Site to-multi site open vpn solution with mysql db
- 1. SITE TO MULTI-SITE OPEN VPN SOLUTION-(CentOS LINUX) DESIGEND , DOCUMEMTED AND TESTED BY CHANAKA LASANTHA NANAYAKKARA WAWAGE Advantages of OpenVPN With the advent of OpenVPN a new generation of VPN entered the scene. While other VPN solutions often use proprietary or non-standard mechanisms, OpenVPN has a modular concept, both for underlying security and for networking. OpenVPN uses the secure, stable, and lauded SSL/TLS mechanisms and combines them in its own reliability layer. It does not suffer from the complexity that characterizes other VPN implementations like the market leader IPsec. At the same time, it offers possibilities that go beyond every other VPN implementation's scope. Layer 2 and Layer 3 VPN: OpenVPN offers two basic modes, which run either as Layer 2 or Layer 3 VPN. Thus, OpenVPN tunnels on Layer 2 can also transport Ethernet frames, IPX packets, and Windows Network Browsing packets (NETBIOS), all of which are problems in most other VPN solutions. Protecting field workers with the internal firewall: A field worker connected to the central branch of their company with a VPN tunnel can change the network setup on their laptop so that all of their network traffic is sent through the tunnel. Once OpenVPN has established a tunnel, the central firewall in the company's central branch can protect the laptop, even though it is not a local machine. Only one network port must be opened to the local (customers') network by the field worker. The employee is protected by the central firewall whenever he is connected to the VPN. Even better, the administrator of the central VPN server can force the client to use the central firewall by imposing configuration options on the clients. OpenVPN connections can be tunneled through almost every firewall and proxy: If you have Internet access and can access HTTPS web sites, then OpenVPN tunnels should work. Setups where OpenVPN tunnels are banned are very rare. OpenVPN has full proxy support including authentication. Server and client mode, UDP and TCP support: OpenVPN can be configured to run as a TCP or UDP service and as a server or client. As a server, OpenVPN simply waits until a client requests a connection, whereas a client establishes a connection according to its configuration. A server on the Internet can be completely shut down from any other machine except the ones in its virtual private network, which extends the security level of such systems enormously. Only one port in the firewall must be opened to allow incoming connections: Since OpenVPN 2.0, the special server mode allows multiple incoming connections on the same TCP or UDP port, while still using different configurations for every single connection. No problems with NAT: Both OpenVPN server and clients can be within a network using only private IP addresses. Every firewall can be used to send the tunnel traffic to the other tunnel endpoint. Virtual interfaces allow flexible very specific networking and almost every imaginable firewall rule: All restrictions, mechanisms like forwarding, and concepts like NAT (Network Address Translation) or package mangling (changing the metadata of network datagrams, like some firewalls do) can be used with and within OpenVPN tunnels. Any IP Protocol is possible. Yes, you can tunnel VPNs, like IPsec, inside an OpenVPN tunnel.
- 2. High flexibility with extensive scripting possibilities: OpenVPN offers numerous points during connection setup to start individual scripts. These scripts can be used for a great variety of purposes from authentication to failover and more. Transparent, high-performance support for dynamic IPs: By using OpenVPN, there is no longer a need to use expensive, static IPs on either side of the tunnel. Both tunnel endpoints can have cheap DSL access with dynamic IPs. The users will rarely notice a change of IP on either side, Windows Terminal Server and Secure Shell (SSH) sessions will only seem to hang for few seconds, but they will not terminate and will carry on with the action requested after a short pause. All traffic can be compressed through the LZO library and OpenVPN continuously checks if the compression has been successful. So-called adaptive compression merely 'zips' the uncompressed data to avoid unnecessary overhead. Simple installation on any platform: Both installation and use are incredibly simple. Especially, if you have tried to set up IPsec connections with different implementations, you will find OpenVPN appealing. Modular Design: The modular design with a high degree of simplicity both in security and networking is outstanding. No other VPN solution can offer the same options at this level of security. Support for mobile and embedded: More and more mobile devices are supported. Packages for Windows Mobile and Nokia's Maemo platform, and embedded operating systems like OpenWrt/FreeWrt have all been provided for recently, and there are many others in development. Very active community: OpenVPN has acquired a huge amount of fans in the last few years. There are installations with high volume users with high availability. History of OpenVPN According to an interview on http://linuxsecurity.com published in 2003, James Yonan was traveling in Central Asia in the days prior to September 11, 2001 and connecting to his office over Asian or Russian Internet Providers. The fact that these connections were established over servers in countries with very dubious security made him more and more aware of and concerned about security issues. His research revealed that there were two main streams in VPN technology, one promoting security, and the other usability. None of the solutions available at that time offered an ideal blend of both objectives. IPsec and all of its implementations were difficult to set up, but offered acceptable security. However, its complex structure made it vulnerable to attacks, bugs, and security flaws. Therefore, the networking approach Yonan found in some of the usability camp's solutions seemed to make more sense to him, leading him to a modular networking model using the TUN/TAP virtual networking devices that are provided by the Linux kernel. After some study of the open source VPN field, my conclusion was that the 'usability first' camp had the right ideas about networking and inter-network tunneling, and the SSH, SSL/TLS, and IPSec camps had the appropriate level of seriousness toward the deep crypto issues. This was the basic conceptual starting point for my work on OpenVPN. James Yonan in a LinuxSecurity.com interview on November 10, 2003. (http://www.linuxsecurity.com/content/view/117363/49/) Choosing the TUN/TAP devices as a networking model immediately offered a flexibility that other VPN solutions could not offer. While other SSL/TLS-based VPN solutions needed a browser to establish connections, OpenVPN would prepare almost real (but still virtual) network devices, on which almost all networking activities can be carried out. Yonan then chose the name OpenVPN with respect to the libraries and programs of the OpenSSL project and
- 3. because of the clear message that this is open source and free software. Introduction A Virtual Private Network (VPN) can be thought of as a secure tunnel which connects two nodes through an insecure connection (although it has other uses not related to security). This can be as simple as securely connecting a road warrior and his/her laptop back to the home office's network or as complex as linking multiple entire networks together. To accomplish this, we can employ one of OpenVPN's two different modes: routed or bridged. Bridging, as the name implies, simply extends the server's network (via the OpenVPN machine) to the client that's connecting. It's quick and easy to set up, but has limited scalability as the network grows. Bridging also expands the broadcast domain as broadcasts are sent through the tunnel since connected clients are assigned IP addresses in the same subnet as the server's network. This is great for services and protocols that rely on it like SMB (Windows file-sharing) . But in a broadcast-heavy environment, that extra traffic over an encrypted tunnel can take its toll on performance. Routing, on the other hand, is a bit trickier to set up, requiring access to both the client and server side routers. But it scales well and separates both the client network and the server network in to separate broadcast domains.
