Schedule Based MAC Protocol
- 1. SCHEDULE BASED MAC PROTOCOLS Darwin Nesakumar A, M.E, (P.hD) Assistant Professor Department of ECE R.M.K. Engineering College
- 2. Agenda • Review of previous session • Scheduled based protocols in WSN • LEACH • SPIN • S-MACS • TRAMA • Quizzes 2Schedule based protocolsFriday, 28August 2020
- 3. Review of previous session • Joinmyquiz.com 3Schedule based protocolsFriday, 28August 2020
- 4. Question MAC stands for Schedule based protocols 4Friday, 28August 2020
- 5. Answer for the Question Medium Access Control Schedule based protocols 5Friday, 28August 2020
- 6. Question MAC is the part of which layer? Physical Layer Data Link Layer Application Layer Schedule based protocols 6Friday, 28August 2020
- 7. Answer for the Question Data Link Layer Schedule based protocols 7Friday, 28August 2020
- 8. Question There are trade offs between energy expenditure and __________ , throughput Delay Data Distance Schedule based protocols 8Friday, 28August 2020
- 9. Answer for the Question Delay Schedule based protocols 9Friday, 28August 2020
- 10. Question What is the energy saving approach? Schedule based protocols 10Friday, 28August 2020
- 11. Answer for the Question Switch the transceiver into sleep mode Schedule based protocols 11Friday, 28August 2020
- 12. Question What is the main issue in MAC Protocol? Schedule based protocols 12Friday, 28August 2020
- 13. Answer for the Question Energy Conservation Schedule based protocols 13Friday, 28August 2020
- 14. Question Energy waste due to Schedule based protocols 14Friday, 28August 2020
- 15. Answer for the Question Overhead Overhearing Collisions Idle listening Schedule based protocols 15Friday, 28August 2020
- 16. Question What are the two responsibilities of Data link Layer Schedule based protocols 16Friday, 28August 2020
- 17. Answer for the Question Error Control Flow Control Schedule based protocols 17Friday, 28August 2020
- 18. Question What are the two types of MAC Protocols? Schedule based protocols 18Friday, 28August 2020
- 19. Answer for the Question Contention based Schedule based Schedule based protocols 19Friday, 28August 2020
- 20. Question LLC stands for Schedule based protocols 20Friday, 28August 2020
- 21. Answer for the Question Logical Link Control layer Schedule based protocols 21Friday, 28August 2020
- 22. Question Provides a fraction of the frequency range to each user for all the time TDMA CDMA FDMA Schedule based protocols 22Friday, 28August 2020
- 23. Answer for the Question FDMA Schedule based protocols 23Friday, 28August 2020
- 24. Question Provides every user a portion of bandwidth for a fraction of time TDMA CDMA FDMA Schedule based protocols 24Friday, 28August 2020
- 25. Answer for the Question CDMA Schedule based protocols 25Friday, 28August 2020
- 26. Question MAC allows multiple users to share a ________ channel Common Single Schedule based protocols 26Friday, 28August 2020
- 27. Answer for the Question Common Schedule based protocols 27Friday, 28August 2020
- 28. Question What are the types of MAC protocols Schedule based protocols 28Friday, 28August 2020
- 29. Answer for the Question Fixed assignment protocols Demand assignment protocols Random access protocols Schedule based protocols 29Friday, 28August 2020
- 30. Question What are the methods to spread the bandwidth Schedule based protocols 30Friday, 28August 2020
- 31. Answer for the Question Direct Sequence (DS) Frequency Hoping (FH) Schedule based protocols 31Friday, 28August 2020
- 32. Question Random access protocols are Partially distributed Fully distributed No distributed Schedule based protocols 32Friday, 28August 2020
- 33. Answer for the Question Fully distributed Schedule based protocols 33Friday, 28August 2020
- 34. Question If the central node is bleached, the protocol is called BLEACH LEACH COACH Schedule based protocols 34Friday, 28August 2020
- 35. Answer for the Question LEACH Schedule based protocols 35Friday, 28August 2020
- 36. IMPORTANT POINTS TO BE REMEMBER MAC Protocols • MAC – Medium Access Control • They coordinate the times where a number of nodes access a shared communication medium. • Main requirement – Energy efficiency • Energy waste due to – Overhead, Overhearing, Collisions and idle listening • Switch the transceiver into Sleep Mode – Energy saving approach • There are trade offs between energy expenditure and delay, throughput • MAC is first protocol above the Physical layer (PHY) • Fundamental task is to regulate the access of number of nodes to a shared medium • Few traditional criteria are delay, throughput, fairness • Energy conservation is an issue in MAC • MAC is apart of Data Link Layer (DLL) – OSI reference model • MAC protocol determines for a node the points in time when it accesses the medium to try to transmit a data, control, or management packet to another node (unicast) or to a set of nodes (multicast, broadcast). 36Schedule based protocolsFriday, 28August 2020
