P2P Resource Discovery for the Browser
- 2. HI, I’M DAVID ://daviddias.me ://blog.daviddias.me ://github.com/diasdavid ://twitter.com/daviddias
- 7. RESOURCE DISCOVERY FOR THE WEB PLATFORM ON TOP OF A P2P OVERLAY NETWORK USING WEBRTC AS THE LAYER OF TRANSPORT
- 9. URL
- 21. P2P networks are only as useful as their Resource Discovery capabilities remain efficient when they scale up
- 22. P2P Overlay Networks primary focus is not to find a peer, it is to find a resource. Peers are ephemeral, resources should be permanent and discoverable.
- 23. GNUTELA 0.4
- 25. • march 2000, Justin Frankel and Tom Pepper • topology is completely random • routing and search using flooding with TTL and hop counter • really slow • lot’s of signalling traffic
- 31. GNUTELA 0.6
- 33. UNSTRUCTURED P2P NETWORKS Without an implicit way to organize content
- 35. CHORD
- 36. • DHT • Highly scalable • Each node only knows of m number of other nodes • Each node has a unique identifier • Each node is responsible for a segment of the data • Ids are 160 bits (SHA-1 for Uniform Distribution) • CHORD is awesome
- 39. 0 1 2 3 4 5 6 7 • 3 bit namespace • Id = hash(IP)
- 40. 0 1 2 3 4 5 6 7 • each node is responsible for a segment
- 41. 0 1 2 3 4 5 6 7 • minimum requirement - each node has to know their successor
- 42. 0 1 2 3 4 5 6 7 • each node is going to have it’s finger table
- 43. start interval sucessor start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = start(k) = start(k+1) sucessor - first node after start(k) n - ID of the peer m - number of bits used k - row number
- 44. 0 1 2 3 4 5 6 7 start interval sucessor start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k)
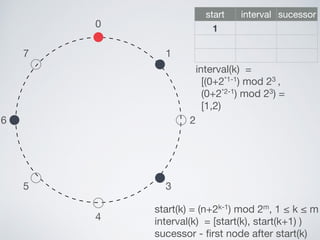
- 45. 0 1 2 3 4 5 6 7 start interval sucessor 1 start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k) interval(k) = [(0+2*1-1) mod 23 , (0+2*2-1) mod 23) = [1,2)
- 46. 0 1 2 3 4 5 6 7 start interval sucessor 1 [1,2) 1 start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k) interval(k) = [(0+2*1-1) mod 23 , (0+2*2-1) mod 23) =
- 47. 0 1 2 3 4 5 6 7 start interval sucessor 1 [1,2) 1 2 start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k) interval(k) = [(0+2*2-1) mod 23 , (0+2*3-1) mod 23)
- 48. 0 1 2 3 4 5 6 7 start interval sucessor 1 [1,2) 1 2 [2,4) 3 start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k) interval(k) = [(0+2*2-1) mod 23 , (0+2*3-1) mod 23)
- 49. 0 1 2 3 4 5 6 7 start interval sucessor 1 [1,2) 1 2 [2,4) 3 4 start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k) interval(k) = [(0+2*3-1) mod 23 , (0+2*4-1) mod 23)
- 50. 0 1 2 3 4 5 6 7 start interval sucessor 1 [1,2) 1 2 [2,4) 3 4 [4,0) 6 start(k) = (n+2k-1) mod 2m, 1 ≤ k ≤ m interval(k) = [start(k), start(k+1) ) sucessor - first node after start(k)
- 52. WEBRTC-EXPLORER
- 53. • Chord inspired P2P overlay network designed for the Web Platform • Uses CHORD routing scheme • Uses WebRTC for transport • WebSockets for Signalling • Peers (browsers) route messages amongst them • 48 bits Ids • Brings a full DHT to the browser WEBRTC-EXPLORER
- 55. HOW DOES IT WORK
- 56. var Explorer = require(‘webrtc-explorer’); var config = { signalingURL: '<url>' }; var peer = new Explorer(config); peer.events.on(‘registered', function(data) { console.log('Id:', data.peerId); }); peer.events.on('ready', function() { console.log('ready to send messages'); }); peer.events.on('message', function(envelope) { console.log(envelope); }); peer.register(); //peer.send(‘<dst_id>’, <data_to_send>); s-register c-registered { id: “<this_peer_id>” }