- 4. Sample Diagram Configuration Main Access Server Office Network (Left Bottom Corner) Router/Firewall’s Public IP Address: 112.135.73.26 Port Forwarding for UDP Port 1194: 112.135.73.26 to 192.168.0.200 (UDP Port: 1194) Router/Firewall’s LAN IP Address: 192.168.0.1 Router/Firewall’s Subnet Mask: 255.255.255.0 (/24) OpenVPN Access Server’s LAN IP Address: 192.168.0.200 OpenVPN Access Server’s Subnet Mask: 255.255.255.0 (/24) OpenVPN Access Server’s Default Gateway: 192.168.0.1 Database and File Server’ 1/2′s LAN IP Address: 192.168.0.3 / 192.168.0.4 LAN 1/2′s Subnet Mask: 255.255.255.0 (/24) LAN 1/2′s Default Gateway: 192.168.0.1 Client VPN Server Office Network (Right Bottom Corner) Router/Firewall’s LAN IP Address: 10.10.10.1 Router/Firewall’s Subnet Mask: 255.255.255.0 (/24) OpenVPN Client Server’s LAN IP Address: 10.10.10.2 OpenVPN Client Server’s Subnet Mask: 255.255.255.0 (/24) OpenVPN Client Server’s Default Gateway: 10.10.10.1 Client VPN Server Office Network (Right Top Corner) Router/Firewall’s LAN IP Address: 20.20.20.1 Router/Firewall’s Subnet Mask: 255.255.255.0 (/24) OpenVPN Client Server’s LAN IP Address: 20.20.20.2 OpenVPN Client Server’s Subnet Mask: 255.255.255.0 (/24) OpenVPN Client Server’s Default Gateway: 20.20.20.1 The diagram above depicts a typical site-to-multi site layer 3(L3) routing setup. In order to complete this setup, all of the following requirements must be met: 1. You have three sites, each one connected to the Internet. One site will be hosting the Access Server and other two sites will be hosting the OpenVPN client Servers. 2. The site hosting the Access Server must be accessible from the Internet, or have its required ports forwarded to it from the Internet. 3. The OpenVPN client servers must have IP forwarding enabled, as well as openvpn installed, and running a Linux operating system (per these instructions). 4. You must have administrative access to the OpenVPN Client Server machines, including uploading files and SSH/SFTP access. Install Packages Add repository EPEL that is provided from Fedora project. wget http://ftp.riken.jp/Linux/fedora/epel/RPM-GPG-KEY-EPEL-5
- 5. rpm --import RPM-GPG-KEY-EPEL-5 rm -f RPM-GPG-KEY-EPEL-5 vim /etc/yum.repos.d/epel.repo [epel] name=EPEL RPM Repository for Red Hat Enterprise Linux baseurl=http://ftp.riken.jp/Linux/fedora/epel/5/$basearch/ gpgcheck=1 enabled=0 rpm –Uvh http://dl.fedoraproject.org/pub/epel/5/x86_64/epel-release-5-4.noarch.rpm yum --enablerepo=epel -y install openvpn lzo policycoreutils-python /sbin/service openvpn start Starting openvpn: [ OK ] Install MySQL Server yum -y install mysql-server /etc/rc.d/init.d/mysqld start chkconfig mysqld on /usr/bin/mysql_secure_installation Log in MySQL as root mysql -uroot -p Create the database 'openvpn' CREATE DATABASE openvpn; Create a MySQL user with username 'USERNAME' and password 'PASSWORD' GRANT ALL ON openvpn.* TO 'USERNAME'@"%" IDENTIFIED BY 'PASSWORD'; exit; Log in MySQL as new user 'USERNAME' mysql -uUSERNAME -pPASSWORD Switch database USE openvpn; Create user, log table and insert user data - user table CREATE TABLE IF NOT EXISTS `user` ( `user_id` varchar(32) COLLATE utf8_unicode_ci NOT NULL, `user_pass` varchar(32) COLLATE utf8_unicode_ci NOT NULL DEFAULT '1234', `user_mail` varchar(64) COLLATE utf8_unicode_ci DEFAULT NULL, `user_phone` varchar(16) COLLATE utf8_unicode_ci DEFAULT NULL,
- 6. `user_online` tinyint(1) NOT NULL DEFAULT '0', `user_enable` tinyint(1) NOT NULL DEFAULT '1', `user_start_date` date NOT NULL, `user_end_date` date NOT NULL, PRIMARY KEY (`user_id`), KEY `user_pass` (`user_pass`) ) ENGINE=MyISAM DEFAULT CHARSET=utf8 COLLATE=utf8_unicode_ci; - log table CREATE TABLE IF NOT EXISTS `log` ( `log_id` int(10) unsigned NOT NULL AUTO_INCREMENT, `user_id` varchar(32) COLLATE utf8_unicode_ci NOT NULL, `log_trusted_ip` varchar(32) COLLATE utf8_unicode_ci DEFAULT NULL, `log_trusted_port` varchar(16) COLLATE utf8_unicode_ci DEFAULT NULL, `log_remote_ip` varchar(32) COLLATE utf8_unicode_ci DEFAULT NULL, `log_remote_port` varchar(16) COLLATE utf8_unicode_ci DEFAULT NULL, `log_start_time` timestamp NOT NULL DEFAULT CURRENT_TIMESTAMP, `log_end_time` timestamp NOT NULL DEFAULT '0000-00-00 00:00:00', `log_received` float NOT NULL DEFAULT '0', `log_send` float NOT NULL DEFAULT '0', PRIMARY KEY (`log_id`), KEY `user_id` (`user_id`) ) ENGINE=MyISAM DEFAULT CHARSET=utf8 COLLATE=utf8_unicode_ci; - user data INSERT INTO `user` ( `user_id`, `user_pass`, `user_mail`, `user_phone`, `user_online`, `user_enable`, `user_start_date`, `user_end_date` ) VALUES ( 'test', '1234', '[email protected]', '+66815447514', 0, 1, '2012-01-01', '0000-00-00' ); Show tables show tables; +-------------------+ | Tables_in_openvpn | +-------------------+ | log | | user | +-------------------+ Show user data select * from user; +---------+-----------+---------------------+--------------+-------------+-------------+-----------------+---------------+ | user_id | user_pass | user_mail | user_phone | user_online | user_enable | user_start_date | user_end_date | +---------+-----------+---------------------+--------------+-------------+-------------+-----------------+---------------+ | test | 1234 | [email protected] | +66815447514 | 0 | 1 | 2012-01-01 | 0000-00-00 |
- 7. +---------+-----------+---------------------+--------------+-------------+-------------+-----------------+---------------+ Log out exit; Edit file /etc/my.cnf insert # to line #bind-address = 127.0.0.1 Install httpd yum -y install httpd rm -f /etc/httpd/conf.d/welcome.conf rm -f /var/www/error/noindex.html ln -s /usr/bin/perl /usr/local/bin/perl Configure httpd vi /etc/httpd/conf/httpd.conf # line 44: change ServerTokens Prod # line 74: change to ON KeepAlive On # line 251: Admin's address ServerAdmin [email protected] # line 265: change to your server's name ServerName www.server.world:80 # line 320: change (enable CGI and disable Indexes) Options FollowSymLinks ExecCGI # line 327: change AllowOverride All # line 391: add file name that it can access only with directory's name DirectoryIndex index.html index.cgi index.php # line 524: change ServerSignature Off # line 747: make it comment #AddDefaultCharset UTF-8 # line 778: uncomment and add file-type that apache looks them CGI AddHandler cgi-script .cgi .pl /etc/rc.d/init.d/httpd start chkconfig httpd on Install and configure phpmyadmin yum --enablerepo=epel -y install phpMyAdmin php-mysql php-mcrypt # install from EPEL vi /etc/httpd/conf.d/phpMyAdmin.conf # line 13: add IP address you permit Allow from 127.0.0.1 10.0.0.0/24
- 8. /etc/rc.d/init.d/httpd reload Access to 'http://192.168.2.204/phpmyadmin' with web browser, then following screen is shown. Login with a user in MySQL. Create a your server's original SSL Certificate. cd /etc/pki/tls/certs make server.key openssl rsa -in server.key -out server.key make server.csr openssl x509 -in server.csr -out server.crt -req -signkey server.key -days 3650 chmod 400 server.* Configration of SSL yum -y install mod_ssl vi /etc/httpd/conf.d/ssl.conf # line 84: uncomment DocumentRoot "/var/www/html" # line 85: uncomment and specify server name ServerName www.server.world:443 # line 112: specify certificate SSLCertificateFile /etc/pki/tls/certs/server.crt # line 119: specify certification key SSLCertificateKeyFile /etc/pki/tls/certs/server.key /etc/rc.d/init.d/httpd restart
- 9. Access to 'https://192.168.2.204/phpmyadmin' with web browser, then following screen is shown. Login with a user in MySQL. If you use your server as a business, it had better buy and use a Formal Certificate from Verisigh and so on. Generate Certificates for TLS Authentication Copy the certificate generation scripts to a temporary working directory and generate the certificates to be used for TLS authentication: mkdir /tmp/openvpn cp -a /usr/share/openvpn/easy-rsa/ /tmp/openvpn/ cd /tmp/openvpn/easy-rsa/2.0 # ----- Edit the vars file to input your institution information ----- vi vars # note: don't worry about the "export PKCS11_MODULE_PATH=changeme" line # You may change the export KEY_SIZE=2048 line to the key size you'd like # ----- Execute the vars script to set environment variables and prepare ----- source ./vars cp openssl-1.0.0.cnf openssl.cnf sh clean-all # ----- Build Cerificate Authority certificates ----- sh build-ca # ----- Build Server Certificate ----- sh build-key-server server # ----- Build a Client Certificate (For as many unique clients as you'd like) ----- sh build-key branch-1 source ./vars sh build-key branch-2 # OR if you need two-factor authentication with passphrase (i.e. for PCI compliance) source ./vars sh build-key user-1
