SOC Architecture Workshop - Part 1
- 1. Advanced SOC Advanced SOC Features and Capabilities Use Case Management – Workshop Incident Management
- 2. Traditional SOCs were driven by Compliance and Have the basic features as follows:- 1. Detect and react to threats, mostly triggered by log correlation rules 2. Perform log collection, correlation and monitoring to meet compliance requirements. 3. SIEM tradionally has log collectors/connectors to collect logs from multiple sources and loggers/processors for processing and storing log data for several years (6 months online and 7-8 years offline) and a console for monitoring events. 4. Monitor attacks and detect threats to manage and respond to those attacks Alerting for incidents/ critical actions. 5. A ticketing system is generally used to track tickets for security violations. 6. Generic and compliance focused use cases, mostly single device correlation and generates generic reports 7. Popular models were in house and outsourced / leveraged SOC Next generation SOCs are driven by threat mitigation, proactive monitoring and intelligence 1. More focus on identifying new / unknown threats and anticipate threats and mitigate risks 2. Integrate with NBAD, forensics and Integration with threat intelligence communities and social sites – to predict the attack 3. Big data analysis a part of SOC tool set; Integrated with national agencies and international CERTs. 4. Proactively provide alerts for financial frauds and violations in business processes. SOC will act as a single agency to prevent security incidents, frauds happening in E-Systems, compliance of regional laws across geographic boundaries 5. Automated response run books, real live simulations and IM framework automated by workflow, collaboration and intelligence tools 6. Customized risk and threat aligned use cases, some modeled on kill chain concept and provides risk aligned and analytical reporting and visualization 7. Popular model changed to expertise based onsite and offshore managed SIEM model. 2 Evolution of A-SOC
- 3. 3 Advanced SOC - Features Threat Assessment and Hunting – Knowing Threats and Adversaries – Their tools and methods – Critical assets as targets – Existing Controls and Weakness – Monitoring presence , IOC Management and Hunting Threat Intelligence – Internal threat intelligence – External threat intelligence – Application of threat intelligence – Automated consumption of threat intelligence (updated SIEM rules/ runbook) Situational Awareness – Context and enrichment (Post correlation, joining the dots to see the attack chain) – Visibility (Visualization to the state of security) Security Analytics – Behavioral profiling for users and systems – Database searches and statistical modeling, reporting and visualization – Forensics capability (Netflow/ replay)
- 4. Requirement Capability Sources IAM Integration User Context User Activity Monitoring IAM Packaged Applications Unsupported Sources Network Application Monitoring Logs DLP Integration Data Context Data Monitoring Internal and External Intelligence Pattern Recognition Anomaly Detection Early Attack Detection Event Stream Integration Cloud-Sourced Application Monitoring Internal and Cloud 4 A-SOC Capabilities
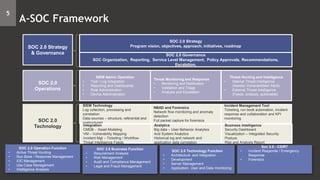
- 5. SOC 2.0 Strategy Program vision, objectives, approach, initiatives, roadmap SIEM Admin Operation • Tool / Log Integration • Reporting and Dashboards • Rule Administration • Device Administration Threat Monitoring and Response • Monitoring and Notification • Validation and Triage • Analysis and Escalation Threat Hunting and Intelligence • Internal Threat Intelligence (Assets/ Vulnerabilities/ Alerts • External Threat Intelligence (Feeds, analysis, actionable) SOC 2.0 Governance SOC Organization, Reporting, Service Level Management, Policy Approvals, Recommendations, Escalation. NBAD and Forensics Network flow monitoring and anomaly detection Full packet capture for forensics SOC 2.0 Operation Function • Active Threat Hunting • Run Book / Response Management • IOC Management • Use Case Management • Intelligence Analysis SOC 2.0 Strategy & Governance SOC 2.0 Operations SIEM Technology Log collection, processing and correlation Data sources – structure, referential and unstructured Incident Management Tool Ticketing, run book automation, incident response and collaboration and KPI monitoring SOC 2.0 Technology Analytics Big data – User Behavior Analytics And System Analytics Historical log and network and application data correlation Integration CMDB - Asset Modeling VM – Vulnerability Mapping Incident Mgt – Ticketing / Workflow Threat Intelligence Feeds Business Intelligence Security Dashboard Visualization – Integrated Security Posture Risk and Analysis Report SOC 2.0 Business Function • Requirement Analysis • Risk Management • Audit and Compliance Management • Legal and Fraud Management SOC 2.0 Technology Function • Architecture and Integration • Development • Server Management • Application, User and Data monitoring Soc 2.0 - CSIRT • Incident Response / Emergency Response • Forensics 5 A-SOC Framework