- 37. IMPORTANT POINTS TO BE REMEMBER MAC Protocols • MAC is a part of Data Link Layer (DLL) • DLL Responsibilities are • Error Control – used to ensure correctness of transmission and to take appropriate actions in case of transmission errors • Flow control - regulates the rate of transmission to protect a slow receiver from being overwhelmed with data • Main approach to conserve energy – Put nodes in sleep state whenever possible • Low duty cycle, Wake up concepts • Two types of MAC Protocols are Contention based and schedule based • Contention based – It is a communication protocol for operating wireless telecommunication equipment that allows many users to use same radio channel without pre coordination • Schedule based - A schedule exists, regulating which participant may use which resource at which time 37Schedule based protocolsFriday, 28August 2020
- 38. Schedule- vs. contention-based MACs • Schedule-based MAC – A schedule exists, regulating which participant may use which resource at which time (TDMA component) – Typical resource: frequency band in a given physical space (with a given code, CDMA) – Schedule can be fixed or computed on demand • Usually: mixed – difference fixed/on demand is one of time scales – Usually, collisions, overhearing, idle listening no issues – Needed: time synchronization! • Contention-based protocols – Risk of colliding packets is deliberately taken – Hope: coordination overhead can be saved, resulting in overall improved efficiency – Mechanisms to handle/reduce probability/impact of collisions required – Usually, randomization used somehow 38Schedule based protocolsFriday, 28August 2020
- 39. Question What is needed in schedule based MACs Frequency Synchronization Time Synchronization Code Synchronization Schedule based protocols 39Friday, 28August 2020
- 40. Answer for the Question Time Synchronization Schedule based protocols 40Friday, 28August 2020
- 41. Question Risk of packet collisions occur in Schedule based MACs Contention based MACs Schedule based protocols 41Friday, 28August 2020
- 42. Answer for the Question Time Synchronization Schedule based protocols 42Friday, 28August 2020
- 43. Schedule based protocols A B C D Distributed, contention-based MAC • Basic ideas for a distributed MAC – ALOHA – no good in most cases – Listen before talk (Carrier Sense Multiple Access, CSMA) – better, but suffers from sender not knowing what is going on at receiver, might destroy packets despite first listening for a hidden terminal scenario 43Friday, 28August 2020
- 44. Receiver informs interferers before transmission • Sender B asks receiver C whether C is able to receive a transmission Request to Send (RTS) • Receiver C agrees, sends out a Clear to Send (CTS) • Potential interferers overhear either RTS / CTS and know about impending transmission and for how long it will last • Store this information in a Network Allocation Vector • B sends, C acks • MACA protocol (used e.g. in IEEE 802.11) A B C D RTS CTS Data Ack NAV indicates busy medium NAV indicates busy medium 44Schedule based protocolsFriday, 28August 2020
- 45. Main options to shut up senders • Receiver informs potential interferers while a reception is on-going – By sending out a signal indication – Problem: Cannot use same channel on which actual reception takes place ! Use separate channel for signaling – Busy tone protocol • Receiver informs potential interferers before a reception is on-going – Can use same channel – Receiver itself needs to be informed, by sender, about impending transmission – Potential interferers need to be aware of such information, need to store it 45Schedule based protocolsFriday, 28August 2020
- 46. Question The two options to shut up senders are to inform potential interferers while a reception is on-going and before a reception is on-going TRUE FALSE Schedule based protocols 46Friday, 28August 2020
- 47. Answer for the Question TRUE Schedule based protocols 47Friday, 28August 2020
- 48. RTS/CTS • RTS/CTS ameliorate, but do not solve hidden/exposed terminal problems • Example problem cases: A B C D RTS CTS Data A B C D RTS RTS CTS RTS RTS CTS CTSData Data Ack 48Schedule based protocolsFriday, 28August 2020
- 49. Schedule-based MAC Protocols 49Schedule based protocolsFriday, 28August 2020
- 50. Requirements for energy-efficient MAC protocols • Recall – Transmissions are costly – Receiving about as expensive as transmitting – Idling can be cheaper but is still expensive • Energy problems – Collisions – wasted effort when two packets collide – Overhearing – waste effort in receiving a packet destined for another node – Idle listening – sitting idly and trying to receive when nobody is sending – Protocol overhead • Always nice: Low complexity solution 50Schedule based protocolsFriday, 28August 2020