- 10. # ----- Build the Diffie-Hellman (DH) Parameters Certificate ----- sh build-dh # ----- Generate a ta key to help block DoS attacks and UDP port flooding ----- openvpn --genkey --secret keys/ta.key At this point you should have CA, server, and client certificates in the /tmp/openvpn/easy-rsa/2.0/keys folder. Configuring the Server Side OpenVPN Machine The server side OpenVPN machine is the heart of the VPN. In routed mode, all clients will connect to the OpenVPN server and all communication between clients (if the "client-to-client" option is enabled) is routed by the OpenVPN server, so it's best to have a dedicated, always-up machine to run it on Copy the sample openvpn config file to the /etc/openvpn folder and the CA, server, and DH keys to the /etc/openvpn/keys folder: mkdir /etc/openvpn/keys sudo cp /tmp/openvpn/easy-rsa/2.0/keys/ca.* /etc/openvpn/keys/ sudo cp /tmp/openvpn/easy-rsa/2.0/keys/branch-1.* /etc/openvpn/keys/ sudo cp /tmp/openvpn/easy-rsa/2.0/keys/branch-2.* /etc/openvpn/keys/ sudo cp /tmp/openvpn/easy-rsa/2.0/keys/user-1.* /etc/openvpn/keys/ sudo cp /tmp/openvpn/easy-rsa/2.0/keys/server.* /etc/openvpn/keys/ sudo cp /tmp/openvpn/easy-rsa/2.0/keys/dh* /etc/openvpn/keys/ sudo cp /tmp/openvpn/easy-rsa/2.0/keys/ta.key /etc/openvpn/keys/ sudo cp /usr/share/doc/openvpn-2.2.2/sample-config-files/server.conf /etc/openvpn/ Edit the /etc/openvpn/server.conf to make the following changes: Enable IP Forwarding (Highly Important!) If you want your OpenVPN clients to be able to access the network, in addition to the push routes statements above you will need to setup ip forwarding for the tunnel interface and change the 0 to a 1. vi /etc/sysctl.conf # ------ Edit the following line changing the 0 to a 1 ----- net.ipv4.ip_forward = 1 Save and close the file. Reload the changes by typing the following command: Or echo "1" > /proc/sys/net/ipv4/ip_forward echo "1" > /proc/sys/net/ipv4/ip_dynaddr sysctl -p Configure IPTables and SELinux on Central VPN Server (192.168.0.200) service iptables start iptables –-flush iptables --table nat -–flush iptables --delete-chain
- 11. service iptables save service iptables restart service network restart iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT DROP iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o tun0 -j ACCEPT iptables -A FORWARD -i tun1 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o tun1 -j ACCEPT iptables -A INPUT -p ICMP -s 10.8.0.0/24 -j ACCEPT iptables -A INPUT -p ICMP -s 10.0.0.0/24 -j ACCEPT iptables -A INPUT -p icmp -m limit --limit 1/s --limit-burst 2 -j ACCEPT iptables -A INPUT -p icmp -j ACCEPT iptables -A OUTPUT -p icmp -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT iptables -A INPUT -m state --state INVALID -j DROP iptables -A OUTPUT -m state --state INVALID -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL ALL -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL NONE -j DROP iptables -A INPUT -p tcp --tcp-flags ALL FIN,URG,PSH -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP iptables -N SYN_FLOOD iptables -A INPUT -p tcp --syn -j SYN_FLOOD iptables -A SYN_FLOOD -m limit --limit 2/s --limit-burst 6 -j RETURN iptables -A SYN_FLOOD -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type address-mask-request -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type timestamp-request -j DROP iptables -A INPUT -p icmp -m icmp -m limit --limit 1/second -j ACCEPT iptables -A INPUT -p tcp -m tcp --tcp-flags RST RST -m limit --limit 2/second --limit-burst 2 -j ACCEPT iptables -A INPUT -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A FORWARD -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A INPUT -m recent --name portscan --remove iptables -A FORWARD -m recent --name portscan –remove iptables -A INPUT -s 0.0.0.0/7 -j DROP iptables -A INPUT -s 2.0.0.0/8 -j DROP iptables -A INPUT -s 5.0.0.0/8 -j DROP iptables -A INPUT -s 7.0.0.0/8 -j DROP iptables -A INPUT -s 10.0.0.0/8 -j DROP iptables -A INPUT -s 23.0.0.0/8 -j DROP iptables -A INPUT -s 27.0.0.0/8 -j DROP iptables -A INPUT -s 31.0.0.0/8 -j DROP iptables -A INPUT -s 36.0.0.0/7 -j DROP
- 12. iptables -A INPUT -s 39.0.0.0/8 -j DROP iptables -A INPUT -s 42.0.0.0/8 -j DROP iptables -A INPUT -s 49.0.0.0/8 -j DROP iptables -A INPUT -s 50.0.0.0/8 -j DROP iptables -A INPUT -s 77.0.0.0/8 -j DROP iptables -A INPUT -s 78.0.0.0/7 -j DROP iptables -A INPUT -s 92.0.0.0/6 -j DROP iptables -A INPUT -s 96.0.0.0/4 -j DROP iptables -A INPUT -s 112.0.0.0/5 -j DROP iptables -A INPUT -s 120.0.0.0/8 -j DROP iptables -A INPUT -s 169.254.0.0/16 -j DROP iptables -A INPUT -s 172.16.0.0/12 -j DROP iptables -A INPUT -s 173.0.0.0/8 -j DROP iptables -A INPUT -s 174.0.0.0/7 -j DROP iptables -A INPUT -s 176.0.0.0/5 -j DROP iptables -A INPUT -s 184.0.0.0/6 -j DROP iptables -A INPUT -s 192.0.2.0/24 -j DROP iptables -A INPUT -s 197.0.0.0/8 -j DROP iptables -A INPUT -s 198.18.0.0/15 -j DROP iptables -A INPUT -s 223.0.0.0/8 -j DROP iptables -A INPUT -s 224.0.0.0/3 -j DROP iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A FORWARD -i tun0 -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun1 -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun0 -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun1 -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 20.20.20.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 20.20.20.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 20.20.20.0/24 -d 192.168.0.0/24 -j ACCEPT
- 13. iptables -A FORWARD -p tcp -s 10.10.10.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.10.10.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.10.10.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j SNAT --to 192.168.0.204 iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -j SNAT --to 192.168.0.204 service iptables save service iptables restart service network restart /sbin/iptables -L iptables -L -t nat –n iptables -vnL /sbin/service openvpn restart Editing Open VPN Access Server’s Main Config File(server-udp-1194.conf) Finally, we need to edit the OpenVPN config file. OpenVPN ships with a collection of good example config files (found in ~/openvpn-2.0.9/sample-config-files) that are very well documented starting points. The man page is also very well written and contains loads of useful information. The OpenVPN server's config file (server-udp-1194.conf) – For The Site to Site Inter-Server Connectivity. cd /etc/openvpn vim server.conf local 192.168.0.204 port 1194 proto udp dev tun ca /etc/openvpn/keys/ca.crt cert /etc/openvpn/keys/server.crt key /etc/openvpn/keys/server.key dh /etc/openvpn/keys/dh2048.pem server 10.8.0.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "route 192.168.0.0 255.255.255.0" client-config-dir /tmp/openvpn/ccd route 20.20.20.0 255.255.255.0 route 10.10.10.0 255.255.255.0
- 14. push "persist-key" push "persist-tun push "explicit-exit-notify 1" push "redirect-gateway def1 bypass-dhcp" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" client-to-client keepalive 10 120 reneg-sec 432000 tls-auth /etc/openvpn/keys/ta.key 0 cipher AES-256-CBC comp-lzo user nobody persist-key persist-tun status /var/log/openvpn-status.log log /var/log/openvpn.log log-append /var/log/openvpn.log verb 5 Make a Automated Shell Script to Permit Inter Routing Between Branches #!/bin/bash # #------------------------Command Start-up Script --------------------------- # test -d /tmp/openvpn || mkdir /tmp/openvpn test -d /tmp/openvpn/ccd || mkdir /tmp/openvpn/ccd echo "iroute 20.20.20.0 255.255.255.0" > /tmp/openvpn/ccd/branch-1 echo "iroute 10.10.10.0 255.255.255.0" > /tmp/openvpn/ccd/branch-2 # #----------------------Command Start-up Script End------------------------ # #Note : You have to make shell script like a "/etc/openvpn-stp-1.sh" and give above start-up script over their. finally #just config it into "vi /etc/rc.local" for the automated running process at the server start-up time as well. Editing Open VPN Access Server’s Main Config File(server-tcp-444.conf) Finally, we need to edit the OpenVPN config file. OpenVPN ships with a collection of good example config files (found in ~/openvpn-2.0.9/sample-config-files) that are very well documented starting points. The man page is also very well written and contains loads of useful information.