- 6. • Data collection capabilities and compliance benefits of log management, • The correlation, normalization and analysis capabilities of SIEM (security information and event management) • The network visibility and advanced threat detection of NBAD (network behavior anomaly detection), and user behavior anomaly detection by machine learning - User Behavior Analytics • The ability to reduce breaches and ensure compliance provided by Risk Management, • The network traffic and application content insight afforded by Network Forensics. • The automation of Incident Response by Artificial Intelligence / Run Books • IOC / VM Management by Threat Intelligence • Reporting and Visualization provided by Presentation Layer SIEM as a platform should be a truly integrated solution built on a common codebase, with a single data management architecture and a single user interface. 6 A-SOC Technical Capabilities
- 7. Monitor everything Logs, network traffic, user activity Correlate intelligently Connect the dots of disparate activity Detect anomalies Unusual yet hidden behavior Prioritize for action Attack high-priority incidents Threat Intelligence • Logs • Contextual Data • Vulnerability Assessments • Asset Inventories • Reports and Analytics Internal • XFORCE • CrowdStrike • SecureWorks • Deepsight External Threat Ingestion - Structured Threat Information eXpression (STIX™) SIEM Environment Single, Unified and Integrated Management Console Machine Learning – Analytics Artificial Intelligence Incident Management Automation * Source - IBM 7 A-SOC Architecture
- 8. D A T A S O U R C E S L I N K E D D A T A A N A L Y S I S Security Data Network Data End Point/Identity data Firewall /IPS/IDS Threat Intel SIEM Alerts Network Data Flow Data Proxy/WiFi Data Endpoint Data User Data /AD Database Data Client Devices Assets Internal Servers Websites Users Dynamic Knowledge Extraction Source Collaboration ANALYTICSENGINE RISK ENGINE SEARCH EXPLORATION REPORTS RISKS ! • A-SOCs leverages Threat Intelligence from multiple commercial and open sources and integrated into a platform for collaboration, correlation, visualization and actionable analysis. • A-SOCs leverages Big Data Platform for UBA, System analytics, visualization and reporting. • Platform is also used for running hunt missions, query engine, reporting and AI for ticketing and incident remediation. 8 A-SOC Big Data Tool-Set – Analytics/ UBA and TH
- 9. • What all patterns have been built and what algorithm the technology uses for machine learning • How accurate is the system in detecting anomalies for malware and behavior • How does it compare it with other similar products; what criteria should be used for evaluation. • Threat Intelligence comes in many forms, difficult to ingest and requires capabilities and continuous analysis and actionables MACHINE LEARNING AND ARTIFICIAL INTELLIGENCE SECURITY ANALYTICS – NBAD AND END POINT AND USER ANALYTICS THREAT INTELLIGENCE AND HUNTING 9 A-SOC Technical Queries
- 10. Other Internal Teams Systems Applications Network Database Vulnerability / Patch Business Risk / Compliance Information Technology Information Security and Risk Management CISO CEO , COO, CRO Board / Shareholders Incident Responder L2/L3 SOC Analysts Service Desk L-1 Monitoring Team SOC Manager SIEM Admins Incident Response Threat Hunter Country CERT Regulatory Bodies CIO SOC Team Internal SOC organization associated roles and responsibilities should be clearly defined. The following is a sample organization structure. Threat Intelligence 10 A-SOC Organization Structure and Functions
