Secure your workloads with microsegmentation
1 like542 views
The document discusses the future of cyber security and securing workloads in hybrid and multi-cloud environments. It notes challenges around evolving threats, security operations, and compliance. It also discusses priorities for business executives around providing transparency, applying business context to network activity, and simplifying operations and compliance reporting. Methods for securing workloads mentioned include microsegmentation, threat control, and visibility.
1 of 5
Download to read offline




More Related Content
What's hot (20)
Similar to Secure your workloads with microsegmentation (20)
PDF
President Donald Trump - Cybersecurity - National Institute of Standards and ...Clifton M. Hasegawa & Associates, LLCPDF
Cisco Connect 2018 Thailand - Security automation and programmability mr. kho...NetworkCollaboratorsPresident Donald Trump - Cybersecurity - National Institute of Standards and ...Clifton M. Hasegawa & Associates, LLC
Cisco Connect 2018 Thailand - Security automation and programmability mr. kho...NetworkCollaborators
Ad
Recently uploaded (20)
PDF
Impact of IEEE Computer Society in Advancing Emerging Technologies including ...Hironori WashizakiAd
Secure your workloads with microsegmentation
- 1. Future of cyber security www.rasoolirfan.com Secure workloads with MicroSegmentation
- 2. Future of cyber security www.rasoolirfan.com Workload security challenges in Hybrid datacenter & Multi-Cloud environments Evolving Threats Security Operations Compliance • Manual process • Short on resources • Long provisioning times • Costly • Complex validation process • Detect, understand, and block
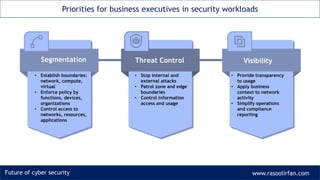
- 3. Future of cyber security www.rasoolirfan.com Priorities for business executives in security workloads • Provide transparency to usage • Apply business context to network activity • Simplify operations and compliance reporting Segmentation Threat Control Visibility • Establish boundaries: network, compute, virtual • Enforce policy by functions, devices, organizations • Control access to networks, resources, applications • Stop internal and external attacks • Patrol zone and edge boundaries • Control information access and usage
- 4. Future of cyber security www.rasoolirfan.com Segmentation Firewall Segmentation Context Aware Segmentation Fabric Segmentation Network Segmentation
- 5. Future of cyber security www.rasoolirfan.com Start your journey with #Application Visibility