- 15. The OpenVPN server's config file (server-tcp-443.conf) - For The Server to Client VPN Clent Connectivity with MySQL local 192.168.2.204 port 444 proto tcp dev tun ca /etc/openvpn/keys/ca.crt cert /etc/openvpn/keys/server.crt key /etc/openvpn/keys/server.key dh /etc/openvpn/keys/dh2048.pem server 10.0.0.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "route 192.168.0.0 255.255.255.0" client-config-dir /tmp/openvpn/ccd route 20.20.20.0 255.255.255.0 route 10.10.10.0 255.255.255.0 push "persist-key" push "persist-tun” push "explicit-exit-notify 1" push "redirect-gateway def1 bypass-dhcp" push "dhcp-option DNS 8.8.8.8" push "dhcp-option DNS 8.8.4.4" client-to-client username-as-common-name client-cert-not-required auth-user-pass-verify /etc/openvpn/script/login.sh via-env keepalive 10 120 reneg-sec 432000 tls-auth /etc/openvpn/keys/ta.key 0 cipher AES-256-CBC comp-lzo user nobody persist-key persist-tun script-security 3 system client-connect /etc/openvpn/script/connect.sh client-disconnect /etc/openvpn/script/disconnect.sh status /var/log/openvpn-status.log log /var/log/openvpn.log log-append /var/log/openvpn.log
- 16. verb 5 Create directory for script '/etc/openvpn/script' mkdir /etc/openvpn/script cd /etc/openvpn/script Create file config.sh '/etc/openvpn/script/config.sh' #!/bin/bash ##Dababase Server HOST='192.168.0.204' #Default port = 3306 PORT='3306' #Username USER='USERNAME' #Password PASS='PASSWORD' #database name DB='openvpn' Create file test_connect_db.sh'/etc/openvpn/script/test_connect_db.sh' #!/bin/bash . /etc/openvpn/script/config.sh ##Test Authentication username=$1 password=$2 user_id=$(mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -sN -e "select user_id from user where user_id = '$username' AND user_pass = '$password' AND user_enable=1 AND user_start_date != user_end_date AND TO_DAYS(now()) >= TO_DAYS(user_start_date) AND (TO_DAYS(now()) <= TO_DAYS(user_end_date) OR user_end_date='0000-00-00')") ##Check user [ "$user_id" != '' ] && [ "$user_id" = "$username" ] && echo "user : $username" && echo 'authentication ok.' && exit 0 || echo 'authentication failed.'; exit 1 Create file login.sh '/etc/openvpn/script/login.sh' #!/bin/bash . /etc/openvpn/script/config.sh ##Authentication user_id=$(mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -sN -e "select user_id from user where user_id = '$username' AND user_pass = '$password' AND user_enable=1 AND user_start_date != user_end_date AND TO_DAYS(now()) >= TO_DAYS(user_start_date) AND (TO_DAYS(now()) <= TO_DAYS(user_end_date) OR user_end_date='0000-00-00')") ##Check user [ "$user_id" != '' ] && [ "$user_id" = "$username" ] && echo "user : $username" && echo 'authentication ok.' && exit 0 || echo 'authentication failed.'; exit 1
- 17. Create file connect.sh '/etc/openvpn/script/connect.sh' #!/bin/bash . /etc/openvpn/script/config.sh ##insert data connection to table log mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -e "INSERT INTO log (log_id,user_id,log_trusted_ip,log_trusted_port,log_remote_ip,log_remote_port,log_start_time,log_end_time,log_re ceived,log_send) VALUES(NULL,'$common_name','$trusted_ip','$trusted_port','$ifconfig_pool_remote_ip','$remote_port_1',now(),'00 00-00-00 00:00:00','$bytes_received','$bytes_sent')" ##set status online to user connected mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -e "UPDATE user SET user_online=1 WHERE user_id='$common_name'" Create file disconnect.sh '/etc/openvpn/script/disconnect.sh' #!/bin/bash . /etc/openvpn/script/config.sh ##set status offline to user disconnected mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -e "UPDATE user SET user_online=0 WHERE user_id='$common_name'" ##insert data disconnected to table log mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -e "UPDATE log SET log_end_time=now(),log_received='$bytes_received',log_send='$bytes_sent' WHERE log_trusted_ip='$trusted_ip' AND log_trusted_port='$trusted_port' AND user_id='$common_name' AND log_end_time='0000-00-00 00:00:00'" Strating and make Open VPN Server Starting at System Boot Start the OpenVPN Server: /sbin/service openvpn restart Setup OpenVPN to start on boot: chkconfig openvpn on Compose OpenVPN configuration files, OpenVPN server will scan .conf files in /etc/openvpn when it starts. For each file, it forks a daemon. In this system, we need both UDP and TCP support. I created two configuration files for two daemons in charge of UDP and TCP respectively. Test VPN Tunnel Establishment Trace on 192.168.0.204 Access Server tail -f /var/log/openvpn-status.log tail -f /var/log/openvpn.log tcpdump tracert {your destination ip} Configuring the Client Side Open VPN Client Server (10.10.10.2/24) First, we need OpenVPN. Grab the latest stable release from here and compile it on both the server side OpenVPN machine and the client side OpenVPN machine. Download, unpack, configure, compile and install The OpenVPN server and pkcs11-helper packages are not available on the default CentOS repositories. You may either install the
- 18. Fedora Extra Packages for Enterprise Linux (EPEL) repo or the RPMForge Repo at the links below. Alternatively you may download the packages from the EPEL repo site here, and here and install them manually: Install Packages Add repository EPEL that is provided from Fedora project. wget http://ftp.riken.jp/Linux/fedora/epel/RPM-GPG-KEY-EPEL-5 rpm --import RPM-GPG-KEY-EPEL-5 rm -f RPM-GPG-KEY-EPEL-5 vim /etc/yum.repos.d/epel.repo [epel] name=EPEL RPM Repository for Red Hat Enterprise Linux baseurl=http://ftp.riken.jp/Linux/fedora/epel/5/$basearch/ gpgcheck=1 enabled=0 rpm –Uvh http://dl.fedoraproject.org/pub/epel/5/x86_64/epel-release-5-4.noarch.rpm yum --enablerepo=epel -y install openvpn lzo policycoreutils-python /sbin/service openvpn start Starting openvpn: [ OK ] mkdir /etc/openvpn Add Key Files Copy the branch-1.crt, branch-1.key, ta.key and ca.crt files form 192.168.0.200 to the 10.10.10.2 Open VPN Client’s - config /Configuration folder (/etc/openvpn) You can use WinSCP to Transfer what ever key files form Linux server to Windows PC via SSH Exsisting root login. Strating and make Open VPN Client Server Starting at System Boot Start the OpenVPN Server: sudo /sbin/service openvpn restart Starting openvpn: [ OK ] Setup OpenVPN to start on boot: chkconfig openvpn on Enable IP Forwarding (Highly Important!) If you want your OpenVPN clients to be able to access the network, in addition to the push routes statements above you will need to setup ip forwarding for the tunnel interface and change the 0 to a 1. vi /etc/sysctl.conf # ------ Edit the following line changing the 0 to a 1 ----- net.ipv4.ip_forward = 1 Save and close the file. Reload the changes by typing the following command: Or echo "1" > /proc/sys/net/ipv4/ip_forward echo "1" > /proc/sys/net/ipv4/ip_dynaddr sysctl -p