- 11. Event Management • Event monitoring, analysis and correlation • Triage and Escalation • Containment • Proactive intelligence and situational awareness • Response collaboration Vulnerability & Patch Mgmt • Vulnerability research • Patch management • Identification • Dissemination • Compliance monitoring • Configuration / Control baselines • Antivirus signature management • Microsoft updates Incident Response • IM Charter, SIRT and TIG Reporting Structure, R&R • Incident Handling Process and Procedures for: • Identification, validation, declaration, escalation, containment, investigation, forensics, eradication, recovery, post incident • Cross functional RACI and coordindation for response • Forms and Templates Threat Specific Response Procedures • Phishhing / Spear Phishing • Malware (virus, worms, trojans, spyware) • NetFlow Abnormal Behavior Incident • Network Behavior Analysis Incident • (Distributed) Denial of Service • Domain hijack or DNS cache poisoning • Website defacement • Web application incident • Unauthorized access • User account compromise • Host compromise • Network compromise • Advanced persistent threat • Suspicious user activity SOC • Charter • Organization • Roles and responsibilities • Business requirements, scope and architecture • Service Catalogue • SOC operations and management procedures • SOC metrics and KPIs • SOC process and procedure manual (all processes and procedures including tool/solution specific) • SOC security policy • SOC business continuity and disaster recovery Threat Hunting • Threat Intelligence • Threat Hunting • Device / source inclusion and exclusion process 11 A-SOC Processes
- 12. 12 Advanced SOC Services • Custom parser creation and log source addition/integration per device type/days 1. Threat Hunting 2. Perform API integration of Vulnerability Management, Business Systems, CMDB etc. 3. Integrate with threat intelligence and automate responses with actionable Additional Services 1. Incident Management – Monitoring, Validation, Notification, Tracking Response and Closure 2. SIEM Administration – Managing Licenses, Patches, all SIEM Components, Health checks, log sources integrity, users and reports 3. Reporting and Dashboard – Creation and emailing the reports and dashboards to stakeholders with trend analysis 4. Use Case Management – New use case creation and fine tuning of existing use cases based on monitoring 5. Log Source Addition – Additional addition of devices and log sources, custom parser creation BAU Service
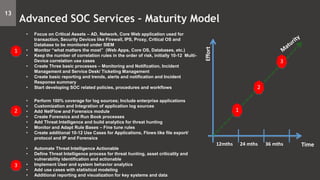
- 13. Effort Time 1 2 3 12mths 24 mths 36 mths 1 • Focus on Critical Assets – AD, Network, Core Web application used for transaction, Security Devices like Firewall, IPS, Proxy, Critical OS and Database to be monitored under SIEM • Monitor “what matters the most” (Web Apps, Core OS, Databases, etc.) • Keep the number of correlation rules in the order of risk, initially 10-12 Multi- Device correlation use cases • Create Three basic processes – Monitoring and Notification, Incident Management and Service Desk/ Ticketing Management • Create basic reporting and trends, alerts and notification and Incident Response summary • Start developing SOC related policies, procedures and workflows 2 • Perform 100% coverage for log sources; Include enterprise applications • Customization and Integration of application log sources • Add NetFlow and Forensics module • Create Forensics and Run Book processes • Add Threat Intelligence and build analytics for threat hunting • Monitor and Adapt Rule Bases – Fine tune rules • Create additional 10-12 Use Cases for Applications, Flows like file export/ protocol and IP and Forensics 3 • Automate Threat Intelligence Actionable • Define Threat Intelligence process for threat hunting, asset criticality and vulnerability identification and actionable • Implement User and system behavior analytics • Add use cases with statistical modeling • Additional reporting and visualization for key systems and data 13 Advanced SOC Services – Maturity Model
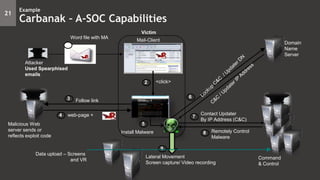
- 14. 21 Example Carbanak – A-SOC Capabilities 2 Malicious Web server sends or reflects exploit code <click> 1 Install Malware Mail-Client 5 Victim Domain Name Server Attacker Used Spearphised emails Command & Control 4 web-page + 3 Follow link Lateral Movement Screen capture/ Video recording 9 6 Remotely Control Malware Contact Updater By IP Address (C&C) 7 8 Word file with MA Data upload – Screens and VR
- 15. 22 Example Carbanak – A-SOC Capabilities 2 Malicious Web server sends or reflects exploit code <click> 1 Install Malware Mail-Client 5 Victim Domain Name Server Attacker Using Spearphised emails Command & Control 4 web-page + 3 Follow link 9 6 Remotely Control Malware Contact Updater By IP Address (C&C) 7 8 Word file with MA Lateral Movement Screen capture/ Video recording Data upload – Screens and VR d) Monitor Web Traffic a) Monitor DNS c) Monitor Port & Protocol Usage b) Monitor NetFlow e) Data in HTML Response - Netflow b) Monitor NetFlow