- 51. Schedule-based protocols Schedule-based protocols that do not explicitly address idle listening avoidance but do so implicitly. For example, by employing TDMA schemes, which explicitly assign transmission and reception opportunities to nodes and let them sleep at all other times. A second fundamental advantage of schedule-based protocols is that transmission schedules can be computed such that no collisions occur at receivers and hence no special mechanisms are needed to avoid hidden-terminal situations. 51Schedule based protocolsFriday, 28August 2020
- 52. However, these schemes also have downsides. First, the setup and maintenance of schedules involves signaling traffic. Second, if a TDMA variant is employed, time is divided into comparably small slots A third drawback is that such schedules are not easily adapted to different load situations on small timescales. A further disadvantage is that the schedule of a node (and possibly those of its neighbors) may require a significant amount of memory, which is a scarce resource in several sensor node designs. 52Schedule based protocolsFriday, 28August 2020
- 53. Low-Energy Adaptive Clustering Hierarchy (LEACH) • Given: Dense network of nodes, reporting to a central sink, each node can reach sink directly • Idea: Group nodes into “clusters”, controlled by clusterhead – About 5% of nodes become clusterhead (depends on scenario) – Role of clusterhead is rotated to share the burden – Clusterheads advertise themselves, ordinary nodes join CH with strongest signal – Clusterheads organize • CDMA code for all member transmissions • TDMA schedule to be used within a cluster • In steady state operation – CHs collect & aggregate data from all cluster members – Report aggregated data to sink using CDMA 53Schedule based protocolsFriday, 28August 2020
- 54. Question Clusterhead uses FDMA TRUE FALSE Schedule based protocols 54Friday, 28August 2020
- 55. Answer for the Question FALSE Schedule based protocols 55Friday, 28August 2020
- 56. Question Role of clusterhead is _____________ to share the burden Distributed Rotated Converged Schedule based protocols 56Friday, 28August 2020
- 57. Answer for the Question Rotated Schedule based protocols 57Friday, 28August 2020
- 58. Question What is the percentage of nodes to become clusterhead? Schedule based protocols 58Friday, 28August 2020
- 59. Answer for the Question 5% Schedule based protocols 59Friday, 28August 2020
- 60. • Set-up phase • Cluster heads assign a TDMA schedule for their members where each node is assigned a time slot when it can transmit. • Each cluster communications using different CDMA codes to reduce interference from nodes belonging to other clusters. • TDMA intra-cluster • CDMA inter-cluster • Spreading codes determined randomly • Broadcast during advertisement phase • In steady state operation – CHs collect & aggregate data from all cluster members – Report aggregated data to sink using CDMA 60Schedule based protocolsFriday, 28August 2020
- 61. LEACH rounds Setup phase Steady-state phase Fixed-length round ……….. ……….. Advertisement phase Cluster setup phase Broadcast schedule Time slot 1 Time slot 2 Time slot n Time slot 1 …..….. ….. Clusterheads compete with CSMA Members compete with CSMA Self-election of clusterheads 61Schedule based protocolsFriday, 28August 2020
- 62. Question Inter cluster uses TDMA CDMA Schedule based protocols 62Friday, 28August 2020
- 63. Answer for the Question CDMA Schedule based protocols 63Friday, 28August 2020
- 64. Question Which transmission is used in advertisement phase? Unicast Multicast Broadcast Schedule based protocols 64Friday, 28August 2020
- 65. Answer for the Question Broadcast Schedule based protocols 65Friday, 28August 2020
- 66. Question TDMA is being used for Intra Cluster Inter Cluster Schedule based protocols 66Friday, 28August 2020
- 67. Answer for the Question Intra Cluster Schedule based protocols 67Friday, 28August 2020
- 68. The LEACH protocol (Low-energy Adaptive Clustering Hierarchy) The LEACH protocol (Low-energy Adaptive Clustering Hierarchy) assumes a dense sensor network of homogeneous, energy- constrained nodes, which shall report their data to a sink node. The reason we need network protocol such as LEACH is due to the fact that a node in the network is no longer useful when its battery dies This protocol allows us to space out the lifespan of the nodes, allowing it to do only the minimum work it needs to transmit data 68Schedule based protocolsFriday, 28August 2020
- 69. Question LEACH stands for Schedule based protocols 69Friday, 28August 2020
- 70. Answer for the Question Low-energy Adaptive Clustering Hierarchy Schedule based protocols 70Friday, 28August 2020
