Programming Windows Azure Programming The Microsoft Cloud 1st Edition Sriram Krishnan
- 1. Programming Windows Azure Programming The Microsoft Cloud 1st Edition Sriram Krishnan download https://ebookbell.com/product/programming-windows-azure- programming-the-microsoft-cloud-1st-edition-sriram- krishnan-2323900 Explore and download more ebooks at ebookbell.com
- 2. Here are some recommended products that we believe you will be interested in. You can click the link to download. Programming Windows Azure Sriram Krishnan Krishnan Sriram https://ebookbell.com/product/programming-windows-azure-sriram- krishnan-krishnan-sriram-11508642 Windows Azure Programming Patterns For Startups 1st Edition Riccardo Becker https://ebookbell.com/product/windows-azure-programming-patterns-for- startups-1st-edition-riccardo-becker-34855828 Programming Microsofts Clouds Windows Azure And Office 365 1st Edition Thomas Rizzo https://ebookbell.com/product/programming-microsofts-clouds-windows- azure-and-office-365-1st-edition-thomas-rizzo-4113120 Programming Windows Phone 7 Charles Petzold https://ebookbell.com/product/programming-windows-phone-7-charles- petzold-2364200
- 3. Programming Windows Consumer Preview 6 Edition 6 Auflage Charles Petzold https://ebookbell.com/product/programming-windows-consumer- preview-6-edition-6-auflage-charles-petzold-2614364 Programming Windows 8 Apps With Html Css And Javascript Kraig Brockschmidt https://ebookbell.com/product/programming-windows-8-apps-with-html- css-and-javascript-kraig-brockschmidt-2618960 Programming Windows Presentation Foundation 1st Edition Chris Sells https://ebookbell.com/product/programming-windows-presentation- foundation-1st-edition-chris-sells-34860144 Programming Windows Phone 7 Xna Framework Edn Charles Petzold https://ebookbell.com/product/programming-windows-phone-7-xna- framework-edn-charles-petzold-4106522 Programming Windows Workflow Foundation Practical Wf Techniques And Examples Using Xaml And C A C Developers Guide To The Features And Programming Interfaces Of Windows Workflow Foundation K Scott Allen https://ebookbell.com/product/programming-windows-workflow-foundation- practical-wf-techniques-and-examples-using-xaml-and-c-a-c-developers- guide-to-the-features-and-programming-interfaces-of-windows-workflow- foundation-k-scott-allen-4452944
- 7. Programming Windows Azure Sriram Krishnan Beijing • Cambridge • Farnham • Köln • Sebastopol • Taipei • Tokyo
- 8. Programming Windows Azure by Sriram Krishnan Copyright © 2010 Sriram Krishnan. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://my.safaribooksonline.com). For more information, contact our corporate/institutional sales department: 800-998-9938 or [email protected]. Editors: Mike Hendrickson and Laurel R.T. Ruma Production Editor: Loranah Dimant Copyeditor: Audrey Doyle Proofreader: Stacie Arellano Indexer: John Bickelhaupt Cover Designer: Karen Montgomery Interior Designer: David Futato Illustrator: Robert Romano Printing History: May 2010: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc., Programming Windows Azure, the image of a dhole, and related trade dress are trademarks of O’Reilly Media, Inc. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information con- tained herein. TM This book uses RepKover™, a durable and flexible lay-flat binding. ISBN: 978-0-596-80197-7 [M] 1273086110
- 9. This book is dedicated to my parents. None of this would have been possible without them.
- 11. Table of Contents Preface . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xiii 1. Cloud Computing . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 1 Understanding Cloud Computing 1 History of Cloud Computing 2 Understanding the Characteristics of Cloud Computing 7 Understanding Cloud Services 8 The Windows Azure Platform 9 Azure AppFabric 9 SQL Azure 10 Windows Azure 10 Understanding the Origins of Windows Azure 10 Understanding Windows Azure Features 12 Virtualization 13 The Fabric Controller 15 Storage 16 When Not to Use the Cloud 18 Service Availability 18 Custom Infrastructure Requirements 19 Security, Confidentiality, and Audits 19 Capacity Planning and Limits 20 Unpredictable Performance 20 Migration and Interoperability 21 Summary 21 2. Under the Hood . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 23 Inside the Cloud 23 The Data Centers 25 Security 26 Compliance 26 The Hypervisor 27 v
- 12. Hypervisor Architecture 28 Hypercalls and Enlightenments 30 Windows Azure Hypervisor Architecture 30 Windows Azure Hypervisor Features 33 The Fabric 34 The Fabric Controller 35 Coding and Modeling 37 Provisioning and Deployment 40 Management and Monitoring 41 Summary 42 3. Your First Cloud App . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 43 Signing Up for Windows Azure 43 The Windows Azure Tool Set 44 Getting and Installing the Tools 44 Satisfying the Prerequisites 44 Getting to Know the SDK and Tools 46 Understanding the Development Fabric 47 Development Storage 49 Developing Your First Cloud Application 50 Writing the Code 50 Packing the Code for the Dev Fabric 52 Running the Code in the Dev Fabric 54 Running the Code in the Cloud 55 Using the Visual Studio Tools 62 Summary 65 4. Service Model . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 67 Understanding Windows Azure Roles 67 Role Instances 69 Role Size 71 Service Definition and Configuration 72 Service Definition 73 Service Configuration 74 Introducing the Service Runtime API 75 Accessing Configuration Settings 78 Understanding Endpoints 78 Understanding Inter-Role Communication 80 Subscribing to Changes 83 Looking at Worker Roles in Depth 84 Creating Worker Roles 84 Understanding the Worker Role Life Cycle 85 Understanding Worker Role Patterns 86 vi | Table of Contents
- 13. Summary 87 5. Managing Your Service . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 89 Common Themes Across Windows Azure Services 89 Windows Azure Developer Portal 90 Service Management API 91 Operations 92 API Authentication 92 Creating an X.509 Certificate 93 Uploading the X.509 Certificate 95 Making API Requests 96 Using Csmanage 99 Dealing with Upgrades 102 In-Place Upgrade 102 VIP Swap 104 Summary 105 6. Native and Non-.NET Code . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 107 The Windows Azure Sandbox 107 Hypervisor and Standard User Privileges 107 Windows Azure Partial Trust 108 Full Trust and Native Code 109 Peeking Under the Hood with a Command Shell 109 Building the Command Shell Proxy 110 Enabling Native Code Execution 113 Running the Command Proxy 114 Running Non-.NET Languages 117 Understanding FastCGI and PHP 117 What Is FastCGI? 118 FastCGI on Windows Azure 119 PHP on Windows Azure 120 “Gotchas” with Running Native Code 125 Summary 126 7. Storage Fundamentals . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 127 Accepting the New Storage System 128 Windows Azure Storage Characteristics 129 Lots and Lots of Space 129 Distribution 129 Scalability 129 Replication 130 Consistency 130 RESTful HTTP APIs 131 Table of Contents | vii
- 14. Geodistribution 131 Pay for Play 131 Windows Azure Storage Services 131 Blob Storage 132 Queue Storage 132 Table Storage 132 SQL Azure 133 Getting Started with a Storage Account 133 Signing Up for a Storage Account 133 Picking a Geographic Location 135 Affinity Groups 136 Pricing 137 Working with the REST API 138 Understanding the RESTful API Resources 139 HTTP Requests and Responses 140 Building a Storage Client 142 Understanding Authentication and Request Signing 147 Using the Signing Algorithm 148 Creating and Uploading Stuff 151 Using the SDK and Development Storage 153 Installation and Prerequisites 153 Using Cloud Drive 154 Using the Development Storage 155 Summary 156 8. Blobs . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 157 Understanding the Blob Service 157 Using Blobs 158 Pricing 160 Data Model 160 Usage Considerations 162 Requests Could Fail 162 Changes Are Reflected Instantly 163 Compressed Content 164 Using the Blob Storage API 164 Using the Storage Client Library 165 Using Containers 167 Understanding Names and URIs 167 Creating a Container 168 Using an Access Policy 172 Listing Containers 174 Using Metadata 175 Deleting Containers 176 viii | Table of Contents
- 15. Using Blobs 176 Names and Paths 177 Creating and Deleting a Block Blob 178 Compressed Content 181 Reading Blobs 184 Conditional Reads 185 Listing, Filtering, and Searching for Blobs 187 Copying Blob 193 Understanding Block Blobs 193 Using Blocks 194 PUT Block 195 Block ID 195 Put BlockList 195 Understanding Page Blobs 196 Pages 197 Windows Azure XDrive 198 XDrive Internals 199 CDN Access and Custom Domain Names 199 Using Custom Domains 200 Summary 202 9. Queues . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 203 Understanding the Value of Queues 204 Decoupling Components 206 Scaling Out 207 Load Leveling 208 Windows Azure Queue Overview 208 Architecture and Data Model 208 The Life of a Message 209 Queue Usage Considerations 211 Understanding Queue Operations 212 Creating a Queue 213 Using Queue Metadata 214 Counting Queue Messages 216 Listing Queues 216 Deleting Queues 218 Understanding Message Operations 219 Enqueuing a Message 219 Understanding Message TTL 220 Peeking at a Message 220 Getting Messages 222 Deleting Messages 223 Deleting and Using PopReceipts 224 Table of Contents | ix
- 16. Summary 224 10. Tables . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 225 Windows Azure Table Overview 226 Core Concepts 226 Azure Tables Versus Traditional Databases 229 ADO.NET Data Services Primer 231 Exposing Data Services 232 Consuming Data Services 236 Table Operations 239 Creating Tables 239 Creating Entities 243 Querying Data 244 Using Partitioning 248 Understanding Pagination 255 Updating Entities 256 Deleting Tables 258 Deleting Entities 258 Summary 260 11. Common Storage Tasks . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 261 Exploring Full-Text Search 261 Understanding Full-Text Search 261 Indexing 262 Building an FTS Engine on Azure 267 Modeling Data 281 One-to-Many 281 Many-to-Many 284 Making Things Fast 286 Secondary Indexes 286 Entity Group Transactions 290 Utilizing Concurrent Updates 291 Summary 293 12. Building a Secure Backup System . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 295 Developing a Secure Backup System 296 Understanding Security 297 Protecting Data in Motion 298 Protecting Data at Rest 304 Understanding the Basics of Cryptography 305 Determining the Encryption Technique 307 Generating Keys 308 Compressing Backup Data 311 x | Table of Contents
- 17. Encrypting Data 313 Decrypting Data 317 Signing and Validating Data 317 Putting the Cryptography Together 319 Uploading Efficiently Using Blocks 321 Usage 324 Summary 325 13. SQL Azure . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 327 Creating and Using a SQL Azure Database 328 Creating a Database 328 Adding Firewall Rules 330 Using SQL Server Management Studio 331 Using ADO.NET 334 Differences Between SQL Azure and SQL Server 334 Resource Restrictions 334 Language/Feature Differences 335 Tips and Tricks 335 Summary 336 Index . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 337 Table of Contents | xi
- 19. Preface I hate the term the cloud. I really do. In a surprisingly short period of time, I’ve seen the term twisted out of shape and become a marketing buzzword and applied to every bit of technology one can conjure up. I have no doubt that in a few years, the term the cloud will be relegated to the same giant dustbin for bad technology branding that the likes of SOA and XML-based web services are now relegated to. Underneath all that marketing fluff, though, is the evolution of an interesting trend. Call it the cloud or Something-as-a-Service—it doesn’t matter. The idea that you can harness computing and storage horsepower as a service is powerful and is here to stay. As a builder of things, I love technology that frees up obstacles and lets me focus on what I want to do: create. The cloud does just that. Whether you’re a startup or a huge Fortune 500 company with private jets, the cloud lets you focus on building things instead of having to worry about procuring hardware or maintaining a storage area network (SAN) somewhere. Someday, we’ll all look back and laugh at the times when trying to run a website with reasonable traffic and storage needs meant waiting a few months for new hardware to show up. My involvement with this book started in early 2009. Windows Azure had just come on the market and other cloud offerings such as Amazon Web Services and Google’s App Engine had been out for some time. I saw a lot of people trying to grapple with what exactly the cloud was, and try to cut through all the marketing jargon and hype. That was no easy feat, let me assure you. I also saw people trying to wrap their heads around Windows Azure. What exactly is it? How do I write code for it? How do I get started? How do I do all those things I need to do to run my app? I hope to answer those questions in this book. One of the problems about putting anything in print is that it will inevitably be out- dated. I have no illusions that this book will be any different. As Windows Azure morphs over time in response to customer needs and industry trends, APIs will change. Features will be added and removed. To that end, this book tries to focus on the “why” more than the “how” or the “what.” I’m a great believer that once you know the “why,” the “how” and the “what” are easy to wrap your head around. Throughout this book, I’ve tried to explain why features act in a certain way or why certain features don’t exist. xiii
- 20. The actual API or class names might have changed by the time you read this book. Thanks to the power of web search, the right answer is never far away. This book is split into two halves. The first half digs into how Windows Azure works and how to host application code on it. The second half digs into the storage services offered by Windows Azure and how to store data in it. The two halves are quite inde- pendent and if you choose, you can read one and skip the other. The nice thing about Windows Azure is that it offers a buffet of services. Like any buffet, you can pick and choose what you want to consume. Want to host code on Windows Azure and host data on the same platform? That’s perfect. Want to use the Windows Azure blob service but want to host code in your own machines? That’s just as good, too. Throughout this book, you’ll find tiny anecdotes and stories strewn around. Several times, they are only tangentially relevant to the actual technology being discussed. I’m a big fan of books that try to be witty and conversational while being educational at the same time. I don’t know whether this book succeeds in that goal. But when you see the umpteenth Star Trek reference, you’ll at least understand why it is in there. How This Book Is Organized The chapters in this book are organized as follows: Chapter 1, Cloud Computing This chapter provides an overview of the cloud and the Windows Azure platform. It gives you a small peek at all the individual components as well as a taste of what coding on the platform looks like. Chapter 2, Under the Hood In this chapter, you dive under the hood of Windows Azure and see how the plat- form works on the inside. The inner workings of the Windows Azure hypervisor and fabric controller are looked at in detail. Chapter 3, Your First Cloud App It is time to get your hands dirty and write some code. This chapter gets you started with the Windows Azure SDK and tool set and walks you through developing and deploying your first application on Windows Azure. Chapter 4, Service Model In this chapter, you see how to build more advanced services. Core Windows Azure concepts such as service definition and configuration, web roles, worker roles, and inter-role communication are dealt with in detail. Chapter 5, Managing Your Service A key part of Windows Azure is managing your service after you have finished writing the code. In this chapter, you see the various service management options provided by Windows Azure. The service management API is looked at in detail. xiv | Preface
- 21. Chapter 6, Native and Non-.NET Code In this chapter, you learn how to run applications on Windows Azure that are not writtenin.NET.ThiscouldinvolvewritingapplicationsinC/C++orrunningother runtimes such as PHP or Ruby. Chapter 7, Storage Fundamentals Chapter 7 kicks off the storage part of the book. This chapter delves into the basics of the Windows Azure storage services and provides a short overview of the various services offered. The REST API behind the storage services is looked at in detail. Chapter 8, Blobs This chapter looks at the blobs service offered by Windows Azure. It delves into how to use the blobs API, different types of blobs, and how to use them in common scenarios. Chapter 9, Queues In this chapter, you learn about the queue service offered by Windows Azure. You see how to use queues in your services, and how to put messages in a queue and take them out. Chapter 10, Tables A key part of Windows Azure is the ability to store massive amounts of structured data and be able to query it efficiently. The table service offered by Windows Azure is a great option to do just that. This chapter delves into tables—how to efficiently partition, query, and update your data. Chapter 11, Common Storage Tasks In this chapter, you learn how to perform tasks that you are used to on other systems but may require some work on the cloud. This chapter looks at building full-text search on top of the Windows Azure table service and wraps up by looking at common modeling and performance issues. Chapter 12, Building a Secure Backup System This chapter happens to be one of my favorites in the book. It walks through the building of a secure backup system, built completely on open source tools and libraries. Along the way, it looks at various security, cryptography, and perform- ance issues while designing applications with the cloud. Chapter 13, SQL Azure This chapter delves into Microsoft’s RDBMS in the cloud: SQL Azure. You see how you can use your SQL Server skill set on Windows Azure and how to port your existing database code to SQL Azure. Preface | xv
- 22. Conventions Used in This Book The following typographical conventions are used in this book: Italic Indicates new terms, URLs, email addresses, filenames, and file extensions Constant width Used for program listings, as well as within paragraphs to refer to program elements such as variable or function names, databases, data types, environment variables, statements, and keywords Constant width bold Used to highlight significant portions of code, and to show commands or other text that should be typed literally by the user Constant width italic Shows text that should be replaced with user-supplied values or by values deter- mined by context This icon signifies a tip, suggestion, or general note. This icon signifies a warning or caution. Using Code Examples This book is here to help you get your job done. In general, you may use the code in this book in your programs and documentation. You do not need to contact us for permission unless you’re reproducing a significant portion of the code. For example, writing a program that uses several chunks of code from this book does not require permission. Selling or distributing a CD-ROM of examples from O’Reilly books does require permission. Answering a question by citing this book and quoting example code does not require permission. Incorporating a significant amount of example code from this book into your product’s documentation does require permission. We appreciate, but do not require, attribution. An attribution usually includes the title, author, publisher, and ISBN. For example: “Programming Windows Azure by Sriram Krishnan. Copyright 2010 Sriram Krishnan, 978-0-596-80197-7.” If you feel your use of code examples falls outside fair use or the permission given here, feel free to contact us at [email protected]. xvi | Preface
- 23. How to Contact Us Please address comments and questions concerning this book to the publisher: O’Reilly Media, Inc. 1005 Gravenstein Highway North Sebastopol, CA 95472 800-998-9938 (in the United States or Canada) 707-829-0515 (international or local) 707-829-0104 (fax) We have a web page for this book, where we list errata, examples, and any additional information. You can access this page at: http://oreilly.com/catalog/9780596801977 To comment or ask technical questions about this book, send email to: [email protected] For more information about our books, conferences, Resource Centers, and the O’Reilly Network, see our website at: http://oreilly.com Safari® Books Online Safari Books Online is an on-demand digital library that lets you easily search over 7,500 technology and creative reference books and videos to find the answers you need quickly. Withasubscription,youcanreadanypageandwatchanyvideofromourlibraryonline. Read books on your cell phone and mobile devices. Access new titles before they are available for print, and get exclusive access to manuscripts in development and post feedback for the authors. Copy and paste code samples, organize your favorites, down- load chapters, bookmark key sections, create notes, print out pages, and benefit from tons of other time-saving features. O’Reilly Media has uploaded this book to the Safari Books Online service. To have full digital access to this book and others on similar topics from O’Reilly and other pub- lishers, sign up for free at http://my.safaribooksonline.com. Preface | xvii
- 24. Acknowledgments First, I would like to thank the single most important person responsible for the creation of this book: my fiancée, Aarthi. In fact, I want to use this section to somehow apologize for what I made her go through. Not only did she put up with me agonizing over unwritten chapters and being unavailable pretty much every evening and weekend for more than a year, but she also proofread all chapters and corrected an uncountable number of mistakes. She did all of this while making sure I didn’t kill myself through the process and essentially taking care of me for more than a year. I promise to never put her through anything like this ever again. Aarthi, I love you and I’m sorry. This book is dedicated to my parents. This book, my career, and pretty much everything I do today is directly because of them. Speaking of my career and work, I have a ton of people to thank in and around the Microsoft community. I wouldn’t even be at Microsoft if it weren’t for people like Janakiram MSV, Paramesh Vaidyanathan, and S. Somasegar. At Microsoft, I’ve had the benefit of having several friends and mentors who have made sure I didn’t get myself fired. In particular, I’d like to mention Barry Bond, who apart from being one of the smartest engineers I’ve seen and my mentor for several years was also kind enough to review several chapters in this book. The entire Windows Azure team was of great support to me while I wrote this book. Chief among them was my boss, Vikram Bhambri. I still don’t know how he puts up with me every day and hasn’t fired me yet. Several people on the Windows Azure team helped me by answering questions and reviewing content. I’d like to thank Manuvir Das, David Lemphers, Steve Marx, Sumit Mehrotra, Mohit Srivastava, and Zhe Yang. Brad Calder and Hoi Vo read early sections of the book and provided feedback. Their early encouragement was of great help. Aleks Gershaft went to a lot of trouble to review my content at the very end and pointed out dozens of minor details. The storage chap- ters are a great deal better thanks to his efforts. One of the biggest reasons for me joining the Windows Azure team was the chance to work with Dave Cutler. He continues to be an inspiration every single day. In the O’Reilly world, I’ve been lucky to work with some great people. Brian Jepson was my first editor and he helped me tremendously. He knows exactly how to deal with the fragile ego of a first-time writer. Laurel Ruma and Mike Hendrickson helped me throughout the process and saw this book out the door. This book is a lot better for their efforts. It couldn’t have been easy dealing with me. I’ll miss all our arguments. An army of technical editors went through early versions of my content and helped me improve it: Ben Day, Johnny Halife, Brian Peek, Janakiram MSV, Michael Stiefel, and Chris Williams. They kept me on my toes and made me think really hard about my content. Any flaws in this book are despite their best efforts and are directly due to my stubbornness. xviii | Preface