- 16. Advanced SOC Use Case Management – Workshop
- 17. 17 Use Case Introduction to Use Cases • Different names are used to define rules that generate alerts in SIEM • There common terminologies used are as follows • SIEM Rules • Correlation Rules • Use Cases • SIEM Alert is typically a rule which does not require enumeration and there is no correlation of 2 conditions. It is a simple log condition that is interesting. For example – Administrative password change, file access, new user added, new table created, configuration change, PO approved etc. • SIEM rules/ alerts are typically simple log matching rules, another example is If I see string ABC 123 in HIPS logs that raise an alert or alert me if the configuration of the router has changed. • One can create some conditions in SIEM alerts and call it a SIEM rule which gives context. For Example – Administrative password changed from XX IP for YY user which is in “white list”. Here too, there is nothing abnormal but an alert to state that interesting event has happened. One can investigate to see why the password was changed or similarly why a table was created and is there a change ticket or an approval for the same.
- 18. • Correlation is the act of linking multiple events together to detect strange behavior. It is the association of different but related events to provide broader context than a single event can provide. • Correlation rules aka known as chaining of SIEM rules or SIEM alerts/events and typically make 2 conditions to match. • Correlation is built on rules for known attack patterns. One has to know what elements constitutes an attack patterns or elements of a compliance requirement in order to determine which device and event types should be linked. Also while correlating we have to factor in the time, because events do not happen simultaneously, so there is a window of time within which events are likely to be related. • So in a nutshell a correlation rule is “combining of multiple SIEM rule/alerts”. It can be from the same device or desperate devices. • E.g. Failed login attempts followed by successful login is correlation condition from same device but a scan detected by firewall, followed by access to application from application logs and then creation of a user in the application is a directory service of database logs creating a COMPROMISE condition. 18 Use Case Co-relation Rules
- 19. • The term use case is used for one or more correlation rules to describe a condition. • A Use Case is a set of steps, representing a business goal or defining interactions between a role (or an "actor") and a system to achieve a goal. The actor can be a human or an external system. In a nutshell a use case in our term is a customized set of conditions occurring from a combination of one or more correlation rule, generally industry specific that constitute an attack vector and also has a response mechanism. • Every use case has a Logic Flow, i.e. something unique to the environment and needs to be defined accordingly. • Use Case Response: After implementation, the Use Case need to be made as a valuable resource by Defining a Use Case Response. This is the stage where you would define “What action needs to be taken and how it needs to be taken”. 19 Use Case Co-relation Rules
- 20. • Use Case Name - Privilege Activity Monitoring – Windows and Linux • Category: Access Control (AC) • Limit facility and information access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems) and to the authorized activities and transactions. • Use Case Number: 1 and 2 • Accounts having Privileged access, e.g. Admin, Sudo should be monitored on activity performed by ID. • References: • ISO/IEC 27001 A.11 • SANS Top 20: CSC 16 • PCI • Internal Policy Compliance • Use Case Description: • Accounts with administrator and/or root privileges should be monitored and flagged if they are locked due to multiple authentication failures. This could indicate potentially malicious activity and alerted on, accordingly. Generate report. • Log Sources: • Active Directory • UNIX Systems • Sample Rule Description: Privileged Role Violations: • Identify IDs not in Security Administration group that have made changes to user IDs and AD groups • Create an active list with users within the Security Admin group. • Create a rule to fire when a user not on the active list makes a change to a user ID and/or AD groups. • Event Name/Category - Use account got locked out • Event Attribute • - User Name • - Source IP Address/Host Name • - Destination IP Address/Host Name • - Event Name // - Event Time Stamp • - Log Source Event Code // Event description 20 Use Cases Sample Use Case