- 71. The LEACH protocol (Low-energy Adaptive Clustering Hierarchy) In LEACH, a TDMA-based MAC protocol is integrated with clustering and a simple “routing” protocol. LEACH partitions the nodes into clusters and in each cluster a dedicated node, the cluster head, is responsible for creating and maintaining a TDMA schedule; all the other nodes of a cluster are member nodes. 71Schedule based protocolsFriday, 28August 2020
- 72. 72Schedule based protocolsFriday, 28August 2020
- 73. • To all member nodes, TDMA slots are assigned, which can be used to exchange data between the member and the clusterhead. • There is no peer-to-peer communication. • With the exception of their time slots, the members can spend their time in sleep state. • The clusterhead aggregates the data of its members and transmits it to the sink node or to other nodes for further relaying. • Since the sink is often far away, the clusterhead must spend significant energy for this transmission. • For a member, it is typically much cheaper to reach the clusterhead than to transmit directly to the sink 73Schedule based protocolsFriday, 28August 2020 The LEACH protocol (Low-energy Adaptive Clustering Hierarchy)
- 74. The protocol is organized in rounds and each round is subdivided into a The Set-Up Phase Where cluster-heads are chosen The Steady-State phase The cluster-head is maintained When data is transmitted between nodes 74Schedule based protocolsFriday, 28August 2020 The LEACH protocol (Low-energy Adaptive Clustering Hierarchy)
- 75. • Advantages • Increases the lifetime of the network • Even drain of energy • Distributed, no global knowledge required • Energy saving due to aggregation by CHs • Disadvantages • LEACH assumes all nodes can transmit with enough power to reach BS if necessary (e.g., elected as CHs) • Each node should support both TDMA & CDMA • Need to do time synchronization • Nodes use single-hop communication • LEACH would not be able to cover large geographical areas of some square miles or more, because a clusterhead two miles away from the sink likely does not have enough energy to reach the sink at all, 75Schedule based protocolsFriday, 28August 2020
- 76. • Sensor Protocols for Information via Negotiation (SPIN) • A Negotiation-Based Protocols for Disseminating Information in Wireless Sensor Networks. • Dissemination is the process of distributing individual sensor observations to the whole network, treating all sensors as sink nodes • Replicate complete view of the environment • Enhance fault tolerance • Broadcast critical piece of information SPIN -Sensor Protocols for Information via Negotiation 76Schedule based protocolsFriday, 28August 2020
- 77. • Flooding is the classic approach for dissemination • Source node sends data to all neighbors • Receiving node stores and sends data to all its neighbors • Disseminate data quickly • Deficiencies • Implosion • Overlap • Resource blindness SPIN 77Schedule based protocolsFriday, 28August 2020
- 78. • Negotiation • Before transmitting data, nodes negotiate with each other to overcome implosion and overlap • Only useful information will be transferred • Observed data must be described by meta-data • Resource adaptation • Each sensor node has resource manager • Applications probe manager before transmitting or processing data • Sensors may reduce certain activities when energy is low SPIN 78Schedule based protocolsFriday, 28August 2020
- 79. • SPIN : A three-stage handshake protocol for point-to-point media • ADV – data advertisement • Node that has data to share can advertise this by transmitting an ADV with meta-data attached • REQ – request for data • Node sends a request when it wishes to receive some actual data • DATA – data message • Contain actual sensor data with a meta-data header • Usually much bigger than ADV or REQ messages SPIN (cont.) 79Schedule based protocolsFriday, 28August 2020
- 80. SPIN Protocol 80Schedule based protocolsFriday, 28August 2020
- 81. The mediation device protocol It is compatible with the peer-to-peer communication mode It allows each node to go into sleep mode periodically and to wake up only for short times There is no global time reference, each node has its own sleeping schedule, and does not take care of its neighbors sleep schedules. 81Schedule based protocolsFriday, 28August 2020
- 82. Upon each periodic wakeup, a node transmits a short query beacon, indicating its node address and its willingness to accept packets from other nodes. When a node wants to transmit a packet to a neighbor, it has to synchronize with it. The dynamic synchronization approach achieves this synchronization without requiring the transmitter to be awake permanently to detect the destinations query beacon. To achieve this, a mediation device (MD) is used. We first discuss the case where the mediation device is not energy constrained and can be active all the time. The mediation device protocol 82Schedule based protocolsFriday, 28August 2020