- 25. Finally, I’d like to thank you, dear reader. Almost every single time I sat down to write, I would think to myself: “Will the people buying this book think they got value for their money?” I sincerely hope that you do. Contact me at [email protected] anytime to tell me what you thought about the book or just to yell at me for some obscure Monty Python reference you didn’t get. Sorry about that. Writing this book was a life-changing experience for me. I hope you have fun reading it and using Windows Azure! Preface | xix
- 27. CHAPTER 1 Cloud Computing If you drive from the airport in San Jose, California, down Interstate 180 South, chances are you’ll spot a sign for a seedy strip joint called the Pink Poodle. The story of Micro- soft’s cloud computing platform starts in 2006 with an eclectic set of people and this most unlikely of locations. Before I tell that story, we’ll examine what cloud comput- ing actually is, where it came from, and why it matters to you. Imagine if tap water didn’t exist. Every household would need to dig a well. Doing so would be a pain. Wells are expensive to build, and expensive to maintain. You wouldn’t be able get a large quantity of water quickly if you needed it—at least not without upgrading your pump. And if you no longer needed the well, there would be no store to return it to, and no way to recoup your capital investment. If you vacated the house, or the proper plumbing were installed in your house, you would have invested in a well you don’t need. Tap water fixes all of that. Someone else spends the money and builds the right plumb- ing and infrastructure. They manage it, and ensure that the water is clean and always available. You pay only for what you use. You can always get more if you want it. That, in a nutshell, is what cloud computing is all about. It is data center resources delivered like tap water. It is always on, and you pay only for what you use. This chapter takes a detailed look at the concepts behind cloud computing, and shows you how Windows Azure utilizes cloud computing. Understanding Cloud Computing Microsoft describes Windows Azure as an “operating system for the cloud.” But what exactly is the “cloud” and, more importantly, what exactly is cloud computing? At its core, cloud computing is the realization of the long-held dream of utility comput- ing. The “cloud” is a metaphor for the Internet, derived from a common representation in computer network drawings showing the Internet as a cloud. Utility computing is a concept that entails having access to computing resources, and paying for the use of 1
- 28. those resources on a metered basis, similar to paying for common utilities such as water, electricity, and telephone service. History of Cloud Computing Before diving into particulars, let’s first take a look at where cloud computing came from. The history of cloud computing includes utilization of the concept in a variety of environments, including the following: • Time-sharing systems • Mainframe computing systems • Transactional computing systems • Grid computing systems Time-sharing systems Cloud computing has its origins in the 1960s. Time-sharing systems were the first to offer a shared resource to the programmer. Before time-sharing systems, programmers typed in code using punch cards or tape, and submitted the cards or tape to a machine that executed jobs synchronously, one after another. This was massively inefficient, since the computer was subjected to a lot of idle time. Bob Bemer, an IBM computer scientist, proposed the idea of time sharing as part of an article in Automatic Control Magazine. Time sharing took advantage of the time the processor spent waiting for I/O, and allocated these slices of time to other users. Since multipleusersweredealtwithatthesametime,thesesystemswererequiredtomaintain the state of each user and each program, and to switch between them quickly. Though today’s machines accomplish this effortlessly, it took some time before computers had the speed and size in core memory to support this new approach. The first real project to implement a time-sharing system was begun by John McCarthy on an IBM 704 mainframe. The system that this led to, the Compatible Time Sharing System (CTSS), had the rudimentary elements of several technologies that to- day are taken for granted: text formatting, interuser messaging, as well as a rudimentary shell and scripting ability. John McCarthy later became famous as the father of LISP and modern artificial intelligence. CTSS led to Multics, which inspired Unix. Tymshare was an innovative company in this space. Started in 1964, Tymshare sold computer time and software packages to users. It had two SDS/XDS 940 mainframes that could be accessed via dial-up connections. In the late 1960s, Tymshare started using remote sites with minicomputers (known as nodes) running its own software 2 | Chapter 1: Cloud Computing
- 29. called the Supervisor. In this, Tymshare created the ancestor of modern networked systems. The product created by Tymshare, Tymnet, still exists today. After a series of takeovers and mergers, Tymshare is now owned by Verizon. These efforts marked the beginning of the central idea of cloud computing: sharing a single computing resource that is intelligently allocated among users. At its peak, there were dozens of vendors (including IBM and General Electric). Or- ganizations opened time-sharing accounts to get access to computing resources on a pay-per-usage model, and for overflow situations when they didn’t have enough inter- nal capacity to meet demand. These vendors competed in uptime, price, and the plat- form they ran on. They started offering applications and database management systems (DBMSs) on a pay-for-play model, as well. They eventually went out of fashion with the rise of the personal computer. Mainframe computing Though nearly outdated today, mainframe computing innovated several of the ideas you see in cloud computing. These large, monolithic systems were characterized by high computation speed, redundancy built into their internal systems, and generally delivering high reliability and availability. Mainframe systems were also early innova- tors of a technology that has resurged over the past few years: virtualization. IBM dominates the mainframe market. One of its most famous model series was the IBM System/360 (S/360). This project, infamous for its appearance in the book The Mythical Man Month: Essays on Software Engineering by Fred Brooks (Addison- Wesley), also brought virtualization to the mainstream. The CP/CMS operating system on the S/360 could create multiple independent virtual machines. This was possible because of hardware assistance from the S/260, which had two modes of instructions: the normal problem state and a special supervisor state. The supervisor state instructions would cause a hardware exception that the operating sys- tem could then handle. Its fundamental principles were similar to modern-day hard- ware assistance such as AMD-V (Pacifica) and Intel VT-X (Vanderpool). Mainframe usage dwindled because several of the technologies once found only on mainframes started showing up on increasingly smaller computers. Mainframe com- puting and cloud computing are similar in the idea that you have a centralized resource (in the case of cloud computing, a data center) that is too expensive for most companies to buy and maintain, but is affordable to lease or rent resources from. Data centers represent investments that only a few companies can make, and smaller companies rent resources from the companies that can afford them. Understanding Cloud Computing | 3
- 30. Transactional computing Transactional systems are the underpinning of most modern services. The technology behind transactional systems is instrumental in modern cloud services. Transactional systems allow processing to be split into individual, indivisible operations called trans- actions. Each transaction is atomic—it either succeeds as a whole or fails as a whole. Transactions are a fundamental part of every modern database system. The history of transactional processing systems has been intertwined with that of database systems. The 1960s, 1970s, and 1980s were a hotbed for database system research. By the late 1960s, database systems were coming into the mainstream. The COBOL committee formed a task group to define a standard database language. Re- lational theory was formalized in the 1970s starting with E.F. Codd’s seminal paper, and this led to SQL being standardized in the 1980s. In 1983, Oracle launched version 3 of its nascent database product, the first version of its database system to support a rudimentary form of transactions. While database systems were emerging, several significant innovations were happening in the transaction processing space. One of the first few systems with transaction pro- cessing capabilities was IBM’s Information Management System (IMS). IMS has a fascinating history. After President John F. Kennedy’s push for a mission to the moon, North America Rockwell won the bid to launch the first spacecraft to the moon. The company needed an auto- mated system to manage large bills of materials for the construction, and contracted with IBM for this system in 1966. IBM put together a small team, and legendary IBM engineer Vern Watts joined the effort. The system that IBM designed was eventually renamed IMS. IMS was a joint hierarchical database and information management system with trans- action processing capabilities. It had several of the features now taken for granted in modern systems: Atomicity, Consistency, Isolation, Durability (ACID) support; device independence; and so on. Somewhat surprisingly, IMS has stayed strong over the ages, and is still in widespread use. IBM also contributed another important project to transaction processing: System R. System R was the first SQL implementation that provided good transaction processing performance.SystemRperformedbreakthroughworkinseveralimportantareas:query optimization, locking systems, transaction isolation, storing the system catalog in a relational form inside the database itself, and so on. Tandem Computers was an early manufacturer of transaction processing systems. Tandem systems used redundant processors and designs to provide failover. Tandem’s flagship product, the NonStop series of systems, was marketed for its high uptime. 4 | Chapter 1: Cloud Computing
- 31. Tandem was also famous for its informal culture and for nurturing sev- eral employees who would go on to become famous in their own right. The most famous of these was Jim Gray, who, among several other ach- ievements, literally wrote the book on transaction processing. Tandem’s systems ran a custom operating system called Guardian. This operating sys- tem was the first to incorporate several techniques that are present in most modern distributed systems. The machine consisted of several processors, many of which exe- cuted in lock-step, and communicated over high-speed data buses (which also had redundancy built in). Process pairs were used to failover operations if execution on one processor halted for any reason. After a series of takeovers, Tandem is now a part of Hewlett-Packard. Tandem’s NonStop line of products is still used, with support for modern technologies such as Java. The fundamental design behind these systems—that is, fault tolerance, failover, two- phase commit, resource managers, Paxos (a fault-tolerance protocol for distributed systems), redundancy, the lessons culled from trying to implement distributed transactions—forms the bedrock of modern cloud computing systems, and has shaped their design to a large extent. Grid computing The term grid computing originated in the 1990s, and referred to making computers accessible in a manner similar to a power grid. This sounds a lot like cloud computing, and reflects the overlap between the two, with some companies even using the terms interchangeably. One of the better definitions of the difference between the two has been offered by Rick Wolski of the Eucalyptus project. He notes that grid computing is about users making few, but very large, requests. Only a few of these allocations can be serviced at any given time, and others must be queued. Cloud computing, on the other hand, is about lots of small allocation requests, with allocations happening in real time. If you want to read more about Wolski’s distinction between grid com- puting and cloud computing, see http://blog.rightscale.com/2008/07/07/ cloud-computing-vs-grid-computing/. The most famous grid computing project is SETI@home. At SETI, employees search for extraterrestrial intelligence. The SETI@home project splits data collected from telescopes into small chunks that are then downloaded into volunteer machines. The software installed on these machines scans through the radio telescope data looking for telltale signs of alien life. The project has logged some astonishing numbers—more than 5 million participants and more than 2 million years of aggregate computing time logged. Understanding Cloud Computing | 5
- 32. Several frameworks and products have evolved around grid computing. The Globus toolkit is an open source toolkit for grid computing built by the Globus Alliance. It allows you to build a computing grid based on commodity hardware, and then submit jobs to be processed on the grid. It has several pluggable job schedulers, both open source and proprietary. Globus is used extensively by the scientific community. CERN will be using Globus to process data from tests of the Large Hadron Collider in Geneva. Microsoft jumped into this space with the launch of Windows High Performance Computing (HPC) Server in September 2008. Windows HPC Server provides a cluster environment, management and monitoring tools, and a job scheduler, among several other features. Figure 1-1 shows the Windows HPC management interface. Most im- portantly,itintegrateswithWindowsDeploymentServices,anditcandeployoperating system images to set up the cluster. Later in this chapter, you’ll learn about how the Windows Azure fabric controller works, and you’ll see similar elements in its design. Figure 1-1. Windows High Performance Computing Cluster Manager The cloud allows you to run workloads similar to a grid. When you have data that must be processed you spin up the required number of machines, split the data across the machines in any number of ways, and aggregate the results together. Throughout this book, you’ll see several technologies that have roots in modern grid and distributed computing. 6 | Chapter 1: Cloud Computing
- 33. Understanding the Characteristics of Cloud Computing A modern cloud computing platform (of which, as you will see later in this chapter, Windows Azure is one) typically incorporates the following characteristics: The illusion of infinite resources Cloud computing platforms provide the illusion of infinite computing and storage resources. (Note that this description includes the word illusion because there will always be some limits, albeit large, that you must keep in mind.) As a user, you are not required to do the kind of capacity planning and provisioning that may be necessary to deploy your own individual storage and computing infrastructure. You can depend on the companies you are dealing with to own several large data centers spread around the world, and you can tap into those resources on an as- needed basis. Scale on demand All cloud platforms allow you to add resources on demand, rather than going through a lengthy sales-and-provisioning process. Instead of having to wait weeks for someone to deliver new servers to your data center, you typically must wait only minutes to get new resources assigned. This is a really good thing in terms of the cost and time required to provision resources, but it also means your applica- tion must be designed to scale along with the underlying hardware provided by your cloud computing supplier. Pay-for-play Cloud computing platforms typically don’t require any upfront investment, reser- vation, or major setup fees. You pay only for the software and hardware you use. This, along with the scaling capacity of cloud platforms, means you won’t incur huge capital expenditure (capex) costs upfront. All cloud platforms let you move away from capex spending and into operating expenditure (opex) spending. In layman’s terms, this converts a fixed cost for estimated usage upfront to a variable cost where you pay only for what you use. High availability and an SLA If you choose to depend on someone else to run your business, you must be assured that you won’t be subjected to frequent outages. Most cloud providers have a Service Level Agreement (SLA) that guarantees a level of uptime, and includes a refund mechanism if the SLA isn’t met. Windows Azure provides an SLA for both its storage and its hosting pieces. Geographically distributed data centers When serving customers around the globe, it is critical to have data centers in multiple geographic locations. Reasons for this requirement include legal/regula- tory concerns, geopolitical considerations, load balancing, network latency, edge caching, and so on. In short, cloud computing is like water or electricity. It is always on when you need it, and you pay only for what you use. Understanding Cloud Computing | 7
- 34. In reality, cloud computing providers today have some way to go before they meet the “several 9s” (99.99% and beyond uptime) availability provided by utility companies (gas, water, electricity) or telecom companies. Understanding Cloud Services Cloud computing platforms can be differentiated by the kind of services they offer. You might hear these referred to as one of the following: Infrastructure-as-a-Service (IaaS) This refers to services that provide lower levels of the stack. They typically provide basic hardware as a service—things such as virtual machines, load-balancer set- tings, and network attached storage. Amazon Web Services (AWS) and GoGrid fall into this category Platform-as-a-service (PaaS) Providers such as Windows Azure and Google App Engine (GAE) provide a plat- form that users write to. In this case, the term platform refers to something that abstracts away the lower levels of the stack. This application runs in a specialized environment. This environment is sometimes restricted—running as a low- privilege process, with restrictions on writing to the local disk and so on. Platform providers also provide abstractions around services (such as email, distributed ca- ches, structured storage), and provide bindings for various languages. In the case of GAE, users write code in a subset of Python, which executes inside a custom hosting environment in Google’s data centers. In Windows Azure, you typically write applications in .NET, but you can also call native code, write code using other languages and runtimes such as Python/PHP/Ruby/Java, and, in general, run most code that can run on Windows. Software-as-a-Service (SaaS) The canonical example of this model is Salesforce.com. Here, specific provided applications can be accessed from anywhere. Instead of hosting applications such as Customer Relationship Management (CRM), Enterprise Resource Planning (ERP), and Human Resources (HR) on-site, companies can outsource these appli- cations. These are higher-level services that we won’t address in much detail this book. In reality, cloud services overlap these categories, and it is difficult to pin any one of them down into a single category. 8 | Chapter 1: Cloud Computing
- 35. The Windows Azure Platform The Windows Azure Platform stack consists of a few distinct pieces, one of which (Windows Azure) is examined in detail throughout this book. However, before begin- ning to examine Windows Azure, you should know what the other pieces do, and how they fit in. The Windows Azure Platform is a group of cloud technologies to be used by applica- tions running in Microsoft’s data centers, on-premises and on various devices. The first question people have when seeing its architecture is “Do I need to run my application on Windows Azure to take advantage of the services on top?” The answer is “no.” You can access Azure AppFabric services and SQL Azure, as well as the other pieces from your own data center or the box under your desk, if you choose to. This is not represented by a typical technology stack diagram—the pieces on the top don’t necessarily run on the pieces on the bottom, and you’ll find that the technology powering these pieces is quite different. For example, the authentication mechanism usedinSQLAzureisdifferentfromtheoneusedinWindowsAzure.Adiagramshowing the Windows Azure platform merely shows Microsoft’s vision in the cloud space. Some of these products are nascent, and you’ll see them converge over time. Now, let’s take a look at some of the major pieces. Azure AppFabric Azure AppFabric services provide typical infrastructure services required by both on- premises and cloud applications. These services act at a higher level of the “stack” than Windows Azure (which you’ll learn about shortly). Most of these services can be ac- cessed through a public HTTP REST API, and hence can be used by applications run- ning on Windows Azure, as well as your applications running outside Microsoft’s data centers. However, because of networking latencies, accessing these services from Win- dows Azure might be faster because they are often hosted in the same data centers. Since this is a distinct piece from the rest of the Windows Azure platform, we will not cover it in this book. Following are the components of the Windows Azure AppFabric platform: Service Bus Hooking up services that live in different networks is tricky. There are several issues to work through: firewalls, network hardware, and so on. The Service Bus com- ponent of Windows Azure AppFabric is meant to deal with this problem. It allows applications to expose Windows Communication Foundation (WCF) endpoints that can be accessed from “outside” (that is, from another application not running inside the same location). Applications can expose service endpoints as public HTTP URLs that can be accessed from anywhere. The platform takes care of such challenges as network address translation, reliably getting data across, and so on. The Windows Azure Platform | 9
