ppt of computer netwokrs.cse engineering.part 5
- 2. Protocol Architecture- TCP/IP Two protocol architectures have served as the basis for the development of interoperable communications standards: TCP/IP protocol suite and Open Systems Interconnection (OSI) reference model. TCP/IP is now the universal interoperable protocol architecture.
- 3. TCP/IP The main design goal of TCP/IP was to build an interconnection of networks, referred to as an interconnected network, or internet. A set of protocols allowing communication across diverse networks TCP = Transmission Control Protocol IP = Internet Protocol
- 4. Need For Protocol Architecture Data exchange can involve complex procedures; -file transfer as an example Better if task broken into subtasks Implemented separately in layers in stack each layer provides functions needed to perform communications for layers above using functions provided by layers below Peer layers communicate using a set of rules or conventions known as a protocol.
- 5. TCP/IP Protocol Architecture Developed by US Defense Advanced Research Project Agency (DARPA) for ARPANET packet switched network Used by the global Internet Protocol suite comprises a large collection of standardized protocols
- 7. TCP/IP Layers No official model but a working one. Application layer Host-to-host, or transport layer Internet layer Network access layer Physical layer
- 8. TCP/IP layers Communications can be said to involve three agents: applications (eg. file transfer), computers (eg. PCs & servers), and networks. Data transfer involves first getting the data to the computer in which the application resides and then getting the data to the intended application within the computer.
- 9. Physical Layer Concerned with physical interface between computer and network concerned with issues such as: characteristics of transmission medium signal levels data rates other related matters
- 10. Network Access Layer Exchange of data between an end system and attached network concerned with issues such as : destination address provision invoking specific services like priority access to & routing data across a network link between two attached systems
- 11. Internet Layer (IP) Routing functions across multiple inter networks for systems attached to different networks. Routing using Internet protocol (IP) Implemented in end systems and in routers A router is a processor that connects two networks and relays data between them.
- 12. Transport Layer Common layer shared by all applications Provides reliable delivery of data-in same order as sent Referred to as Host-to-host, or transport layer provides an end-to-end connection between two devices during communication by performing sequencing, acknowledgments, checksums, and flow control. Commonly uses TCP to provide this functionality.
- 13. TCP(Transmission Control protocol) For most applications running as part of the TCP/IP protocol architecture, the transport layer protocol is TCP TCP provides a reliable connection for the transfer of data between applications. A connection is simply a temporary logical association between two entities in different systems.
- 14. Application Layer Provide support for user applications. Need a separate module for each type of application. Ex:File transfer, e-mail
- 15. Addressing Requirements Two levels of addressing required Each host on a subnet needs a unique global network address IP address (Network ID+Host ID)-192.168.16.21 Each application on a (multi-tasking) host needs a unique address within the host. known as a port (eg: port 80 for http, 25 for mail(SMTP)) Socket->IP address + Port No->192.168.16.21:80
- 16. Port number Network ports are provided by the TCP or UDP protocols at the Transport layer. Ports allow a single host with a single IP address to run network services. Each port number identifies a distinct service, and each host can have 65535 ports per IP address. Port use is regulated by the Internet Corporation for Assigning Names and Numbers (ICANN). By ICANN there are three categories for ports: • From 0 to 1023 – well known ports assigned to common protocols and services • From 1024 to 49151 – registered ports assigned by ICANN to a specific service • From 49152 to 65 535 – dynamic (private, high) ports range from 49,152 to 65,535. Can be used by any service on an ad hoc basis. Ports are assigned when a session is established, and released when the session ends.
- 17. Well known ports
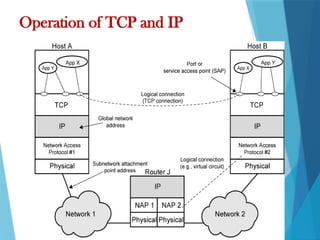
- 18. Operation of TCP and IP
- 19. Host A, wishes to send a message to another process on host B. TCP may break this block into smaller pieces to make it more manageable. To each of these pieces, TCP appends control information known as the TCP header, forming a TCP segment. TCP hands each segment over to IP, with instructions to transmit it to B. These segments must be transmitted across one or more subnetworks and relayed through one or more intermediate routers. Each IP datagram is presented to the network access layer for transmission across the first subnetwork in its journey to the destination. The packet is transmitted across the subnetwork to router J.
- 21. TCP(Transport Control protocol) TCP appends control information known as the TCP header, forming a TCP segment. Destination port: When the TCP entity at B receives the segment, it must know to whom the data are to be delivered. Sequence number: TCP numbers the segments that it sends to a particular destination port sequentially, so that if they arrive out of order, the TCP entity at B can reorder them. Checksum: TCP performs the same calculation and compares the result with the incoming code.