- 19. Configure IPTables and SELinux on Client VPN Server (10.10.10.2/24) service iptables start iptables –-flush iptables --table nat -–flush iptables --delete-chain service iptables save service iptables restart service network restart iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT DROP iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o tun0 -j ACCEPT iptables -A FORWARD -i tun1 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o tun1 -j ACCEPT iptables -A INPUT -p ICMP -s 10.8.0.0/24 -j ACCEPT iptables -A INPUT -p ICMP -s 10.0.0.0/24 -j ACCEPT iptables -A INPUT -p icmp -m limit --limit 1/s --limit-burst 2 -j ACCEPT iptables -A INPUT -p icmp -j ACCEPT iptables -A OUTPUT -p icmp -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT iptables -A INPUT -m state --state INVALID -j DROP iptables -A OUTPUT -m state --state INVALID -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL ALL -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL NONE -j DROP iptables -A INPUT -p tcp --tcp-flags ALL FIN,URG,PSH -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP iptables -N SYN_FLOOD iptables -A INPUT -p tcp --syn -j SYN_FLOOD iptables -A SYN_FLOOD -m limit --limit 2/s --limit-burst 6 -j RETURN iptables -A SYN_FLOOD -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type address-mask-request -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type timestamp-request -j DROP iptables -A INPUT -p icmp -m icmp -m limit --limit 1/second -j ACCEPT iptables -A INPUT -p tcp -m tcp --tcp-flags RST RST -m limit --limit 2/second --limit-burst 2 -j ACCEPT iptables -A INPUT -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A FORWARD -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A INPUT -m recent --name portscan --remove iptables -A FORWARD -m recent --name portscan –remove iptables -A INPUT -s 0.0.0.0/7 -j DROP iptables -A INPUT -s 2.0.0.0/8 -j DROP iptables -A INPUT -s 5.0.0.0/8 -j DROP
- 20. iptables -A INPUT -s 7.0.0.0/8 -j DROP iptables -A INPUT -s 10.0.0.0/8 -j DROP iptables -A INPUT -s 23.0.0.0/8 -j DROP iptables -A INPUT -s 27.0.0.0/8 -j DROP iptables -A INPUT -s 31.0.0.0/8 -j DROP iptables -A INPUT -s 36.0.0.0/7 -j DROP iptables -A INPUT -s 39.0.0.0/8 -j DROP iptables -A INPUT -s 42.0.0.0/8 -j DROP iptables -A INPUT -s 49.0.0.0/8 -j DROP iptables -A INPUT -s 50.0.0.0/8 -j DROP iptables -A INPUT -s 77.0.0.0/8 -j DROP iptables -A INPUT -s 78.0.0.0/7 -j DROP iptables -A INPUT -s 92.0.0.0/6 -j DROP iptables -A INPUT -s 96.0.0.0/4 -j DROP iptables -A INPUT -s 112.0.0.0/5 -j DROP iptables -A INPUT -s 120.0.0.0/8 -j DROP iptables -A INPUT -s 169.254.0.0/16 -j DROP iptables -A INPUT -s 172.16.0.0/12 -j DROP iptables -A INPUT -s 173.0.0.0/8 -j DROP iptables -A INPUT -s 174.0.0.0/7 -j DROP iptables -A INPUT -s 176.0.0.0/5 -j DROP iptables -A INPUT -s 184.0.0.0/6 -j DROP iptables -A INPUT -s 192.0.2.0/24 -j DROP iptables -A INPUT -s 197.0.0.0/8 -j DROP iptables -A INPUT -s 198.18.0.0/15 -j DROP iptables -A INPUT -s 223.0.0.0/8 -j DROP iptables -A INPUT -s 224.0.0.0/3 -j DROP iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A FORWARD -i tun0 -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun1 -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun0 -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun1 -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT
- 21. iptables -A FORWARD -p icmp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 20.20.20.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 20.20.20.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 20.20.20.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 192.168.0.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 192.168.0.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 192.168.0.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP service iptables save service iptables restart service network restart /sbin/iptables -L iptables -L -t nat –n iptables -vnL /sbin/service openvpn restart Editing Open VPN Access Server’s Main Config File(branch-1.conf) Finally, we need to edit the OpenVPN config file. OpenVPN ships with a collection of good example config files (found in ~/openvpn-2.0.9/sample-config-files) that are very well documented starting points. The man page is also very well written and contains loads of useful information. For this example, the OpenVPN Client server's config file (branch-1.conf) cd /etc/openvpn vim branch-1.conf client dev tun proto udp remote 112.135.73.26 1194 resolv-retry infinite route 192.168.0.0 255.255.255.0 route 20.20.20.0 255.255.255.0 persist-key persist-tun ca ca.crt cert branch-1.crt key branch-1.key tls-auth ta.key 1 cipher AES-256-CBC comp-lzo verb 4
- 22. Start Initializing & Strart the Open VPN Clent Server on branch-1.conf openvpn branch-1.conf Start the OpenVPN Server: /sbin/service openvpn restart Setup OpenVPN to start on boot: chkconfig openvpn on Compose OpenVPN configuration files, OpenVPN server will scan .conf files in /etc/openvpn when it starts. For each file, it forks a daemon. In this system, we need both UDP and TCP support. I created two configuration files for two daemons in charge of UDP and TCP respectively Test VPN Tunnel Establishment Trace on 10.10.10.2/24 Client Server tail -f /var/log/openvpn-status.log tail -f /var/log/openvpn.log tcpdump tracert {your destination ip} ping 10.8.0.1 -c 2 PING 10.8.0.1 (10.8.0.1) 56(84) bytes of data. 64 bytes from 10.8.0.1: icmp_seq=1 ttl=64 time=21.1 ms 64 bytes from 10.8.0.1: icmp_seq=2 ttl=64 time=14.8 ms FINISHED You should not be able to select the connection from the client and connect to your server. Once connected you should be able to ping your server's private IP, and other IP's on your network. If forwarding DNS servers you should be able to dig google.com. Configuring the Client Side Open VPN Client Server (20.20.20.2/24) First, we need OpenVPN. Grab the latest stable release from here and compile it on both the server side OpenVPN machine and the client side OpenVPN machine. Download, unpack, configure, compile and install The OpenVPN server and pkcs11-helper packages are not available on the default CentOS repositories. You may either install the Fedora Extra Packages for Enterprise Linux (EPEL) repo or the RPMForge Repo at the links below. Alternatively you may download the packages from the EPEL repo site here, and here and install them manually: Install Packages Add repository EPEL that is provided from Fedora project. wget http://ftp.riken.jp/Linux/fedora/epel/RPM-GPG-KEY-EPEL-5 rpm --import RPM-GPG-KEY-EPEL-5 rm -f RPM-GPG-KEY-EPEL-5 vim /etc/yum.repos.d/epel.repo [epel] name=EPEL RPM Repository for Red Hat Enterprise Linux baseurl=http://ftp.riken.jp/Linux/fedora/epel/5/$basearch/ gpgcheck=1