- 36. Access Control Thisserviceletsyouusefederatedauthenticationforyourservicebasedonaclaims- based, RESTful model. It also integrates with Active Directory Federation Services, letting you integrate with enterprise/on-premises applications. SQL Azure In essence, SQL Azure is SQL Server hosted in the cloud. It provides relational database features, but does it on a platform that is scalable, highly available, and load-balanced. Most importantly, unlike SQL Server, it is provided on a pay-as-you-go model, so there are no capital fees upfront (such as for hardware and licensing). As you’ll see shortly, there are several similarities between SQL Azure and the table services provided by Windows Azure. They both are scalable, reliable services hosted in Microsoft data centers. They both support a pay-for-usage model. The fundamental differences come down to what each system was designed to do. Windows Azure tables were designed to provide low-cost, highly scalable storage. They don’t have any relational database features—you won’t find foreign keys or joins or even SQL. SQL Azure, on the other hand, was designed to provide these features. We will examine these differences in more detail later in this book in the discussions about storage. Windows Azure Windows Azure is Microsoft’s platform for running applications in the cloud. You get on-demand computing and storage to host, scale, and manage web applications through Microsoft data centers. Unlike other versions of Windows, Windows Azure doesn’t run on any one machine—it is distributed across thousands of machines. There will never be a DVD of Windows Azure that you can pop in and install on your machine. Before looking at the individual features and components that make up Windows Azure, let’s examine how Microsoft got to this point, and some of the thinking behind the product. Understanding the Origins of Windows Azure The seeds for Windows Azure were sown in a 2005 memo from Ray Ozzie, Microsoft’s then-new Chief Software Architect, who had just taken over from Bill Gates. In that memo, Ozzie described the transformation of software from the kind you installed on your system via a CD to the kind you accessed through a web browser. It was a call to action for Microsoft to embrace the services world. Among other things, Ozzie called for a services platform. Several teams at Microsoft had been running successful services, but these lessons hadn’t been transformed into actual bits that internal teams or ex- ternal customers could use. 10 | Chapter 1: Cloud Computing
- 37. If you want to read the Ozzie memo, you can find it at http://www.script ing.com/disruption/ozzie/TheInternetServicesDisruptio.htm. In 2006, Amitabh Srivastava, a long-time veteran at Microsoft, was in charge of fixing the engineering processes in Windows. As Windows Vista drew close to launch, Srivastava met Ozzie and agreed to lead a new project to explore a services platform. Srivastava quickly convinced some key people to join him. Arguably, the most impor- tant of these was Dave Cutler, the father of Windows NT and Virtual Memory System (VMS). Cutler is a legendary figure in computing, and a near-mythical figure at Micro- soft, known for his coding and design skills as well as his fearsome personality. Con- vincing Cutler to come out of semiretirement to join the new team was a jolt in the arm. During this period, the nascent team made several trips to all of Microsoft’s major online services to see how they ran things, and to get a feel for what problems they faced. It was during one such trip to California to see Hotmail that Cutler suggested (in jest) that they name their new project “Pink Poodle” after a strip joint they spotted on the drive from the San Jose airport. A variant of this name, “Red Dog,” was suggested by another team member, and was quickly adopted as the codename for the project they were working on. After looking at several internal and external teams, they found similar problems across them all. They found that everyone was spending a lot of time managing the machines/ virtual machines they owned, and that these machines were inefficiently utilized in the first place. They found that there was little sharing of resources, and that there was no shared platform or standard toolset that worked for everyone. They also found several good tools, code, and ideas that they could reuse. The growing team started building out the various components that made up Red Dog: a new hypervisor (software that manages and runs virtual machines), a “fabric” con- troller (a distributed system to manage machines and applications), a distributed stor- age system, and, like every other Microsoft platform, compelling developer tools. They realized that they were exploring solutions that would solve problems for everyone outside Microsoft, as well as inside, and switched to shaping this into a product that Microsoft’s customers could use. Working in a startup-like fashion, they did things that weren’t normally done at Microsoft, and broke some rules along the way (such as turninganearbybuildingintoasmalldatacenter,andstealingpowerfromthebuildings around it). You can read more about this adventure at http://www.wired.com/tech biz/people/magazine/16-12/ff_ozzie?currentPage=1. Windows Azure | 11
- 38. Red Dog, now renamed Windows Azure, was officially unveiled along with the rest of the Azure stack during the Professional Developers Conference in Los Angeles on October 27, 2008. Understanding Windows Azure Features As shown in Figure 1-2, when you use Windows Azure you get the following key features: Service hosting You can build services that are then hosted by Windows Azure. Services here refers to any generic server-side application—be it a website, a computation service to crunch massive amounts of data, or any generic server-side application. Note that, in the current release of Windows Azure, there are limits to what kind of code is allowed and not allowed. For example, code that requires administrative privileges on the machine is not allowed. Service management In a traditional environment, you must deal with diverse operational tasks— everything from dealing with application updates, to monitoring the application, to replacing failed hardware. In a traditional environment, there are a variety of tools to help you do this. In the Microsoft ecosystem outside of Azure, you might use the capabilities built into Windows Server and products such as Systems Cen- ter. In the non-Microsoft world, you might be using tools such as Capistrano for deployment and projects such as Ganglia for monitoring. Windows Azure’s fabric controller brings this “in-house” and deals with this automatically for you. It mon- itors your services, deals with hardware and software failures, and handles oper- ating system and application upgrades seamlessly. Storage Windows Azure provides scalable storage in which you can store data. Three key services are provided: binary large object (blob) storage (for storing raw data), semistructured tables, and a queue service. All services have an HTTP API on top of them that you can use to access the services from any language, and from outside Microsoft’s data centers as well. The data stored in these services is also replicated multiple times to protect from internal hardware or software failure. Storage (like computation) is based on a consumption model where you pay only for what you use. Windows Server If you’re wondering whether your code is going to look different because it is run- ning in the cloud, or whether you’re going to have to learn a new framework, the answer is “no.” You’ll still be writing code that runs on Windows Server. The .NET Framework (3.5 SP1, as of this writing) is installed by default on all machines, and your typical ASP.NET code will work. If you choose to, you can use FastCGI sup- port to run any framework that supports FastCGI (such as PHP, Ruby on Rails, 12 | Chapter 1: Cloud Computing
- 39. Python, and so on). If you have existing native code or binaries, you can run that as well. Development tools Like every major Microsoft platform, Windows Azure has a bunch of tools to make developing on it easier. Windows Azure has an API that you can use for logging anderrorreporting,aswellasmechanismstoreadandupdateserviceconfiguration files. There’s also an SDK that enables you to deploy your applications to a cloud simulator, as well as Visual Studio extensions. Virtualization At the bottom of the Windows Azure stack, you’ll find a lot of machines in Microsoft data centers. These are state-of-the-art data centers with efficient power usage, beefy bandwidth, and cooling systems. Even the most efficient facilities still possess a lot of room for overhead and waste when it comes to utilization of resources. Since the biggest source of data center cost is power, this is typically measured in performance/watts/ dollars. What causes that number to go up? As of this writing, Windows Azure is hosted in six locations spread across the United States, Europe, and Asia. If you run services on the “bare metal” (directly on a physical machine), you soon run into a number of challenges as far as utilization is concerned. If a service is using a machine and is experiencing low traffic while another service is experiencing high Figure 1-2. Windows Azure overview Windows Azure | 13
- 40. traffic, there is no easy way to move hardware from one service to the other. This is a big reason you see services from large organizations experience outages under heavy traffic, even though they have excess capacity in other areas in their data centers—they don’t have a mechanism to shift workloads easily. The other big challenge with running on the bare metal is that you are limited to running one service per box. You cannot host multiple services, since it is difficult to offer guarantees for resources and security. As an answer to these problems, the industry has been shifting to a virtualized model. In essence, hardware virtualization lets you partition a single physical machine into manyvirtualmachines.IfyouuseVMwareFusion,ParallelsDesktop,Sun’sVirtualBox, or Microsoft Virtual PC, you’re already using virtualization, albeit the desktop flavor. The hypervisor is a piece of software that runs in the lower parts of the system and lets the host hardware be shared by multiple guest operating systems. As far as the guest operating systems and the software running on them are concerned, there is no dis- cernible difference. There are several popular server virtualization products on the market, including VMware’s product, Xen (which Amazon uses in its cloud services), and Microsoft’s Windows Hyper-V. Windows Azure has its own hypervisor built from scratch and optimized for cloud services. In practice this means that, since Microsoft controls the specific hardware in its data centers, this hypervisor can make use of specific hardware enhancements that a generic hypervisor targeted at a wide range of hardware (and a heterogeneous envi- ronment) cannot. This hypervisor is efficient, has a small footprint, and is tightly inte- grated with the kernel of the operating system running on top of it. This leads to performance close to what you’d see from running on the bare metal. In case you are wondering whether you can use this hypervisor in your data center, you’ll be happy to hear that several innovations from this will be incorporated into future editions of Hyper-V. Each hypervisor manages several virtual operating systems. All of these run a Windows Server 2008–compatible operating system. In reality, you won’t see any difference between running on normal Windows Server 2008 and these machines—the only dif- ferences are some optimizations for the specific hypervisor they’re running on. This Windows Server 2008 image has the .NET Framework (3.5 SP1, as of this writing) installed on it. Running on a hypervisor provides Windows Azure with a lot of freedom. For example, no lengthy operating system installation is required. To run your application, Windows Azure can just copy over an image of the operating system, a Virtual Hard Disk (VHD) containing your application-specific binaries. You simply boot the machine from the image using a new boot-from-VHD feature. If you have, say, a new operating system patch, no problem. Windows Azure just patches the image, copies it to the target 14 | Chapter 1: Cloud Computing
- 41. machine, and boots. Voilà! You have a patched machine in a matter of minutes, if not seconds. You can write applications just as you did before, and in almost all cases, you can simply ignore the fact that you’re not running on native hardware. The Fabric Controller Imagine that you’re describing your service architecture to a colleague. You probably walk up to the whiteboard and draw some boxes to refer to your individual machines, and sketch in some arrows. In the real world, you spend a lot of time implementing this diagram. You first set up some machines on which you install your bits. You deploy the various pieces of software to the right machines. You set up various networking settings: firewalls, virtual LANs, load balancers, and so on. You also set up monitoring systems to be alerted when a node goes down. In a nutshell, Azure’s fabric controller (see Figure 1-3) automates all of this for you. Azure’s fabric controller is a piece of highly available, distributed software that runs across all of Windows Azure’s nodes, and monitors the state of every node. You tell it what you want by specifying your service model (effectively, a declarative version of the whiteboard diagram used to describe your architecture to a colleague), and the fabric controller automates the details. It finds the right hardware, sets up your bits, and applies the right network settings. It also monitors your application and the hardware so that, in case of a crash, your application can be restarted on either the same node or a different node. Figure 1-3. What the fabric does Windows Azure | 15
- 42. In short, the fabric controller performs the following key tasks: Hardware management The fabric controller manages the low-level hardware in the data center. It provi- sions and monitors, and takes corrective actions when things go wrong. The hard- ware it manages ranges from nodes to TOR/L2 switches, load balancers, routers, and other network elements. When the fabric controller detects a problem, it tries to perform corrective actions. If that isn’t possible, it takes the hardware out of the pool and gets a human operator to investigate it. Service modeling The fabric controller maps declarative service specifications (the written down, logical version of the whiteboard diagrams mentioned at the beginning of this sec- tion) and maps them to physical hardware. This is the key task performed by the fabric controller. If you grok this, you grok the fabric controller. The service model outlines the topology of the service, and specifies the various roles and how they’re connected, right down to the last precise granular detail. The fabric controller can then maintain this model. For example, if you specify that you have three frontend nodes talking to a backend node through a specific port, the fabric controller can ensure that the topology always holds up. In case of a failure, it deploys the right binaries on a new node, and brings the service model back to its correct state. Later in this book, you’ll learn in detail how the fabric controller works, and how your application can take advantage of this. Operating system management The fabric controller takes care of patching the operating systems that run on these nodes, and does so in a manner that lets your service stay up. Service life cycle The fabric controller also automates various parts of the service life cycle—things such as updates and configuration changes. You can partition your application into sections (update domains and fault domains), and the fabric controller updates only one domain at a time, ensuring that your service stays up. If you’re pushing new configuration changes, it brings down one section of your machines and updates them, then moves on to the next set, and so on, ensuring that your service stays up throughout. Storage If you think of Windows Azure as being similar to an operating system, the storage services are analogous to its filesystem. Normal storage solutions don’t always work very well in a highly scalable, scale-out (rather than scale-up) cloud environment. This is what pushed Google to develop systems such as BigTable and Google File System, and Amazon to develop Dynamo and to later offer S3 and SimpleDb. Windows Azure offers three key data services: blobs, tables, and queues. All of these services are highly scalable, distributed, and reliable. In each case, multiple copies of 16 | Chapter 1: Cloud Computing
- 43. the data are made, and several processes are in place to ensure that you don’t lose your data. All of the services detailed here are available over HTTP through a simple REST API, and can be accessed from outside Microsoft’s data centers as well. Like everything else in Azure, you pay only for what you use and what you store. Unlike some other distributed storage systems, none of Windows Azure’s storage services are eventually consistent. This means that when you do a write, it is instantly visible to all subsequent readers. Eventu- ally, consistency is typically used to boost performance, but is more difficult to code against than consistent APIs (since you cannot rely on reading what you just wrote). Azure’s storage services allow for opti- mistic concurrency support to give you increased performance if you don’tcareabouthavingtheexactrightdata(forexample,logs,analytics, and so on). Blob storage The blob storage service provides a simple interface for storing named files along with metadata. Files can be up to 1 TB in size, and there is almost no limit to the number you can store or the total storage available to you. You can also chop uploads into smaller sections, which makes uploading large files much easier. Here is some sample Python code to give you a taste of how you’d access a blob using the API. This uses the unofficial library from http://github.com/sriramk/winazurestor age/. (We will explore the official .NET client in detail later in this book.) blobs = BlobStorage(HOST,ACCOUNT,SECRET_KEY) blobs.create_container("testcontainer", False) blobs.put_blob("testcontainer","test","Hello World!" ) Queue service The queue service provides reliable storage and delivery of messages for your applica- tion. You’ll typically use it to hook up the various components of your application, and not have to build your own messaging system. You can send an unlimited number of messages, and you are guaranteed reliable delivery. You can also control the lifetime of the message. You can decide exactly when you’re finished processing the message and remove it from the queue. Since this service is available over the public HTTP API, you can use it for applications running on your own premises as well. Table storage The table storage service is arguably the most interesting of all the storage services. Almost every application needs some form of structured storage. Traditionally, this is through a relational database management system (RDBMS) such as Oracle, SQL Server, MySQL, and the like. Google was the first company to build a large, distributed, Windows Azure | 17
- 44. structured storage system that focused on scale-out, low cost, and high performance: BigTable. In doing this, Google was also willing to give up some relational capabilities—SQL support, foreign keys, joins, and everything that goes with it—and denormalize its data. Systems such as Facebook’s Cassandra and Amazon’s SimpleDb follow the same principles. The Windows Azure table storage service provides the same kind of capability. You can create massively scalable tables (billions of rows, and it scales along with traffic). The data in these tables is replicated to ensure that no data is lost in the case of hardware failure. Data is stored in the form of entities, each of which has a set of properties. This is similar to (but not the same as) a database table and column. You control how the data is partitioned using PartitionKeys and RowKeys. By partitioning across as many machines as possible, you help query performance. You may be wondering what language you use to query this service. If you’re in the .NET world, you can write Language Integrated Query (LINQ) code, and your code will look similar to LINQ queries you’d write against other data stores. If you’re coding in Python or Ruby or some other non-.NET environment, you have an HTTP API where you can encode simple queries. If you’re familiar with ADO.NET Data Services (pre- viously called Astoria), you’ll be happy to hear that this is just a normal ADO.NET Data Service API. If you’re intimidated by all this, don’t be. Moving to a new storage system can be daunting, and you’ll find that there are several tools and familiar APIs to help you along the way. You also have the option to use familiar SQL Server support if you are willing to forego some of the features you get with the table storage service. When Not to Use the Cloud You may be surprised to see a section talking about the pitfalls of cloud computing in thischapter.Tobesure,someproblemsexistwithallcloudcomputingplatformstoday, and Windows Azure is no exception. This section helps you carefully determine whether you can live with these problems. More often than not, you can. If you find that cloud computing isn’t your cup of tea, there is nothing wrong with that; traditional hosting isn’t going away anytime soon. Note that the following discussion applies to every cloud computing platform in exis- tence today, and is by no means unique to Windows Azure. Service Availability Outages happen. As a user, you expect a service to always be running. But the truth is that the current state of cloud providers (or any sort of hosting providers, for that matter) doesn’t give the level of availability offered by a power utility or a telecom 18 | Chapter 1: Cloud Computing
