Signature verification Using SIFT Features
- 1. Islamic University of Technology(IUT) Department of Computer Science and Engineering(CSE) Offline Signature Verification Using Local Keypoint Features Supervised By: Dr. Hasanul kabir Assistant professor, CSE dept. Islamic university of technology(iut) Presented By: Ashikur Rahman (104401) Golam Mostaeen (104404)
- 2. Contents Introduction Offline Signature Verification Research Challenges Thesis Objective Related Works Proposed Method Dataset & Implementation Future Works References 2
- 3. INTRODUCTION A signature is a person's name written in a distinctive way as a form of identification in authorizing a check or document or concluding a letter. Signature forgery refers to the act of falsely replicating the signature of another person. Signature forgery is done in order to- Commit frauds Deceive others Alter data etc. One common example of signature forgery is cheque writing. 3
- 4. Offline Signature Verification Those forgeries can be verified in two methods- Online Signature Verification • Deals with dynamic features like speed, pen pressure, directions, stoke length and when the pen is lifted from the paper Offline Signature Verification • Uses features(static information) from the image. • Deals with shape only. • Largely used for verifying bank cheques 4
- 5. Research Challenges Differentiating different parts of signature that varies with each signing- Signature orientation can be different- Input image may contain noise. Isolating the sector of interest from the total input image- Threshold value should be taken wisely so that False accept and False Reject occur very less. The nature and variety of the writing pen 5
- 6. Thesis Objective Our main objective of this thesis is to develop a method that will calculate features of a signature and verify it comparing with sample prototype in spite of having- Noise in the image Different orientation Various writing Already we have implemented several existing detection methods signature verification and figured out the limitations of the methods. Our goal is to ensure better performance in robust nature so that we can easily detect the forged signature in different challenging situations. 6
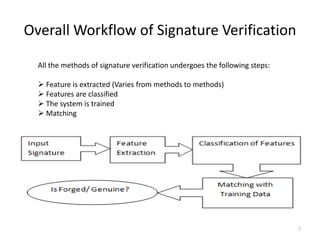
- 7. Overall Workflow of Signature Verification All the methods of signature verification undergoes the following steps: Feature is extracted (Varies from methods to methods) Features are classified The system is trained Matching 7
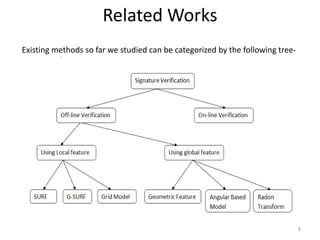
- 8. Related Works Existing methods so far we studied can be categorized by the following tree- 8
- 9. Related works(contd.) Global & geometric Method(A. C. Verma,D. Saha,H. Saikia,2013): • Geometric data(aspect ratio, center of gravity, baseline shift etc.) are considered as feature • Mean of each feature calculated from the training data • Variance is used to calculate the Euclidian distance which is the basis of comparison The formula is- Limitations: • Cannot detect skilled forgery as the geometric value get closer • False accept occurs more often Angular based model(Prashanth & Raja, 2012): • Calculate average no. of rows and columns for random forgery detection • For skilled, split the image in two blocks recursively until 128 blocks have found on basis of geometric center • Angle and distance for all the center points of each block is calculated from the point (1,1) for feature extraction. Limitation: • Depends on global value(angle and distance) 9
- 10. Related works(contd.) Grid Model(Madasu & Brian,2002): • Image is partitioned into 8 partitions using equal horizontal density approximation method. • Each Box portioned into 12 boxes (total 96 boxes) • calculate the summation of the angles of all points in each box taken with respect to the bottom left corner and normalize it for feature. Limitations: • Even a little change in the signature leads to much change in the result. Radon transform model(Kiani & Pourreza,2011): • Computes projection sum of the image intensity along a radial line oriented at a specific angle with the formula- Where the δ(r) is Dirac function. • Computation of Radon Transform is its projections across the image at arbitrary orientations θ and offsets ρ which is used as feature Limitations: • False reject rate is little high for this method 10
- 11. Related works(contd.) SURF model(Bay & Gool,2006): • First, key point is detected using fast Hessian Detector and Haar wavelet. The formula of Hessian matrix is- • Then SURF descriptor is extracted using assignment orientation. Limitations: • The time needed to detect can be beaten today G-SURF model(Pal, Chanda & Franke,2012): • Uses Gabor filter along with SURF algorithm • A two dimensional Gabor Filter in spatial domain can be defined as follows- Limitations: • Though it overcomes the performance of SIFT and SURF, still need to be upgraded 11
