OWASP AppSec EU 2016 - Security Project Management - How to be Agile in Security Testing Projects
- 1. Security Project Management How to be Agile in Security Testing Projects
- 2. whoami # Simone Onofri • Security Business Consultant at Hewlett Packard Enterprise • Director at DSDM Consortium • Volunteer: OWASP (Author TG v4), CoderDojo… • Certs: PRINCE2®, Agile Project Management®, ITIL, Certified ScrumMaster®, ISO 27001… Disclaimer: The opinions expressed in this presentation and on the following slides are solely those of the presenter. Any reference to events or persons is purely coincidental 2
- 3. About us here You «offer» Penetration Testing Services (Provider/Supplier) 3
- 4. About us here You «receive» Penetration Testing services? 4
- 5. About us here Something else? 5
- 6. Agenda • What is Agile in Security Project Management • The process and how to be Agile • Embed Security in Agile Software Development Lifecycle • Q&A 6
- 8. What is Agile “Agile” is an umbrella term for several iterative and incremental methodologies. Is a mindset and a style of working where requirements and solutions evolve through collaboration. Agile promotes adaptive planning, evolutionary development and delivery, a timeboxed, iterative approach and encourages rapid and flexible response to change. 8
- 9. Quote from Sun Tzu “Order and disorder depends on organization” 9
- 10. What is Project Management The planning (adaptively), delegating (at the lower level as possible), monitoring-control (without micro- manage) of all aspects of the project, and the motivation of those involved, to achieve the project objectives within the expected performance targets (e.g. time, cost, quality, scope, benefits and risks), delivering proper business product (what?) (Inspired from PRINCE2® definition)
- 11. Question time • Question: which is the typical business product of a Web Application Penetration Test? • Scenario: Security Assessment is the process of determining how effectively an “entity” (e.g. Web Application) meets specific security objectives. • Hint: what the final customer will have at the end of the activities? (Security Assessment definition inspired by NIST SP800-115)
- 12. Which is the typical business product of a Web Application Penetration Test? «Document the Test Results To conclude the testing process, it is important to produce a formal record of what testing actions were taken, by whom, when they were performed, and details of the test findings. It is wise to agree on an acceptable format for the report which is useful to all concerned parties, which may include developers, project management, business owners, IT department, audit, and compliance.» OWASP Testing Guide v4 - Introduction
- 13. Why Agile in Security Testing? 13 Enviormental factors: • Nowaday Software Developmnet is already Agile. • Work is often on a fixed deadline, fixed budget and we still need to deliver results without compromising quality. Specific Testing factors: • Security Testing is Agile «by definition». • We canot have info «by design» of testing project (e.g. Black-Box). • Often we will explore from the first technical stage (OTG-INFO-001/010).
- 14. How be Agile in Security Testing • Transparency and communication between customer and supplier • Use Agile techniques to solve common issues. – Planning Poker for collaborative planning – Timeboxing for managing time – MoSCoW for managing priorities • Integrate Security in Agile Development 14
- 15. AN AGILE SECURITY TESTING PROJECT 15
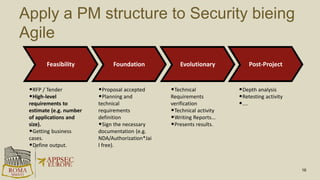
- 16. Apply a PM structure to Security bieing Agile 16 Feasibility Foundation Evolutionary Post-Project •RFP / Tender •High-level requirements to estimate (e.g. number of applications and size). •Getting business cases. •Define output. •Proposal accepted •Planning and technical requirements definition •Sign the necessary documentation (e.g. NDA/Authorization*Jai l free). •Technical Requirements verification •Technical activity •Writing Reports... •Presents results. •Depth analysis •Retesting activity •….