- 23. enabled=0 rpm –Uvh http://dl.fedoraproject.org/pub/epel/5/x86_64/epel-release-5-4.noarch.rpm yum --enablerepo=epel -y install openvpn lzo policycoreutils-python /sbin/service openvpn start Starting openvpn: [ OK ] mkdir /etc/openvpn Add Key Files Copy the branch-2.crt, branch-2.key, ta.key and ca.crt files form 192.168.0.200 to the 20.20.20.2 Open VPN Client’s - config /Configuration folder (/etc/openvpn) You can use WinSCP to Transfer what ever key files form Linux server to Windows PC via SSH Exsisting root login. Strating and make Open VPN Client Server Starting at System Boot Start the OpenVPN Server: sudo /sbin/service openvpn restart Starting openvpn: [ OK ] Setup OpenVPN to start on boot: chkconfig openvpn on Enable IP Forwarding (Highly Important!) If you want your OpenVPN clients to be able to access the network, in addition to the push routes statements above you will need to setup ip forwarding for the tunnel interface and change the 0 to a 1. vi /etc/sysctl.conf # ------ Edit the following line changing the 0 to a 1 ----- net.ipv4.ip_forward = 1 Save and close the file. Reload the changes by typing the following command: Or echo "1" > /proc/sys/net/ipv4/ip_forward echo "1" > /proc/sys/net/ipv4/ip_dynaddr sysctl -p Configure IPTables and SELinux on Client VPN Server (20.20.20.2/24) service iptables start iptables –-flush iptables --table nat -–flush iptables --delete-chain service iptables save service iptables restart service network restart iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT DROP
- 24. iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT iptables -A FORWARD -i tun0 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o tun0 -j ACCEPT iptables -A FORWARD -i tun1 -o eth0 -j ACCEPT iptables -A FORWARD -i eth0 -o tun1 -j ACCEPT iptables -A INPUT -p ICMP -s 10.8.0.0/24 -j ACCEPT iptables -A INPUT -p ICMP -s 10.0.0.0/24 -j ACCEPT iptables -A INPUT -p icmp -m limit --limit 1/s --limit-burst 2 -j ACCEPT iptables -A INPUT -p icmp -j ACCEPT iptables -A OUTPUT -p icmp -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT iptables -A INPUT -m state --state INVALID -j DROP iptables -A OUTPUT -m state --state INVALID -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL ALL -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL NONE -j DROP iptables -A INPUT -p tcp --tcp-flags ALL FIN,URG,PSH -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP iptables -N SYN_FLOOD iptables -A INPUT -p tcp --syn -j SYN_FLOOD iptables -A SYN_FLOOD -m limit --limit 2/s --limit-burst 6 -j RETURN iptables -A SYN_FLOOD -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type address-mask-request -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type timestamp-request -j DROP iptables -A INPUT -p icmp -m icmp -m limit --limit 1/second -j ACCEPT iptables -A INPUT -p tcp -m tcp --tcp-flags RST RST -m limit --limit 2/second --limit-burst 2 -j ACCEPT iptables -A INPUT -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A FORWARD -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A INPUT -m recent --name portscan --remove iptables -A FORWARD -m recent --name portscan –remove iptables -A INPUT -s 0.0.0.0/7 -j DROP iptables -A INPUT -s 2.0.0.0/8 -j DROP iptables -A INPUT -s 5.0.0.0/8 -j DROP iptables -A INPUT -s 7.0.0.0/8 -j DROP iptables -A INPUT -s 10.0.0.0/8 -j DROP iptables -A INPUT -s 23.0.0.0/8 -j DROP iptables -A INPUT -s 27.0.0.0/8 -j DROP iptables -A INPUT -s 31.0.0.0/8 -j DROP iptables -A INPUT -s 36.0.0.0/7 -j DROP iptables -A INPUT -s 39.0.0.0/8 -j DROP iptables -A INPUT -s 42.0.0.0/8 -j DROP iptables -A INPUT -s 49.0.0.0/8 -j DROP iptables -A INPUT -s 50.0.0.0/8 -j DROP iptables -A INPUT -s 77.0.0.0/8 -j DROP
- 25. iptables -A INPUT -s 78.0.0.0/7 -j DROP iptables -A INPUT -s 92.0.0.0/6 -j DROP iptables -A INPUT -s 96.0.0.0/4 -j DROP iptables -A INPUT -s 112.0.0.0/5 -j DROP iptables -A INPUT -s 120.0.0.0/8 -j DROP iptables -A INPUT -s 169.254.0.0/16 -j DROP iptables -A INPUT -s 172.16.0.0/12 -j DROP iptables -A INPUT -s 173.0.0.0/8 -j DROP iptables -A INPUT -s 174.0.0.0/7 -j DROP iptables -A INPUT -s 176.0.0.0/5 -j DROP iptables -A INPUT -s 184.0.0.0/6 -j DROP iptables -A INPUT -s 192.0.2.0/24 -j DROP iptables -A INPUT -s 197.0.0.0/8 -j DROP iptables -A INPUT -s 198.18.0.0/15 -j DROP iptables -A INPUT -s 223.0.0.0/8 -j DROP iptables -A INPUT -s 224.0.0.0/3 -j DROP iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A FORWARD -i tun0 -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun1 -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.8.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun0 -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -i tun1 -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.0.0.0/24 -d 192.168.0.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 10.10.10.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 10.10.10.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 10.10.10.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p tcp -s 192.168.0.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p udp -s 192.168.0.0/24 -d 10.10.10.0/24 -j ACCEPT iptables -A FORWARD -p icmp -s 192.168.0.0/24 -d 10.10.10.0/24 -j ACCEPT
- 26. iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP service iptables save service iptables restart service network restart /sbin/iptables -L iptables -L -t nat –n Editing Open VPN Access Server’s Main Config File(branch-2.conf) Finally, we need to edit the OpenVPN config file. OpenVPN ships with a collection of good example config files (found in ~/openvpn-2.0.9/sample-config-files) that are very well documented starting points. The man page is also very well written and contains loads of useful information. For this example, the OpenVPN Client server's config file (branch-2.conf) cd /etc/openvpn vim branch-2.conf client dev tun proto udp remote 112.135.73.26 1194 resolv-retry infinite route 192.168.0.0 255.255.255.0 route 10.10.10.0 255.255.255.0 persist-key persist-tun ca ca.crt cert branch-2.crt key branch-2.key tls-auth ta.key 1 cipher AES-256-CBC comp-lzo verb 4 Start Initializing & Strart the Open VPN Clent Server on branch-2.conf openvpn branch-2.conf Start the OpenVPN Server: /sbin/service openvpn restart Setup OpenVPN to start on boot: chkconfig openvpn on Compose OpenVPN configuration files, OpenVPN server will scan .conf files in /etc/openvpn when it starts. For each
- 27. file, it forks a daemon. In this system, we need both UDP and TCP support. I created two configuration files for two daemons in charge of UDP and TCP respectively Test VPN Tunnel Establishment Trace on 20.20.20.2/24 Client Server tail -f /var/log/openvpn-status.log tail -f /var/log/openvpn.log tcpdump tracert {your destination ip} ping 10.8.0.1 -c 2 PING 10.8.0.1 (10.8.0.1) 56(84) bytes of data. 64 bytes from 10.8.0.1: icmp_seq=1 ttl=64 time=21.1 ms 64 bytes from 10.8.0.1: icmp_seq=2 ttl=64 time=14.8 ms FINISHED You should not be able to select the connection from the client and connect to your server. Once connected you should be able to ping your server's private IP, and other IP's on your network. If forwarding DNS servers you should be able to dig google.com. Open VPN Visiting Client config and installing Open VPN Clinet Software (UK Client with MySQL Database User Athentication) Download and install the OpenVPN client installer file from the below Link OpenVPN client Download link (works with WindowsXP,Vista and Windows7) Note: Installing client and initializing the VPN connection requires Administrator privileges. After installatling OpenVPN client, Copy C:Program FilesOpenVPNsample-configclient.ovpn to C:Program FilesOpenVPNconfigclient.ovpn And open the client.ovpn file and edit like below OpenVPN client Download link Copy the ta.key and ca.crt files form 192.168.0.204 to the your’s Laptop Open VPN Client’s -config /Configuration folder “C:Program FilesOpenVPNconfig” Copy C:Program FilesOpenVPNsample-configclient.ovpn to C:Program FilesOpenVPNconfigclient.ovpn client dev tun proto tcp remote 112.135.73.26 1194 reneg-sec 432000 nobind auth-user-pass resolv-retry infinite route 192.168.2.0 255.255.255.0 route 20.20.20.0 255.255.255.0 route 10.10.10.0 255.255.255.0 user nobody
