Sql injection attack
- 1. By RAJ KUMAR RAMPELLI RAJ KUMAR RAMPELLI 10/27/13 1
- 2. SQL stands for Structured Query Language Allows us to access a database SQL can: ◦ ◦ ◦ ◦ ◦ execute queries against a database retrieve data from a database insert new records in a database delete records from a database update records in a database RAJ KUMAR RAMPELLI 10/27/13 2
- 3. A relational database contains one or more tables identified each by a name Tables contain records (rows) with data For example, the following table is called "users" and contains data distributed in rows and columns: UserID Name Last Name Uname Password 1 Rama Krishna shiva 12345 2 Raj Kumar rajkumar 54321 RAJ KUMAR RAMPELLI 10/27/13 3
- 4. With SQL, we can query a database and have a result set returned Using the previous table, a query like this: SELECT LastName FROM users WHERE UserID = 1; Gives a result set like this: LastName -------------Krishna RAJ KUMAR RAMPELLI 10/27/13 4
- 5. Data Manipulation Language ◦ ◦ ◦ ◦ o SELECT - extracts data UPDATE - updates data INSERT INTO - inserts new data DELETE - deletes data Data Definition Language ◦ CREATE TABLE - creates a new database table ◦ ALTER TABLE - alters (changes) a database table ◦ DROP TABLE - deletes a database table RAJ KUMAR RAMPELLI 10/27/13 5
- 6. The ability to inject SQL commands into the database engine through an existing application. Example: Username : Password : SUBMIT ASP/MS SQL Server login syntax var sql = "SELECT * FROM users WHERE uname = '" + formusr + "' AND password = '" + formpwd + "'"; RAJ KUMAR RAMPELLI 10/27/13 6
- 7. Username : Password : shiva 12345 SELECT * FROM USERS WHERE UNAME=‘shiva‘ AND PASSWORD=‘12345’; Result: UserId Name Last Name Uname Password 1 Rama Krishna shiva 12345 RAJ KUMAR RAMPELLI 10/27/13 7
- 8. Username : Password : ‘ OR 1=1; -Any Value Final query would look like this: SELECT * FROM USERS WHERE UNAME=‘ ‘ OR 1=1; --’AND PWD=‘Any Value’; .....Successfully Executed.... Result: UserId Name Last Name Uname Password 1 Rama Krishna 2 Raj Kumar shiva 12345 rajkumar 54321 RAJ KUMAR RAMPELLI 10/27/13 8
- 9. SELECT * FROM clients WHERE account = 12345678 AND pin = 1111 PHP/MySQL login syntax $sql = "SELECT * FROM clients WHERE " . "account = $formacct AND " . "pin = $formpin"; RAJ KUMAR RAMPELLI 10/27/13 9
- 10. $formacct = 1 or 1=1 # $formpin = 1111 Final query would look like this: SELECT * FROM clients WHERE account = 1 or 1=1 # AND pin = 1111 RAJ KUMAR RAMPELLI 10/27/13 10
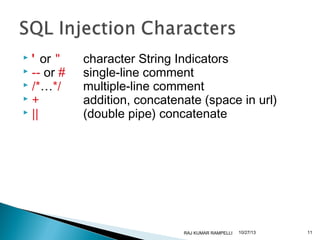
- 11. ' or " -- or # /*…*/ + || character String Indicators single-line comment multiple-line comment addition, concatenate (space in url) (double pipe) concatenate RAJ KUMAR RAMPELLI 10/27/13 11
- 12. Adding NEW Data To Databases… like uname: ‘ UNION UPDATE QUERY;/* pwd : any value */ Modifying The Data… Deleting The Required Data.. like uname: ‘ union delete tablename; /* pwd : any value */ Accessing Users Data… using select…. RAJ KUMAR RAMPELLI 10/27/13 12
- 13. Simple: Input Validation Use provided functions for escaping strings ◦ Many attacks can be thwarted by simply using the SQL string escaping mechanism ‘ ’ and “ ” ◦ mysql_real_escape_string() is the preferred function for this Have length limits on input ◦ Many SQL injection attacks depend on entering long strings RAJ KUMAR RAMPELLI 10/27/13 13
- 14. Some people use PHP addslashes() function to escape characters ◦ single quote (') ◦ double quote (") ◦ backslash () ◦ NUL (the NULL byte) Define data types for each field ◦ Implement stringent "allow only good" filters If the input is supposed to be numeric, use a numeric variable in your script to store it ◦ Implement stringent "known bad" filters For example: reject "select", "insert", "update", "shutdown", "delete", "drop", "--", "'" RAJ KUMAR RAMPELLI 10/27/13 14
- 15. Limit database permissions and segregate users ◦ If you’re only reading the database, connect to database as a user that only has read permissions ◦ Never connect as a database administrator in your web application Configure database error reporting ◦ Default error reporting often gives away information that is valuable for attackers (table name, field name, etc.) ◦ Configure so that this information is never exposed to a user RAJ KUMAR RAMPELLI 10/27/13 15
- 16. SQL Injection is a fascinating and dangerous vulnerability All programming languages and all SQL databases are potentially vulnerable Protecting against it requires ◦ strong design ◦ correct input validation RAJ KUMAR RAMPELLI 10/27/13 16