Shameful secrets of proprietary network protocols
- 1. Shameful secrets of proprietary protocols Sławomir Jasek Jakub Kałużny SecuRing Photo: https://www.flickr.com/photos/ektogamat/2687444500
- 2. Who are we ● Pentesters @ ● Security assessments of applications, networks, systems... Sławomir Jasek Jakub Kałużny
- 3. Agenda ● Case studies – proprietary protocols – Home automation – Pull printing #1 – Remote desktop – Pull printing #2 – Trading ● Cheatsheet for architects & developers ● How to hack it
- 4. Proprietary network protocols • A pentester will encounter one. • Don’t have the protocol specs nor tools to attack it • How to hack it? • decompile the client? • search for some tools? • watch the raw packets? • Let’s try! https://www.flickr.com/photos/canonsnapper/2566562866
- 5. Home automation remote control ● „Plug the device, configure your router for port forwarding (and dynamic dns if necessary), set password.” ● Proprietary TCP protocol, direct connection from Internet to device, password protected access http://www.flickr.com/photos/99832244@N07/9436065073/
- 6. Protocol – a few packets ab 55 41 00 15 39 64 64 34 65 34 36 31 32 36 .UA..9dd 4e46126 02 01 00 00 a9 39 64 64 34 65 34 36 31 32 36 .....9dd 4e46126 aa 55 41 00 14 39 64 64 34 65 34 36 31 32 36 .UA..9dd 4e46126 ab 55 41 00 15 39 64 64 34 65 34 36 31 32 36 .UA..9dd 4e46126 0c 02 00 00 a4 39 64 64 34 65 34 36 31 32 36 .....9dd 4e46126 aa 55 41 00 14 39 64 64 34 65 34 36 31 32 36 .UA..9dd 4e46126 aa 53 41 02 01 01 f0 f1 f1 f1 f1 00 be f1 f1 00 .SA..... ........ c4 00 e1 f1 f1 f1 f1 f1 f1 f1 f1 f1 f1 f1 f1 f1 ........ ........ f1 f1 f1 00 64 00 00 00 01 00 f0 f0 0a f1 00 02 ....d... ........ 0f 0f e7 S E R V E R C L I E N T
- 7. And what if we change the password? Password 1: Password 2 Password 3
- 8. Home automation protocol Internal command (5 bytes) MD5(password) – first 10 bytes Status returned by the appliance (sensors, settings, etc).
- 9. Home automation - failures ● Sniffing ● MITM ● Connect directly to the appliance - sniffed hash is enough ● Recommendation: SSL!
- 10. Home automation - SSL ● Vendor: OK, we have added SSL support! sslcontext = SSLContext.getInstance("TLS"); atrustmanager = new TrustManager[1]; atrustmanager[0] = new EasyX509TrustManager(null); sslcontext.init(null, atrustmanager, null); • Empty TrustManager – accepts all certificates
- 11. Side effect How to build your own appliance: socat tcp4-listen:1234,fork,readbytes=5 /dev/ttyUSB0,vmin=51
- 12. Side effect And for the new version with SSL support: socat openssl-listen:1234,key=s.key, cert=s.crt,verify=0,fork,readbytes=5 /dev/ttyUSB0,vmin=51
- 14. Why hack pull printing? • Widely used • Confidential data • Getting popular
- 15. Threat modelling – key risks sniffing print queues accountability users’ data
- 16. Attack vectors Other users’ data Access to other print queues Sniffing, MITM Authorization bypass User/admin interface vulnerabilities
- 17. Pull Printing #1 – access control “With its roots in education and the full understanding that college kids “like to hack”, our development processes continually focus on security.”
- 18. Pull Printing #1 – access control “With its roots in education and the full understanding that college kids “like to hack”, our development processes continually focus on security.” “Secure print release (…) can integrate card-swipe user authentication at devices (…) ensuring jobs are only printed when the collecting user is present.”