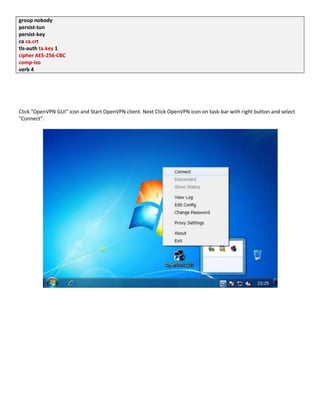
- 28. group nobody persist-tun persist-key ca ca.crt tls-auth ta.key 1 cipher AES-256-CBC comp-lzo verb 4 Click "OpenVPN GUI" icon and Start OpenVPN client. Next Click OpenVPN icon on task-bar with right button and select "Connect".
- 29. Open VPN Visiting Client config and installing Open VPN Clinet Software (USA Client With Client Private Key Athentication with Only on VPN Server) Download and install the OpenVPN client installer file from the below Link OpenVPN client Download link (works with WindowsXP,Vista and Windows7) Note: Installing client and initializing the VPN connection requires Administrator privileges. After installatling OpenVPN client, Copy C:Program FilesOpenVPNsample-configclient.ovpn to C:Program FilesOpenVPNconfigclient.ovpn And open the client.ovpn file and edit like below OpenVPN client Download link Copy the ta.key, client-1.key, client-1.crt and ca.crt files form 192.168.2.204 to the your’s Laptop Open VPN Client’s - config /Configuration folder “C:Program FilesOpenVPNconfig” Copy C:Program FilesOpenVPNsample-configclient.ovpn to C:Program FilesOpenVPNconfigclient.ovpn client dev tun proto tcp remote 112.135.73.26 444 reneg-sec 432000 resolv-retry infinite route 192.168.2.0 255.255.255.0 route 20.20.20.0 255.255.255.0 route 10.10.10.0 255.255.255.0 user nobody group nobody persist-tun
- 30. persist-key ca ca.crt cert client-1.crt key client-1.key tls-auth ta.key 1 cipher AES-256-CBC comp-lzo verb 4 Test VPN Tunnel Establishment Trace on Client Laptop ping 10.0.0.1 -t PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data. 64 bytes from 10.0.0.1: icmp_seq=1 ttl=64 time=21.1 ms 64 bytes from 10.0.0.1: icmp_seq=2 ttl=64 time=14.8 ms tracert 192.168.0.200 or what ever Head Office LAN PC FINISHED You should not be able to select the connection from the client and connect to your server. Once connected you should be able to ping your server's private IP, and other IP's on your network. If forwarding DNS servers you should be able to dig google.com. Troubleshooting There are quite a few pieces that have to play nicely together to get OpenVPN working correctly. Here are a few tools that come in handy if things don't work smoothly right out of the gates. Check the OpenVPN logs There is lots of good information in there that can point you right to the problem. This is especially handy when tweaking the config files. Increase the verbosity This will show you more of what OpenVPN is thinking. A verbosity level of 5 or 6 is pretty handy for high level checking, anything higher is great for really tracking where packets are going. Use "tcpdump" tcpdump is a great network troubleshooting tool, especially since both OpenVPN machines are acting as routers. Check the tcpdump man page for more details. Take baby steps! Build up the VPN incrementally and test the connection along the way. (i.e. bring up





![rpm --import RPM-GPG-KEY-EPEL-5
rm -f RPM-GPG-KEY-EPEL-5
vim /etc/yum.repos.d/epel.repo
[epel] name=EPEL RPM Repository for Red Hat Enterprise Linux
baseurl=http://ftp.riken.jp/Linux/fedora/epel/5/$basearch/ gpgcheck=1 enabled=0
rpm –Uvh http://dl.fedoraproject.org/pub/epel/5/x86_64/epel-release-5-4.noarch.rpm
yum --enablerepo=epel -y install openvpn lzo policycoreutils-python
/sbin/service openvpn start
Starting openvpn: [ OK ]
Install MySQL Server
yum -y install mysql-server
/etc/rc.d/init.d/mysqld start
chkconfig mysqld on
/usr/bin/mysql_secure_installation
Log in MySQL as root
mysql -uroot -p
Create the database 'openvpn'
CREATE DATABASE openvpn;
Create a MySQL user with username 'USERNAME' and password 'PASSWORD'
GRANT ALL ON openvpn.* TO 'USERNAME'@"%" IDENTIFIED BY 'PASSWORD';
exit;
Log in MySQL as new user 'USERNAME'
mysql -uUSERNAME -pPASSWORD
Switch database
USE openvpn;
Create user, log table and insert user data
- user table
CREATE TABLE IF NOT EXISTS `user` (
`user_id` varchar(32) COLLATE utf8_unicode_ci NOT NULL,
`user_pass` varchar(32) COLLATE utf8_unicode_ci NOT NULL DEFAULT '1234',
`user_mail` varchar(64) COLLATE utf8_unicode_ci DEFAULT NULL,
`user_phone` varchar(16) COLLATE utf8_unicode_ci DEFAULT NULL,](https://image.slidesharecdn.com/site-to-multisiteopenvpnsolutionwithmysqldb-200213033704/85/Site-to-multi-site-open-vpn-solution-with-mysql-db-5-320.jpg)










![verb 5
Create directory for script '/etc/openvpn/script'
mkdir /etc/openvpn/script
cd /etc/openvpn/script
Create file config.sh '/etc/openvpn/script/config.sh'
#!/bin/bash
##Dababase Server
HOST='192.168.0.204'
#Default port = 3306
PORT='3306'
#Username
USER='USERNAME'
#Password
PASS='PASSWORD'
#database name
DB='openvpn'
Create file test_connect_db.sh'/etc/openvpn/script/test_connect_db.sh'
#!/bin/bash
. /etc/openvpn/script/config.sh
##Test Authentication
username=$1
password=$2
user_id=$(mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -sN -e "select user_id from user where user_id =
'$username' AND user_pass = '$password' AND user_enable=1 AND user_start_date != user_end_date AND
TO_DAYS(now()) >= TO_DAYS(user_start_date) AND (TO_DAYS(now()) <= TO_DAYS(user_end_date) OR
user_end_date='0000-00-00')")
##Check user
[ "$user_id" != '' ] && [ "$user_id" = "$username" ] && echo "user : $username" && echo 'authentication ok.' && exit
0 || echo 'authentication failed.'; exit 1
Create file login.sh '/etc/openvpn/script/login.sh'
#!/bin/bash
. /etc/openvpn/script/config.sh
##Authentication
user_id=$(mysql -h$HOST -P$PORT -u$USER -p$PASS $DB -sN -e "select user_id from user where user_id =
'$username' AND user_pass = '$password' AND user_enable=1 AND user_start_date != user_end_date AND
TO_DAYS(now()) >= TO_DAYS(user_start_date) AND (TO_DAYS(now()) <= TO_DAYS(user_end_date) OR
user_end_date='0000-00-00')")
##Check user
[ "$user_id" != '' ] && [ "$user_id" = "$username" ] && echo "user : $username" && echo 'authentication ok.' && exit
0 || echo 'authentication failed.'; exit 1](https://image.slidesharecdn.com/site-to-multisiteopenvpnsolutionwithmysqldb-200213033704/85/Site-to-multi-site-open-vpn-solution-with-mysql-db-16-320.jpg)

![Fedora Extra Packages for Enterprise Linux (EPEL) repo or the RPMForge Repo at the links below. Alternatively
you may download the packages from the EPEL repo site here, and here and install them manually:
Install Packages
Add repository EPEL that is provided from Fedora project.