- 83. • Because of its full duty cycle, the mediation device can receive the query beacons from all nodes in its vicinity and learn their wakeup period Protocol • Sender A sends RTS to MD • MD stores this information • Receiver B sends query to MD • MD tells reciever B when to wake up • B sends CTS to A (now in sync) • A sends data • B acknowledges • B returns to old timing 83Schedule based protocolsFriday, 28August 2020
- 84. Advantages First, it does not require any time synchronization between the nodes, only the mediation device has to learn the periods of the nodes. Second, the protocol is asymmetric in the sense that most of the energy burden is shifted to the mediation device, which so far is assumed to be power unconstrained. 84Schedule based protocolsFriday, 28August 2020
- 85. Disadvantages The nodes transmit their query beacons without checking for ongoing transmissions If the wakeup periods are properly randomized and the node density is sufficiently low, this collision probability can be low too. However, in case of higher node densities or unwanted synchronization between the nodes, the number of collisions can be significant. A possible solution to this is the following: When the MD registers collisions, it might start to emit a dedicated reschedule control frame. 85Schedule based protocolsFriday, 28August 2020
- 86. Disadvantages All colliding nodes can hear this frame as long as the MD repeats it often enough. Reception of this frame causes each node to randomly pick a new period from a certain interval [a, b] indicated in the reschedule frame. If the MD continues to perceive collisions, it can enlarge the interval accordingly 86Schedule based protocolsFriday, 28August 2020
- 87. Main Drawbacks The mediation device is energy unconstrained, which does not conform to the idea of a “simply thrown out” wireless sensor network There are sufficient mediation devices to cover all nodes. The distributed mediation device protocol deals with these problems in a probabilistic manner. 87Schedule based protocolsFriday, 28August 2020
- 88. • MACA’s idle listening is particularly unsuitable if average data rate is low • Most of the time, nothing happens • Idea: Switch nodes off, ensure that neighboring nodes turn on simultaneously to allow packet exchange Sensor-MAC (S-MAC) • Only in these active periods, packet exchanges happen • Need to also exchange wakeup schedule between neighbors • When awake, essentially perform RTS/CTS • Use SYNCH, RTS, CTS phases Wakeup period Active period Sleep period For SYNCH For RTS For CTS 88Schedule based protocolsFriday, 28August 2020
- 89. S-MAC Synchronized islands • Nodes try to pick up schedule synchronization from neighboring nodes • If no neighbor found, nodes pick some schedule to start with • If additional nodes join, some node might learn about two different schedules from different nodes – “Synchronized islands” • To bridge this gap, it has to follow both schemes Time A A A A C C C C A B B B B D D D A C B D E E E EE E E 89Schedule based protocolsFriday, 28August 2020
- 90. Timeout-MAC (T-MAC) • In S-MAC, active period is of constant length • What if no traffic actually happens? • Nodes stay awake needlessly long • Idea: Prematurely go back to sleep mode when no traffic has happened for a certain time (=timeout) ! T-MAC • Adaptive duty cycle! • One ensuing problem: Early sleeping • C wants to send to D, but is hindered by transmission A! B A B C D CTS May not send Timeout, go back to sleep as nothing happened 90Schedule based protocolsFriday, 28August 2020
- 91. SMACS • Given: Many radio channels, superframes of known length (not necessarily in phase, but still time synchronization required!) • Goal: Set up directional links between neighboring nodes – Link: radio channel + time slot at both sender and receiver – Free of collisions at receiver – Channel picked randomly, slot is searched greedily until a collision-free slot is found • Receivers sleep and only wake up in their assigned time slots, once per superframe • In effect: a local construction of a schedule 91Schedule based protocolsFriday, 28August 2020
- 92. TRAMA • Nodes are synchronized • Time divided into cycles, divided into – Random access periods – Scheduled access periods • Nodes exchange neighborhood information – Learning about their two-hop neighborhood – Using neighborhood exchange protocol: In random access period, send small, incremental neighborhood update information in randomly selected time slots • Nodes exchange schedules – Using schedule exchange protocol – Similar to neighborhood exchange 92Schedule based protocolsFriday, 28August 2020
