ad Hoc Networks,” in Proc. 3rd IEEE ASSET’00, Mar. 2000, pp. 25–32. [15] J. Wu et al., “On Calculating Power-Aware Connected Dominating Sets for Efficient Routing in Ad Hoc Wireless Networks,” J. Commun. and Networks, vol. 4, no. 1, Mar. 2002, pp. 59–70. [16] J.-H. Ryu, S. Song, and D.-H. Cho, “New Clustering Schemes for Energy Conservation in Two-Tiered Mobile Ad-Hoc Networks,” in Proc. IEEE ICC’01, vo1. 3, June 2001, pp. 862–66. [17] T. Ohta, S. Inoue, and Y. Kakuda, “An Adaptive Multihop Clustering Scheme for Highly Mobile Ad Hoc Networks,” in Proc. 6th ISADS’03, Apr. 2003. [18] M. Chatterjee, S. K. Das, and D. Turgut, “An On-Demand Weighted Clustering Algorithm (WCA) for Ad hoc Networks,” in Proc. IEEE Globecom’00, 2000, pp. 1697–701. [19] D. Turgut, S. Das, R. Elmasri, and B. Turgut, “Optimizing clustering algorithm in mobile ad hoc networks using genetic algorithmic approach,”in Proceedings of GLOBECOM 2002, November 2002. [20] D. Turgut, B. Turgut, R. Elmasri, and T. V. Le, “Optimizing clustering algorithm in mobile ad hoc networks using simulated annealing,” in Proceedings of WCNC 2003, March 2003. [21] C. Ji, Y. Zhang, S. Gao, P. Yuan, and Z. Li, “Particle swarm optimization for mobile ad hoc networks clustering,” in Networking, Sensing and Control, 2004 IEEE International Conference on, vol. 1, 2004, pp. 372– 375. [22] Mohamed Elhoucine Elhdhili, Lamia Ben Azzouz, Farouk Kamoun. A Totally Distributed Cluster Based KeyManagement Model for Ad hoc Networks. Med-Hoc-Net 2004, The Third Annual Mediterranean Ad Hoc Networking Workshop. [23] M. Bechler, H.-J. Hof, D. Kraft, F. Pählke, L. Wolf. A Cluster-Based Security Architecture for Ad Hoc Networks. IEEE, INFOCOM 2004.
- 11. International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010 91 [24] Panagiotis Papadimitratos, and Zygmunt J. Haas. Secure Data Communication in. Mobile Ad Hoc Networks. IEEE Journal on Selected Areas In Communications, Vol. 24,No. 2, 2006 PP. 343,356. [25] Fatiha Djemili Tolba, Damien Magoni, Pascal Lorenz, "A Stable Clustering Algorithm for Highly Mobile Ad Hoc Networks," icsnc, pp.11, Second International Conference on Systems and Networks Communications (ICSNC 2007), 2007 [26] A. Ephremides, J. E. Wieselthier and D. J. Baker, “A design concept for reliable mobile radio networks with frequency hopping signaling,” Proc. IEEE, vol. 75, no. 1, Jan. 1987, pp. 56-73. [27] A. Bhatnagar and T. G. Robertazzi, “Layer Net: a new self-organizing network protocols,” Proc. IEEE MILCOM ’90, pp. 845-849. [28] M. Gerla and T. C. Tsai, “Multicluster, mobile, multimedia radio network,” ACM-Baltzer J. Wireless Networks, vol. 1, no. 3, 1995, pp. 255-65. [29] A. Alwan, R. Bagrodia, N. Bambos et al.,“Adaptive mobile multimedia networks,” IEEE Personal Commun., Apr. 1996, pp. 34-51. [30] A. B. McDonald and T. F. Znati, “A mobilitybased framework for adaptive clustering in wireless ad hoc networks,” IEEE J. Select. Areas Commun., vol. 17, no. 8, Aug. 1999, pp. 1466-1487. [31] C. R. Lin and M. Gerla, “Adaptive clustering for mobile wireless networks,” IEEE J. Select. Areas Commun., vol.15, no. 7, Sep. 1997, pp. 1265-1275. [32] W. Chen, N. Jain and S. Singh, “ANMP: ad hoc network management protocol,” IEEE J. Select. Areas Commun., vol. 17, no. 8, Aug. 1999, pp. 1506-1531. [33] C. R. Lin and M. Geria, “Real-time support in multihop wireless network,” ACM-Baltzer J. Wireless Networks, vol. 5, no. 2, 1999, pp. 125-135. [34] S. Chen and K. Nahrstedt, “Distributed quality-of-service routing in ad hoc networks,” IEEE JSAC, vol. 17, no. 8, Aug. 1999, pp. 1488-1505. [35] A. Iwata, C.-C. Chiang, G. Pei, M. Gerla and T.-W. Chen, “Scalable routing strategies for ad hoc wireless networks,” IEEE J. Select. Areas Commun., vol. 17, no. 8, Aug. 1999, pp. 1369-1379.