- 12. Related works(contd.) Harris Corner Detection: • This method detects corner first recognizing the points by looking the intensity within the small window • Shifting the window in any direction should yield a large change in appearance • Different output can be gained by setting a desirable threshold value Feature descriptor: • Describe a point assigning orientation around it • Divides the surrounding area into 16 blocks, each blocks have a histogram of 8 bins each • So, each point has a (16x8) 128 long feature vector 12
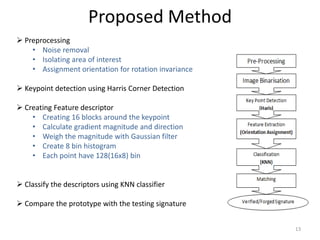
- 13. Proposed Method Preprocessing • Noise removal • Isolating area of interest • Assignment orientation for rotation invariance Keypoint detection using Harris Corner Detection Creating Feature descriptor • Creating 16 blocks around the keypoint • Calculate gradient magnitude and direction • Weigh the magnitude with Gaussian filter • Create 8 bin histogram • Each point have 128(16x8) bin Classify the descriptors using KNN classifier Compare the prototype with the testing signature 13
- 14. Proposed Method(Contd.) • Further checking for skilled Forgery A high level of skilled forgery may pass the above test but those can be further detected using the following tests: Edge thickness will be calculated to detect overwriting Straightness of the edges will be checked Sudden blobs in the signature need to be detected End point will be checked to detect sharp finish If a Signature Passes all those tests we consider it as a authentic signature. 14
- 15. Dataset & Implementation Dataset We have collected our dataset from different persons. Signature s was taken in white paper and scanned for training our system. Similarly we took forged and genuine version of the signatures for testing the performance of different verification method we implemented. Global & Geometric Method: After implementing this method we compared its performance for varying threshold of acceptance. The graph at the right represents its performance. As the threshold is increased FAR increases but FRR is decreases somewhat proportionately. 15
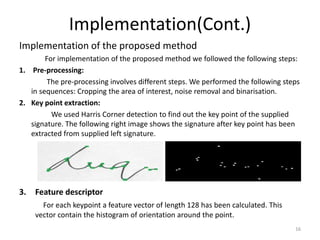
- 16. Implementation(Cont.) Implementation of the proposed method For implementation of the proposed method we followed the following steps: 1. Pre-processing: The pre-processing involves different steps. We performed the following steps in sequences: Cropping the area of interest, noise removal and binarisation. 2. Key point extraction: We used Harris Corner detection to find out the key point of the supplied signature. The following right image shows the signature after key point has been extracted from supplied left signature. 3. Feature descriptor For each keypoint a feature vector of length 128 has been calculated. This vector contain the histogram of orientation around the point. 16
- 17. Future Works • So far we have figured out several problems of existing methods of signature detection through implementation • Still we did not implemented our proposed method but from the implementation & analysis of existing method we can say that it will give us better performance • So our future work is to implement the proposed method so that it can ensure- more robust with rotation invariance robustness in noise robust in variant ink with minimum complexity 17
- 18. Thank you. Any Question ? 18
- 19. References • A. C. Verma,D. Saha, H. Saikia; ’FORGERY DETECTION IN OFFLINE HANDWRITTENSIGNATURE USING GLOBAL AND GEOMETRIC FEATURES’, IJCER(Vol.2, Issue 2, April 2013) • Prashanth C R, K B Raja, Venugopal K R, L M Patnaik,’ Intra-modal Score level Fusion for Off- line Signature Verification’, IJITEE, ISSN: 2278-3075, Vol.1, Issue 2, July 2012 • Prashanth C. R. and K. B. Raja,’ Off-line Signature Verification Based on Angular Features’ IJMO, Vol. 2, No. 4, August 2012 • M.Radmehr, S.M.Anisheh, I.Yousefian,’ Offline Signature Recognition using Radon Transform’, WASET, Vol:6 2012-02-28 • Bay H,Tinne t.,Gool l.,’ SURF: Speeded Up Robust Features’; • Samaneh G., Mohsen E., i Moghaddam, “Off-line Persian Signature Identification and Verification Based on Image Registration and Fusion,” Journal of Multimedia, Vol. 4, No. 3, pp.137-144, June 2009. • Jesus F Vargas, Miguel A Ferrer, Carlos M Travieso, and Jesus B Alonso, “Off-line Signature Verification Based on Psuedo-Cepstral Coefficients,” International Conference on Document Analysis and Recognition, pp. 126-130, 2009 • V A Bharadi and H B Kekre, “Off-line Signature Recognition Systems,” International Journal of Computer Applications, Vol. 1, No. 27, pp. 61-70, 2010 19