SharePoint Security A to Z
- 1. SharePoint Security A-Z: Who Has Access to What? Steve Goldberg, Axceler [email protected] @iamgoldberg
- 2. About Me Steve Goldberg, Sales Engineer at Axceler • Software Engineer at Axceler for ControlPoint- a SharePoint administration product • Prior to Axceler, was a consultant at Computer Sciences Corporation (CSC), specializing in SharePoint development • Current Role: • Talk to 30-40 people weekly about how to govern SharePoint • Managing permissions is the #1 issue administrators face • Manage and cleanup • Twitter: @iamgoldberg Blog: iamgoldberg.com Email: [email protected] Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 3. Axceler Overview Improving Collaboration Since 2007 Mission: To enable enterprises to simplify, optimize, and secure their collaborative platforms Delivered award-winning administration and migration software since 1994 Over 2,500 global customers Dramatically improve the management of SharePoint Innovative products that improve security, scalability, reliability, “deployability” Making IT more effective and efficient and lower the total cost of ownership Focus on solving specific SharePoint problems (Administration & Migration) Coach enterprises on SharePoint best practices Give administrators the most innovative tools available Anticipate customers’ needs Deliver best of breed offerings Stay in lock step with SharePoint development and market trends Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 4. Always Ask Yourself… How is your organization using SharePoint? Is there secure content in your SharePoint environment? Who needs to have access to SharePoint? Are there ways you can expand the use of SharePoint to offer more benefits to your organization? 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 5. 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 6. Authentication Methods A SharePoint environment must support user accounts that can be authenticated by a trusted authority How do you authenticate your users? Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 7. Windows Authentication NTLM: Users authenticated by using the credentials on the running thread Simple to implement SharePoint will not be integrated with other applications Kerberos If your SharePoint sites use external data Credentials passed from one server to another (“double hop”) Faster, more secure, and can be less error prone then NTLM Anonymous Access No authentication needed to browse the site Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 8. Active Directory Domain Services (AD DS) Authentication based on user account and password from AD This works well for Windows environments Do you need support Internet, partner, or cloud-based computing models? 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 9. Forms-based Authentication Used mostly for Extranets Credentials stored in: Lightweight Directory Access Protocol (LDAP) data store (Novell, Sun) AD DS SQL or other database Custom or third-party membership and role providers In SharePoint 2010, forms-based authentication is only available when you use claims-based authentication Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 10. Claims-Based Authentication (SharePoint 2010) Usually for external customers or partners An outside identity provider authenticates users A claim is just a piece of information describing a user: name, email, age, hire date, etc. used to authenticate the user Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 11. So Much Potential… Integration with Facebook, Google, Live ID, etc. 1. “I’d like to access the Axceler Microsoft technology partners site.” 2. “Not until you can prove to me that you are in the Axceler Microsoft technology partners group.” 3. “Here is my Live ID and password.” 4. “Hi, Steve. I see you are in the Axceler Microsoft technology partners group. Here is a token you can use.” 5. “I’d like to access the Axceler Microsoft technology partner document, and here’s proof I have access to it!” 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 12. SharePoint Authentication Defined at the web application level Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 13. Who Needs to Access SharePoint? Claims-based authentication mode: use any supported authentication method or else you will support only Windows authentication 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 14. Now That We’ve Authenticated Our Users…. Is permission management part of your governance plan? Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 15. Governance is about taking action to help your organization organize, optimize, and manage your systems and resources. Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 16. What do your permissions look like in SharePoint? Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 17. Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 18. How did that happen? No plan The business grows and evolves People and project turn over Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 19. Securable Objects What can we secure? Site Library or List Folder Document or Item Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 20. Structure/Architecture Sub-site Site Sub-site Site Site Collection Web App Site Sub-site Site Site Farm Collection Site Site Web App Collection Site Sub-site Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 21. Plan! How granular do you need to control access to content? Who manages all the different parts of your SharePoint farm? How do you want to manage your users? Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 22. Farm Administrators Group Assigned in Central Admin and has permission to all servers and settings in the farm Central Administration access, create new web apps, manage services, stsadm/PowerShell command Can take ownership of content: make themselves Site Collection Administrators 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 23. Web Application Policies Quick way to apply permissions across web applications Users can be explicitly denied access Set in Central Admin 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 24. Site Collection Administrators Given full control over all sites in a site collection Access to settings pages: Manage users, restores items, manage site hierarchy Cannot access Central Admin 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
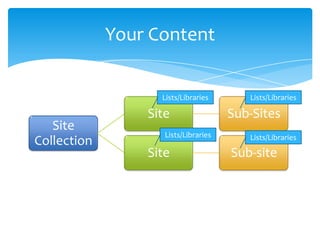
- 25. Your Content Lists/Libraries Lists/Libraries Site Sub-Sites Site Lists/Libraries Lists/Libraries Collection Site Sub-site Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 26. Permission Levels Collections of permissions that allow users to perform a set of related tasks Permission levels are defined at the site collection level Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 27. SharePoint Groups A group of users that are defined at site collection level for easy management of permissions The default SharePoint groups are Owners, Visitors, and Members, with Full Control, Read, and Contribute as their default permission levels respectively Anyone with Full Control permission can create custom groups 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 28. Customizing Permission Levels The default permission levels are Full Control, Design, Contribute, Read, and Limited Access What does “Read” mean to your organization? 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 29. The Basics: Permissions Permissions are applied on objects: 1. Directly to users 2. Directly to domain groups (visibility warning) 3. To SharePoint Groups Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 30. Check Permission Button SharePoint 2010 lets administrators Check Permissions to determine a user or group’s permissions on all content 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 31. Inheritance If all sites and site content inherit those permissions defined at the site collection, what’s so hard about managing permissions if they are defined so high in the hierarchy? Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 32. Fine Grained Permissions Sites, lists, libraries, folders, docum ents, items can all have unique security Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 33. What Exactly is Happening? Copies groups, users, and permission levels from the parent object to the child object Changes to parent object do not affect the child 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 34. Limited Access Auto applied to every securable objects above the uniquely permissioned item Is not directly “applied” 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 35. Permissions Management Becomes Impossible “If you use fine-grained permissions extensively, you will spend more time managing the permissions, and users will experience slower performance when they try to access site content” ~Planning site permissions, technet http://bit.ly/InKv9i Permission management (additions, deletions, edits) is done one securable object at a time! 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 36. Performance is Affected too! Performance is reduced once 1000 objects have broken inheritance in a list or library Sites, lists, and libraries need to build security trimmed navigation List load time increases *Apply unique permissions to folders if need be* 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 37. Orphaned Domain Users Deleted and disabled Active Directory users are not updated in SharePoint Permissions User Profiles My Sites 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 38. Distributed Administration SharePoint is designed to have site administrators and power users 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 39. Be Careful! Train your admins and power users! “I didn’t know that restoring inheritance would remove our unique security model!” ~Countless well intentioned site admins 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 40. Power Users Tip Manage power users through the “Owners” SharePoint groups. limit the members to only those users you trust to change the structure, settings, or appearance of the site 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 41. Best Practice Make most users members of the Members or Visitors groups Members group can contribute to the site by adding or removing items or documents, but cannot change the structure, site settings, or appearance of the site. Visitors group has read-only access to the site, which means that they can see pages and items, and open items and documents, but cannot add or remove pages, items, or documents. 