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
DOI : 10.5121/ijasuc.2010.1408 81
Optimizing On Demand Weight -Based Clustering
Using Trust Model for Mobile Ad Hoc Networks
1
V.G.Rani and
2
Dr.M.Punithavelli
1
Research and Development Center Bharathiar University, Coimbatore, India.
ranikhans@gmail.com
2
Director, Department of Computer Science, Sri Ramakrishna College of Arts and
Science for women, Coimbatore, India.
mpunitha_srcw@yahoo.co.in
Abstract: Mobile ad hoc networks are growing in popularity due to the explosive growth of modern
devices with wireless capability such as laptop, mobile phones, PDA, etc., makes the application more
challenging. The mobile nodes are vulnerable to security attacks. To protect the ad hoc network it is
essential to evaluate the trust worthiness. The proposed TWCA is similar to WCA in terms of cluster
formation and cluster head election. However, in WCA security features are not included. The proposed
TWCA is a cluster based trust evaluation, in which the mobile nodes are grouped into clusters with one
cluster head. It establishes trust relationship for the cluster based on the previous transaction result. The
simulation result confirms the efficiency of our scheme than the WCA and SEMC.
Keywords: Ad Hoc networks, Clustering, Security, Trust.
1. Introduction
Hand held devices have faster processing power and consumes less energy. Most of the
technologies available today for mobile communication are based on existing cellular
communication architecture, eg., Cellular Digital Packet Data(CDPD) for connection to packet-
switched network [3], and Global System for Mobiles (GSM) [17] for connection to circuit
switched networks. For the Internet, Mobile IP [20] provides a one hop wireless connection of
mobile computers to the fixed network. Mobile ad hoc network is such type of network which is a
collection of wireless communication nodes that are dynamically self configure to form a network
without any fixed infrastructure or centralized administration. Their life duration is generally
short. Each node in a MANET is free to move independently in any direction, and will therefore
frequent change of topology is unavoidable. Earlier this type of network was used only in military
purpose, now the need of wireless and easy installation is most wanted in the civilian applications
also. Applications of ad-hoc networks range from military tactical application to civil rapid
deployment such as emergency search and rescue missions, data collection sensor networks and
instantaneous class room and meeting room application.
Routing is a fundamental issue is MANET. There are no one-for-all schemes that work
well for different network sizes, traffic overheads, and node mobility patterns. The routing
schemes in dynamic environment must consider the topology changes while the packets are being
routed. When a source node is unable to send a message directly to the destination node due to
the limited transmission range, it uses the intermediate nodes to forward the message. Each node
must forward traffic unrelated to its own use, and therefore be routers.](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-1-320.jpg)
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
82
Routing in MANET are classified in to four major groups namely, flooding, proactive,
reactive and hybrid. Flooding is a distributed process in which node transmit control message to
all its neighbors consequently until the message has been send to the entire network. This type of
routing is simple but it generates a huge amount of traffic. In proactive routing, every node in the
network will maintain the valid rout. These type of routing is mostly applied for small network
because of increasing overhead when the network size increase. Reactive routing performs well
for small scale network but it does not support for large scale networks due to the increasing in
high load. The best way to solve the problem of scalability and efficient solution is hybrid
routing, which is based on implementation of a hierarchical approach called clustering.
