Robots, Ninjas, Pirates and Building an Effective Vulnerability Management Program
- 1. Robots, Ninjas, Pirates and Building an Effective Vulnerability Management Program © Copyright Defensive Intuition, LLC 2004-2015 Paul Asadoorian Day: Product Strategist, Tenable Network Security Nights & Weekends: Founder & CEO, Security Weekly
- 2. © Copyright Defensive Intuition, LLC 2004-2015 Slide 2 About Paul
- 3. Agenda • Some slides with random pictures from the Internet • Paul talks about vulnerability management over said slides • Folks may have questions or challenge my thoughts/ideas (please do) • More random Internet pictures • Paul ranting a bit more while laughing at ridiculous pictures • These are the only bullets in this presentation… • End with tips on how to be successful © Copyright Defensive Intuition, LLC 2004-2015 Slide 3
- 4. Vulnerability Management… © Copyright Defensive Intuition, LLC 2004-2015 Slide 4 You have all the right tools…
- 5. A Robot, Ninja & Pirate Get Into a Fight, Who Wins? © Copyright Defensive Intuition, LLC 2004-2015 Slide 5 We have arguments like this all the time. ! Sometimes they center around vulnerability management…
- 6. Why Do We Need Vulnerability Management? © Copyright Defensive Intuition, LLC 2004-2015 Slide 6 You The Internet
- 7. Don’t Be Blind… You can’t fix what you don’t know is broken… © Copyright Defensive Intuition, LLC 2004-2015
- 8. Meet The Robots, Ninjas and Pirates in the Security Dept. © Copyright Defensive Intuition, LLC 2004-2015
- 9. The Robot Without a care in the world… © Copyright Defensive Intuition, LLC 2004-2015 “Going to scan the network!”
- 10. The Robot Cares even less how long the report will be… © Copyright Defensive Intuition, LLC 2004-2015 File -> Print… Reporting!!!!
- 11. The Robot What your network looks like after the scan… © Copyright Defensive Intuition, LLC 2004-2015
- 12. The Robot What the sysadmins, network admins, developers, help desk and operations are saying about you… © Copyright Defensive Intuition, LLC 2004-2015
- 13. Robots reporting to management © Copyright Defensive Intuition, LLC 2004-2015 “The chances of cross-site scripting being exploited are 725 to 1. Its quite possible the buffer overflow attacks aren’t quite stable.The odds of successfully surviving an attack on the Apache web server are…[Shut up 3po!].They’ve encased the web server in a WAF, it should be quite well protected, unless there is a bypass. I noticed the IPS pre-processor rules are damaged, its impossible to block attacks.”
- 14. Moral of the story… © Copyright Defensive Intuition, LLC 2004-2015
- 15. The Ninjas © Copyright Defensive Intuition, LLC 2004-2015 Wrote Nmap script to patch everything and disable TELNET.
- 16. The Report © Copyright Defensive Intuition, LLC 2004-2015
- 17. The Network Problems can be mysterious…. © Copyright Defensive Intuition, LLC 2004-2015
- 18. Sysadmins be like… Sysadmins be like… © Copyright Defensive Intuition, LLC 2004-2015
- 19. Ninjas be like… © Copyright Defensive Intuition, LLC 2004-2015
- 20. Pirates To find the booty… © Copyright Defensive Intuition, LLC 2004-2015 I’m gonna scan your network. Hard.
- 21. During the scan… © Copyright Defensive Intuition, LLC 2004-2015
- 22. The Report © Copyright Defensive Intuition, LLC 2004-2015 +
- 23. Pirate in meeting after report has been distributed © Copyright Defensive Intuition, LLC 2004-2015 Patch your shit! Aaaaaaaaaarrgh!! Pirates Lack Social Skillz
- 24. Sysadmins: Fear them… © Copyright Defensive Intuition, LLC 2004-2015
- 25. Meet the Robots, Ninja and Pirate Attackers © Copyright Defensive Intuition, LLC 2004-2015
- 26. Perception Of Scanning Even a broken clock is right twice a day © Copyright Defensive Intuition, LLC 2004-2015 “Your slave?” “You wish!You'll do shitwork, scan, crack copyrights…"
- 27. Attackers, like robots, automate… Attacks above are common, but less severe (typically) © Copyright Defensive Intuition, LLC 2004-2015
- 28. Or APT, or Cyber<something> © Copyright Defensive Intuition, LLC 2004-2015
- 29. Ninjas © Copyright Defensive Intuition, LLC 2004-2015
- 30. Cyber Pirate Attackers Pirates will steal bandwidth, often very loud. © Copyright Defensive Intuition, LLC 2004-2015
- 31. Now We Understand Some Of The Dynamics What we learned up to this point: ! Vulnerability Management is HARD, attackers will not let up. © Copyright Defensive Intuition, LLC 2004-2015
- 32. © Copyright Defensive Intuition, LLC 2004-2015 Slide 32 Shortcuts Are Trouble
- 33. “We’ll just scan once per quarter” ! “We can just use the default scan policy” ! “We can just scan parts of the network” © Copyright Defensive Intuition, LLC 2004-2015
- 34. © Copyright Defensive Intuition, LLC 2004-2015 “We don’t care about finding all the vulnerabilities. Just show me the important ones. I can’t fix everything, so don’t bother showing me everything.”