- 59. DEMO
- 60. PAPERS• Afify, Y. (2008). Access Control in a Peer-to-peer Social Network. Ph. D. thesis, ECOLE POLYTECHNIQUE FEDERALE DE LAUSANNE. • Anderson, B. D. P., J. Cobb, E. Korpela, & M. Lebofsky (2002). SETI@Home, an Ex- perimentinPublic-ResourceComputing. 45(11). • Anderson, D. (2004). Boinc: A system for public-resource computing and storage. In • Grid Computing, 2004. Proceedings. • Armbrust, M., I. Stoica, M. Zaharia, A. Fox, R. Griffith, A. D. Joseph, R. Katz, A. Kon- winski, G. Lee, D. Patterson, & A. Rabkin (2010, April). A view of cloud computing. Communications of the ACM 53(4), 50. • Bakhtiari, S. & J. Pieprzyk (1995). Cryptographic hash functions: A survey.” Centre for Computer Security Research, Department of Computer Science. pp. 1–26. • Barabási,a.L.,V.W.Freeh,H.Jeong,&J.B.Brockman(2001,August). Parasitic computing. Nature 412(6850), 894–7. • Barraca, J. a. P., A. Matos, & R. L. Aguiar (2011, April). User Centric Community Clouds. Wireless Personal Communications 58(1), 31–48. • Bharambe, A. R., M. Agrawal, & S. Seshan. Mercury : Supporting Scalable Multi- Attribute Range Queries. pp. 353–366. • Byers, J., J. Considine, & M. Mitzenmacher (2003). Simple Load Balancing for Dis- tributed Hash Tables. In M. Frans Kaashoek ; Ion Stoica (Ed.), Peer-to-Peer Systems II, pp. 80–88. Springer Berlin Heidelberg. • Clarke, I., O. Sandberg, B. Wiley, & T. Hong (2001). Freenet: A distributed anony- mous information storage and retrieval system. In H. Federrath (Ed.), Designing Privacy, pp. 46–66. Springer Berlin Heidelberg.
- 61. PAPERS• Cohen, B. (2009). The BitTorrent Protocol Specification. • Costa, F., J. Silva, L. Veiga, & P. Ferreira (2012). Large-scale volunteer computing over • the Internet. Internet Services and Applications, 1–18. D. Eastlake, 3rd Motorola; P. Jones Systems, C. (2001). RFC 3174 US Secure Hash • Decandia, G., D. Hastorun, M. Jampani, G. Kakulapati, A. Lakshman, A. Pilchin, S. Sivasubramanian, P. Vosshall, & W. Vogels (2007). Dynamo : Amazon’s Highly Avail- able Key-value Store. pp. 205–220. • Definition, P. (2003). The Gnutella Protocol Specification v0 . 4. Solutions, 1–8. Desmedt, Y. & Y. Frankel (1990). Threshold cryptosystems. Advances in Cryptol- • ogy—CRYPTO’89 . . . . Douceur, J. R. (2002). The Sybil Attack. In P. D. [email protected] & A. R. • [email protected] (Eds.), Peer-to-Peer Systems, pp. 251–260. Springer Berlin Heidelberg. Duda, J. & W. Dłubacz (2013). Distributed evolutionary computing system based on • web browsers with javascript. Applied Parallel and Scientific Computing. • Ecma, S. (2009). ECMA-262 ECMAScript Language Specification. • Filipe, P. & G. Oliveira (2011). Gridlet Economics : Resource Management Models and Policies for Cycle-Sharing Systems. • Golle, P., K. Leyton-brown, I. Mironov, & M. Lillibridge (2001). Incentives for Sharing in Peer-to-Peer Networks. pp. 75–87. • Handley, M. & R. Karp (2001). A Scalable Content-Addressable Network. In SIG- COMM ’01 Proceedings of the 2001 conference on Applications, technologies, architectures, and protocols for computer communications, Volume 21, pp. 161–172. • Karger, D., T. Leightonl, D. Lewinl, E. Lehman, & R. Panigrahy (1997). Consistent Hashing and Random Trees : Distributed Caching Protocols for Relieving Hot Spots on the World Wide Web *. In STOC ’97 Proceedings of the twenty-ninth annual ACM symposium on Theory of computing, pp. 654–663.