In the following section II give a brief overview of the security and the existing
techniques I mobile ad hoc networks. In section III we describe the new security concept is
described. Our work result is discussed in section IV and compared with the well popular
algorithms. Finally Section V concludes the paper and gives the future work.
2. Security of Mobile Ad Hoc Network
Mobile wireless networks are more prone to security threads than the wired network. Due
to the dynamic and cooperative nature of the network it is very difficult to manage the security.
Unlike wired network where an adversary must gain physical access to the network. Ad hoc
networks experience common security vulnerabilities that cause attacks such as denial of service
attack, intruding, spoofing, eavesdropping and signal jamming. Attacks in ad hoc network can be
divided into two classes, passive attack and active attacks. Detection of passive attacks is very
difficult since the operation of the network itself does not get affected. Active attacks can be
classified into two classes, external and internal attack. External attack is carried out by the nodes
that are not belonging to the network. Internal attack are carried out by the compromised nodes in
the network.
Researchers have already proposed a number of security solutions. Looking from the
current research, many of them are trying to give better security solution based on hierarchical
mechanism. In [1], [2] cluster based distribution authentication were proposed to detect the
compromising nodes. In [3],[4] the distributed clustering algorithm used the trust level and
mobility metrics for the cluster head election .the more value of reputation the node has, the better
the node is. Several public key management protocols have been proposed for ad hoc networks.
PKI (Public Key Infrastructure) use digitally signed certificate to verify the identity of the owner.
In this method each user has to receive a digitally signed certificate from the certificate authority
(CA). Popular network authentication architecture include X.509 standard [5] and Kerberos [6].
Traditional CA based solution does not meet the requirements of the mobile ad hoc network due
to the absence of infrastructure and lack of centralized network. Partially Distributed certificate
authority [7] which uses threshold (k,n) schemes for distributing the certificate authority to a set
specialized node. The self-issued certificate proposed [8] which is similar to PGP in the sense that
public key certificate are issued by user.
Therefore, our design aims to optimize the WCA well-known weight clustering algorithm
in terms of security. In our model the trust was adopted from the Chen and Yang [9]. Proposed
model is divided into network model and trusted model.](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-2-320.jpg)
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
83
3. Clustering in Ad Hoc Network
MANET with the plane structure will increase routing control overhead and the
scalability problem. Clustering the mobile node helps to reduce network traffic, because each
node has only the information of the nodes which belong to the same group. Choosing the
optimal clustering assignment is an NP-hard problem [1].Clustering algorithm will help to
construct the hierarchical topology which will solve the above problem. Clustering has five
outstanding advantages over other protocols. First, multiple channels are used efficiently and also
it improves system capacity [26, 28, 29, 30, and 31]. Second, the exchange of control overhead is
reduced and strengthens node management [27, 28, 29, 30, 31, and 32].Third, easy to implement
local synchronization of network [28, 31, and 33]. Fourth, quality of service routing for
multimedia services efficiently [30, 31, 33, and 34]. Finally, it supports large no of nodes [32,
35].
a. Overview of existing clustering Algorithms:
There are several studies regarding clustering algorithm for Ad hoc networks are carried
out, LCA[2] (Link Clustering Algorithm) which creates bigger clusters and requires less frequent
cluster reorganizations. Lowest Identity [10] (LID), cluster head election is based on lowest
identity based node among the neighbors, the system performance is better that the HID in terms
of throughput. Least Cluster head Change (LCC) [8] .Maximum Connectivity Clustering (MCC)
[7] is based on the degree of connectivity. a node is elected as cluster head if it is the highest
connected node. Mobility Metric Based Algorithm (MOBIC) [9], where received signal strength
is the key parameter to measure the relative mobility. The weaknesses of the algorithm, large
cluster setup time and high reaffiliation rate increases computation and communication overhead.
