Securing Open Source Code in Enterprise
- 1. Securing Open Source Code in Enterprise Asankhaya Sharma
- 3. Projection: > 400M Libraries by 2026
- 4. Complexity of Libraries has exploded For every 1 Java library you add to your projects, 4 others are added For every one library you add to a Node.js project, 9 others are added
- 5. SourceClear Scan of apache/spark
- 7. Control Over What is in Your Code Has Changed Reference : http://anvaka.github.io/allnpmviz.an/ From YOU to: - Developer Tools - Open-Source Code - 3rd Party Developers
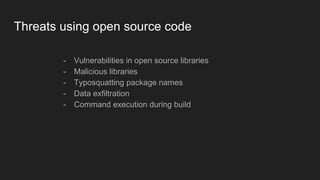
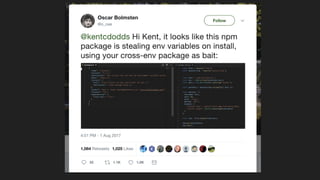
- 8. Threats using open source code - Vulnerabilities in open source libraries - Malicious libraries - Typosquatting package names - Data exfiltration - Command execution during build
- 14. Software Composition Analysis (SCA) Discover and identify software vulnerabilities and expose licenses for open source components Scanner Data
- 15. Scanning Technology App A v1.0 B v2.0 C v1.0 B v2.0 B v2.0 App A v1.0 B v2.0 C v1.0 Dependency Locked File Dependency GraphSCA Scanner
- 16. Scanning Technology App A v1.0 B v1.0 C v1.0 App A v1.0 B v2.0 C v1.0 Dependency File Dependency Graph App A v1.0 B v2.0 C v1.0 B v2.0 B v2.0 Resolved DependenciesSCA Scanner
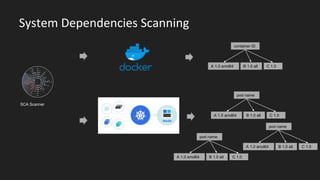
- 17. System Dependencies Scanning SCA Scanner container ID A 1.0 amd64 B 1.0 all C 1.0 pod name A 1.0 amd64 B 1.0 all C 1.0 pod name A 1.0 amd64 B 1.0 all C 1.0 pod name A 1.0 amd64 B 1.0 all C 1.0
- 18. Vulnerabilities in Open Source Libraries ● Known Sources ○ CVEs / NVD ○ Advisories ○ Mailing list disclosures ● Unidentified issues ○ Commit logs ○ Bug reports ○ Change logs ○ Pull Requests Security Issues are often not reported or publicly mentioned How do we get the data?
- 19. Mining for unidentified vulnerabilities
- 20. NLP and Machine Learning for Harvesting Data https://asankhaya.github.io/pdf/automated-identification-of-security-issues-fr om-commit-messages-and-bug-reports.pdf
- 21. SCA Vendors
- 22. Evaluation Framework For Dependency Analysis EFDA is an open source project that allows users to test the dependency analysis tool of their choice and see how accurate the tool is. https://github.com/devsecops-community/efda
- 23. Software Supply Chain Source Control Management Continuous Delivery (CI/CD) ProductionDeveloper Software Composition Analysis
- 24. DevSecOps - Integrate SCA scanning in your CI pipeline - Create open source usage policy - Fail builds on high severity vulnerabilities - Gather data on open source libraries, vulnerabilities and licenses - Review bill of material (BOM) reports on what’s running in your applications
- 25. Rules for using 3rd party code 1. Know what you are using 2. Think about where it came from 3. Understand what it is doing 4. Avoid using vulnerable libraries
- 26. Thank you! ● Questions? ● Contact ○ Twitter: @asankhaya