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 42. Stick to the Plan If you do break inheritance, Microsoft recommends using groups to avoid having to track individual users People move in and out of teams and change responsibilities frequently Tracking those changes and updating the permissions for uniquely secured objects would be time-consuming and error-prone. 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 43. Plan for Permission Inheritance Arrange sites and subsites, and lists and libraries so they can share most permissions Separate sensitive data into their own lists, libraries, or subsite Permission worksheet: http://go.microsoft.com/fwlink/p/?LinkID=213970&clcid=0x409 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 44. It’s SharePoint’s Fault! Administrators can audit permission changes by going to the site collection’s settings page 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 46. Contact me Steve Goldberg [email protected] @iamgoldberg Additional Resources available 11 Strategic Considerations for SharePoint Migrations http://bit.ly/j4Vuln The Insider’s Guide to Upgrading to SharePoint 2010 http://bit.ly/mIpOBZ Why Do SharePoint Projects Fail? http://bit.ly/d1mJmw Best practices for capacity management for SharePoint Server 2010, TechNet http://bit.ly/nvNrig What to Look for in a SharePoint Management Tool http://bit.ly/l26ida The Five Secrets to Controlling Your SharePoint Environment http://bit.ly/kzdTjZ Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 47. We want your feedback! Use this QR code or visit: http://sps.la/feedback Silver Sponsors:
- 48. Victory Lap- social event "SharePoint Victory Lap" Social Event for SPSLA will be at: 5:30pm to 8pm at Di Piazzas (5205 E. Pacific Coast Hwy, 90804)
- 49. What I left out…
- 50. Windows Authentication - Basic: - Users have previously assigned Windows credentials - Browser provides credentials during HTTP transaction - Not encrypted- should enable Secure Sockets Layer (SSL) encryption - Digest - Credentials are encrypted These are set directly in IIS Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 51. Zones Each "zone" is essentially a new IIS Website Access the same content through a different URL Allows for multiple authentication methods to the same site Since SharePoint 2010 allows web applications to have mixed authentication methods when choosing claims based authentication, zones are more useful to for load balancing, caching, content databases, and custom modules 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
- 52. Audience targeting To display content such as list or library items, navigation links, and entire Web Parts to specific groups of people. This is useful when you want to present information that is relevant only to a particular group of people. For example, you can add a Web Part to the legal department's portal site that contains a list of legal contracts that is visible only to that department. 6/4/2012 Email Cell Twitter Blog [email protected] 425.246.2823 @buckleyplanet http://buckleyplanet.com
Editor's Notes
- #5: Currently, is SharePoint a document repository? Is it critical to day to day business?Just internal users? Are there ways you can expand the use of SharePoint to offer more benefits to your organization? To partners? To the outside world?
- #6: Things change
- #8: - Kerberos: Less traffic between servers, clients, and domain controllers- uses tickets instead of tokens so it doesn’t have to do a double hop to AD with each requestMuch more planning needed Anonymous: Instead, add the all Authenticated users security instead. This way actions can be traced to users.
- #9: Active Directory Domain Services (AD DS) stores directory data and manages communication between users and domains, including user logon processes, authentication, and directory searches. An Active Directory domain controller is a server that is running AD DS.Used for many things in your organization besides SharePointThe potential for SharePoint to be used and accessed by people outside your organization…2010 makes it easier!
- #10: Organization don’t want external user accounts within their internal domains so forms based authentication is used.
- #11: Less user management
- #12: Seeing more and more login pages with “use facebook or twitter to log in”
- #15: We’re going to be talking mostly about securing intranet content- not an extranet
- #16: Who has one? Not a checklist…it’s constantly changing every day and needs to be managed in the long term
- #21: CB lead, MG color
- #22: Who do you trust to manage all the different parts of your SharePoint farm?
- #26: CB lead, MG color
- #29: Break the inheritance and customize the Read permission level for a subsite to define what “read” really means to your organization
- #31: Still hard to manage at lower levels
- #34: More work! Harder to manage!
- #39: There designed to make your life easier…I swear!
- #40: If you restore inherited permissions, the child object will inherit its users, groups, and permission levels from the parent again, and you will lose any users, groups, or permission levels that were unique to the child object.