Secure Programming With Static Analysis
2 likes1,477 views
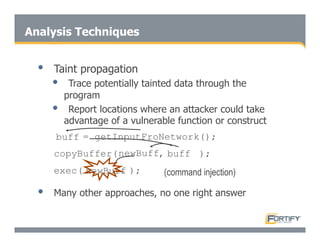
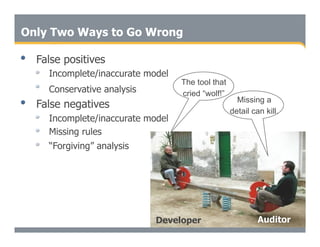
This document discusses the importance of static analysis for secure programming. It describes how static analysis tools work by analyzing code without executing it to find security vulnerabilities based on predefined rules. Good tools prioritize results by risk and provide easy-to-understand interfaces for programmers to review issues. The document recommends adopting static analysis by running tools regularly during development, focusing on high priority issues, and measuring outcomes to improve security over time. Static analysis is presented as a way to bring security expertise to all programmers and make code reviews more efficient.
1 of 48
Downloaded 165 times














































More Related Content
What's hot (20)
PDF
Root via SMS: 4G access level security assessment, Sergey Gordeychik, Alexand...Sergey GordeychikViewers also liked (18)
PDF
Determinants of Anemia in Antenatal Cases: A Cross-sectional Analysis International Multispeciality Journal of HealthDeterminants of Anemia in Antenatal Cases: A Cross-sectional Analysis International Multispeciality Journal of Health
Ad
Similar to Secure Programming With Static Analysis (20)
Ad
More from ConSanFrancisco123 (20)
Recently uploaded (20)
PDF
“Voice Interfaces on a Budget: Building Real-time Speech Recognition on Low-c...Edge AI and Vision AlliancePDF
“NPU IP Hardware Shaped Through Software and Use-case Analysis,” a Presentati...Edge AI and Vision Alliance“Voice Interfaces on a Budget: Building Real-time Speech Recognition on Low-c...Edge AI and Vision Alliance
“NPU IP Hardware Shaped Through Software and Use-case Analysis,” a Presentati...Edge AI and Vision Alliance