- 45. company. Can you live with outages? That depends on several factors, including some possible mitigation strategies: • Do you know how frequently your existing infrastructure has outages? In most cases, this is probably a much higher number than what you’ll see with cloud computing providers. • You can use multiple cloud computing providers as a backup strategy in case of an outage. • You can host core business functions on-premises and use the cloud for excess capacity. Or you can run a small on-premises infrastructure and fall back to that in case of an outage. Outages aren’t caused only by software issues. DDoS attacks are another critical prob- lem, and attacks from large botnets are still difficult to defend against, regardless of what kind of provider you’re hosted on. Custom Infrastructure Requirements Several users have custom hardware needs. Some users may need high-end GPUs for heavy graphics processing, while others need high-speed interconnects for high- performance computing and aren’t satisfied with gigabit Ethernet. High-end storage area networks (SANs) and special RAID configurations are popular requests. Cloud computing thrives on homogeneous data center environments running mostly com- modity hardware. It is this aspect that drives the cost of these services down. In such an environment, it is difficult to have custom hardware. Having said that, it is only a matter of time before providers of cloud computing start rolling out some specialized hardware to satisfy the more common requests. Security, Confidentiality, and Audits This is probably the biggest showstopper with cloud computing adoption today. With on-premises hardware, you have complete control over your hardware and processes— where the data center is located, who touches the hardware, what security processes are in place, and so on. With cloud computing, you must outsource these critical steps to a third party, and that can be hard to swallow for the following reasons: • You might need data in a specific physical location for legal and regulatory reasons. For example, several firms cannot store data for European customers outside Eu- rope. Other firms cannot take data outside the United States. Some don’t want their data in specific countries for legal reasons, with China and the United States leading the list. With cloud computing, you must carefully inspect where your provider hosts the data centers. • There are several standards with which you may need to comply. The Health In- surance Portability and Accountability Act (HIPAA), the Sarbanes-Oxley Act When Not to Use the Cloud | 19
- 46. (SOX), and Payment Card Industry (PCI) Data Security Standards are some of the popular ones. Most cloud computing providers are not compliant. Some are in the process of being audited, while some standards may never be supported. You must examine your cloud computing provider’s policy. With some standards, it may be possible to comply by encrypting data before placing it in the cloud. Health services use this approach today on Amazon S3 and Windows Azure storage to maintain compliance. • You must ensure that you’re following security best practices when inside the cloud—setting the right network settings, using Secure Sockets Layer (SSL) when- ever possible, and so on. For the storage services, you must keep the keys safe, and regenerate them periodically. At the end of the day, the cloud is not inherently less secure than your own infrastruc- ture. It mostly comes down to a trust issue: do you trust the provider to maintain your business-critical data in a responsible manner? Capacity Planning and Limits The idea that you don’t have to do capacity planning in the cloud is a myth. You still must plan for usage, or you might wind up getting stuck with a huge bill. For example, when hit by a Slashdot effect, you may not want to scale your application beyond a particular point, and you may be willing to live with a degraded experience. Unfortu- nately, optimizing your applications to cost less on the cloud is a topic that is not well understood, primarily because of the nascent nature of this space—the years of un- derstanding that have gone into planning traditional systems just haven’t been expe- rienced with cloud computing. With cloud computing, the decision to use up more capacity need not rest with the chief investment officer. It could rest with the developer, or someone quite low in the food chain. This raises a lot of unanswered questions regarding how companies should plan for usage. Though there are no good answers today, one good book on the best practices in this space is The Art of Capacity Planning by John Allspaw from Flickr (O’Reilly). Unpredictable Performance All cloud computing providers have SLA-backed guarantees on the performance you can get. However, there are no good benchmarks or measurement tools today. You might find that your performance is what was promised most of the time, but once in a while, you might see some variance. Since you’re running on a shared infrastructure, this is unavoidable. The customer hosted on the switch next to yours might experience a sudden burst in traffic and have a knock-on effect. On the other hand, this is what you’ll experience in most collocation sites, too. 20 | Chapter 1: Cloud Computing
- 47. A favorite anecdote in this regard is of a critical business service that was collocated in the same data center as a component from World of War- craft (WoW). Whenever WoW did a major update, the data center’s bandwidth got swamped, and the business service started seeing out- ages. Now, that’s a problem that’s hard to plan for (and explain to your customers)! Migration and Interoperability There are two kinds of migrations that you should care about. One is from traditional on-premises systems to the cloud, and the other is from one cloud provider to another. For migrating on-premises systems to the cloud, you’ll often find yourself needing to rewrite/modify parts of your application. Though platforms such as Windows Azure try to make it as seamless as possible to port applications, there are some inherent differences, and you’ll need to make at least some small changes. Migrating from one cloud provider to another is much more complicated. There is a lack of standards, even de facto ones, in this space. Most APIs are incompatible, and you’ll have to hand-roll some custom scripts/code to migrate. In some cases, migration may not be possible at all. All of this raises questions about lock-in. You must examine how you can get to your data. In the case of Windows Azure, you can always get to your data over HTTP and publicly documented protocols. If you decide to stop using Windows Azure one day, you can pull your data out of the system and put it elsewhere. The same goes for code. Since these are early days for cloud computing, the tools and thinking around intero- perabilityareearly,too.Severaleffortsrelatedtointeroperabilitystandardsarespinning up to tackle this problem. Summary Very few technologies can claim to be the “Next Big Thing” because their advantages are so obvious. Cloud computing can legitimately claim to be one of them. However, the basic principles and technology behind the cloud have existed for decades. Like Yogi Berra said, “It is like déjà vu all over again.” This chapter provided a lot of text with very little code. In Chapter 3, you’ll get to crank open the editor and do some coding! Summary | 21
- 49. CHAPTER 2 Under the Hood As you wade through the details of a new platform, you may feel like you are fighting a battle without understanding the battlefield. It is critical to know the internals of any platform and how it works. Whether you are building a better-performing application, or trying to understand why you’re seeing a weird error message, knowing how things look under the hood can mean the difference between winning and losing the battle. Even if it isn’t useful, peeking under the hood of a complex system is always fun and educational. This chapter provides just that sort of glimpse inside Windows Azure to help you to understand how this new platform works. Inside the Cloud Windows Azure is a complex, multitiered platform. It combines hardware and soft- ware, split across many layers and many geographic locations. In this complexity, it is easy to get confused. How does your code run? Which operating system is it running on? How is your code protected? How does Windows Azure work? The best way to answer these important questions is to walk through the Windows Azure “stack.” Windows Azure is best visualized through an “onion skin” diagram such as the one in Figure 2-1. This chapter examines all the lower layers of that diagram in detail, starting from the innermost ring (the hardware) and working outward. The actual hardware appears at the innermost “ring.” Microsoft operates several data centers around the world, and Windows Azure runs on some of these data centers. Each machine runs a custom hypervisor optimized and tuned for the data center, as well as for the specific hardware that runs these machines. 23
- 50. This hypervisor really doesn’t have an “official” name. You’ll often hear it referred to as the Windows Azure hypervisor, which is the reference that will be used here for the sake of simplicity. The important thing to remember is that this is not the same as Hyper-V, the hypervisor that ships with Windows Server 2008. Later in this chapter, you’ll learn more about the differences between the two. These machines are grouped and managed by a massive distributed software applica- tion called the fabric. The fabric manages hardware, the operating systems on the ma- chines, and the applications running on the machines. These applications can include everything from the services Windows Azure offers (such as blob, queue, and table storage) to your own code. There are several of these fabrics in different geographic locations. When you deploy your application, or when you create a storage account, you can choose at which of these locations you want to host it. Let’s dig into each of these concepts in a bit more detail. Is Windows Azure a “Cloud Operating System”? You often hear of Windows Azure being described as a “cloud operating system,” or as an “operating system for the cloud.” Though this is a useful analogy for a nontech- nical audience, it often confuses developers who wonder whether there is a new oper- ating system on the loose in Microsoft’s data centers. The key thing to remember here is that this is a stretched analogy. If you look at an operating system, one of its core tasks is to abstract away the hardware from the Figure 2-1. Windows Azure onion 24 | Chapter 2: Under the Hood
- 51. applications that run on it. Instead of having to worry about the specifics of the hard- ware, you can write code to a generic API, and let the operating system manage the hardware for you. Windows Azure is an “operating system for the cloud” in a similar sense, because it abstracts away the hardware in the data center. Just as a good desktop operating system abstracts away physical memory and hardware specifics, Windows Azure tries to abstract away the physical aspects of the data center. However, the analogy ends there. Windows Azure in itself is not a “real operating system” like Windows or Linux or Mac OS X. The operating system that your code winds up running on is just Windows Server 2008. The Data Centers Data centers are where all the action is as far as Windows Azure is concerned. Windows Azure physically runs in several of Microsoft’s data centers around the world. Like all other major companies building and running data centers, Microsoft likes to keep cer- tain information about them close to the vest, so this section may seem light on details in some areas. Microsoft built its first data center in September 1989. It was located in the heart of the Microsoft campus in Redmond, Washington, and was a far cry from the modern data centers that power Microsoft’s online services today. The first data centers were similar to the ones you’ve probably seen in many offices. They had cables running under raised floors, some enhanced security, and environ- mental controls, but they weren’t meant to run services at the massive scale required today. Microsoft has even built several mega data centers around the world over the past few years. Microsoft doesn’t reveal the exact number of data centers—the only official comment to this point has been that the number is between “10 and 100.” Also, Microsoft doesn’t talk about the exact location of all its data centers. Note that these are Microsoft data centers used for a wide variety of purposes, and not necessarily for running Windows Azure. Each of these data centers is massive in scale, but at the same time is built to be envi- ronmentally friendly. For example, the one in Quincy is approximately 500,000 square feet in area, with critical power of 27 megawatts. That’s a lot of juice. However, all power is from a hydroelectric source. Similarly, the one in San Antonio uses recycled water for cooling. How does Microsoft decide where to build these data centers? Picking locations for data centers is a difficult task, and is almost an art in itself. Think of it as buying a house, albeit one that you can’t easily sell. Just as you would scope out the neighborhood, look for the nearest grocery store, and think about the daily commute, any company The Data Centers | 25
- 52. spending hundreds of millions of dollars building a new data center must also worry about several factors. Microsoft uses a “heat map” of more than 35 different criteria when picking a location. The criteria include close proximity to an ample power source (for obvious reasons), fiber-optic networks, a large pool of skilled labor, affordable energy rates, tax consid- erations, and several other factors. Most of these factors are highly stable over time, but once in a while, they change and cause a ripple effect in services that run on these data centers. As an example of how things can fluctuate over time, during the time it was in CTP mode, Windows Azure itself was forced to change when a geolocation was removed because of local tax law changes. Security As you might expect, security is very tight in these data centers. Let’s look at two specific aspects of data center security. This discussion is quite limited in scope, and touches only lightly on some of the protection mechanisms. A complete look at the security controls in place in Windows Azure would be voluminous and beyond the scope of this book. Physical security Each data center has several layers of physical security with increasing controls through each perimeter. Access is restricted, and only essential personnel are au- thorized to manage customer applications and services. To keep the “baddies” out, as well as to detect intrusions, a wide array of security devices are in use, including cameras, biometrics, card readers, and so on. Network security Network protection comes from a wide collection of network devices, including load balancers, specialized hardware firewalls, and intrusion prevention devices. Applications and services are split into segmented virtual local area networks (VLANs) to ensure that traffic doesn’t cross application boundaries. Additional controlsarealsoinplacetolessentheimpactofdistributeddenialofservice(DDoS) attacks. Compliance Compliance is a hot topic in cloud computing, especially for those looking to move enterprise applications to the cloud. Microsoft’s data centers are periodically audited to ensure that they are in compliance with Payment Card Industry (PCI) Data Security 26 | Chapter 2: Under the Hood
- 53. Standards, Sarbanes-Oxley (SOX), Health Insurance Portability and Accountability Act (HIPAA), and several other hard-to-pronounce standards. However, note that this is compliance as far as the data centers go. As of this writing, Microsofthasn’tmadeanypubliccommentregardingwhichstandardsWindowsAzure is compliant with. This is one area where users should expect future statements and clarification. The Hypervisor With all of the machines in these data centers, the next obvious question concerns how an operating system actually runs on these machines. The default option would be to install Windows Server 2008 directly on these machines and run them. This is, in fact, how most people run Microsoft software in their data centers today, and indeed is how Microsoft runs several of its services in its data centers. Microsoft doesn’t reveal how many machines it uses to run Windows Azure. The exact hardware used in Microsoft data centers also has not been specified, but as with most modern data center deployments, it is safe to assume that it is fairly homogeneous. When managing thousands of machines, you want as much uniformity as you can get away with. However, there are two key problems with this approach: Sharing resources Henry Ford once said, “Any customer can have a car painted any color, as long as it is black.” Running operating systems directly on the hardware means the same holds true for machine size. Every application gets to use the same type of machine in the data center. However, if you have beefy, eight-core machines with tens of gigabytesofRAM,andseveraluserseachhavetinywebsiteswithnotraffic,itmakes little sense to give each user his own machine (and make the user pay for the entire machine). Migrating workloads You cannot move applications and workloads around easily. If Website A were experiencing low traffic and Website B suddenly goes viral and is taking a pound- ing, you cannot quickly take A’s machines and give them to B. You would need to wipe A’s machines to get rid of any custom installation and changes A might have performed, install Windows again, and then install B on top of it. The industry solution to these (and several other) problems with running different workloads in the data center is to use virtualization. This refers to the capability to run several guest operating systems simultaneously on the same machine under a host op- erating system. Each operating system sees an entire machine (typically called a virtual machine), and is unaware of the existence of the other operating systems. These virtual The Hypervisor | 27
- 54. machines share the resources of the underlying hardware, and also run in a sandbox to ensure that they can’t access resources they’re not supposed to, or affect any of the other operating systems running on the machine. How Is Virtualization Different from What Operating Systems Do Today? In general, virtualization refers to abstracting away some hardware resource. Most modern operating systems have a degree of virtualization built in. Different processes on the same machine all see the same amount of RAM, and can’t get at virtual memory from another process. Multiple disks might be bound together under a RAID config- urationandappearasonelogicaldisk.However,thisisolationisn’tsufficientfortoday’s cloud computing needs. For example, some providers try to work around the problem of sharing resources by running multiple services/websites on the same machine, and using operating system user accounts/access control lists (ACLs) to isolate one service from another. However, this frequently proves insufficient. One website could consume 100% of the CPU and starve other websites on the machine, or use up all the bandwidth on the network interface. The best way to fix that is to use one of the virtualization techniques described in this chapter. Hypervisor Architecture To create several virtual machines on one physical machine, a thin piece of low-level system software called the hypervisor or Virtual Machine Monitor (VMM) is used. The hypervisor is responsible for fair allocation of resources between the various virtual machines. It schedules CPU time and I/O requests, and provides for isolation between the various virtual machines. To perform these tasks efficiently, the hypervisor relies on hardware support. Since this is a relatively new development in the x86/x64 hardware world, each vendor has its own twist on how this support works. Both Intel and AMD developed extensions to their x86/x64 processor line. Though they are incompatible, fortunately for you (and for all the developers building hypervisors) they both work using similar concepts. To understand how they work, let’s first look a bit deeper at certain parts of how x86/x64 code is executed on your machine. A typical x86/x64 processor has four privilege levels called Rings, with Ring 0 being the most powerful and Ring 3 being the most restricted. In general, code executing in Ring N has access to all the same functionality as code executing in Ring 0..N. All modern operating systems follow a model where the operating system kernel (the core or heart of the operating system) runs in Ring 0, and all user-mode applications run in Ring 3. 28 | Chapter 2: Under the Hood
- 55. Exploring the Variety of Random Documents with Different Content
- 56. XI. THE FIGHTING QUAILS. Wang Ch‘êng belonged to an old family in P‘ing-yüan, but was such an idle fellow that his property gradually disappeared, until at length all he had left was an old tumble-down house. His wife and he slept under a coarse hempen coverlet, and the former was far from sparing of her reproaches. At the time of which we are speaking the weather was unbearably hot; and Wang went to pass the night with many other of his fellow-villagers in a pavilion which stood among some dilapidated buildings belonging to a family named Chou. With the first streaks of dawn his comrades departed; but Wang slept well on till about nine o’clock, when he got up and proceeded leisurely home. All at once he saw in the grass a gold hair-pin; and taking it up to look at it, found engraved thereon in small characters—“The property of the Imperial family.” Now Wang’s own grandfather had married into the Imperial family, [84] and consequently he had formerly possessed many similar articles; but while he was thinking it over up came an old woman in search of the hair-pin, which Wang, who though poor was honest, at once produced and handed to her. The old woman was delighted, and thanked Wang very much for his goodness, observing that the pin was not worth much in itself, but was a relic of her departed husband. Wang asked what her husband had been; to which she
- 57. replied, “His name was Wang Chien-chih, and he was connected by marriage with the Imperial family.” “My own grandfather!” cried Wang, in great surprise; “how could you have known him?” “You, then,” said the old woman, “are his grandson. I am a fox, and many years ago I was married to your grandfather; but when he died I retired from the world. Passing by here I lost my hair-pin, which destiny conveyed into your hands.” Wang had heard of his grandfather’s fox-wife, and believing therefore the old woman’s story, invited her to return with him, which she did. Wang called his wife out to receive her; but when she came in rags and tatters, with unkempt hair and dirty face, the old woman sighed, and said, “Alas! Alas! has Wang Chien-chih’s grandson come to this?” Then looking at the broken, smokeless stove, she added, “How, under these circumstances, have you managed even to support life?” Here Wang’s wife told the tale of their poverty, with much sobbing and tears; whereupon the old woman gave her the hair-pin, bidding her go pawn it, and with the proceeds buy some food, saying that in three days she would visit them again. Wang pressed her to stay, but she said, “You can’t even keep your wife alive; what would it benefit you to have me also dependent on you?” So she went away, and then Wang told his wife who she was, at which his wife felt very much alarmed; but Wang was so loud in her praises, that finally his wife consented to treat her with all proper respect. In three days she returned as agreed, and, producing some money, sent out for a hundred-weight of rice and a hundred-weight of corn. She passed the night with them, sleeping with Mrs. Wang, who was at first rather frightened, but who soon laid aside her suspicions when she found that the old lady meant so well towards them. Next day, the latter addressed Wang, saying, “My grandson, you must not be so lazy. You should try to make a little money in some way or other.”