- 22. Internet layer- IP appends a header of control information –IP datagram, eg: destination host address(host B) Network access layer create packets. Packet transmitted to router J. Packet header contains: Destination subnetwork address. Facilities requests-priority
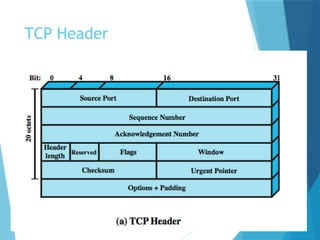
- 23. TCP Header
- 24. Header length- It indicates the length of the TCP header so that we know where the actual data begins. Acknowledgment number: this 32 bit field is used by the receiver to request the next TCP segment. This value will be the sequence number incremented by 1. Window: the 16 bit window field specifies how many bytes the receiver is willing to receive. It is used so the receiver can tell the sender that it would like to receive more data than what it is currently receiving. Flags: there are 9 bits for flags, we also call them control bits. We use them to establish connections, send data and terminate connections: ACK,SYN,URG etc URG: urgent pointer. When this bit is set, the data should be treated as priority over other data. FIN: this finish bit is used to end the TCP connection. TCP is full duplex so both parties will have to use the FIN bit to end the connection. This is the normal method how we end a connection. Urgent pointer: these 16 bits are used when the URG bit has been set, the urgent pointer is used to indicate where the urgent data ends.
- 25. Process of transmitting a packet with TCP/IP Step 1: Establish connection When two computers want to send data to each other over TCP, they first need to establish a connection using a three-way handshake. The first computer sends a packet with the SYN bit set to 111 (SYN = "synchronize?"). The second computer sends back a packet with the ACK bit set to 111 (ACK = "acknowledge!") plus the SYN bit set to 111. The first computer replies back with an ACK. The SYN and ACK bits are both part of the TCP header:
- 26. In fact, the three packets involved in the three-way handshake do not typically include any data. Once the computers are done with the handshake, they're ready to receive packets containing actual data.
- 27. Step 2: Send packets of data When a packet of data is sent over TCP, the recipient must always acknowledge what they received. The first computer sends a packet with data and a sequence number. The second computer acknowledges it by setting the ACK bit and increasing the acknowledgement number by the length of the received data. The sequence and acknowledgement numbers are part of the TCP header: Those two numbers help the computers to keep track of which data was successfully received, which data was lost, and which data was
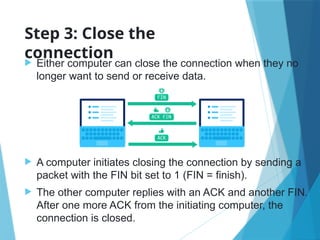
- 28. Step 3: Close the connection Either computer can close the connection when they no longer want to send or receive data. A computer initiates closing the connection by sending a packet with the FIN bit set to 1 (FIN = finish). The other computer replies with an ACK and another FIN. After one more ACK from the initiating computer, the connection is closed.
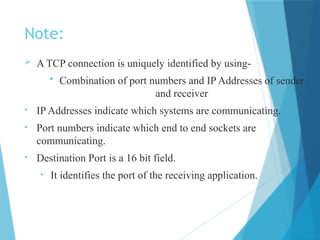
- 29. Note: A TCP connection is uniquely identified by using- Combination of port numbers and IP Addresses of sender and receiver • IP Addresses indicate which systems are communicating. • Port numbers indicate which end to end sockets are communicating. • Destination Port is a 16 bit field. • It identifies the port of the receiving application.
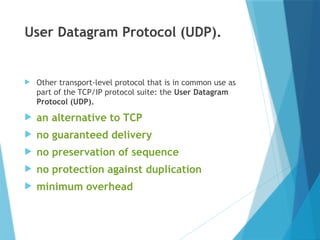
- 30. User Datagram Protocol (UDP). Other transport-level protocol that is in common use as part of the TCP/IP protocol suite: the User Datagram Protocol (UDP). an alternative to TCP no guaranteed delivery no preservation of sequence no protection against duplication minimum overhead
- 31. UDP Header
- 33. TCP Reliable, slow, heavy weight(because of acknowledgment header) Connection Oriented Overhead-retxn of packets and Ackn packet size 20 Bytes UDP Unreliable, fast,light weight, less compuation. Small packet size(8 Bytes), connectionless
Editor's Notes
- #4: When computers, terminals, and/or other data processing devices exchange data, the procedures involved can be quite complex. eg. file transfer. There must be a data path between the two computers. But also need: Source to activate communications Path or inform network of destination Source must check destination is prepared to receive File transfer application on source must check destination file management system will accept and store file for its user May need file format translation Instead of implementing the complex logic for this as a single module, the task is broken up into subtasks, implemented separately. In a protocol architecture, the modules are arranged in a vertical stack, each layer in the stack performs a related subset of the functions. It relies on the next lower layer to perform more primitive functions. It provides services to the next higher layer. The peer layers communicate using a set of rules or conventions known as a protocol.