- 93. TRAMA – possible conflicts • When does a node have to receive? – Easy case: one-hop neighbor has won a time slot and announced a packet for it – But complications exist – compare example C A B D Prio 100 Prio 95 Prio 79 Prio 200 What does B believe? A thinks it can send B knows that D has higher priority in its 2- hop neighborhood! Rules for resolving such conflicts are part of TRAMA 93Schedule based protocolsFriday, 28August 2020
- 94. Comparison : TRAMA, S-MAC • Comparison between TRAMA & S-MAC – Energy savings in TRAMA depend on load situation – Energy savings in S-MAC depend on duty cycle – TRAMA (as typical for a TDMA scheme) has higher delay but higher maximum throughput than contention-based S-MAC • TRAMA disadvantage: substantial memory/CPU requirements for schedule computation 94Schedule based protocolsFriday, 28August 2020
- 95. • Directed diffusion consists of – Interest - Query which specifies what a user wants – Data - Collected information – Gradient • Direction and data-rate • Events start flowing towards the originators of interests – Reinforcement • After the sink starts receiving events, it reinforces at least one neighbor to draw down higher quality events Directed Diffusion 95Schedule based protocolsFriday, 28August 2020
- 96. Contention-based protocols If only one neighbor tries its luck, the packet goes through the channel. If two or more neighbors try their luck, these have to compete with each other and in unlucky cases, for example, due to hidden-terminal situations, a collision might occur, wasting energy for both transmitter and receiver. two important contention based protocols: (slotted) ALOHA and CSMA, along with mechanisms to solve the hidden-terminal problem. In the following sections, we discuss variations of these protocols with the goal to conserve energy. As opposed to some of the contention-based protocols having a periodic wakeup scheme the protocols described in this section have no idle listening avoidance and make no restrictions as to when a node can receive a packet. 96Schedule based protocolsFriday, 28August 2020
- 97. The PAMAS protocol (Power Aware Multiaccess with Signaling) Originally designed for ad hoc networks. It provides a detailed overhearing avoidance mechanism while it does not consider the idle listening problem. The protocol combines the busy-tone solution and RTS/CTS handshake similar to the MACA protocol A distinctive feature of PAMAS is that it uses two channels: Data channel (while the data channel is reserved for data packets) Control channel. (All the signaling packets (RTS, CTS, busy tones) are transmitted on the control channel. 97Schedule based protocolsFriday, 28August 2020
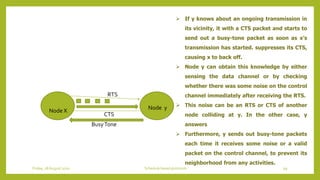
- 98. • first describing the main protocol operation and then discussing the power-conservation enhancements Node X Node y RTS CTS BusyTone • First, x sends an RTS packet on the control channel without doing any carrier sensing. This packet carries both x’s and y’s MAC addresses • If y receives this packet, it answers with a CTS packet if y does not know of any ongoing transmission in its vicinity. • Upon receiving the CTS, x starts to transmit the packet to y on the data channel. When y starts to receive the data, it sends out a busy-tone packet on the control channel. • If x fails to receive a CTS packet within some time window, it enters the backoff mode, where a binary exponential backoff scheme is used (i.e., the backoff time is uniformly chosen from a time interval that is doubled after each failure to receive a CTS) 98Schedule based protocolsFriday, 28August 2020
- 99. Node X Node y RTS CTS BusyTone If y knows about an ongoing transmission in its vicinity, it with a CTS packet and starts to send out a busy-tone packet as soon as x’s transmission has started. suppresses its CTS, causing x to back off. Node y can obtain this knowledge by either sensing the data channel or by checking whether there was some noise on the control channel immediately after receiving the RTS. This noise can be an RTS or CTS of another node colliding at y. In the other case, y answers Furthermore, y sends out busy-tone packets each time it receives some noise or a valid packet on the control channel, to prevent its neighborhood from any activities. 99Schedule based protocolsFriday, 28August 2020
- 100. When can a node put its transceivers (control and data) into sleep mode? Any time a node knows that it cannot transmit or receive packets because some other node in its vicinity is already doing so. This decision is easy if a node x knows about the length of an ongoing transmission, for example from overhearing the RTS or CTS packets or the header of the data packets on the data channel. However, often this length is unknown to x, for example, because these packets are corrupted or a foreign data transmission cycle starts when x is just sleeping. Additional procedures are needed to resolve this 100Schedule based protocolsFriday, 28August 2020