- 62. PAPERS• Karger, D. R. & M. Ruhl (2004). Simple efficient load balancing algorithms for peer-to- peer systems. Proceedings of the sixteenth annual ACM symposium on Parallelism in algorithms and architectures - SPAA ’04, 36. • Koloniari, G. & E. Pitoura (2005). Peer-to-Peer Management of XML Data : Issues andResearchChallenges. 34(2),6–17. • Korpela, E. & D. Werthimer (2001). SETI@Home, Massively Distributed Computing for SETI. Computing in Science & Engineering, 78–83. • Larson, S., C. Snow, & M. Shirts (2002). Folding@ Home and Genome@ Home: Using distributed computing to tackle previously intractable problems in computational biol- ogy. • Marti, S. & H. Garcia-molina (2006, March). Taxonomy of Trust : Categorizing P2P Reputation Systems. Computer Networks (April 2005), 472–484. • Maymounkov, P. & D. Mazie`res. Kademlia: A Peer-to-peer Information System Based on the XOR Metric. • Merelo,J.-j.,A.Mora-garćıa,J.Lupión,&F.Tricas(2007).Browser-basedDistributed Evolutionary Computation : Performance and Scaling Behavior Categories and Subject Descriptors. pp. 2851–2858. • Milojicic, D. S., V. Kalogeraki, R. Lukose, K. Nagaraja, J. Pruyne, B. Richard, S. Rollins, Z. Xu, & J. I. M. Pruyne (2003). Peer-to- Peer Computing. Technical report. • Navarro, L. (2012). Experimental research on community networks. Technical report. • Nurmi, D., R. Wolski, C. Grzegorczyk, G. Obertelli, S. Soman, L. Youseff, & D. Zagorodnov (2009). The Eucalyptus Open-Source Cloud-Computing System. 2009 9th IEEE/ACM International Symposium on Cluster Computing and the Grid, 124–131. • Paulson, L. (2005, October). Building rich web applications with Ajax. Com- puter 38(10), 14–17. • Preneel, B. (1999). The State of Cryptographic Hash Functions. pp. 158–182. • Ranjan, R., A. Harwood, & R. Buyya (2006). A study on peer-to-peer based discovery of grid resource information. Australia, Technical Report GRIDS, 1–36.
- 63. PAPERS• Rao, A., K. Lakshminarayanan, S. Surana, & R. Karp (2003). Load Balancing in Structured P2PSystems. 0225660,68–79. • Rieche, S., L. Petrak, & K. Wehrle. A thermal-dissipation-based approach for balanc- ing data load in distributed hash tables. 29th Annual IEEE International Conference on Local Computer Networks, 15–23. • Ripeanu, M. (2002). Peer-to-peer architecture case study: Gnutella network. Proceed- ings First International Conference on Peer- to-Peer Computing, 99–100. • Rodrigues, R. & P. Ferreira. GiGi : An Ocean of Gridlets on a “ Grid-for-the-Masses ”. • Rowstron, A. & P. Druschel (2001a). PAST A large-scale , persistent peer-to-peer storage utility. Proceedings of the eighteenth ACM symposium on Operating systems principles - SOSP ’01, 75–80. • Rowstron, A. & P. Druschel (2001b). Pastry : Scalable , Decentralized Object Location , and Routing for Large-Scale Peer-to-Peer Systems. pp. 329–350. • Ruellan, H. & R. Peon (2013). HPACK-Header Compression for HTTP/2.0. draft-ietf- httpbis-header-compression-04 (work in progress) (c), 1–57. • Silva, J. a. N., L. Veiga, & P. Ferreira (2008, October). nuBOINC: BOINC Extensions for Community Cycle Sharing. In 2008 Second IEEE International Conference on Self-Adaptive and Self-Organizing Systems Workshops, pp. 248–253. IEEE. • Silva, J. a. N., L. Veiga, & P. Ferreira (2011, August). A2HA—automatic and adap- tive host allocation in utility computing for bag- of-tasks. Journal of Internet Services and Applications 2(2), 171–185. • Stoica,I.,R.Morris,D.Karger,M.F.Kaashoek,H.B.Ý,&H.Balakrishnan(2001). Chord : A Scalable Peer-to-peer Lookup Service for Internet. pp. 149–160. • T. Klingberg, R. M. (2002). RFC - Gnutella 0.6 Protocol Specification. • Thomson, M. & A. Melnikov (2013). Hypertext Transfer Protocol version 2.0 draft- ietf-httpbis-http2-09.
- 64. PAPERS • Tilkov, S. & S. V. Verivue (2010). Node.js : Using JavaScript to Build High- Performance Network Programs. • Vishnumurthy, V., S. Chandrakumar, & G. Emin (2003). Karma: A secure economic framework for peer-to-peer resource sharing. • Vogt, C., M. Werner, & T. Schmidt (2013). Leveraging WebRTC for P2P Content Distribution in Web Browsers. 21st IEEE Internanicoal Conference. • Wallach, D. S. (2003). A Survey of Peer-to-Peer Security Issues. In M. O. Mitsu@abelard.flet.keio.ac.jp (Ed.), Software Security — Theories and Systems, pp. 42–57. • Zakai, A. (2011). Emscripten: an llvm-to-javascript compiler. In Proceedings of the ACM international conference companion on Object oriented programming systems languages and applications companion. ACM. • Zhao, B. Y., J. Kubiatowicz, & A. D. Joseph (2001). Tapestry : An Infrastructure for Fault-tolerant Wide-area Location and Routing. Technical Report April, University of California, Berkeley,.
- 65. THANK YOU! :D