On demand Weight based clustering algorithm (WCA) [18] which elect lowest weighted node
and weight is calculated by considering various factors like degree of the node, mobility, battery
power and transmission power. Strength of this algorithm is stability and very low reaffiliation
which reduce the overhead.
b. Cluster structure and Cluster formation
The nodes in the network are subdivided into groups called cluster. A node may hold one
of the three stages namely cluster head, gateway node, and member node. One node is elected
with some criteria as cluster head and others will be the members of the cluster and can
communicate with the cluster head and vice versa. Each cluster has exactly one cluster head
which is one hop away from its entire cluster member. Each cluster member belongs to one
cluster only and the set of cluster head is known as a dominant set. The elected cluster head takes
the responsibility for forwarding the information as well as the membership management.
Electing of cluster head and clusters are formed by the cluster formation algorithm and then
maintained by the cluster maintenance algorithm. Initially all nodes will be in undecided status,
which means that a node is still in search of its cluster. Cluster head consumes more battery
power than an ordinary node since it has an extra responsibility than the other nodes in the
cluster. Due to the dynamic nature of the mobile node the cluster heads are constantly changing
and creating a large overhead, minimizing the number of cluster head becomes essential. During
the cluster formation, nodes that are within the transmission range of 2 cluster head are called
gateway nodes and these types of nodes will take care of intra cluster communication.](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-3-320.jpg)
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
84
Every node should broadcast a HELLO message regularly. Cluster member adds it IP
address into its HELLO message and a cluster head adds the IP address of its cluster member into
its HELLO message. During the cluster head discover process, cluster member keeps the IP
address of other cluster head that can hear. When the former cluster head moves away or a
cluster member does not receive three HELLO packets continuously from its cluster head, it
considers that the wireless link between them is broken. Thus, a cluster member chooses the latest
cluster head in the routing table as its new cluster head, which is one hop from it, or becomes
itself a cluster head if it cannot hear any existing cluster head. After broadcasting its HELLO
right next packet, the selected cluster head is informed that a new cluster member has joined its
group. The cluster member will obtain the confirmation of its new cluster head when it receives
the HELLO packet that carries its IP address.
4. Trust in Ad Hoc Network
To improve security in MANET is to develop mechanisms that allow a node to evaluate
trustworthiness of other nodes. In ad hoc network the trust relationship can be established in two
ways: Direct observation and recommendation. In the first case the node directly observe the
other nodes behavior, such as packet dropping etc. In the second way trust of one node is taken
from the recommendation of another node. In this work the trust concept was same as the trust
model [9].Trust can be discrete and continuous. Discrete values are easy to represent and classify
but it will not suite for ad hoc network. Ad hoc network is dynamic in nature due to the mobility
of the nodes. In our trust model, the trust has continuous range form 0 to +1 representing the trust
level from complete distrust to most trust. Trust model evaluation for mobile ad hoc networks has
been studied for several research efforts. Trust is calculated in two ways as direct trust which
calculates by tacking the direct information between two nodes. The result of the previous
transaction is classified as success and failure.
5. Models
a. Network Model
Clustering is proved in optimizing the use of network bandwidth and minimizing the
amount of storage of communication information [10]. The clustering schemes of MANET can be
classified according to different criteria as Mobility based clustering [11-13].which takes the
mobility of the mobile nodes into consideration. Movement of mobile node will cause the
topology changes frequently. In this type of clustering the nodes are grouped according to the
speed of the node. Energy efficient based clustering [14-16], these type of clustering balance
energy consumption among different mobile nodes, so as to prolong the life time of the network.