- 101. Suppose that x wakes up and finds the data channel busy. There are two cases to distinguish: either x has no own packet to send or x wants to transmit. In the first case, x desires to go back into sleep mode and to wake up exactly when the ongoing transmission ends to be able to receive an immediately following packet. Waking up at the earliest possible time has the advantage of avoiding unwanted delays. However, since x may not have overheard the RTS, CTS, or data packet header belonging to the ongoing transmission, it runs a probing protocol on the control channel to inquire the length of the ongoing packet. 101Schedule based protocolsFriday, 28August 2020
- 102. Demand Assignment Protocols • Resources are allocated on a short term basis • Centralized and distributed versions are possible • Central – Nodes request a reource (e.g. time slot) from a central server – Waits for ACK and then transmits – Polling by central station is possible – Central server to be switced on always – Central node requires a lot of energy – Central node may be rotated (LEACH) 102Schedule based protocolsFriday, 28August 2020
- 103. Distributed Demand Assignment Protocols • Token passing (IEEE 802.4) may be used • Token is passed among stations in a logical ring • Ring management needed – Include/exclude nodes from the ring – Correct lost tokens • In WSNs, maintenance is difficult – Channel errors – Node xceiver must be switched on all the time (energy ..) due to variable token delivery times 103Schedule based protocolsFriday, 28August 2020
- 104. Random Access Protocols • Fully distributed • ALOHA (more on this later) • CSMA based – Listen to the medium – If idle, xmit – If busy, wait (p persistent, non-persistent etc.) • RTS/CTS based on MACAW protocol (more later) 104Schedule based protocolsFriday, 28August 2020
- 105. Main options Wireless medium access Centralized Distributed Contention- based Schedule- based Fixed assignment Demand assignment Contention-basedSchedule-based Fixed assignment Demand assignment 105Schedule based protocolsFriday, 28August 2020
- 106. Centralized medium access • Idea: Have a central station control when a node may access the medium – Example: Polling, centralized computation of TDMA schedules – Advantage: Simple, quite efficient (e.g., no collisions), burdens the central station • Not directly feasible for non-trivial wireless network sizes • But: Can be quite useful when network is somehow divided into smaller groups – Clusters, in each cluster medium access can be controlled centrally – compare Bluetooth piconets, for example ! Usually, distributed medium access is considered 106Schedule based protocolsFriday, 28August 2020
- 107. • STEM • Sparse topology and energy management S-MAC sensor MAC T-MAC B-MAC Low duty cycle & Wakeup concepts 107Schedule based protocolsFriday, 28August 2020
- 108. Preamble Sampling • So far: Periodic sleeping supported by some means to synchronize wake up of nodes to ensure rendez-vous between sender and receiver • Alternative option: Don’t try to explicitly synchronize nodes – Have receiver sleep and only periodically sample the channel • Use long preambles to ensure that receiver stays awake to catch actual packet – Example: WiseMAC Check channel Check channel Check channel Check channel Start transmission: Long preamble Actual packet Stay awake! 108Schedule based protocolsFriday, 28August 2020
- 109. B-MAC • Combines several of the above discussed ideas – Takes care to provide practically relevant solutions • Clear Channel Assessment – Adapts to noise floor by sampling channel when it is assumed to be free – Samples are exponentially averaged, result used in gain control – For actual assessment when sending a packet, look at five channel samples – channel is free if even a single one of them is significantly below noise – Optional: random backoff if channel is found busy • Optional: Immediate link layer acknowledgements for received packets 109Schedule based protocolsFriday, 28August 2020
- 110. B-MAC II • Low Power Listening (= preamble sampling) – Uses the clear channel assessment techniques to decide whether there is a packet arriving when node wakes up – Timeout puts node back to sleep if no packet arrived • B-MAC does not have – Synchronization – RTS/CTS – Results in simpler, leaner implementation – Clean and simple interface • Currently: Often considered as the default WSN MAC protocol 110Schedule based protocolsFriday, 28August 2020
- 111. CONTENTION BASED PROTOCOLS 111Schedule based protocolsFriday, 28August 2020
- 112. PAMAS - Power Aware Multi access with Signaling • Idea: combine busy tone with RTS/CTS – Results in detailed overhearing avoidance, does not address idle listening – Uses separate data and control channels • Procedure – Node A transmits RTS on control channel, does not sense channel – Node B receives RTS, sends CTS on control channel if it can receive and does not know about ongoing transmissions – B sends busy tone as it starts to receive data Time Control channel Data channel RTS A ! B CTS B ! A Data A ! B Busy tone sent by B 112Schedule based protocolsFriday, 28August 2020