- 58. Wang replied that he had no capital; upon which the old lady said, “When your grandfather was alive, he allowed me to take what money I liked; but not being a mortal, I had no use for it, and consequently did not draw largely upon him. I have, however, saved from my pin-money the sum of forty ounces of silver, which has long been lying idle for want of an investment. Take it, and buy summer cloth, which you may carry to the capital and re-sell at a profit.” So Wang bought some fifty pieces of summer cloth; and the old lady made him get ready, calculating that in six or seven days he would reach the capital. She also warned him, saying, “Be neither lazy nor slow— For if a day too long you wait, Repentance comes a day too late.” Wang promised all obedience, and packed up his goods and went off. On the road he was overtaken by a rain-storm which soaked him through to the skin; and as he was not accustomed to be out in bad weather, it was altogether too much for him. He accordingly sought shelter in an inn, but the rain went on steadily till night, running over the eaves of the house like so many ropes. Next morning the roads were in a horrible state; and Wang, watching the passers-by slipping about in the slush, unable to see any path, dared not face it all, and remained until noon, when it began to dry up a little. Just then, however, the clouds closed over again, and down came the rain in torrents, causing him to stay another night before he could go on. When he was nearing the capital, he heard to his great joy that summer cloth was at a premium; and on arrival proceeded at once to take up his quarters at an inn. There the landlord said it was a pity he had come so late, as communications with the south having
- 59. been only recently opened, the supply of summer cloth had been small; and there being a great demand for it among the wealthy families of the metropolis, its price had gone up to three times the usual figure. “But,” he added, “two days ago several large consignments arrived, and the price went down again, so that the late comers have lost their market.” Poor Wang was thus left in the lurch, and as every day more summer cloth came in, the value of it fell in a corresponding ratio. Wang would not part with his at a loss, and held on for some ten days, when his expenses for board and lodging were added to his present distress. The landlord urged him to sell even at a loss, and turn his attention to something else, which he ultimately did, losing over ten ounces of silver on his venture. Next day he rose in the morning to depart, but on looking in his purse found all his money gone. He rushed away to tell the landlord, who, however, could do nothing for him. Some one then advised him to take out a summons and make the landlord reimburse him; but he only sighed, and said, “It is my destiny, and no fault of the landlord’s.” Thereupon the landlord was very grateful to him, and gave him five ounces of silver to enable him to go home. He did not care, however, to face his grandmother empty-handed, and remained in a very undecided state, until suddenly he saw a quail- catcher winning heaps of money by fighting his birds, and selling them at over 100 cash a-piece. He then determined to lay out his five ounces of silver in quails, and pay back the landlord out of the profits. The latter approved very highly of this plan, and not only agreed to lend him a room but also to charge him little or nothing for his board. So Wang went off rejoicing, and bought two large baskets of quails, with which he returned to the city, to the great satisfaction of the landlord who advised him to lose no time in disposing of them. All that night it poured in torrents, and the next
- 60. morning the streets were like rivers, the rain still continuing to fall. Wang waited for it to clear up, but several days passed and still there were no signs of fine weather. He then went to look at his quails, some of which he found dead and others dying. He was much alarmed at this, but was quite at a loss what to do; and by the next day a lot more had died, so that only a few were left, which he fed all together in one basket. The day after this he went again to look at them, and lo! there remained but a single quail. With tears in his eyes he told the landlord what had happened, and he, too, was much affected. Wang then reflected that he had no money left to carry him home, and that he could not do better than cease to live. But the landlord spoke to him and soothed him, and they went together to look at the quail. “This is a fine bird,” said the landlord, “and it strikes me that it has simply killed the others. Now, as you have got nothing to do, just set to work and train it; and if it is good for anything, why you’ll be able to make a living out of it.” Wang did as he was told; and when the bird was trained, the landlord bade him take it into the street and gamble for something to eat. This, too, he did, and his quail won every main; whereupon the landlord gave him some money to bet with the young fellows of the neighbourhood. Everything turned out favourably, and by the end of six months he had saved twenty ounces of silver, so that he became quite easy in his mind and looked upon the quail as a dispensation of his destiny. Now one of the princes was passionately fond of quail-fighting, and always at the Feast of Lanterns anybody who owned quails might go and fight them in the palace against the prince’s birds. The landlord therefore said to Wang, “Here is a chance of enriching yourself by a single stroke; only I can’t say what your luck will do for you.” He then explained to him what it was, and away they went
- 61. together, the landlord saying, “If you lose, burst out into lamentations; but if you are lucky enough to win, and the prince wishes, as he will, to buy your bird, don’t consent. If he presses you very much watch for a nod from me before you agree.” This settled, they proceeded to the palace where they found crowds of quail- fighters already on the ground; and then the prince came forth, heralds proclaiming to the multitude that any who wished to fight their birds might come up. Some man at once stepped forward, and the prince gave orders for the quails to be released; but at the first strike the stranger’s quail was knocked out of time. The prince smiled, and by-and-by won several more mains, until at last the landlord said, “Now’s our time,” and went up together with Wang. The Prince looked at their bird and said, “It has a fierce-looking eye and strong feathers. We must be careful what we are doing.” So he commanded his servants to bring out Iron Beak to oppose Wang’s bird; but, after a couple of strikes, the prince’s quail was signally defeated. He sent for a better bird, but that shared the same fate; and then he cried out, “Bring the Jade Bird from the palace!” In a little time it arrived, with pure white feathers like an egret, and an unusually martial appearance. Wang was much alarmed, and falling on his knees prayed to be excused this main, saying, “Your highness’s bird is too good. I fear lest mine should be wounded, and my livelihood be taken from me.” But the Prince laughed and said, “Go on. If your quail is killed I will make it up to you handsomely.” Wang then released his bird and the prince’s quail rushed at it at once; but when the Jade bird was close by, Wang’s quail awaited its coming head down and full of rage. The former made a violent peck at its adversary, and then sprung up to swoop down on it. Thus they went on up and down, backwards and forwards, until at length they got hold of each other, and the prince’s bird was beginning to show
- 62. signs of exhaustion. This enraged it all the more, and it fought more violently than ever; but soon a perfect snowstorm of feathers began to fall, and, with drooping wings, the Jade bird made its escape. The spectators were much moved by the result; and the prince himself, taking up Wang’s bird, examined it closely from beak to claws, finally asking if it was for sale. “My sole dependence,” replied Wang, “is upon this bird. I would rather not part with it.” “But,” said the prince, “if I give you as much as the capital, say of an ordinary tradesman, will not that tempt you?” Wang thought some time, and then answered, “I would rather not sell my bird; but as your highness has taken a fancy to it I will only ask enough to find me in food and clothes.” “How much do you want?” inquired the prince; to which Wang replied that he would take a thousand ounces of silver. “You fool!” cried the Prince; “do you think your bird is such a jewel as all that?” “If your highness,” said Wang, “does not think the bird a jewel, I value it more than that stone which was priced at fifteen cities.” “How so?” asked the prince. “Why,” said Wang, “I take my bird every day into the market-place. It there wins for me several ounces of silver, which I exchange for rice; and my family, over ten in number, has nothing to fear from either cold or hunger. What jewel could do that?” “You shall not lose anything,” replied the prince; “I will give you two hundred ounces.” But Wang would not consent, and then the prince added another hundred; whereupon Wang looked at the landlord, who, however, made no sign. Wang then offered to take nine hundred; but the prince ridiculed the idea of paying such a price for a quail, and Wang was preparing to take his leave with the bird, when the prince called him back, saying, “Here! here! I will give you six hundred. Take it or leave it as you please.” Wang here looked at the landlord, and the landlord remained motionless as before. However, Wang was satisfied himself
- 63. with this offer, and being afraid of missing his chance, said to his friend, “If I get this price for it I shall be quite content. If we go on haggling and finally come to no terms, that will be a very poor end to it all.” So he took the prince’s offer, and the latter, overjoyed, caused the money to be handed to him. Wang then returned with his earnings; but the landlord said to him, “What did I say to you? You were in too much of a hurry to sell. Another minute, and you would have got eight hundred.” When Wang got back he threw the money on the table and told the landlord to take what he liked; but the latter would not, and it was only after some pressing that he would accept payment for Wang’s board. Wang then packed up and went home, where he told his story and produced his silver to the great delight of all of them. The old lady counselled the purchase of a quantity of land, the building of a house, and the purchase of implements; and in a very short time they became a wealthy family. The old lady always got up early in the morning and made Wang attend to the farm, his wife to her spinning; and rated them soundly at any signs of laziness. The husband and wife henceforth lived in peace, and no longer abused each other, until at the expiration of three years the old lady declared her intention of bidding them adieu. They both tried to stop her, and with the aid of tears succeeded in persuading her; but the next day she had disappeared. [85]
- 64. XII. THE PAINTED SKIN. At T‘ai-yüan there lived a man named Wang. One morning he was out walking when he met a young lady carrying a bundle and hurrying along by herself. As she moved along with some difficulty, [86] Wang quickened his pace and caught her up, and found she was a pretty girl of about sixteen. Much smitten he inquired whither she was going so early, and no one with her. “A traveller like you,” replied the girl, “cannot alleviate my distress; why trouble yourself to ask?” “What distress is it?” said Wang; “I’m sure I’ll do anything I can for you.” “My parents,” answered she, “loved money, and they sold me as concubine into a rich family, where the wife was very jealous, and beat and abused me morning and night. It was more than I could stand, so I have run away.” Wang asked her where she was going; to which she replied that a runaway had no fixed place of abode. “My house,” said Wang, “is at no great distance; what do you say to coming there?” She joyfully acquiesced; and Wang, taking up her bundle, led the way to his house. Finding no one there, she asked Wang where his family were; to which he replied that that was only the library. “And a very nice place, too,” said she; “but if you are kind enough to wish to save my life, you mustn’t let it be known that I am here.” Wang promised he would not divulge her secret, and so she remained there for some days without anyone
- 65. knowing anything about it. He then told his wife, and she, fearing the girl might belong to some influential family, advised him to send her away. This, however, he would not consent to do; when one day, going into the town, he met a Taoist priest, who looked at him in astonishment, and asked him what he had met. “I have met nothing,” replied Wang. “Why,” said the priest, “you are bewitched; what do you mean by not having met anything?” But Wang insisted that it was so, and the priest walked away, saying, “The fool! Some people don’t seem to know when death is at hand.” This startled Wang, who at first thought of the girl; but then he reflected that a pretty young thing as she was couldn’t well be a witch, and began to suspect that the priest merely wanted to do a stroke of business. When he returned, the library door was shut, and he couldn’t get in, which made him suspect that something was wrong; and so he climbed over the wall, where he found the door of the inner room shut too. Softly creeping up, he looked through the window and saw a hideous devil, with a green face and jagged teeth like a saw, spreading a human skin upon the bed and painting it with a paint- brush. The devil then threw aside the brush, and giving the skin a shake out, just as you would a coat, threw it over its shoulders, when, lo! it was the girl. Terrified at this, Wang hurried away with his head down in search of the priest who had gone he knew not whither; subsequently finding him in the fields, where he threw himself on his knees and begged the priest to save him. “As to driving her away,” said the priest, “the creature must be in great distress to be seeking a substitute for herself; [87] besides, I could hardly endure to injure a living thing.” [88] However, he gave Wang a fly-brush, and bade him hang it at the door of the bedroom, agreeing to meet again at the Ch‘ing-ti temple. Wang went home, but did not dare enter the library; so he hung up the brush at the
- 66. bedroom door, and before long heard a sound of footsteps outside. Not daring to move, he made his wife peep out; and she saw the girl standing looking at the brush, afraid to pass it. She then ground her teeth and went away; but in a little while came back, and began cursing, saying, “You priest, you won’t frighten me. Do you think I am going to give up what is already in my grasp?” Thereupon, she tore the brush to pieces, and bursting open the door, walked straight up to the bed, where she ripped open Wang and tore out his heart, with which she went away. Wang’s wife screamed out, and the servant came in with a light; but Wang was already dead and presented a most miserable spectacle. His wife, who was in an agony of fright, hardly dared cry for fear of making a noise; and next day she sent Wang’s brother to see the priest. The latter got into a great rage, and cried out, “Was it for this that I had compassion on you, devil that you are?” proceeding at once with Wang’s brother to the house, from which the girl had disappeared without anyone knowing whither she had gone. But the priest, raising his head, looked all round, and said, “Luckily she’s not far off.” He then asked who lived in the apartments on the south side, to which Wang’s brother replied that he did; whereupon the priest declared that there she would be found. Wang’s brother was horribly frightened and said he did not think so; and then the priest asked him if any stranger had been to the house. To this he answered that he had been out to the Ch‘ing-ti temple and couldn’t possibly say; but he went off to inquire, and in a little while came back and reported that an old woman had sought service with them as a maid-of-all-work, and had been engaged by his wife. “That is she,” said the priest, as Wang’s brother added she was still there; and they all set out to go to the house together. Then the priest took his wooden sword, and standing in the middle of the court-yard, shouted out, “Base-born
- 67. fiend, give me back my fly-brush!” Meanwhile the new maid-of-all- work was in a great state of alarm, and tried to get away by the door; but the priest struck her and down she fell flat, the human skin dropped off, and she became a hideous devil. There she lay grunting like a pig, until the priest grasped his wooden sword and struck off her head. She then became a dense column of smoke curling up from the ground, when the priest took an uncorked gourd and threw it right into the midst of the smoke. A sucking noise was heard, and the whole column was drawn into the gourd; after which the priest corked it up closely and put it in his pouch. [89] The skin, too, which was complete even to the eyebrows, eyes, hands, and feet, he also rolled up as if it had been a scroll, and was on the point of leaving with it, when Wang’s wife stopped him, and with tears entreated him to bring her husband to life. The priest said he was unable to do that; but Wang’s wife flung herself at his feet, and with loud lamentations implored his assistance. For some time he remained immersed in thought, and then replied, “My power is not equal to what you ask. I myself cannot raise the dead; but I will direct you to some one who can, and if you apply to him properly you will succeed.” Wang’s wife asked the priest who it was; to which he replied, “There is a maniac in the town who passes his time grovelling in the dirt. Go, prostrate yourself before him, and beg him to help you. If he insults you, shew no sign of anger.” Wang’s brother knew the man to whom he alluded, and accordingly bade the priest adieu, and proceeded thither with his sister-in-law. They found the destitute creature raving away by the road side, so filthy that it was all they could do to go near him. Wang’s wife approached him on her knees; at which the maniac leered at her, and cried out, “Do you love me, my beauty?” Wang’s wife told him what she had come for, but he only laughed and said, “You can get
- 68. plenty of other husbands. Why raise the dead one to life?” But Wang’s wife entreated him to help her; whereupon he observed, “It’s very strange: people apply to me to raise their dead as if I was king of the infernal regions.” He then gave Wang’s wife a thrashing with his staff, which she bore without a murmur, and before a gradually increasing crowd of spectators. After this he produced a loathsome pill which he told her she must swallow, but here she broke down and was quite unable to do so. However, she did manage it at last, and then the maniac crying out, “How you do love me!” got up and went away without taking any more notice of her. They followed him into a temple with loud supplications, but he had disappeared, and every effort to find him was unsuccessful. Overcome with rage and shame, Wang’s wife went home, where she mourned bitterly over her dead husband, grievously repenting the steps she had taken, and wishing only to die. She then bethought herself of preparing the corpse, near which none of the servants would venture; and set to work to close up the frightful wound of which he died. While thus employed, interrupted from time to time by her sobs, she felt a rising lump in her throat, which by-and-by came out with a pop and fell straight into the dead man’s wound. Looking closely at it, she saw it was a human heart; and then it began as it were to throb, emitting a warm vapour like smoke. Much excited, she at once closed the flesh over it, and held the sides of the wound together with all her might. Very soon, however, she got tired, and finding the vapour escaping from the crevices, she tore up a piece of silk and bound it round, at the same time bringing back circulation by rubbing the body and covering it up with clothes. In the night, she removed the coverings, and found that breath was coming from the nose; and by next morning her husband was alive again, though disturbed in mind as if awaking from a dream and feeling a pain in
- 69. his heart. Where he had been wounded, there was a cicatrix about as big as a cash, which soon after disappeared.