- 19. Pull Printing #1 – binary protocol S E R V E R P R I N T E R HELLO USER: user1 token HASH(password + token) Password ok Release my print queue OK Just copied 100 pages
- 20. Pull Printing #1 – closer look Release my print queue Just copied 100 pages User permissions beginDeviceTransaction (…) guest-xyz S E R V E R P R I N T E R
- 21. Charge user “guest-xyz” for copying 100 pages Pull Printing #1 – closer look Release my print queue Just copied 100 pages User permissions beginDeviceTransaction (…) guest-xyz Release print queue for user “guest-xyz” S E R V E R P R I N T E R
- 22. Pull printing #1 - consequences sniffing print queues accountability users’ data
- 23. Pull printing #1 - vendor gets notified • Gave access to KB and support service • And all versions of software • Responded in few hours and patched in few days • Was happy to be pentested
- 24. Remote desktop protocol ● X-win „on steroids” (encryption, compression, access control...) ● Mainframe access for critical business operations ● „More than 100,000 users around the world” ● „Prevents unauthorized eavesdropping FIPS 140-2 Validated End-to-end data encryption” http://en.wikipedia.org/wiki/X_Window_System_protocols_and_architecture
- 25. Remote desktop protocol 00000000 0b 00 00 00 .... C L I E N T S E R V E R 00000000 01 01 00 00 .... 00000004 16 03 00 00 6d 01 00 00 69 03 00 52 8d e8 02 cf ....m... i..R.... 00000014 88 d3 96 14 f4 a3 7c 47 f3 0d 85 57 58 d6 c9 f7 ......|G ...WX... 00000024 18 24 95 15 2e 05 82 27 b7 1e ff 00 00 42 00 3a .$.....' .....B.: 00000034 00 39 00 38 00 35 00 34 00 33 00 32 00 2f 00 1b .9.8.5.4 .3.2./.. 00000044 00 1a 00 19 00 18 00 17 00 16 00 15 00 14 00 13 ........ ........ 00000054 00 12 00 11 00 0a 00 09 00 08 00 07 00 06 00 05 ........ ........ SSL
- 26. Remote desktop protocol 00000000 0b 00 00 00 .... C L I E N T S E R V E R 00000000 01 01 00 00 .... 00000000 01 00 00 00 ....00000000 01 00 00 00 .... LOGIN ENCODED PASSWORD Protocol version without encryption
- 27. Password Encoding key / algorithm? 54657374696e6750617373776f72643132333454657374696e6750617373776f7264 1c101e1900000032080117572c1d095c475d5d3704071d060014702d1a1e1e1b1700 Cleartext password: TestingPassword1234TestingPassword Encoded password
- 28. Password 54657374696e6750617373776f72643132333454657374696e6750617373776f7264 XOR 1c101e1900000032080117572c1d095c475d5d3704071d060014702d1a1e1e1b1700 = 48756d6d696e676269726420436f6d6d756e69636174696f6e73204c696d69746564 Cleartext password: TestingPassword1234TestingPassword Encoded password Encoded password is the vendor's name: [redacted] Communications Limited
- 29. Remote Desktop - SSL C L I E N T CLIENTHELLO! cipher suites: SSL_DHE_RSA_WITH_AES_256_CBC_SHA SSL_DHE_DSS_WITH_AES_256_CBC_SHA SSL_RSA_WITH_AES_256_CBC_SHA (...) default configuration SERVERHELLO! I don’t have any certificate! cipherSuite: SSL_DH_anon_WITH_AES_256_CBC_SHA OK, no problem! You have to be the right server if you say so, don’t you?
- 30. Remote Desktop - SSL C L I E N T CLIENTHELLO! certificates configured SERVERHELLO! Certificate Non-anonymous cipher suites: (...) 1st connection: OK, certificate stored! Following connections: OK, certificate valid / ALERT: MITM ATTACK!
- 31. Remote Desktop - SSL C L I E N T CLIENTHELLO! certificates configured SERVERHELLO! Certificate Non-anonymous cipher suites: (...) 1st connection: OK, certificate stored! Following connections: OK, certificate valid / ALERT: MITM ATTACK! SERVERHELLO! I don’t have any certificate! cipherSuite: SSL_DH_anon_WITH_AES_256_CBC_SHA I have your certificate, but since you don’t offer it any more, I won’t check it. OK, let’s connect!
- 32. Remote desktop protocol - vendor ● „We don’t know PGP, use zip with our CEO’s name as password” ● Do not plan to solve the issues (?) ● > /dev/null 2>&1 ● Full disclosure! ● ... and a few weeks later the mysterious shut down of our beloved ;)
- 33. Pull Printing #2 - encryption “is a modern printing solution that safeguards document confidentiality and unauthorized access to print, scan, copy and e-mail functions. Its user-authentication provides air-tight security on your shared MFPs that function as personal printers.”
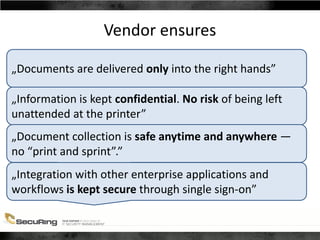
- 34. Vendor ensures „Documents are delivered only into the right hands” „Information is kept confidential. No risk of being left unattended at the printer” „Document collection is safe anytime and anywhere — no “print and sprint”.” „Integration with other enterprise applications and workflows is kept secure through single sign-on”
- 35. Pull Printing #2 – binary protocol First look on communication: • TCP, 2 ports • No cleartext, no SSL • Seems to follow some scheme…
- 36. Ex1: Deeper sight on traffic S E R V E R P R I N T E R constant 263B 96B, “X” B, 128B always different 64 B many identical 16B blocks HELLO HELLO, CERTIFICATE SESSION KEY PostScript, ECB mode
- 37. Ex1: Deeper sight on traffic S E R V E R P R I N T E R constant 263B 96B, “X” B, 128B always different 64 B many identical 16B blocks HELLO HELLO, CERTIFICATE SESSION KEY PostScript, ECB mode https://en.wikipedia.org/wiki/ECB_mode
- 38. Pull Printing #2 - Reverse-engineered • Hardcoded RSA certificate in printer embedded software • No trust store • AES-128 ECB used for traffic encryption • Same protocol in admin interface
- 39. Pull Printing #2 - Consequences sniffing print queues accountability users’ data
- 40. “Many of the devices do not have the CPU power that allows a fast login response and at the same time establish a high security level” Pull Printing #1 - vendor gets notified
- 41. “Many of the devices do not have the CPU power that allows a fast login response and at the same time establish a high security level” For example changing ECB to CBC mode encryption will be more CPU intensive and introducing that may cause slower performance of the devices, which the customers are very reluctant to see implemented.” Pull Printing #1 - vendor gets notified
- 42. “Many of the devices do not have the CPU power that allows a fast login response and at the same time establish a high security level” For example changing ECB to CBC mode encryption will be more CPU intensive and introducing that may cause slower performance of the devices, which the customers are very reluctant to see implemented.” Pull Printing #1 - vendor gets notified “(…) system has been deployed at many high security customers and has passed internal audits.”