Load balancing clustering [14, 17] here the number of nodes in each clusters will have similar
size. Thus, the load of the network will be equally distributed. Combined weight based clustering
[18] usually consider multiple metrics, such as node degreoe, cluster size, mobility speed, and
battery energy for cluster configuration and especially for the election of clusterhead. The
weighting factor can be adjusted to different application scenario. Chatterjee et al. in [18] propose
a weighted clustering mechanism called WCA (Weight clustering Algorithm). Four parameters
are consider in the weight computation, namely the node degree, the battery power, the mobility
and the transmission power are consider for the selection of cluster head election. The combined
weight associated to a node v is defined as](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-4-320.jpg)
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
85
W
v
= w
1
∆
v
+ w
2
D
v
+ w
3
M
v
+ w
4
P
v
,
Where, Mv is the measure of mobility taken by computing the running average speed of
every node during a specified time T. ∆v is the degree difference obtained by first calculating the
number of neighbors of each node. To ensure the load balancing the degree difference is
calculated as |d
v
-δ| for every node v. the parameter D
v
is defined as sum of distance from a given
node to its entire neighbor. The parameter Pv
is the cumulative time of a node being a cluster
head. Pv
is measured of how much battery power has been consumed. Interesting work presented
in which WCA is optimized by advanced computational methods such as genetic algorithm [19],
simulated annealing [20] and particle swarm optimization [21]. In this work we have proposed a
method to optimize the WCA in terms of security. As mentioned in [21, 22, 23], security problem
must be taken into consideration in all schemes devoted to ad hoc network.
b. Trust model
Direct trust computation: Direct trust between two nodes N
i
and N
j
. node N
i
takes into account
the individual experience of the past transaction with N
j
. If N
i
and N
j
have n times transaction
with m times success, the direct value is calculated as:
0λ0,nm,,
λn
λ/2m
Tij
D >≥
+
+
= (1)
The direct trust value is taken as 0.5 if there is no previous interaction between Ni and Nj.
If the first interaction is success, the direct trust value increases rapidly. On the contrary, it is
decreases rapidly.
Recommendation trust computation: recommendation trust is calculated to the
unknown or unfamiliar nodes. Cluster head calculates the recommendation trust for every node in
the cluster.
.,T/T.TT hi
D
1
hi
D
ij
D
1
hi
D
ij
R jiHwhereT
n
i
n
i
≠>= ∑∑ ==
(2)
Where, n is the number of nodes in the current cluster, the aggregation weight is the
direct trust value of node Ni by cluster head. The direct trust is the recommendation value given
by the cluster head to node NijDTijDTi
about the node Nj .
cluster head collects the recommendation
and calculates the recommendation value of N
j by
by formula (2). Note that the recommendation
trust of cluster head is always 1 in the proposed model.
6. Experimental and Analysis
We have implemented our design in the network simulator NS2. We evaluated the
performance of our schemes as listed in the table 1.We have taken SEMC where The result of
time vs. average number of cluster members is depicted in fig.1 which shows the less members
than the other two. Fig 2 in the graph is drawn for energy comparison between WCA, SEMC and](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-5-320.jpg)


![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
89
PACKET RECEIVED
Fig 5: Time Vs Packet received
7. Conclusion and Future work
In this proposed TWCA (Trusted Weight Clustering Algorithm) we have optimized the WCA
with a security concept based on trust. WCA is one such algorithm which can dynamically adapt
itself with the ever changing topology of ad hoc networks. The proposed model elects the cluster
head according to the weight as in WCA. Using the concept of Trust proposed in [25] the WCA
was optimized and the result is compared with both WCA and SEMC [26] and the result shows
that TWCA achieved significant performance compared to the other two algorithms in term of
average number of cluster member, average number of cluster head, energy, throughput and
packed received ratio. In future work, we plan to introduce a new trust model which can support
more security concepts and we have a plan to evaluate TWCA in Large-sized mobile ad hoc
networks in order to measure the performance.
References
[1] A.Rachedi, A.Benslimane, “Trust and mobility-based clustering algorithm for secure mobile ad hoc
networks”,Proceeding of ICSNC’06, IEEE Computer Society Press, Tahiti, 2006, pp.72-77.
[2] M.Y.Hsieh, Y.M.Huang, and H.C.Chao, “Adaptive security design with malicious node detection in
cluster-based sensor networks”, Computer Communications, Elsevier B.V.,2007, pp.2385-2400..