- 70. XIII. THE TRADER’S SON. In the province of Hunan there dwelt a man who was engaged in trading abroad; and his wife, who lived alone, dreamt one night that some one was in her room. Waking up, she looked about, and discovered a small creature which on examination she knew to be a fox; but in a moment the thing had disappeared, although the door had not been opened. The next evening she asked the cook-maid to come and keep her company; as also her own son, a boy of ten, who was accustomed to sleep elsewhere. Towards the middle of the night, when the cook and the boy were fast asleep, back came the fox; and the cook was waked up by hearing her mistress muttering something as if she had nightmare. The former then called out, and the fox ran away; but from that moment the trader’s wife was not quite herself. When night came she dared not blow out the candle, and bade her son be sure and not sleep too soundly. Later on, her son and the old woman having taken a nap as they leant against the wall, suddenly waked up and found her gone. They waited some time, but she did not return, and the cook was too frightened to go and look after her; so her son took a light, and at length found her fast asleep in another room. She didn’t seem aware that anything particular had happened, but she became queerer and queerer every day, and wouldn’t have either her son or the cook to keep her
- 71. company any more. Her son, however, made a point of running at once into his mother’s room if he heard any unusual sounds; and though his mother always abused him for his pains, he paid no attention to what she said. At the same time, the more people urged him on to keep a sharp look-out, the more eccentric were his mother’s ways. One day she played at being a mason, and piled up stones upon the window-sill, in spite of all that was said to her; and if anyone took away a stone, she threw herself on the ground, and cried like a child, so that nobody dared go near her. In a few days she had got both windows blocked up and the light excluded; and then she set to filling up the chinks with mud. She worked hard all day without minding the trouble, and when it was finished she smoothed it off with the kitchen chopper. Everyone who saw her was disgusted with such antics, and would take no notice of her. At night her son darkened his lamp, and, with a knife concealed on his person, sat waiting for his mother to mutter. As soon as she began he uncovered his light, and, blocking up the doorway, shouted out at the top of his voice. Nothing, however, happened, and he moved from the door a little way, when suddenly out rushed something like a fox, which was disappearing through the door, when he made a quick movement and cut off about two inches of its tail, from which the warm blood was still dripping as he brought the light to bear upon it. His mother hereupon cursed and reviled him, but he pretended not to hear her, regretting only as he went to bed that he hadn’t hit the brute fair. But he consoled himself by thinking that although he hadn’t killed it outright, he had done enough to prevent it coming again. On the morrow he followed the tracks of blood over the wall and into the garden of a family named Ho; and that night, to his great joy, the fox did not reappear. His mother was meanwhile prostrate, with hardly any life in her, and in the midst of it all his
- 72. father came home. The boy told him what had happened, at which he was much alarmed, and sent for a doctor to attend his wife; but she only threw the medicine away, and cursed and swore horribly. So they secretly mixed the medicine with her tea and soup, and in a few days she began to get better, to the inexpressible delight of both her husband and son. One night, however, her husband woke up and found her gone; and after searching for her with the aid of his son, they discovered her sleeping in another room. From that time she became more eccentric than ever, and was always being found in strange places, cursing those who tried to remove her. Her husband was at his wits’ end. It was no use keeping the door locked, for it opened of itself at her approach; and he had called in any number of magicians to exorcise the fox, but without obtaining the slightest result. One evening her son concealed himself in the Ho family garden, and lay down in the long grass with a view to detecting the fox’s retreat. As the moon rose he heard the sound of voices, and, pushing aside the grass, saw two people drinking, with a long-bearded servant pouring out their wine, dressed in an old dark-brown coat. They were whispering together, and he could not make out what they said; but by-and-by he heard one of them remark, “Get some white wine for to-morrow,” and then they went away, leaving the long-bearded servant alone. The latter then threw off his coat, and lay down to sleep on the stones; whereupon the trader’s son eyed him carefully, and saw that he was like a man in every respect except that he had a tail. The boy would then have gone home; but he was afraid the fox might hear him, and accordingly remained where he was till near dawn, when he saw the other two come back, one at a time, and then they all disappeared among the bushes. On reaching home his father asked him where he had been, and he replied that he had stopped the night with the
- 73. Ho family. He then accompanied his father to the town, where he saw hanging up at a hat-shop a fox’s tail, and finally, after much coaxing, succeeded in making his father buy it for him. While the latter was engaged in a shop, his son, who was playing about beside him, availed himself of a moment when his father was not looking and stole some money from him, and went off and bought a quantity of white wine, which he left in charge of the wine- merchant. Now an uncle of his, who was a sportsman by trade, lived in the city, and thither he next betook himself. His uncle was out, but his aunt was there, and inquired after the health of his mother. “She has been better the last few days,” replied he; “but she is now very much upset by a rat having gnawed a dress of hers, and has sent me to ask for some poison.” His aunt opened the cupboard and gave him about the tenth of an ounce in a piece of paper, which he thought was very little; so, when his aunt had gone to get him something to eat, he took the opportunity of being alone, opened the packet, and abstracted a large handful. Hiding this in his coat, he ran to tell his aunt that she needn’t prepare anything for him, as his father was waiting in the market, and he couldn’t stop to eat it. He then went off; and having quietly dropped the poison into the wine he had bought, went sauntering about the town. At nightfall he returned home, and told his father that he had been at his uncle’s. This he continued to do for some time, until one day he saw amongst the crowd his long-bearded friend. Marking him closely, he followed him, and at length entered into conversation, asking him where he lived. “I live at Pei-ts‘un,” said he; “where do you live?” “I,” replied the trader’s son, falsely, “live in a hole on the hill-side.” The long-bearded man was considerably startled at his answer, but much more so when he added, “We’ve lived there for generations: haven’t you?” The other then asked his name, to which the boy replied, “My
- 74. name is Hu. [90] I saw you with two gentlemen in the Ho family garden, and haven’t forgotten you.” Questioning him more fully, the long-bearded man was still in a half-and-half state of belief and doubt, when the trader’s son opened his coat a little bit, and showed him the end of the tail he had bought, saying, “The like of us can mix with ordinary people, but unfortunately we can never get rid of this.” The long-bearded man then asked him what he was doing there, to which he answered that his father had sent him to buy wine; whereupon the former remarked that that was exactly what he had come for, and the boy then inquired if he had bought it yet or not. “We are poor,” replied the stranger, “and as a rule I prefer to steal it.” “A difficult and dangerous job,” observed the boy. “I have my master’s instructions to get some,” said the other, “and what am I to do?” The boy then asked him who his masters were, to which he replied that they were the two brothers the boy had seen that night. “One of them has bewitched a lady named Wang; and the other, the wife of a trader who lives near. The son of the last-mentioned lady is a violent fellow, and cut off my master’s tail, so that he was laid up for ten days. But he is putting her under spells again now.” He was then going away, saying he should never get his wine; but the boy said to him, “It’s much easier to buy than steal. I have some at the wine-shop there which I will give to you. My purse isn’t empty, and I can buy some more.” The long-bearded man hardly knew how to thank him; but the boy said, “We’re all one family. Don’t mention such a trifle. When I have time I’ll come and take a drink with you.” So they went off together to the wine-shop, where the boy gave him the wine and they then separated. That night his mother slept quietly and had no fits, and the boy knew that something must have happened. He then told his father, and they went to see if there were any results; when lo! they found both foxes stretched out dead
- 75. in the arbour. One of the foxes was lying on the grass, and out of its mouth blood was still trickling. The wine-bottle was there; and on shaking it they heard that some was left. Then his father asked him why he had kept it all so secret; to which the boy replied that foxes were very sagacious, and would have been sure to scent the plot. Thereupon his father was mightily pleased, and said he was a perfect Ulysses [91] for cunning. They then carried the foxes home, and saw on the tail of one of them the scar of a knife-wound. From that time they were left in peace; but the trader’s wife became very thin, and though her reason returned, she shortly afterwards died of consumption. The other lady, Mrs. Wang, began to get better as soon as the foxes had been killed; and as to the boy, he was taught riding and archery [92] by his proud parent, and subsequently rose to high rank in the army.
- 76. XIV. JUDGE LU. At Ling-yang there lived a man named Chu Erh-tan, whose literary designation [93] was Hsiao-ming. He was a fine manly fellow, but an egregious dunce, though he tried hard to learn. One day he was taking wine with a number of fellow-students, when one of them said to him, by way of a joke, “People credit you with plenty of pluck. Now, if you will go in the middle of the night to the Chamber of Horrors, [94] and bring back the Infernal Judge from the left-hand porch, we’ll all stand you a dinner.” For at Ling-yang there was a representation of the Ten Courts of Purgatory, with the Gods and devils carved in wood, and almost life-like in appearance; and in the eastern vestibule there was a full-length image of the Judge with a green face, and a red beard, and a hideous expression in his features. Sometimes sounds of examination under the whip were heard to issue during the night from both porches, and persons who went in found their hair standing on end from fear; so the other young men thought it would be a capital test for Mr. Chu. Thereupon Chu smiled, and rising from his seat went straight off to the temple; and before many minutes had elapsed they heard him shouting outside, “His Excellency has arrived!” At this they all got up, and in came Chu with the image on his back, which he proceeded to deposit on the table, and then poured out a triple libation in its
- 77. honour. His comrades who were watching what he did, felt ill at ease, and did not like to resume their seats; so they begged him to carry the Judge back again. But he first poured some wine upon the ground, invoking the image as follows:—“I am only a fool-hardy, illiterate fellow: I pray Your Excellency excuse me. My house is close by, and whenever Your Excellency feels so disposed I shall be glad to take a cup of wine with you in a friendly way.” He then carried the Judge back, and the next day his friends gave him the promised dinner, from which he went home half-tipsy in the evening. But not feeling that he had had enough, he brightened up his lamp, and helped himself to another cup of wine, when suddenly the bamboo curtain was drawn aside, and in walked the Judge. Mr. Chu got up and said, “Oh, dear! Your Excellency has come to cut off my head for my rudeness the other night.” The Judge parted his thick beard, and smiling, replied, “Nothing of the kind. You kindly invited me last night to visit you; and as I have leisure this evening, here I am.” Chu was delighted at this, and made his guest sit down, while he himself wiped the cups and lighted a fire. [95] “It’s warm weather,” said the Judge; “let’s drink the wine cold.” Chu obeyed, and putting the bottle on the table, went out to tell his servants to get some supper. His wife was much alarmed when she heard who was there, and begged him not to go back; but he only waited until the things were ready, and then returned with them. They drank out of each other’s cups, [96] and by-and-by Chu asked the name of his guest. “My name is Lu,” replied the Judge; “I have no other names.” They then conversed on literary subjects, one capping the other’s quotation as echo responds to sound. The Judge then asked Chu if he understood composition; to which he answered that he could just tell good from bad; whereupon the former repeated a little infernal poetry which was not very different from that of mortals. He was a deep drinker,
- 78. and took off ten goblets at a draught; but Chu who had been at it all day, soon got dead drunk and fell fast asleep with his head on the table. When he waked up the candle had burnt out and day was beginning to break, his guest having already departed; and from this time the Judge was in the habit of dropping in pretty often, until a close friendship sprang up between them. Sometimes the latter would pass the night at the house, and Chu would show him his essays, all of which the Judge scored and underlined as being good for nothing. One night Chu got tipsy and went to bed first, leaving the Judge drinking by himself. In his drunken sleep he seemed to feel a pain in his stomach, and waking up he saw that the Judge, who was standing by the side of the bed, had opened him, and was carefully arranging his inside. “What harm have I done you?” cried Chu, “that you should thus seek to destroy me?” “Don’t be afraid,” replied the Judge, laughing, “I am only providing you with a more intelligent heart.” [97] He then quietly put back Chu’s viscera, and closed up the opening, securing it with a bandage tied tightly round his waist. There was no blood on the bed, and all Chu felt was a slight numbness in his inside. Here he observed the Judge place a piece of flesh upon the table, and asked him what it was. “Your heart,” said the latter, “which wasn’t at all good at composition, the proper orifice being stuffed up. [98] I have now provided you with a better one, which I procured from Hades, and I am keeping yours to put in its place.” [99] He then opened the door and took his leave. In the morning Chu undid the bandage, and looked at his waist, the wound on which had quite healed up, leaving only a red seam. From that moment he became an apt scholar, and found his memory much improved; so much so, that a few days afterwards he showed an essay to the Judge for which he was very much commended. “However,” said the latter, “your success will be limited to the
- 79. master’s degree. You won’t get beyond that.” “When shall I take it?” asked Chu. “This year,” replied the Judge. And so it turned out. Chu passed first on the list for the bachelor’s degree, and then among the first five for the master’s degree. His old comrades, who had been accustomed to make a laughing-stock of him, were now astonished to find him a full blown M.A., and when they learned how it had come about, they begged Chu to speak to the Judge on their behalf. The Judge promised to assist them, and they made all ready to receive him; but when in the evening he did come, they were so frightened at his red beard and flashing eyes that their teeth chattered in their heads, and one by one they stole away. Chu then took the Judge home with him to have a cup together, and when the wine had mounted well into his head, he said, “I am deeply grateful to Your Excellency’s former kindness in arranging my inside; but there is still another favour I venture to ask which possibly may be granted.” The Judge asked him what it was; and Chu replied, “If you can change a person’s inside, you surely could also change his face. Now my wife is not at all a bad figure, but she is very ugly. I pray Your Excellency try the knife upon her.” The Judge laughed, and said he would do so, only it would be necessary to give him a little time. Some days subsequently, the Judge knocked at Chu’s door towards the middle of the night; whereupon the latter jumped up and invited him in. Lighting a candle, it was evident that the Judge had something under his coat, and in answer to Chu’s inquiries, he said, “It’s what you asked me for. I have had great trouble in procuring it.” He then produced the head of a nice-looking young girl, and presented it to Chu, who found the blood on the neck was still warm. “We must make haste,” said the Judge, “and take care not to wake the fowls or dogs.” [100] Chu was afraid his wife’s door might be bolted; but the Judge laid his hand on it and it opened at once. Chu
- 80. then led him to the bed where his wife was lying asleep on her side; and the Judge, giving Chu the head to hold, drew from his boot a steel blade shaped like the handle of a spoon. He laid this across the lady’s neck, which he cut through as if it had been a melon, and the head fell over the back of the pillow. Seizing the head he had brought with him, he now fitted it on carefully and accurately, and pressing it down to make it stick, bolstered the lady up with pillows placed on either side. When all was finished, he bade Chu put his wife’s old head away, and then took his leave. Soon after Mrs. Chu waked up, and perceived a curious sensation about her neck, and a scaly feeling about the jaws. Putting her hand to her face, she found flakes of dry blood; and much frightened called a maid-servant to bring water to wash it off. The maid-servant was also greatly alarmed at the appearance of her face, and proceeded to wash off the blood, which coloured a whole basin of water; but when she saw her mistress’s new face she was almost frightened to death. Mrs. Chu took a mirror to look at herself, and was staring at herself in utter astonishment, when her husband came in and explained what had taken place. On examining her more closely, Chu saw that she had a well-featured pleasant face, of a medium order of beauty; and when he came to look at her neck, he found a red seam all round, with the parts above and below of a different coloured flesh. Now the daughter of an official named Wu was a very nice-looking girl who, though nineteen years of age, had not yet been married, two gentlemen who were engaged to her having died before the day. [101] At the Feast of Lanterns, [102] this young lady happened to visit the Chamber of Horrors, whence she was followed home by a burglar, who that night broke into the house and killed her. Hearing a noise, her mother told the servant to go and see what was the matter; and the murder being thus discovered, every member of the family got
- 81. up. They placed the body in the hall, with the head alongside, and gave themselves up to weeping and wailing the livelong night. Next morning, when they removed the coverings, the corpse was there but the head had disappeared. The waiting-maids were accordingly flogged for neglect of duty, and consequent loss of the head, and Mr. Wu brought the matter to the notice of the Prefect. This officer took very energetic measures, but for three days no clue could be obtained; and then the story of the changed head in the Chu family gradually reached Mr. Wu’s ears. Suspecting something, he sent an old woman to make inquiries; and she at once recognised her late young mistress’s features, and went back and reported to her master. Thereupon Mr. Wu, unable to make out why the body should have been left, imagined that Chu had slain his daughter by magical arts, and at once proceeded to the house to find out the truth of the matter; but Chu told him that his wife’s head had been changed in her sleep, and that he knew nothing about it, adding that it was unjust to accuse him of the murder. Mr. Wu refused to believe this, and took proceedings against him; but as all the servants told the same story, the Prefect was unable to convict him. Chu returned home and took counsel with the Judge, who told him there would be no difficulty, it being merely necessary to make the murdered girl herself speak. That night Mr. Wu dreamt that his daughter came and said to him, “I was killed by Yang Ta-nien, of Su-ch‘i. Mr. Chu had nothing to do with it; but desiring a better-looking face for his wife, Judge Lu gave him mine, and thus my body is dead while my head still lives. Bear Chu no malice.” When he awaked, he told his wife, who had dreamt the same dream; and thereupon he communicated these facts to the officials. Subsequently, a man of that name was captured, who confessed under the bamboo that he had committed the crime; so Mr. Wu went off to Chu’s house, and asked to be
- 82. allowed to see his wife, regarding Chu from that time as his son-in- law. Mrs. Chu’s old head was fitted on to the young lady’s body, and the two parts were buried together. Subsequent to these events Mr. Chu tried three times for his doctor’s degree, but each time without success, and at last he gave up the idea of entering into official life. Then when thirty years had passed away, Judge Lu appeared to him one night, and said, “My friend, you cannot live for ever. Your hour will come in five days’ time.” Chu asked the Judge if he could not save him; to which he replied, “The decrees of Heaven cannot be altered to suit the purposes of mortals. Besides, to an intelligent man life and death are much the same. [103] Why necessarily regard life as a boon and death as a misfortune?” Chu could make no reply to this, and forthwith proceeded to order his coffin and shroud; [104] and then, dressing himself in his grave-clothes, yielded up the ghost. Next day, as his wife was weeping over his bier, in he walked at the front door, to her very great alarm. “I am now a disembodied spirit,” said Chu to her, “though not different from what I was in life; and I have been thinking much of the widow and orphan I left behind.” His wife, hearing this, wept till the tears ran down her face, Chu all the time doing his best to comfort her. “I have heard tell,” said she, “of dead bodies returning to life; and since your vital spark is not extinct, why does it not resume the flesh?” “The ordinances of Heaven,” replied her husband, “may not be disobeyed.” His wife here asked him what he was doing in the infernal regions; and he said that Judge Lu had got him an appointment as Registrar, with a certain rank attached, and that he was not at all uncomfortable. Mrs. Chu was proceeding to inquire further, when he interrupted her, saying, “The Judge has come with me; get some wine ready and something to eat.” He then hurried out, and his wife did as he had told her, hearing them
- 83. laughing and drinking in the guest chamber just like old times come back again. About midnight she peeped in, and found that they had both disappeared; but they came back once in every two or three days, often spending the night, and managing the family affairs as usual. Chu’s son was named Wei, and was about five years old; and whenever his father came he would take the little boy upon his knee. When he was about eight years of age, Chu began to teach him to read; and the boy was so clever that by the time he was nine he could actually compose. At fifteen he took his bachelor’s degree, without knowing all this time that he had no father. From that date Chu’s visits became less frequent, occurring not more than once or so in a month; until one night he told his wife that they were never to meet again. In reply to her inquiry as to whither he was going, he said he had been appointed to a far-off post, where press of business and distance would combine to prevent him from visiting them any more. The mother and son clung to him, sobbing bitterly; but he said, “Do not act thus. The boy is now a man, and can look after your affairs. The dearest friends must part some day.” Then, turning to his son, he added, “Be an honourable man, and take care of the property. Ten years hence we shall meet again.” With this he bade them farewell, and went away. Later on, when Wei was twenty-two years of age, he took his doctor’s degree, and was appointed to conduct the sacrifices at the Imperial tombs. On his way thither he fell in with a retinue of an official, proceeding along with all the proper insignia, [105] and, looking carefully at the individual sitting in the carriage, he was astonished to find that it was his own father. Alighting from his horse, he prostrated himself with tears at the side of the road; whereupon his father stopped and said, “You are well spoken of. I now take leave of this world.” Wei remained on the ground, not
- 84. daring to rise; and his father, urging on his carriage, hurried away without saying any more. But when he had gone a short distance, he looked back, and unloosing a sword from his waist, sent it as a present to his son, shouting out to him, “Wear this and you will succeed.” Wei tried to follow him; but, in an instant, carriage, retinue, and horses, had vanished with the speed of wind. For a long time his son gave himself up to grief, and then seizing the sword began to examine it closely. It was of exquisite workmanship, and on the blade was engraved this legend:—“Be bold, but cautious; round in disposition, square in action.” [106] Wei subsequently rose to high honours, and had five sons named Ch‘ên, Ch‘ien, Wu, Hun, and Shên. One night he dreamt that his father told him to give the sword to Hun, which he accordingly did; and Hun rose to be a Viceroy of great administrative ability.