- 17. Top tips - Feasibility • In the feasibility phase the issue is to known the Business Case of the Customer: Why needs a PT? Often there are: – Compliance: e.g. laws and regulamentations (e.g. ISO 27001, Bank laws, PCI-DSS). – Risk Management to protect the enterprise (e.g. known vulnerabilities first to the attackers can exploit them). • Define what is the business product (the report), and the structure, of the final output of the project. 17
- 18. Top tips - Reporting • Is often suggested that the report will have different levels for different audience. – Executive Summary – Methodology and Tools – Technical Summary – Technical Details (exploits, TOP 10 mapping, CVSS v2…) • Specific needs? Be Agile! 18
- 19. Question time • Scenario: You are asked to test a Web Application, using OWASP Testing Guide. The application should be 20-40 dynamic pages with 2 different profiles. • Questions: who have to do the estimate? Other requirements to ask? 19
- 20. Top tips – Estimates! • Ask for a lot of information as possible: technology used, • Who? Technical guys/girls!!! • Active/Idle time? People are active often about 80% • Report warning the writing of the report can take about half the time of technical activies • Remote/on-site Travel time? • Specific timeframe? As a risk reduction and possibility to run automatic tools H24. • Project Management Time/Meetings/Writing? 20
- 21. Agile is your friend «We have a BrightRay™ Portal with 2 custom portlets and one for payment of membership via SecurePaymentGatewy™ portlet» The Team Lead said to testers. Think about the estimate and pick a card from your deck, wait to show to not influence others. 21
- 22. Planning Poker – first hand 22 13 13 13 5 Tester #1 Tester #2 Tester #3 Tester #4
- 23. Agile is your friend Team Lead sees that one tester is not aligned to the others, he/she can has important info to share with others, Tester #3 «I tested BrightRay™ few weeks ago and already automated the procedure for IG (portlets ids enumeration) and have a set of evil portlets for exploitation and post-exploitation» Tester #1 said «this is a good news. From my side I lost a lot of time with SPM portlet because of sophisticated defenses in place. 23
- 24. Planning Poker – second hand 24 8 13 5 5 Tester #1 Tester #2 Tester #3 Tester #4
- 25. Foundations – Top tips • Prepare a document with Scope, Rules of Engagements, Limitations, Communication Management Strategy (remember Transparency). • Prioritize activities in particular if we are timeboxed (we have an pre-defined and fixed amount of time e.g. to get a fixed price), in order to get suitable and useful results. Better a workshop with Supplier/Customer 25
- 26. Project Variables 26 Quality Time Functiona lities Quality Cost Time Waterfall approach Agile approach Cost Can vary Fixed Funcional ities
- 27. What to prioritize? • We have: • Vulnerabilities • Functionalities / Components • Specific «Evil» Use Cases • And Combine in a Matrix • Y axis – Functionalities • X axis - OWASP TOP 10 • Think also about: • When and how to go deep? • When to do manual and automatic activity? • False Positive Management Take care of vulnerabilities who have a wide application impact. 27
- 28. How to prioritize MoSCoW 28 Level Importance Effect if not met Effort Must Vital Project will fail. 60% Should Imporant Not wiil not fail, but challanged 20% Could Desirable Contingency 20% Won’t Out of scope May be a next PT --
- 29. Wasp in MoSCoW Injection Auth/SM XSS IDOR Security Misconfig. Payment Functionality Must Must (auto) Must (AutoScan™), Should (man) Must (man) Must (AutoScan™) Registration Must (AutoScan™), Could (man) Could Must (AutoScan™), Should (man) Could Must (AutoScan™) Authentication Must (AutoScan™), Should (man) Control itself Must (AutoScan™), Should (man) Could Must (AutoScan™) Private Content portlet Must (AutoScan™), Should (man) Must (man) Must Must (man) Must (AutoScan™) 29 Priorities Exploitation: No False Positive Management: High (Must), Medium (Should)
- 30. Timeboxing – top tips 30 • Kick-off: define objective • Investigation: do initial test and find quick-wins • Refinenement: the big testing work • Consolidation: stop starting, start finishing • Close-out: met with customer about the job done Kick-Off Close-Out Investigation (effort 10-20%) Consolidation (effort 10-20%) Refinement (effort 60-80%)
- 32. Embedding Security in Agile SSDLC In some cases, the customer has already an Agile process for SDLC. How Agile can be secure? • Security Testing is still needed for final testing at least (even if my team is competent, it is goof to ask for a Technical Advisor • Implement a Definition of Done / Acceptance Criteria for Security • Implement Evil User Stories • Pair Programming with Developers and Security Experts Image from Wikipedia, Lisamarie Babik
- 33. Be Agile, and Lean… how to manage the Vulnerabilities All todos are blocked (red is present on the Kanban). Now is the time to ask to the Penetration Tester team to Retest.
- 34. THANK YOU 34 Simone Onofri [email protected] https://onofri.org/ Trust the QR Code… (linkedin, will publish slides)