[3] S.Jin, C.park, D.Choi, K.Chung, and H.Yoon, “Cluster-based trust evaluation schemes in an ad hoc
networks”,ETRI Journal, Seoul,2005,pp,465-468.](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-9-320.jpg)
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
90
[4] M.E. Elhdhili, L.B Azzouz, and F. Kamoun, “CASAN:Clustering algorithm for security in ad hoc
networks”, Computer Communications, Elsevier B.V..,2008,pp.2972-2980.
[5] PKIX Workingg Group, “Internet X.509 Public Key Infrastructure,,”draft-ietf-pkix-roadmap-
06.txt,2002.
[6] J.Kohl and B.neuman, “The Kerberous nnetwork authentication service(version 5),” RFC-1510,1991.
[7] L.Zhon and Z.J.Hass,”Securing Ad Hoc Networks,” IEEE Networks Magazine, Vol.13,Issue 6,pp.24-
30,1999.
[8]. J-P. Hubaux, L. Buttyan, and S. Capkun, “The Quest for Security in Mobile Ad Hoc Networks,”
Proceedings of the 2001 ACM International Symposium on Mobile ad hoc networking & computing, Long
Beach, CA, USA, pp. 146-155, October 4-5 2001.
[9].Chen Alguo, XU Guoai, YANG-Yixian, “A Cluster Based Trust Model For Mobile Ad Hoc networks,”
Wireless Communication , 2008,WiCOM’08, pp. 1-4.
[10].Edith.C.H.Ngai, and Michael R.Lyu, “Trust and Cluster Based Authentication Services in Mobile Ad
Hoc Network,” 2
nd
international workshop on mobile distributed computing (MDC) ,2004 ,pp.582-587
[11]. A. B. MaDonald and T. F. Znati, “A Mobility-based Frame Work for Adaptive Clustering in Wireless
Ad Hoc Networks,” IEEEJSAC, vol. 17, Aug. 1999., pp. 1466–87.
[12]. P. Basu, N. Khan, and T. D. C. Little, “A Mobility Based Metric for Clustering in Mobile Ad Hoc
Networks,” in Proc. IEEE ICDCSW’01, Apr. 2001, pp. 413–18
[13] A. B. McDonald and T. F. Znati, “Design and Performance of a Distributed Dynamic Clustering
Algorithm for Ad-Hoc Networks,” in Proc. 34th Annual Simulation Symp., Apr. 2001, pp. 27–35.
[14] A. D. Amis and R. Prakash, “Load-Balancing Clusters in Wireless Ad Hoc Networks,” in Proc. 3rd
IEEE ASSET’00, Mar. 2000, pp. 25–32.
[15] J. Wu et al., “On Calculating Power-Aware Connected Dominating Sets for Efficient Routing in Ad
Hoc Wireless Networks,” J. Commun. and Networks, vol. 4, no. 1, Mar. 2002, pp. 59–70.
[16] J.-H. Ryu, S. Song, and D.-H. Cho, “New Clustering Schemes for Energy Conservation in Two-Tiered
Mobile Ad-Hoc Networks,” in Proc. IEEE ICC’01, vo1. 3, June 2001, pp. 862–66.
[17] T. Ohta, S. Inoue, and Y. Kakuda, “An Adaptive Multihop Clustering Scheme for Highly Mobile Ad
Hoc Networks,” in Proc. 6th ISADS’03, Apr. 2003.
[18] M. Chatterjee, S. K. Das, and D. Turgut, “An On-Demand Weighted Clustering Algorithm (WCA) for
Ad hoc Networks,” in Proc. IEEE Globecom’00, 2000, pp. 1697–701.
[19] D. Turgut, S. Das, R. Elmasri, and B. Turgut, “Optimizing clustering algorithm in mobile ad hoc
networks using genetic algorithmic approach,”in Proceedings of GLOBECOM 2002, November 2002.