- 35. 5 Reasons Why This Will End Badly © Copyright Defensive Intuition, LLC 2004-2015
- 36. #1 What you don’t know will probably be the thing that hurts you © Copyright Defensive Intuition, LLC 2004-2015
- 37. #2 Ask any evil bad guy or penetration tester and they will tell you “we string together seemingly low severity vulnerabilities to achieve a goal” © Copyright Defensive Intuition, LLC 2004-2015 Example: Chris Gates from Low to Pwned (2012) https:// www.youtube.com/watch?v=u68QvWXYW_Q
- 38. #3 External conditions change, so not patching a vulnerabilities because there is no public exploit today doesn’t mean there will not be an exploit in the future (or someone has it already) © Copyright Defensive Intuition, LLC 2004-2015
- 39. #4 Internal conditions change. Not discovering vulnerabilities in XYZ software because you don’t use XYZ software is dangerous ! Someone could be installing XYZ software as we speak © Copyright Defensive Intuition, LLC 2004-2015
- 40. For Example… © Copyright Defensive Intuition, LLC 2004-2015
- 41. #5 Vulnerability management is a historical reference. ! You may not care which USB device were plugged into your systems today, but when malware spreads via USB devices tomorrow… © Copyright Defensive Intuition, LLC 2004-2015
- 42. Malware Here? © Copyright Defensive Intuition, LLC 2004-2015
- 43. ! “Just send them the raw results” ! “Just patch CVSS > 8.0” Goals & Results Matter… © Copyright Defensive Intuition, LLC 2004-2015
- 44. Results Matter, Don’t Be Lazy No one reads raw results © Copyright Defensive Intuition, LLC 2004-2015
- 45. Can You Make That 8 a 7? CVSS is subjective © Copyright Defensive Intuition, LLC 2004-2015
- 46. Vulnerability Management Goals © Copyright Defensive Intuition, LLC 2004-2015
- 47. Goal: Prevention – prevent bad things with the resources you have © Copyright Defensive Intuition, LLC 2004-2015 Stop waiting around for the perfect solution!
- 48. Goal: Detection ! Know where you are vulnerable and monitor © Copyright Defensive Intuition, LLC 2004-2015
- 49. Goal: React - Define priorities and enable people to take action Vulnerability management is a repeatable process. © Copyright Defensive Intuition, LLC 2004-2015
- 50. Goal: Do it yourself. ! Vulnerability scanning is not what a pen tester should do for you Tools have matured to allow for continuous scanning. © Copyright Defensive Intuition, LLC 2004-2015
- 51. Goal: Evaluate tools – Define the evaluation criteria Virtualization, Cloud, Mobile, Patch Management, Agents, Web Apps. © Copyright Defensive Intuition, LLC 2004-2015
- 52. Goal: Checks and Balances: How are my other defenses working or not? Anti-Virus, Firewalls, Compliance/System Hardening Programs © Copyright Defensive Intuition, LLC 2004-2015
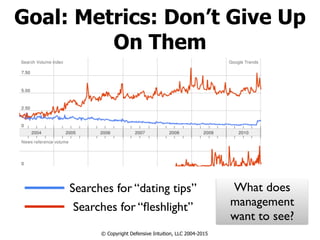
- 53. Goal: Metrics: Don’t Give Up On Them © Copyright Defensive Intuition, LLC 2004-2015 Searches for “dating tips” Searches for “fleshlight” What does management want to see?
- 54. Goal: Threat Modeling © Copyright Defensive Intuition, LLC 2004-2015
- 55. Goal: Don’t just find a standard or copy what may work for others Be a LEADER and set your own standards. © Copyright Defensive Intuition, LLC 2004-2015
- 56. Goal: Get people to understand and change their behavior Become a remarkable IT Security Leader © Copyright Defensive Intuition, LLC 2004-2015
- 57. Some Fun Facts Podcasts/Blogs/Videos: http://securityweekly.com Contact Me: [email protected] © Copyright Defensive Intuition, LLC 2004-2015 http://securityweekly.com/attend Security Weekly & Tenable are always hiring. ! You can some to our studio on Thursday nights and watch the show live. ! I post all my slides to http://slideshare.net/securityweekly ! Larry really does have a tattoo in “that place”. ! Jack is really old. ! Also, Ninja is the winner.













![Robots reporting to management
© Copyright Defensive Intuition, LLC 2004-2015
“The chances of cross-site scripting being
exploited are 725 to 1. Its quite possible the buffer
overflow attacks aren’t quite stable.The odds of
successfully surviving an attack on the Apache web server
are…[Shut up 3po!].They’ve encased the web server in a
WAF, it should be quite well protected, unless there is a
bypass. I noticed the IPS pre-processor rules are
damaged, its impossible to block attacks.”](https://image.slidesharecdn.com/robotsninjaspirates-vulnmgt-2015-150511135624-lva1-app6891/85/Robots-Ninjas-Pirates-and-Building-an-Effective-Vulnerability-Management-Program-13-320.jpg)