SQL Injection in PHP
- 1. SQL Injection What it is, how it happens, and how to prevent it.
- 2. What is SQL Injection? According to WIKIPEDIA: SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application . The vulnerability is present when user input is either incorrectly filtered for string literalescape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another. SQL injection attacks are also known as SQL insertion attacks.
- 3. What can it do? Allow logging in as another use, such as the administrator Cause extra DB records to be displayed Allow vandalism of the database Allow destruction of the database Ruin your day... or night... or weekend... The recent theft of 130 million credit card numbers involved SQL Injection.
- 4. How does it work? By passing un-filtered user data into a SQL query, a user can cause un-intended SQL queries to be executed. $SQL = "SELECT * FROM users WHERE name = '{$_GET['name']}'" $_GET['name'] = " a' or 't'='t " ; SELECT * FROM users WHERE name = 'a' OR 't' = 't' ;
- 5. How do you stop SQL Injection? Do not allow direct user input into the database. Parameterized statements Use a library that uses parameters Use a built in functionality that supports Parametization such as MySQLi in PHP5 $db = new mysqli ( "localhost" , "user" , "pass" , "database" ) ; $stmt = $db -> prepare ( "SELECT * FROM Usrs WHERE usrnm=? AND psswrd=?" ) ; $stmt -> bind_param ( "ss" , $user , $pass ) ; $stmt -> execute () ; Escaping Escape the query using a built in or library function $ Password = mysql_real_escape_string ( $Password ) ;
- 6. Why does this work? $ name = mysql_real_escape_string ( $_GET['name'] ) ; $SQL = "SELECT * FROM users WHERE name = '{$name}'" $_GET['name'] = " a' or 't'='t " ; $name = " a\' or \'t\'=\'t " ; SELECT * FROM users WHERE name = 'a\' OR \'t\'=\'t' ;
- 7. Preventing SQL injection in CMSes ALWAYS keep all your modules, themes, components etc. current. The CMS communities stay on top of security issues with their software. ALWAYS keep all your modules, themes, components etc. current. When a compromise is announced, the 'bad people' get just as busy as the 'good people'. ALWAYS keep all your modules, themes, components etc. current.
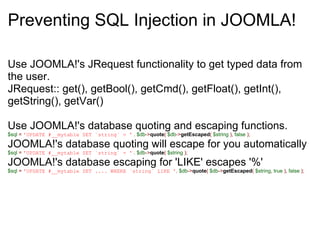
- 8. Preventing SQL Injection in JOOMLA! Use JOOMLA!'s JRequest functionality to get typed data from the user. JRequest:: get(), getBool(), getCmd(), getFloat(), getInt(), getString(), getVar() Use JOOMLA!'s database quoting and escaping functions. $sql = 'UPDATE #__mytable SET `string` = ' . $db -> quote ( $db -> getEscaped ( $string ), false ); JOOMLA!'s database quoting will escape for you automatically $sql = 'UPDATE #__mytable SET `string` = ' . $db -> quote ( $string ); JOOMLA!'s database escaping for 'LIKE' escapes '%' $sql = 'UPDATE #__mytable SET .... WHERE `string` LIKE ' . $db -> quote ( $db -> getEscaped ( $string , true ), false );
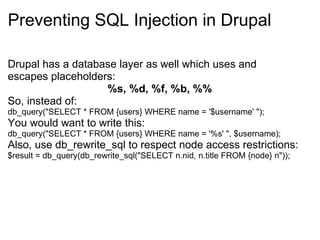
- 9. Preventing SQL Injection in Drupal Drupal has a database layer as well which uses and escapes placeholders: %s, %d, %f, %b, %% So, instead of: db_query("SELECT * FROM {users} WHERE name = '$username' "); You would want to write this: db_query("SELECT * FROM {users} WHERE name = '%s' ", $username); Also, use db_rewrite_sql to respect node access restrictions: $result = db_query(db_rewrite_sql("SELECT n.nid, n.title FROM {node} n"));
- 10. Prevent SQL Injection in Wordpress Wordpress has a database object that supports prepared statements and will escape the values for you. $sql = $wpdb -> prepare ( 'query' [, value_parameter , value_parameter ... ] ); Additionally, the $wpdb object will escape data for you. $wpdb -> insert ( $table, (array) $data ); $wpdb -> update ( $table, (array) $data, (array) $where ); $data should be unescaped. Keys are columns, Values are values. $where should be unescaped. Multiple WHERE conditions are ANDed together.
- 11. Any Questions?
Editor's Notes
- #3: http://en.wikipedia.org/wiki/SQL_injection
- #4: http://en.wikipedia.org/wiki/SQL_injection#Real-world_examples
- #9: http://developer.joomla.org/tutorials/181-preventing-sql-injections.html http://api.joomla.org/Joomla-Framework/Environment/JRequest.html



![How does it work? By passing un-filtered user data into a SQL query, a user can cause un-intended SQL queries to be executed. $SQL = "SELECT * FROM users WHERE name = '{$_GET['name']}'" $_GET['name'] = " a' or 't'='t " ; SELECT * FROM users WHERE name = 'a' OR 't' = 't' ;](https://image.slidesharecdn.com/sqlinjectioninphp-091211080413-phpapp01/85/SQL-Injection-in-PHP-4-320.jpg)

![Why does this work? $ name = mysql_real_escape_string ( $_GET['name'] ) ; $SQL = "SELECT * FROM users WHERE name = '{$name}'" $_GET['name'] = " a' or 't'='t " ; $name = " a\' or \'t\'=\'t " ; SELECT * FROM users WHERE name = 'a\' OR \'t\'=\'t' ;](https://image.slidesharecdn.com/sqlinjectioninphp-091211080413-phpapp01/85/SQL-Injection-in-PHP-6-320.jpg)

![Prevent SQL Injection in Wordpress Wordpress has a database object that supports prepared statements and will escape the values for you. $sql = $wpdb -> prepare ( 'query' [, value_parameter , value_parameter ... ] ); Additionally, the $wpdb object will escape data for you. $wpdb -> insert ( $table, (array) $data ); $wpdb -> update ( $table, (array) $data, (array) $where ); $data should be unescaped. Keys are columns, Values are values. $where should be unescaped. Multiple WHERE conditions are ANDed together.](https://image.slidesharecdn.com/sqlinjectioninphp-091211080413-phpapp01/85/SQL-Injection-in-PHP-10-320.jpg)