[20] D. Turgut, B. Turgut, R. Elmasri, and T. V. Le, “Optimizing clustering algorithm in mobile ad hoc
networks using simulated annealing,” in Proceedings of WCNC 2003, March 2003.
[21] C. Ji, Y. Zhang, S. Gao, P. Yuan, and Z. Li, “Particle swarm optimization for mobile ad hoc networks
clustering,” in Networking, Sensing and Control, 2004 IEEE International Conference on, vol. 1, 2004, pp.
372– 375.
[22] Mohamed Elhoucine Elhdhili, Lamia Ben Azzouz, Farouk Kamoun. A Totally Distributed Cluster
Based KeyManagement Model for Ad hoc Networks. Med-Hoc-Net 2004, The Third Annual
Mediterranean Ad Hoc Networking Workshop.
[23] M. Bechler, H.-J. Hof, D. Kraft, F. Pählke, L. Wolf. A Cluster-Based Security Architecture for Ad
Hoc Networks. IEEE, INFOCOM 2004.](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-10-320.jpg)
![International Journal of Ad hoc, Sensor & Ubiquitous Computing (IJASUC) Vol.1, No.4, December 2010
91
[24] Panagiotis Papadimitratos, and Zygmunt J. Haas. Secure Data Communication in. Mobile Ad Hoc
Networks. IEEE Journal on Selected Areas In Communications, Vol. 24,No. 2, 2006 PP. 343,356.
[25] Fatiha Djemili Tolba, Damien Magoni, Pascal Lorenz, "A Stable Clustering Algorithm for Highly
Mobile Ad Hoc Networks," icsnc, pp.11, Second International Conference on Systems and Networks
Communications (ICSNC 2007), 2007
[26] A. Ephremides, J. E. Wieselthier and D. J. Baker, “A design concept for reliable mobile radio
networks with frequency hopping signaling,” Proc. IEEE, vol. 75, no. 1, Jan. 1987, pp. 56-73.
[27] A. Bhatnagar and T. G. Robertazzi, “Layer Net: a new self-organizing network protocols,” Proc. IEEE
MILCOM ’90, pp. 845-849.
[28] M. Gerla and T. C. Tsai, “Multicluster, mobile, multimedia radio network,” ACM-Baltzer J. Wireless
Networks, vol. 1, no. 3, 1995, pp. 255-65.
[29] A. Alwan, R. Bagrodia, N. Bambos et al.,“Adaptive mobile multimedia networks,” IEEE Personal
Commun., Apr. 1996, pp. 34-51.
[30] A. B. McDonald and T. F. Znati, “A mobilitybased framework for adaptive clustering in wireless ad
hoc networks,” IEEE J. Select. Areas Commun., vol. 17, no. 8, Aug. 1999, pp. 1466-1487.
[31] C. R. Lin and M. Gerla, “Adaptive clustering for mobile wireless networks,” IEEE J. Select. Areas
Commun., vol.15, no. 7, Sep. 1997, pp. 1265-1275.
[32] W. Chen, N. Jain and S. Singh, “ANMP: ad hoc network management protocol,” IEEE J. Select. Areas
Commun., vol. 17, no. 8, Aug. 1999, pp. 1506-1531.
[33] C. R. Lin and M. Geria, “Real-time support in multihop wireless network,” ACM-Baltzer J. Wireless
Networks, vol. 5, no. 2, 1999, pp. 125-135.
[34] S. Chen and K. Nahrstedt, “Distributed quality-of-service routing in ad hoc networks,” IEEE JSAC,
vol. 17, no. 8, Aug. 1999, pp. 1488-1505.
[35] A. Iwata, C.-C. Chiang, G. Pei, M. Gerla and T.-W. Chen, “Scalable routing strategies for ad hoc
wireless networks,” IEEE J. Select. Areas Commun., vol. 17, no. 8, Aug. 1999, pp. 1369-1379.](https://image.slidesharecdn.com/1210ijasuc08-201123053110/85/Optimizing-On-Demand-Weight-Based-Clustering-Using-Trust-Model-for-Mobile-Ad-Hoc-Networks-11-320.jpg)