Script Fragmentation - Stephan Chenette - OWASP/RSA 2008
- 1. Script Fragmentation Attacks OWASP November 2008 Stephan Chenette, Security Researcher Websense Security Labs
- 2. Agenda What Web Developer 101 Web 1.0 versus Web 2.0 Malicious Web 1.0 Malicious Web 2.0 + Script Fragmentation Possible Solutions 2
- 3. What am I talking about today The success of any exploit depends on some basic assumptions: The vulnerable service or application is: 1) Active 2) Accessible The exploit is: 1) Reliable 2) Undetected 3
- 4. What am I talking about today This presentation will focus on: Evading detection of the exploit Specifically: A new evasion technique to avoid detection of client-side web exploitation (Browser, ActiveX control, etc bugs) 4
- 5. Basic Web Developer 101 HTML Browser Document Object Model (DOM) JavaScript/JSON Remote Requests - XMLHTTPRequest (XHR) Cross-Domains Requests - XDomainRequest (XDR) Available in: – Internet Explorer, Firefox – Safari, Opera and Konqeror, etc. 5
- 6. Basic HTML document and DOM <html> <body> <div id=“target” /> HTML </body> </html> <html> <body> <div id=“target” /> DOM </body> </html> 6
- 7. JavaScript can change DOM <script> var d = document.getElementById(“target”); var n = document.createElement(“script”); n.text = “alert(„test‟);” d.appendChild(n); </script> 7
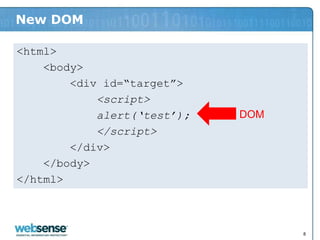
- 8. New DOM <html> <body> <div id=“target”> <script> alert(‘test’); DOM </script> </div> </body> </html> 8
- 9. Basic HTML document <html> <body> </body> </html> 9
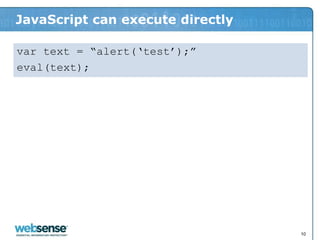
- 10. JavaScript can execute directly var text = “alert(„test‟);” eval(text); 10
- 11. DOM stays the same <html> <body> </body> </html> 11
- 12. The power of scripting var text=“ale” + “rt(“ + “„te” + “st‟” + “);” eval(text); 12
- 13. JSON Basics var text = { "firstName" : "John", "lastName" : "Doe" }; var JSONObj = eval(text); // Outputs John document.writeln(JSONObj.firstName); // Outputs Doe document.writeln(JSONObj.lastName); 13
- 14. XHR basics var client = new XMLHttpRequest(); client.onreadystatechange = handler; client.open("GET", "test.cgi"); client.send(); var client = new XMLHttpRequest(); client.open("POST", "/log"); client.setRequestHeader("Content-Type", "text/plain;charset=UTF-8"); client.send(message); 14
- 15. XDR requests (Cross-site requests) var xdr= new XDomainRequest(); Xdr.onload= handler; xdr.open("GET",“http://test.com/test.cgi"); xdr.send(); var xdr= new XMLHTTPRequest(); xdr.onload = handler; xdr.open("GET",“http://test.com/test.cgi"); xdr.send(); 15
- 16. Web 1.0 client/server communication •GET / HTTP/1.1 •Client Browser •Web Server 16
- 17. Web 2.0 Websites Client fetching content from multiple Servers + Servers receiving content from Client Benign JavaScript/HTTPXMLRequest technologies: – Gadgets – Widgets – Mashups Gmail, orkut, facebook, hi5.com, etc use JavaScript and XMLHTTPRequest. 17
- 18. Web 2.0 Websites •Client Browser •Web Server 18
- 19. Web attacks and defense Attack trends have shifted over the years. Intruders are focusing more prominently on the Web Most companies/users don‟t block HTTP at the firewall ALL Malicious client-side web attacks are assumed to be protected by desktop or gateway AV/IDS. 19
- 20. HTTP client/server communication •GET / HTTP/1.1 •Client Browser •Web Server 20
- 21. Current desktop/gateway protection Looking at initial content 21
- 22. Current evasion techniques Obfuscated JS code 22
- 23. REGEX for Deobfuscation routine for (fubatifi = 0; fubatifi < 1445; fubatifi++) fepab += String.fromCharCode(mosetib[fubatifi] ^ fedene); fors{0,5}(w{0,10}s{0,5}=s{0,5}0;s{0,5}w{0,10}s{0,5}<s{0 ,5}d{0,10};s{0,5}w{0,10}++)s{0,5}w{0,10}s{0,5}+=s{0,5 }String.fromCharCode(w{0,10}[w{0,10}]s{0,2}^s{0,2}w{ 0,10}); 23
- 24. Successful Evasion… Passing malicious content over the network has a higher chance of evading detection the indistinguishable it is from benign traffic. A.K.A. Make malicious web 2.0 traffic look like good web 2.0 traffic. 24
- 25. Malicious Web 2.0/Script Fragmentation Script Active Content e.g. JavaScript, VBscript, etc. Fragmentation Little chunks of data Note: The use of AJAX for malicious use was mentioned at Toorcon 2007, but not in the detail I‟m about to go in… 25
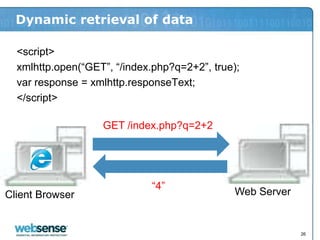
- 26. Dynamic retrieval of data <script> xmlhttp.open(“GET”, “/index.php?q=2+2”, true); var response = xmlhttp.responseText; </script> •GET /index.php?q=2+2 “4” •Client Browser •Web Server 26