- 43. Trading protocol ● An online application for instant financial operations ● A proprietary, binary protocol, designed in order to minimise delays ● TCP in SSL tunnel https://www.flickr.com/photos/tradingrichmom/5571144428/
- 44. Trading protocol – a few packets
- 45. Trading protocol – a few packets
- 46. Trading protocol – a few packets
- 47. Trading protocol – a few packets
- 48. Trading protocol – a few packets
- 51. And what if we...
- 52. And how about...
- 53. RegisterUser <soapenv:Body> <registerUserResponse soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <registerUserReturn xsi:type="xsd:string"> <error code="266" >Incorrect login</error> </registerUserReturn> </registerUserResponse> </soapenv:Body> • Incorrect password • Incorrect first name • Group with name null doesn't exist • Group with name admin doesn't exist • Group with name Administrator doesn't exist • And how about „root”?
- 54. Game Over <soapenv:Body> <registerUserResponse soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <registerUserReturn xsi:type="xsd:string"> User was registered sucessfully with id=5392745 </registerUserReturn> </registerUserResponse> </soapenv:Body> So now we can manage all the other accounts and spend their money!
- 55. Architecture
- 56. Cheat sheet – owners While deploying a proprietary solution: • Get it pentested • Verify vendor claims • Ask the vendor for secure development lifecycle, procedures of addressing vulnerabilities, previous bugs
- 57. Cheat sheet - developers ● Protocol is NOT secure by its secrecy ● Proper encryption. Use known standards, implement them with care. ● Input validation, access control, many layers of security, least privilege principle...
- 58. How to hack protocols? Decompile client? Inject code? Search for the specs? Use some tools? Watch the packets? https://www.flickr.com/photos/nkphillips/2865781749
- 59. Decompile client ● Sometimes easy – e.g. not obfuscated Android application byte abyte3[] = pass.getBytes(); byte abyte4[] = MessageDigest.getInstance("MD5").digest(abyte3); ● Sometimes really hard & time consuming. ● May be fun, but often leads astray: Sywek1?-# 45Schtirlitz&Pianistka
- 60. Look for the fine manual ● There may be an unofficial client, or e.g. wireshark plugin ● Ask for the docs ● Search for them – Yes, we have found internal protocol specification by google hacking!
- 61. Watch the packets ● Various tools to analyze proprietary protocols – time consuming, usually do not work ● Raw, just try to spot some scheme – of course with a little help of your friends: wireshark, tcpdump, ssldump etc. ● Your favourite scripting language
- 62. The end? [email protected] [email protected] www.securing.pl Work with us! [email protected] Talk with us! you are welcome to our stand!










![Home automation - SSL
● Vendor: OK, we have added SSL support!
sslcontext = SSLContext.getInstance("TLS");
atrustmanager = new TrustManager[1];
atrustmanager[0] = new EasyX509TrustManager(null);
sslcontext.init(null, atrustmanager, null);
• Empty TrustManager – accepts all certificates](https://image.slidesharecdn.com/shamefulsecretsofproprietarynetworkprotocols-151028112021-lva1-app6892/85/Shameful-secrets-of-proprietary-network-protocols-10-320.jpg)

















![Password
54657374696e6750617373776f72643132333454657374696e6750617373776f7264
XOR
1c101e1900000032080117572c1d095c475d5d3704071d060014702d1a1e1e1b1700
=
48756d6d696e676269726420436f6d6d756e69636174696f6e73204c696d69746564
Cleartext password:
TestingPassword1234TestingPassword
Encoded password
Encoded password is the vendor's name:
[redacted] Communications Limited](https://image.slidesharecdn.com/shamefulsecretsofproprietarynetworkprotocols-151028112021-lva1-app6892/85/Shameful-secrets-of-proprietary-network-protocols-28-320.jpg)




























![Decompile client
● Sometimes easy – e.g. not obfuscated Android
application
byte abyte3[] = pass.getBytes();
byte abyte4[] = MessageDigest.getInstance("MD5").digest(abyte3);
● Sometimes really hard & time consuming.
● May be fun, but often leads astray:
Sywek1?-# 45Schtirlitz&Pianistka](https://image.slidesharecdn.com/shamefulsecretsofproprietarynetworkprotocols-151028112021-lva1-app6892/85/Shameful-secrets-of-proprietary-network-protocols-59-320.jpg)