- 21. Advanced SOC Incident Response
- 22. Situational Awareness Ability to identify what is happening in the networks Reconnaissance Weaponization & Delivery Lateral Movement Data Exfiltration Persistency Identification and selection of the target/s host or network by active scanning Transmission/Inject of the malicious payload in to the target/s Detect, exploit and compromise other vulnerable hosts Steal and exhilarate data Establish a foothold in the corporate network In military strategy, a “Kill Chain” is a phase model to describe the stages of an attack, which also helps inform ways to prevent attacks. 22 Incident Response Kill Chain Model for Use Cases Assist in IR
- 23. Know your adversaries and their methods Detect threat activity in kill chain Disrupt the kill chain and stop the attack Eradicate threat agent and remove the threat Our Best Defence against advanced cyber threats has our built in threat intelligence, security operations and incident response working in cordial manner defined by our processes Threat Intelligence Security Operation Incident Response Response StrategyThreat Indicators 23 Incident Response Threat Indicators – Our defence in Cyber Kill Chain
- 24. Topic Descriptions / Actions Purpose The purpose of this document is the provide guidance to Tier2 Triage and Tier 3 Response analysts on the approach to incident remediation. Scope The scope of this guidance includes 3 stages: Containment Eradication Recovery Containment The intention of this stage is to limit the damage caused by the incident without yet removing the cause of the incident. This is typically done as the first step as it may take additional time to understand the cause of the incident and the appropriate eradication strategy. Examples of containment may include shutting down of affected systems, closing firewall ports etc. Eradication This stage is typically done after the containment stage where the cause of the incident is removed. Eradication can only be performed before containment if the incident cause is immediately clear and eradication can be performed swiftly before additional damage is caused by the incident. Examples of eradication include deleting malicious code, removing malicious accounts etc. Recovery This stage is done once the “victim” system impacted is no longer vulnerable. Examples of recovery include restoring from backup, patching servers etc. 24 Incident Response IR response process
- 25. Topic Descriptions / Actions Attack Category Authentication Attack Sub Categories Misc Login Succeeded, General Authentication Failed, User Login Failure, Unknown Authentication, Host Login Succeeded, Host Login Failed, Misc Login Failed, Privilege Escalation Failed, Privilege Escalation Succeeded, Mail Service Login Succeeded, Mail Service Login Failed, Auth Server Login Failed, Auth Server, Group Added, Group Changed, Group Removed, Computer Account Added, Computer Account Changed, Computer Account Removed, Remote Access Login Succeeded, Remote Access Login Failed, General Authentication Successful, Telnet Login Succeeded, Telnet Login Failed, Suspicious Password, Samba Login Succeeded, Samba Login Failed and etc Response Remediation Options 1. Containment a. Terminate processes with any active connections with attacker IP or port b. Disable user id in question 2. Eradication a. Work with network team to physically locate internal attacker b. Physically remove internal attacker c. Turn off switch port of internal attacker d. Remove user access 3. Recovery a. Implement strong password policy b. Reconfigure vulnerable service as applicable c. Restore to previous good state from backup or recovery application 25 Incident Response IR response process
- 26. 1. Extract attack source IP from Helpdesk/IR Ticket 2. Notify application owner of attack 3. Implement firewall rule to block attacker IP 4. If attack source is on local network, remote to a machine within same subnet of unauthorized device 5. Ping offending machine IP 6. Run “arp –a” command on command prompt to extract MAC Address 26 Incident Response IR Steps from Playbook SQL Injection
- 27. Questions? Questions, Comments and Feedback