- 27. Steps for script fragmentation attack 1. Store malicious content on server 2. SERVER: Serve client webpage with script fragmentation decoder routine. 3. CLIENT: Use XMLHTTPRequest object to request only small chunk of malicious content from server 4. SERVER: respond with requested chunk of malicious content 5. CLIENT: Use JavaScript variable to save chunks of data and continue to use JavaScript and XMLHTTPRequest object to request new chunk of data until there is no more data 6. CLIENT: Execute resulting code once all data is received 27
- 28. Steps in action Step 1) Store malicious content on server •Web Server 28
- 29. Steps in action Step 1) Store malicious content on server •Web Server 29
- 30. Steps in action Step 2) SERVER: Serve client webpage with script fragmentation decoder routine. •<DECODER> •Client Browser •Web Server 30
- 31. Script Fragmentation decoder routine 31
- 32. Steps in action Step 2) CLIENT: use XMLHTTPRequest object to request only small chunk of malicious content from server •GET /index.cgi?o=0&rl=3 •Client Browser •Web Server 32
- 33. Steps in action Step 3) SERVER: respond with requested chunk of malicious content •“var” •Client Browser •Web Server 33
- 34. Steps in action Step 4) CLIENT: store chunk and continually request more chunks until there is no more data. •GET /index.cgi?o=3&rl=3 •“ he” •Client Browser •Web Server •var text = “var he”; 34
- 35. Steps in action Step 4) CLIENT: store chunk and continually request more chunks until there is no more data. •GET /index.cgi?o=6&rl=3 •“apS” •Client Browser •Web Server •var text = “var heapS”; 35
- 36. Steps in action Step 4) CLIENT: store chunk and continually request more chunks until there is no more data. •GET /index.cgi?o=9&rl=3 •“pra” •Client Browser •Web Server •var text = “var heapSpra”; 36
- 37. Steps in action Step 4) CLIENT: store chunk and continually request more chunks until there is no more data. •GET /index.cgi?o=12&rl=3 •“yTo ” •Client Browser •Web Server •var text = “var heapSprayTo”; 37
- 38. Steps in action Step 5) CLIENT: execute resulting code once all data is received. •Client Browser •// Method 1 •// Method 2 •eval(text); •var div = GetElementById(„target‟); var n = document.CreateElement(“script”); n.text = text; div.appendChild(n); 38
- 39. The possibilities Beyond the basic script fragmentation attacks: Randomize sequence of offsets xor/encrypt data Spread data across multiple web servers (botnet) (XDR) In memory keep string encrypted until the last minute 39
- 40. Options for data transfer XMLHttpRequest is the object to make dynamic remote HTTP request, but there are multiple data formats that may be used for data transfer: RAW XML JSON etc.… 40
- 41. RAW data format •GET /index.cgi?o=0&rl=3&u=guid •Client Browser “var” •Web Server 41
- 42. XML data format •GET /index.cgi?o=0&rl=3 •Client Browser “<Data eof=“0” text=“var” />” •Web Server 42
- 43. JSON data format •GET /index.cgi?o=0&rl=3 “{ •Client Browser •Web Server eof : “0”, // S = server resp. text : “var” var data = eval(S); }” var text = data.text; 43
- 44. Flawlessly works on all major browsers Proof of concept (POC) exploited within 10-20s 44
- 45. AV won’t detect Script Fragmentations Initial page will hold decoder routine in script tag and then blank body. The file on disk will never change DOM in memory will never change NO SUBSTANTIAL CONTENT TO SCAN AS MALICIOUS! 45
- 46. HTML file on disk File on disk is the same before and after C:Documents and Settings<USER>Local SettingsTemporary Internet Files 46
- 47. Victory! Script Fragmentation is a very successful evasion attack that current desktop and gateway AV do not detect. 47
- 48. Ending remarks Reality: This attack is still a few years away We haven‟t seen this in the wild Possible Reasons: Dealing with scripting and obfuscation are still the biggest problems 48
- 49. Possible solutions Detecting the decoder routine Detecting network anomalies Using a “feedback loop” and executing in remote location. Dis-allow execution of content that comes from XMLHTTPRequest, hard to implement and would break functionality – so no go. Post-detection Hooking Browser internals Install security add-ons – NoScript, Flashblock, SafeHistory, Adblock Plus, LocalRodeo, CustomizeGoogle, etc. 49
- 50. Thank you. Any questions? Stephan Chenette, Websense Security Labs [email protected] Check out our website and blogs http://securitylabs.websense.com/content/blogs.aspx http://securitylabs.websense.com/ 50





















![REGEX for Deobfuscation routine
for (fubatifi = 0; fubatifi < 1445; fubatifi++)
fepab += String.fromCharCode(mosetib[fubatifi] ^ fedene);
fors{0,5}(w{0,10}s{0,5}=s{0,5}0;s{0,5}w{0,10}s{0,5}<s{0
,5}d{0,10};s{0,5}w{0,10}++)s{0,5}w{0,10}s{0,5}+=s{0,5
}String.fromCharCode(w{0,10}[w{0,10}]s{0,2}^s{0,2}w{
0,10});
23](https://image.slidesharecdn.com/scriptfragmentationowasp-13443002902427-phpapp01-120806194555-phpapp01/85/Script-Fragmentation-Stephan-Chenette-OWASP-RSA-2008-23-320.jpg)