- 85. XV. MISS YING-NING; OR, THE LAUGHING GIRL. At Lo-tien, in the province of Shantung, there lived a youth named Wang Tzŭ-fu, who had been left an orphan when quite young. He was a clever boy, and took his bachelor’s degree at the age of fourteen, being quite his mother’s pet, and not allowed by her to stray far away from home. One young lady to whom he had been betrothed having unhappily died, he was still in search of a wife when, on the occasion of the Feast of Lanterns, his cousin Wu asked him to come along for a stroll. But they had hardly got beyond the village before one of his uncle’s servants caught them up and told Wu he was wanted. The latter accordingly went back; but Wang, seeing plenty of nice girls about and being in high spirits himself, proceeded on alone. Amongst others, he noticed a young lady with her maid. She had just picked a sprig of plum-blossom, and was the prettiest girl he had ever heard of—a perfect bunch of smiles. He stared and stared at her quite regardless of appearances; and when she had passed by, she said to her maid, “That young fellow has a wicked look in his eyes.” As she was walking away, laughing and talking, the flower dropped out of her hand; and Wang, picking it up, stood there disconsolate as if he had lost his wits. He then went
- 86. home in a very melancholy mood; and, putting the flower under his pillow, lay down to sleep. He would neither talk nor eat; and his mother became very anxious about him, and called in the aid of the priests. [107] By degrees, he fell off in flesh and got very thin; and the doctor felt his pulse and gave him medicines to bring out the disease. Occasionally, he seemed bewildered in his mind, but in spite of all his mother’s inquiries would give no clue as to the cause of his malady. One day when his cousin Wu came to the house, Wang’s mother told him to try and find out what was the matter; and the former, approaching the bed, gradually and quietly led up to the point in question. Wang, who had wept bitterly at the sight of his cousin, now repeated to him the whole story, begging him to lend some assistance in the matter. “How foolish you are, cousin,” cried Wu; “there will be no difficulty at all, I’ll make inquiries for you. The girl herself can’t belong to a very aristocratic family to be walking alone in the country. If she’s not already engaged, I have no doubt we can arrange the affair; and even if she is unwilling, an extra outlay will easily bring her round. [108] You make haste and get well: I’ll see to it all.” Wang’s features relaxed when he heard these words; and Wu left him to tell his mother how the case stood, immediately setting on foot inquiries as to the whereabouts of the girl. All his efforts, however, proved fruitless, to the great disappointment of Wang’s mother; for since his cousin’s visit Wang’s colour and appetite had returned. In a few days Wu called again, and in answer to Wang’s questions falsely told him that the affair was settled. “Who do you think the young lady is?” said he. “Why, a cousin of ours, who is only waiting to be betrothed; and though you two are a little near, [109] I daresay the circumstances of the case will be allowed to overrule this objection.” Wang was overjoyed, and asked where she lived; so Wu had to tell another lie, and say, “On
- 87. the south-west hills, about ten miles from here.” Wang begged him again and again to do his best for him, and Wu undertook to get the betrothal satisfactorily arranged. He then took leave of his cousin, who from this moment was rapidly restored to health. Wang drew the flower from underneath his pillow, and found that, though dried up, the leaves had not fallen away. He often sat playing with this flower and thinking of the young lady; but by-and-by, as Wu did not reappear, he wrote a letter and asked him to come. Wu pleaded other engagements, being unwilling to go; at which Wang got in a rage and quite lost his good spirits; so that his mother, fearing a relapse, proposed to him a speedy betrothal in another quarter. Wang shook his head at this, and sat day after day waiting for Wu, until his patience was thoroughly exhausted. He then reflected that ten miles was no great distance, and that there was no particular reason for asking anybody’s aid; so, concealing the flower in his sleeve, he went off in a huff by himself without letting it be known. Having no opportunity of asking the way, he made straight for the hills; and after about ten miles walking found himself right in the midst of them, enjoying their exquisite verdure, but meeting no one, and with nothing better than mountain paths to guide him. Away down in the valley below, almost buried under a densely luxuriant growth of trees and flowers, he espied a small hamlet, and began to descend the hill and make his way thither. He found very few houses, and all built of rushes, but otherwise pleasant enough to look at. Before the door of one, which stood at the northern end of the village, were a number of graceful willow trees, and inside the wall plenty of peach and apricot trees, with tufts of bamboo between them, and birds chirping on the branches. As it was a private house he did not venture to go in, but sat down to rest himself on a huge smooth stone opposite the front door. By-and-by he heard a girl’s
- 88. voice from within calling out Hsiao-jung; and, noticing that it was a sweet-toned voice, set himself to listen, when a young lady passed with a bunch of apricot-flowers in her hand, and occupied in putting hair-pins into her downcast head. As soon as she raised her face she saw Wang, and stopped putting in hair-pins; then, smothering a laugh, picked a few flowers and ran in. Wang perceived to his intense delight that she was none other than his heroine of the Feast of Lanterns; but recollecting that he had no right to follow her in, was on the point of calling after her as his cousin. There was no one, however, in the street, and he was afraid lest he might have made a mistake; neither was there anybody at the door of whom he could make inquiries. So he remained there in a very restless state till the sun was well down in the west, and his hopes were almost at an end, forgetting all about food and drink. He then saw the young lady peep through the door, apparently very much astonished to find him still there; and in a few minutes out came an old woman leaning on a stick, who said to him, “Whence do you come, Sir? I hear you have been here ever since morning. What is it you want? Aren’t you hungry?” Wang got up, and making a bow, replied that he was in search of some relatives of his; but the old woman was deaf and didn’t catch what he said, so he had to shout it out again at the top of his voice. She asked him what their names were, but he was unable to tell her; at which she laughed and said, “It is a funny thing to look for people when you don’t know their names. I am afraid you are an unpractical gentleman. You had better come in and have something to eat; we’ll give you a bed and you can go back to- morrow and find out the names of the people you are in quest of.” Now Wang was just beginning to get hungry, and, besides, this would bring him nearer to the young lady; so he readily accepted and followed the old woman in. They walked along a paved path
- 89. Welcome to our website – the perfect destination for book lovers and knowledge seekers. We believe that every book holds a new world, offering opportunities for learning, discovery, and personal growth. That’s why we are dedicated to bringing you a diverse collection of books, ranging from classic literature and specialized publications to self-development guides and children's books. More than just a book-buying platform, we strive to be a bridge connecting you with timeless cultural and intellectual values. With an elegant, user-friendly interface and a smart search system, you can quickly find the books that best suit your interests. Additionally, our special promotions and home delivery services help you save time and fully enjoy the joy of reading. Join us on a journey of knowledge exploration, passion nurturing, and personal growth every day! ebookbell.com







![Programming Windows Azure
by Sriram Krishnan
Copyright © 2010 Sriram Krishnan. All rights reserved.
Printed in the United States of America.
Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472.
O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions
are also available for most titles (http://my.safaribooksonline.com). For more information, contact our
corporate/institutional sales department: 800-998-9938 or corporate@oreilly.com.
Editors: Mike Hendrickson and Laurel R.T. Ruma
Production Editor: Loranah Dimant
Copyeditor: Audrey Doyle
Proofreader: Stacie Arellano
Indexer: John Bickelhaupt
Cover Designer: Karen Montgomery
Interior Designer: David Futato
Illustrator: Robert Romano
Printing History:
May 2010: First Edition.
Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of
O’Reilly Media, Inc., Programming Windows Azure, the image of a dhole, and related trade dress are
trademarks of O’Reilly Media, Inc.
Many of the designations used by manufacturers and sellers to distinguish their products are claimed as
trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a
trademark claim, the designations have been printed in caps or initial caps.
While every precaution has been taken in the preparation of this book, the publisher and author assume
no responsibility for errors or omissions, or for damages resulting from the use of the information con-
tained herein.
TM
This book uses RepKover™, a durable and flexible lay-flat binding.
ISBN: 978-0-596-80197-7
[M]
1273086110](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-8-320.jpg)









































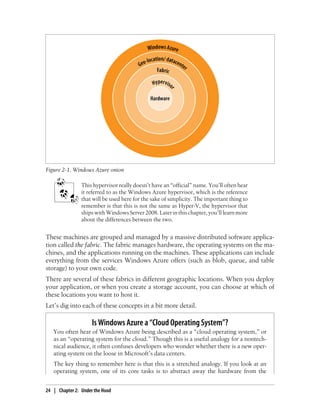





![XI.
THE FIGHTING QUAILS.
Wang Ch‘êng belonged to an old family in P‘ing-yüan, but was
such an idle fellow that his property gradually disappeared, until at
length all he had left was an old tumble-down house. His wife and
he slept under a coarse hempen coverlet, and the former was far
from sparing of her reproaches. At the time of which we are
speaking the weather was unbearably hot; and Wang went to pass
the night with many other of his fellow-villagers in a pavilion which
stood among some dilapidated buildings belonging to a family
named Chou. With the first streaks of dawn his comrades departed;
but Wang slept well on till about nine o’clock, when he got up and
proceeded leisurely home. All at once he saw in the grass a gold
hair-pin; and taking it up to look at it, found engraved thereon in
small characters—“The property of the Imperial family.” Now Wang’s
own grandfather had married into the Imperial family, [84]
and
consequently he had formerly possessed many similar articles; but
while he was thinking it over up came an old woman in search of the
hair-pin, which Wang, who though poor was honest, at once
produced and handed to her. The old woman was delighted, and
thanked Wang very much for his goodness, observing that the pin
was not worth much in itself, but was a relic of her departed
husband. Wang asked what her husband had been; to which she](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-56-320.jpg)






![with this offer, and being afraid of missing his chance, said to his
friend, “If I get this price for it I shall be quite content. If we go on
haggling and finally come to no terms, that will be a very poor end
to it all.” So he took the prince’s offer, and the latter, overjoyed,
caused the money to be handed to him. Wang then returned with
his earnings; but the landlord said to him, “What did I say to you?
You were in too much of a hurry to sell. Another minute, and you
would have got eight hundred.” When Wang got back he threw the
money on the table and told the landlord to take what he liked; but
the latter would not, and it was only after some pressing that he
would accept payment for Wang’s board. Wang then packed up and
went home, where he told his story and produced his silver to the
great delight of all of them. The old lady counselled the purchase of
a quantity of land, the building of a house, and the purchase of
implements; and in a very short time they became a wealthy family.
The old lady always got up early in the morning and made Wang
attend to the farm, his wife to her spinning; and rated them soundly
at any signs of laziness. The husband and wife henceforth lived in
peace, and no longer abused each other, until at the expiration of
three years the old lady declared her intention of bidding them
adieu. They both tried to stop her, and with the aid of tears
succeeded in persuading her; but the next day she had disappeared.
[85]](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-63-320.jpg)
![XII.
THE PAINTED SKIN.
At T‘ai-yüan there lived a man named Wang. One morning he
was out walking when he met a young lady carrying a bundle and
hurrying along by herself. As she moved along with some difficulty,
[86]
Wang quickened his pace and caught her up, and found she was
a pretty girl of about sixteen. Much smitten he inquired whither she
was going so early, and no one with her. “A traveller like you,”
replied the girl, “cannot alleviate my distress; why trouble yourself to
ask?” “What distress is it?” said Wang; “I’m sure I’ll do anything I
can for you.” “My parents,” answered she, “loved money, and they
sold me as concubine into a rich family, where the wife was very
jealous, and beat and abused me morning and night. It was more
than I could stand, so I have run away.” Wang asked her where she
was going; to which she replied that a runaway had no fixed place of
abode. “My house,” said Wang, “is at no great distance; what do you
say to coming there?” She joyfully acquiesced; and Wang, taking up
her bundle, led the way to his house. Finding no one there, she
asked Wang where his family were; to which he replied that that
was only the library. “And a very nice place, too,” said she; “but if
you are kind enough to wish to save my life, you mustn’t let it be
known that I am here.” Wang promised he would not divulge her
secret, and so she remained there for some days without anyone](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-64-320.jpg)
![knowing anything about it. He then told his wife, and she, fearing
the girl might belong to some influential family, advised him to send
her away. This, however, he would not consent to do; when one day,
going into the town, he met a Taoist priest, who looked at him in
astonishment, and asked him what he had met. “I have met
nothing,” replied Wang. “Why,” said the priest, “you are bewitched;
what do you mean by not having met anything?” But Wang insisted
that it was so, and the priest walked away, saying, “The fool! Some
people don’t seem to know when death is at hand.” This startled
Wang, who at first thought of the girl; but then he reflected that a
pretty young thing as she was couldn’t well be a witch, and began to
suspect that the priest merely wanted to do a stroke of business.
When he returned, the library door was shut, and he couldn’t get in,
which made him suspect that something was wrong; and so he
climbed over the wall, where he found the door of the inner room
shut too. Softly creeping up, he looked through the window and saw
a hideous devil, with a green face and jagged teeth like a saw,
spreading a human skin upon the bed and painting it with a paint-
brush. The devil then threw aside the brush, and giving the skin a
shake out, just as you would a coat, threw it over its shoulders,
when, lo! it was the girl. Terrified at this, Wang hurried away with
his head down in search of the priest who had gone he knew not
whither; subsequently finding him in the fields, where he threw
himself on his knees and begged the priest to save him. “As to
driving her away,” said the priest, “the creature must be in great
distress to be seeking a substitute for herself; [87]
besides, I could
hardly endure to injure a living thing.” [88]
However, he gave Wang a
fly-brush, and bade him hang it at the door of the bedroom,
agreeing to meet again at the Ch‘ing-ti temple. Wang went home,
but did not dare enter the library; so he hung up the brush at the](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-65-320.jpg)

![fiend, give me back my fly-brush!” Meanwhile the new maid-of-all-
work was in a great state of alarm, and tried to get away by the
door; but the priest struck her and down she fell flat, the human
skin dropped off, and she became a hideous devil. There she lay
grunting like a pig, until the priest grasped his wooden sword and
struck off her head. She then became a dense column of smoke
curling up from the ground, when the priest took an uncorked gourd
and threw it right into the midst of the smoke. A sucking noise was
heard, and the whole column was drawn into the gourd; after which
the priest corked it up closely and put it in his pouch. [89]
The skin,
too, which was complete even to the eyebrows, eyes, hands, and
feet, he also rolled up as if it had been a scroll, and was on the point
of leaving with it, when Wang’s wife stopped him, and with tears
entreated him to bring her husband to life. The priest said he was
unable to do that; but Wang’s wife flung herself at his feet, and with
loud lamentations implored his assistance. For some time he
remained immersed in thought, and then replied, “My power is not
equal to what you ask. I myself cannot raise the dead; but I will
direct you to some one who can, and if you apply to him properly
you will succeed.” Wang’s wife asked the priest who it was; to which
he replied, “There is a maniac in the town who passes his time
grovelling in the dirt. Go, prostrate yourself before him, and beg him
to help you. If he insults you, shew no sign of anger.” Wang’s
brother knew the man to whom he alluded, and accordingly bade
the priest adieu, and proceeded thither with his sister-in-law.