- 113. PAMAS – Already ongoing transmission • Suppose a node C in vicinity of A is already receiving a packet when A initiates RTS • Procedure – A sends RTS to B – C is sending busy tone (as it receives data) – CTS and busy tone collide, A receives no CTS, does not send data A B C ? Time Control channel Data channel RTS A ! B CTS B ! A No data! Busy tone by C Similarly:Ongoing transmission near B destroys RTS by busy tone 113Schedule based protocolsFriday, 28August 2020
- 114. Three categories • Data-centric • Hierarchical • Location based routing Classification of WSN routing protocols 114Schedule based protocolsFriday, 28August 2020
- 115. Classification of routing protocols 115Schedule based protocolsFriday, 28August 2020
- 116. • Natural information gradient • Gradient is known as fingerprint f ( d ) = t / d2. Regions • Flat region • Gradient region RoUting on finGerprint Gradient in sEnsor networks (RUGGED) 116Schedule based protocolsFriday, 28August 2020
- 117. • there could be multiple gradient regions active • A query may be initiated at any arbitrary node • If the node is in a flat region, • It uses flooding to forward the query • It sets the query mode to flat region mode • The query doesn’t switch to the gradient mode unless gradient information is found RoUting on finGerprint Gradient in sEnsor networks (RUGGED)-con 117Schedule based protocolsFriday, 28August 2020
- 118. • If the node is in gradient information region • Uses a greedy forwarding approach • well suited for broad range of applications • time gradient based target tracking, event boundary detection. RoUting on finGerprint Gradient in sEnsor networks (RUGGED)-con 118Schedule based protocolsFriday, 28August 2020
- 119. • Active query routed • Resolves query partially in each node • Next node can be selected randomly or selected intelligently based on other information • Query gets resolved as quickly as possible • Last active node answers the last remaining piece of the original query ACtive QUery forwarding In sensoR nEtworks (ACQUIRE) 119Schedule based protocolsFriday, 28August 2020
- 120. • Routing protocol is based on ANT colony • highly adaptive, efficient and scalable • ANTS travel through the WSN looking for path between sensor nodes and a destination node • that are both short in length and energy efficient An Energy Efficient ANT Based Routing algorithm (EEABR) 120Schedule based protocolsFriday, 28August 2020
- 121. • Forward (FANT) and backward ANTS (BANT). • A forward ANT is launched periodically from every node • ANT stores the identifiers of all the nodes it visits • selection probability is a trade-off between visibility(Energy) and actual trail intensity • BANT sent back along the path stored An Energy Efficient ANT Based Routing algorithm (EEABR)-con 121Schedule based protocolsFriday, 28August 2020
- 122. EECDA (Energy Efficient Clustering and Data Aggregation) Protocol After the CHs election, a path with maximum sum of residual energy would be selected for data communication instead of the path with minimum energy consumption. Therefore, each CH first aggregates the received data and then transmits the aggregated data to the Base Station (BS). The main contributions of EECDA protocol is to provide longest stability and improves the network lifetime 122Schedule based protocolsFriday, 28August 2020
- 123. Energy-Aware Unequal Clustering with Fuzzy (EAUCF) • EAUCF is a distributed competitive unequal clustering algorithm. It makes local decisions for determining competition radius and electing cluster-heads. In order to estimate the competition radius for tentative cluster-heads, EAUCF employs both residual energy and distance to the base station parameters. • EAUCF aims to decrease the work of the cluster-heads that are either close to the base station or have low remaining battery power. • A fuzzy logic approach is adopted in order to handle uncertainties in cluster-head radius estimation. 123Schedule based protocolsFriday, 28August 2020
- 124. THANK YOU 124Schedule based protocolsFriday, 28August 2020






















































































![Disadvantages
All colliding nodes can hear this frame as long as the MD repeats it often
enough.
Reception of this frame causes each node to randomly pick a new period
from a certain interval [a, b] indicated in the reschedule frame.
If the MD continues to perceive collisions, it can enlarge the interval
accordingly
86Schedule based protocolsFriday, 28August 2020](https://image.slidesharecdn.com/schedulebasedmacprotocol-200828065834/85/Schedule-Based-MAC-Protocol-86-320.jpg)