wget http://ftp.riken.jp/Linux/fedora/epel/RPM-GPG-KEY-EPEL-5
rpm --import RPM-GPG-KEY-EPEL-5
rm -f RPM-GPG-KEY-EPEL-5
vim /etc/yum.repos.d/epel.repo
[epel] name=EPEL RPM Repository for Red Hat Enterprise Linux
baseurl=http://ftp.riken.jp/Linux/fedora/epel/5/$basearch/ gpgcheck=1 enabled=0
rpm –Uvh http://dl.fedoraproject.org/pub/epel/5/x86_64/epel-release-5-4.noarch.rpm
yum --enablerepo=epel -y install openvpn lzo policycoreutils-python
/sbin/service openvpn start
Starting openvpn: [ OK ]
mkdir /etc/openvpn
Add Key Files
Copy the branch-1.crt, branch-1.key, ta.key and ca.crt files form 192.168.0.200 to the 10.10.10.2 Open VPN Client’s -
config /Configuration folder (/etc/openvpn)
You can use WinSCP to Transfer what ever key files form Linux server to Windows PC via SSH Exsisting root login.
Strating and make Open VPN Client Server Starting at System Boot
Start the OpenVPN Server:
sudo /sbin/service openvpn restart
Starting openvpn: [ OK ]
Setup OpenVPN to start on boot:
chkconfig openvpn on
Enable IP Forwarding (Highly Important!)
If you want your OpenVPN clients to be able to access the network, in addition to the push routes statements above
you will need to setup ip forwarding for the tunnel interface and change the 0 to a 1.
vi /etc/sysctl.conf
# ------ Edit the following line changing the 0 to a 1 -----
net.ipv4.ip_forward = 1
Save and close the file. Reload the changes by typing the following command:
Or
echo "1" > /proc/sys/net/ipv4/ip_forward
echo "1" > /proc/sys/net/ipv4/ip_dynaddr
sysctl -p](https://image.slidesharecdn.com/site-to-multisiteopenvpnsolutionwithmysqldb-200213033704/85/Site-to-multi-site-open-vpn-solution-with-mysql-db-18-320.jpg)



![Start Initializing & Strart the Open VPN Clent Server on branch-1.conf
openvpn branch-1.conf
Start the OpenVPN Server:
/sbin/service openvpn restart
Setup OpenVPN to start on boot:
chkconfig openvpn on
Compose OpenVPN configuration files, OpenVPN server will scan .conf files in /etc/openvpn when it starts. For each
file, it forks a daemon. In this system, we need both UDP and TCP support. I created two configuration files for two
daemons in charge of UDP and TCP respectively
Test VPN Tunnel Establishment Trace on 10.10.10.2/24 Client Server
tail -f /var/log/openvpn-status.log
tail -f /var/log/openvpn.log
tcpdump
tracert {your destination ip}
ping 10.8.0.1 -c 2
PING 10.8.0.1 (10.8.0.1) 56(84) bytes of data.
64 bytes from 10.8.0.1: icmp_seq=1 ttl=64 time=21.1 ms
64 bytes from 10.8.0.1: icmp_seq=2 ttl=64 time=14.8 ms
FINISHED
You should not be able to select the connection from the client and connect to your server. Once connected you should
be able to ping your server's private IP, and other IP's on your network. If forwarding DNS servers you should be able to
dig google.com.
Configuring the Client Side Open VPN Client Server (20.20.20.2/24)
First, we need OpenVPN. Grab the latest stable release from here and compile it on both the server side OpenVPN
machine and the client side OpenVPN machine. Download, unpack, configure, compile and install The OpenVPN
server and pkcs11-helper packages are not available on the default CentOS repositories. You may either install the
Fedora Extra Packages for Enterprise Linux (EPEL) repo or the RPMForge Repo at the links below. Alternatively
you may download the packages from the EPEL repo site here, and here and install them manually:
Install Packages
Add repository EPEL that is provided from Fedora project.
wget http://ftp.riken.jp/Linux/fedora/epel/RPM-GPG-KEY-EPEL-5
rpm --import RPM-GPG-KEY-EPEL-5
rm -f RPM-GPG-KEY-EPEL-5
vim /etc/yum.repos.d/epel.repo
[epel]
name=EPEL RPM Repository for Red Hat Enterprise
Linux baseurl=http://ftp.riken.jp/Linux/fedora/epel/5/$basearch/
gpgcheck=1](https://image.slidesharecdn.com/site-to-multisiteopenvpnsolutionwithmysqldb-200213033704/85/Site-to-multi-site-open-vpn-solution-with-mysql-db-22-320.jpg)
![enabled=0
rpm –Uvh http://dl.fedoraproject.org/pub/epel/5/x86_64/epel-release-5-4.noarch.rpm
yum --enablerepo=epel -y install openvpn lzo policycoreutils-python
/sbin/service openvpn start
Starting openvpn: [ OK ]
mkdir /etc/openvpn
Add Key Files
Copy the branch-2.crt, branch-2.key, ta.key and ca.crt files form 192.168.0.200 to the 20.20.20.2 Open VPN Client’s -
config /Configuration folder (/etc/openvpn)
You can use WinSCP to Transfer what ever key files form Linux server to Windows PC via SSH Exsisting root login.
Strating and make Open VPN Client Server Starting at System Boot
Start the OpenVPN Server:
sudo /sbin/service openvpn restart
Starting openvpn: [ OK ]
Setup OpenVPN to start on boot:
chkconfig openvpn on
Enable IP Forwarding (Highly Important!)
If you want your OpenVPN clients to be able to access the network, in addition to the push routes statements above
you will need to setup ip forwarding for the tunnel interface and change the 0 to a 1.
vi /etc/sysctl.conf
# ------ Edit the following line changing the 0 to a 1 -----
net.ipv4.ip_forward = 1
Save and close the file. Reload the changes by typing the following command:
Or
echo "1" > /proc/sys/net/ipv4/ip_forward
echo "1" > /proc/sys/net/ipv4/ip_dynaddr
sysctl -p
Configure IPTables and SELinux on Client VPN Server (20.20.20.2/24)
service iptables start
iptables –-flush
iptables --table nat -–flush
iptables --delete-chain
service iptables save
service iptables restart
service network restart
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT DROP](https://image.slidesharecdn.com/site-to-multisiteopenvpnsolutionwithmysqldb-200213033704/85/Site-to-multi-site-open-vpn-solution-with-mysql-db-23-320.jpg)