They found the destitute creature raving away by the road side,
so filthy that it was all they could do to go near him. Wang’s wife
approached him on her knees; at which the maniac leered at her,
and cried out, “Do you love me, my beauty?” Wang’s wife told him
what she had come for, but he only laughed and said, “You can get](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-67-320.jpg)






![name is Hu. [90]
I saw you with two gentlemen in the Ho family
garden, and haven’t forgotten you.” Questioning him more fully, the
long-bearded man was still in a half-and-half state of belief and
doubt, when the trader’s son opened his coat a little bit, and showed
him the end of the tail he had bought, saying, “The like of us can
mix with ordinary people, but unfortunately we can never get rid of
this.” The long-bearded man then asked him what he was doing
there, to which he answered that his father had sent him to buy
wine; whereupon the former remarked that that was exactly what he
had come for, and the boy then inquired if he had bought it yet or
not. “We are poor,” replied the stranger, “and as a rule I prefer to
steal it.” “A difficult and dangerous job,” observed the boy. “I have
my master’s instructions to get some,” said the other, “and what am
I to do?” The boy then asked him who his masters were, to which he
replied that they were the two brothers the boy had seen that night.
“One of them has bewitched a lady named Wang; and the other, the
wife of a trader who lives near. The son of the last-mentioned lady is
a violent fellow, and cut off my master’s tail, so that he was laid up
for ten days. But he is putting her under spells again now.” He was
then going away, saying he should never get his wine; but the boy
said to him, “It’s much easier to buy than steal. I have some at the
wine-shop there which I will give to you. My purse isn’t empty, and I
can buy some more.” The long-bearded man hardly knew how to
thank him; but the boy said, “We’re all one family. Don’t mention
such a trifle. When I have time I’ll come and take a drink with you.”
So they went off together to the wine-shop, where the boy gave him
the wine and they then separated. That night his mother slept
quietly and had no fits, and the boy knew that something must have
happened. He then told his father, and they went to see if there
were any results; when lo! they found both foxes stretched out dead](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-74-320.jpg)
![in the arbour. One of the foxes was lying on the grass, and out of its
mouth blood was still trickling. The wine-bottle was there; and on
shaking it they heard that some was left. Then his father asked him
why he had kept it all so secret; to which the boy replied that foxes
were very sagacious, and would have been sure to scent the plot.
Thereupon his father was mightily pleased, and said he was a
perfect Ulysses [91]
for cunning. They then carried the foxes home,
and saw on the tail of one of them the scar of a knife-wound. From
that time they were left in peace; but the trader’s wife became very
thin, and though her reason returned, she shortly afterwards died of
consumption. The other lady, Mrs. Wang, began to get better as
soon as the foxes had been killed; and as to the boy, he was taught
riding and archery [92]
by his proud parent, and subsequently rose to
high rank in the army.](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-75-320.jpg)
![XIV.
JUDGE LU.
At Ling-yang there lived a man named Chu Erh-tan, whose
literary designation [93]
was Hsiao-ming. He was a fine manly fellow,
but an egregious dunce, though he tried hard to learn. One day he
was taking wine with a number of fellow-students, when one of
them said to him, by way of a joke, “People credit you with plenty of
pluck. Now, if you will go in the middle of the night to the Chamber
of Horrors, [94]
and bring back the Infernal Judge from the left-hand
porch, we’ll all stand you a dinner.” For at Ling-yang there was a
representation of the Ten Courts of Purgatory, with the Gods and
devils carved in wood, and almost life-like in appearance; and in the
eastern vestibule there was a full-length image of the Judge with a
green face, and a red beard, and a hideous expression in his
features. Sometimes sounds of examination under the whip were
heard to issue during the night from both porches, and persons who
went in found their hair standing on end from fear; so the other
young men thought it would be a capital test for Mr. Chu. Thereupon
Chu smiled, and rising from his seat went straight off to the temple;
and before many minutes had elapsed they heard him shouting
outside, “His Excellency has arrived!” At this they all got up, and in
came Chu with the image on his back, which he proceeded to
deposit on the table, and then poured out a triple libation in its](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-76-320.jpg)
![honour. His comrades who were watching what he did, felt ill at
ease, and did not like to resume their seats; so they begged him to
carry the Judge back again. But he first poured some wine upon the
ground, invoking the image as follows:—“I am only a fool-hardy,
illiterate fellow: I pray Your Excellency excuse me. My house is close
by, and whenever Your Excellency feels so disposed I shall be glad to
take a cup of wine with you in a friendly way.” He then carried the
Judge back, and the next day his friends gave him the promised
dinner, from which he went home half-tipsy in the evening. But not
feeling that he had had enough, he brightened up his lamp, and
helped himself to another cup of wine, when suddenly the bamboo
curtain was drawn aside, and in walked the Judge. Mr. Chu got up
and said, “Oh, dear! Your Excellency has come to cut off my head
for my rudeness the other night.” The Judge parted his thick beard,
and smiling, replied, “Nothing of the kind. You kindly invited me last
night to visit you; and as I have leisure this evening, here I am.” Chu
was delighted at this, and made his guest sit down, while he himself
wiped the cups and lighted a fire. [95]
“It’s warm weather,” said the
Judge; “let’s drink the wine cold.” Chu obeyed, and putting the bottle
on the table, went out to tell his servants to get some supper. His
wife was much alarmed when she heard who was there, and begged
him not to go back; but he only waited until the things were ready,
and then returned with them. They drank out of each other’s cups,
[96]
and by-and-by Chu asked the name of his guest. “My name is
Lu,” replied the Judge; “I have no other names.” They then
conversed on literary subjects, one capping the other’s quotation as
echo responds to sound. The Judge then asked Chu if he understood
composition; to which he answered that he could just tell good from
bad; whereupon the former repeated a little infernal poetry which
was not very different from that of mortals. He was a deep drinker,](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-77-320.jpg)
![and took off ten goblets at a draught; but Chu who had been at it all
day, soon got dead drunk and fell fast asleep with his head on the
table. When he waked up the candle had burnt out and day was
beginning to break, his guest having already departed; and from this
time the Judge was in the habit of dropping in pretty often, until a
close friendship sprang up between them. Sometimes the latter
would pass the night at the house, and Chu would show him his
essays, all of which the Judge scored and underlined as being good
for nothing. One night Chu got tipsy and went to bed first, leaving
the Judge drinking by himself. In his drunken sleep he seemed to
feel a pain in his stomach, and waking up he saw that the Judge,
who was standing by the side of the bed, had opened him, and was
carefully arranging his inside. “What harm have I done you?” cried
Chu, “that you should thus seek to destroy me?” “Don’t be afraid,”
replied the Judge, laughing, “I am only providing you with a more
intelligent heart.” [97]
He then quietly put back Chu’s viscera, and
closed up the opening, securing it with a bandage tied tightly round
his waist. There was no blood on the bed, and all Chu felt was a
slight numbness in his inside. Here he observed the Judge place a
piece of flesh upon the table, and asked him what it was. “Your
heart,” said the latter, “which wasn’t at all good at composition, the
proper orifice being stuffed up. [98]
I have now provided you with a
better one, which I procured from Hades, and I am keeping yours to
put in its place.” [99]
He then opened the door and took his leave. In
the morning Chu undid the bandage, and looked at his waist, the
wound on which had quite healed up, leaving only a red seam. From
that moment he became an apt scholar, and found his memory
much improved; so much so, that a few days afterwards he showed
an essay to the Judge for which he was very much commended.
“However,” said the latter, “your success will be limited to the](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-78-320.jpg)
![master’s degree. You won’t get beyond that.” “When shall I take it?”
asked Chu. “This year,” replied the Judge. And so it turned out. Chu
passed first on the list for the bachelor’s degree, and then among
the first five for the master’s degree. His old comrades, who had
been accustomed to make a laughing-stock of him, were now
astonished to find him a full blown M.A., and when they learned how
it had come about, they begged Chu to speak to the Judge on their
behalf. The Judge promised to assist them, and they made all ready
to receive him; but when in the evening he did come, they were so
frightened at his red beard and flashing eyes that their teeth
chattered in their heads, and one by one they stole away. Chu then
took the Judge home with him to have a cup together, and when the
wine had mounted well into his head, he said, “I am deeply grateful
to Your Excellency’s former kindness in arranging my inside; but
there is still another favour I venture to ask which possibly may be
granted.” The Judge asked him what it was; and Chu replied, “If you
can change a person’s inside, you surely could also change his face.
Now my wife is not at all a bad figure, but she is very ugly. I pray
Your Excellency try the knife upon her.” The Judge laughed, and said
he would do so, only it would be necessary to give him a little time.
Some days subsequently, the Judge knocked at Chu’s door towards
the middle of the night; whereupon the latter jumped up and invited
him in. Lighting a candle, it was evident that the Judge had
something under his coat, and in answer to Chu’s inquiries, he said,
“It’s what you asked me for. I have had great trouble in procuring it.”
He then produced the head of a nice-looking young girl, and
presented it to Chu, who found the blood on the neck was still
warm. “We must make haste,” said the Judge, “and take care not to
wake the fowls or dogs.” [100]
Chu was afraid his wife’s door might be
bolted; but the Judge laid his hand on it and it opened at once. Chu](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-79-320.jpg)
![then led him to the bed where his wife was lying asleep on her side;
and the Judge, giving Chu the head to hold, drew from his boot a
steel blade shaped like the handle of a spoon. He laid this across the
lady’s neck, which he cut through as if it had been a melon, and the
head fell over the back of the pillow. Seizing the head he had
brought with him, he now fitted it on carefully and accurately, and
pressing it down to make it stick, bolstered the lady up with pillows
placed on either side. When all was finished, he bade Chu put his
wife’s old head away, and then took his leave. Soon after Mrs. Chu
waked up, and perceived a curious sensation about her neck, and a
scaly feeling about the jaws. Putting her hand to her face, she found
flakes of dry blood; and much frightened called a maid-servant to
bring water to wash it off. The maid-servant was also greatly
alarmed at the appearance of her face, and proceeded to wash off
the blood, which coloured a whole basin of water; but when she saw
her mistress’s new face she was almost frightened to death. Mrs.
Chu took a mirror to look at herself, and was staring at herself in
utter astonishment, when her husband came in and explained what
had taken place. On examining her more closely, Chu saw that she
had a well-featured pleasant face, of a medium order of beauty; and
when he came to look at her neck, he found a red seam all round,
with the parts above and below of a different coloured flesh. Now
the daughter of an official named Wu was a very nice-looking girl
who, though nineteen years of age, had not yet been married, two
gentlemen who were engaged to her having died before the day. [101]
At the Feast of Lanterns, [102]
this young lady happened to visit the
Chamber of Horrors, whence she was followed home by a burglar,
who that night broke into the house and killed her. Hearing a noise,
her mother told the servant to go and see what was the matter; and
the murder being thus discovered, every member of the family got](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-80-320.jpg)

![allowed to see his wife, regarding Chu from that time as his son-in-
law. Mrs. Chu’s old head was fitted on to the young lady’s body, and
the two parts were buried together.
Subsequent to these events Mr. Chu tried three times for his
doctor’s degree, but each time without success, and at last he gave
up the idea of entering into official life. Then when thirty years had
passed away, Judge Lu appeared to him one night, and said, “My
friend, you cannot live for ever. Your hour will come in five days’
time.” Chu asked the Judge if he could not save him; to which he
replied, “The decrees of Heaven cannot be altered to suit the
purposes of mortals. Besides, to an intelligent man life and death are
much the same. [103]
Why necessarily regard life as a boon and death
as a misfortune?” Chu could make no reply to this, and forthwith
proceeded to order his coffin and shroud; [104]
and then, dressing
himself in his grave-clothes, yielded up the ghost. Next day, as his
wife was weeping over his bier, in he walked at the front door, to her
very great alarm. “I am now a disembodied spirit,” said Chu to her,
“though not different from what I was in life; and I have been
thinking much of the widow and orphan I left behind.” His wife,
hearing this, wept till the tears ran down her face, Chu all the time
doing his best to comfort her. “I have heard tell,” said she, “of dead
bodies returning to life; and since your vital spark is not extinct, why
does it not resume the flesh?” “The ordinances of Heaven,” replied
her husband, “may not be disobeyed.” His wife here asked him what
he was doing in the infernal regions; and he said that Judge Lu had
got him an appointment as Registrar, with a certain rank attached,
and that he was not at all uncomfortable. Mrs. Chu was proceeding
to inquire further, when he interrupted her, saying, “The Judge has
come with me; get some wine ready and something to eat.” He then
hurried out, and his wife did as he had told her, hearing them](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-82-320.jpg)
![laughing and drinking in the guest chamber just like old times come
back again. About midnight she peeped in, and found that they had
both disappeared; but they came back once in every two or three
days, often spending the night, and managing the family affairs as
usual. Chu’s son was named Wei, and was about five years old; and
whenever his father came he would take the little boy upon his
knee. When he was about eight years of age, Chu began to teach
him to read; and the boy was so clever that by the time he was nine
he could actually compose. At fifteen he took his bachelor’s degree,
without knowing all this time that he had no father. From that date
Chu’s visits became less frequent, occurring not more than once or
so in a month; until one night he told his wife that they were never
to meet again. In reply to her inquiry as to whither he was going, he
said he had been appointed to a far-off post, where press of
business and distance would combine to prevent him from visiting
them any more. The mother and son clung to him, sobbing bitterly;
but he said, “Do not act thus. The boy is now a man, and can look
after your affairs. The dearest friends must part some day.” Then,
turning to his son, he added, “Be an honourable man, and take care
of the property. Ten years hence we shall meet again.” With this he
bade them farewell, and went away.
Later on, when Wei was twenty-two years of age, he took his
doctor’s degree, and was appointed to conduct the sacrifices at the
Imperial tombs. On his way thither he fell in with a retinue of an
official, proceeding along with all the proper insignia, [105]
and,
looking carefully at the individual sitting in the carriage, he was
astonished to find that it was his own father. Alighting from his
horse, he prostrated himself with tears at the side of the road;
whereupon his father stopped and said, “You are well spoken of. I
now take leave of this world.” Wei remained on the ground, not](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-83-320.jpg)
![daring to rise; and his father, urging on his carriage, hurried away
without saying any more. But when he had gone a short distance,
he looked back, and unloosing a sword from his waist, sent it as a
present to his son, shouting out to him, “Wear this and you will
succeed.” Wei tried to follow him; but, in an instant, carriage,
retinue, and horses, had vanished with the speed of wind. For a long
time his son gave himself up to grief, and then seizing the sword
began to examine it closely. It was of exquisite workmanship, and on
the blade was engraved this legend:—“Be bold, but cautious; round
in disposition, square in action.” [106]
Wei subsequently rose to high
honours, and had five sons named Ch‘ên, Ch‘ien, Wu, Hun, and
Shên. One night he dreamt that his father told him to give the sword
to Hun, which he accordingly did; and Hun rose to be a Viceroy of
great administrative ability.](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-84-320.jpg)

![home in a very melancholy mood; and, putting the flower under his
pillow, lay down to sleep. He would neither talk nor eat; and his
mother became very anxious about him, and called in the aid of the
priests. [107]
By degrees, he fell off in flesh and got very thin; and the
doctor felt his pulse and gave him medicines to bring out the
disease. Occasionally, he seemed bewildered in his mind, but in spite
of all his mother’s inquiries would give no clue as to the cause of his
malady. One day when his cousin Wu came to the house, Wang’s
mother told him to try and find out what was the matter; and the
former, approaching the bed, gradually and quietly led up to the
point in question. Wang, who had wept bitterly at the sight of his
cousin, now repeated to him the whole story, begging him to lend
some assistance in the matter. “How foolish you are, cousin,” cried
Wu; “there will be no difficulty at all, I’ll make inquiries for you. The
girl herself can’t belong to a very aristocratic family to be walking
alone in the country. If she’s not already engaged, I have no doubt
we can arrange the affair; and even if she is unwilling, an extra
outlay will easily bring her round. [108]
You make haste and get well:
I’ll see to it all.” Wang’s features relaxed when he heard these
words; and Wu left him to tell his mother how the case stood,
immediately setting on foot inquiries as to the whereabouts of the
girl. All his efforts, however, proved fruitless, to the great
disappointment of Wang’s mother; for since his cousin’s visit Wang’s
colour and appetite had returned. In a few days Wu called again,
and in answer to Wang’s questions falsely told him that the affair
was settled. “Who do you think the young lady is?” said he. “Why, a
cousin of ours, who is only waiting to be betrothed; and though you
two are a little near, [109]
I daresay the circumstances of the case will
be allowed to overrule this objection.” Wang was overjoyed, and
asked where she lived; so Wu had to tell another lie, and say, “On](https://image.slidesharecdn.com/1161950-250529061121-b347592c/85/Programming-Windows-Azure-Programming-The-Microsoft-Cloud-1st-Edition-Sriram-Krishnan-86-320.jpg)