- #5: The TCP/IP protocol architecture is a result of protocol research and development conducted on the experimental packet-switched network, ARPANET, funded by the Defense Advanced Research Projects Agency (DARPA), and is generally referred to as the TCP/IP protocol suite. This protocol suite consists of a large collection of protocols that have been issued as Internet standards by the Internet Activities Board (IAB).
- #7: TCP/IP doesn’t have an “official” layer model (& it predates the OSI Reference Model we’ll introduce later), but it does have a “working” layer model, as shown.
- #9: The physical layer covers the physical interface between a data transmission device (e.g., workstation, computer) and a transmission medium or network. This layer is concerned with specifying the characteristics of the transmission medium, the nature of the signals, the data rate, and related matters.
- #10: The network access layer is concerned with the exchange of data between an end system (server, workstation, etc.) and the network to which it is attached. The sending computer must provide the network with the address of the destination computer, so that the network may route the data to the appropriate destination. The sending computer may wish to invoke certain services, such as priority, that might be provided by the network. The specific software used at this layer depends on the type of network to be used; different standards have been developed for circuit switching, packet switching (e.g., frame relay), LANs (e.g., Ethernet), and others. Thus it makes sense to separate those functions having to do with network access into a separate layer.
- #11: The internet layer provides procedures used to allow data to traverse multiple interconnected networks, to provide communications between devices are attached to different networks. The Internet Protocol (IP) is used at this layer to provide the routing function across multiple networks. This protocol is implemented not only in the end systems but also in routers. A router is a processor that connects two networks and whose primary function is to relay data from one network to the other on its route from the source to the destination end system.
- #12: The host-to-host layer, or transport layer, collects mechanisms in a common layer shared by all applications to provide reliable delivery of data. Regardless of the nature of the applications, there is usually a requirement that data be exchanged reliably, ensuring that all of the data arrives at the destination application and that the data arrives in the same order in which they were sent. These mechanisms for providing reliability are essentially independent of the nature of the applications. The Transmission Control Protocol (TCP) is the most commonly used protocol to provide this functionality.
- #14: Finally, the application layer contains the logic needed to support the various user applications. For each different type of application, such as file transfer, a separate module is needed that is peculiar to that application.
- #15: For successful communication, every entity in the overall system must have a unique address. Actually, two levels of addressing are needed. Each host on a subnetwork must have a unique global internet address; this allows the data to be delivered to the proper host. Each process with a host must have an address that is unique within the host; this allows the host-to-host protocol (TCP) to deliver data to the proper process. These latter addresses are known as ports.
- #18: Stallings DCC8e Figure 2.1 indicates how these protocols are configured for communications. To make clear that the total communications facility may consist of multiple networks, the constituent networks are usually referred to as subnetworks. Some sort of network access protocol, such as the Ethernet logic, is used to connect a computer to a subnetwork. This protocol enables the host to send data across the subnetwork to another host or, if the target host is on another subnetwork, to a router that will forward the data. IP is implemented in all of the end systems and the routers. It acts as a relay to move a block of data from one host, through one or more routers, to another host. TCP is implemented only in the end systems; it keeps track of the blocks of data to assure that all are delivered reliably to the appropriate application.
- #20: Consider a simple operation where a process on host A, wishes to send a message to another process on host B. The process at A hands the message down to TCP with instructions to send it to host B. TCP hands the message down to IP with instructions to send it to host B. Note that IP need not be told the identity of the destination port. Next, IP hands the message down to the network access layer (e.g., Ethernet logic) with instructions to send it to router J (the first hop on the way to B). To control this operation, control information as well as user data must be transmitted, as suggested in Stallings DCC8e Figure 2.2. The sending process generates a block of data and passes this to TCP. TCP may break this block into smaller pieces to make it more manageable. To each of these pieces, TCP appends control information known as the TCP header, forming a TCP segment. Next, TCP hands each segment over to IP, with instructions to transmit it to B. These segments must be transmitted across one or more subnetworks and relayed through one or more intermediate routers. This operation, too, requires the use of control information. Thus IP appends a header of control information to each segment to form an IP datagram. Finally, each IP datagram is presented to the network access layer for transmission across the first subnetwork in its journey to the destination. The network access layer appends its own header, creating a packet, or frame. The packet is transmitted across the subnetwork to router J.