Symmetric key encryption
- 1. Abstracts of Clape Technologies www.clape.io
- 2. Asansol Astha IT Projects (P) Ltd. is an well- established, result-oriented IT Solutions Company. We are highly client-oriented and quality-conscious and our portfolio basket includes a wide range of services and solutions in the area of Data Security & Business Applications. Clape Technologies Ltd (A sister organization of Asansol Astha IT Projects (P) Ltd.) is working upon the patent pending symmetric key encryption standard and the Abstract of the patent application is detailed below. Asansol Astha IT Projects (P) Ltd.
- 3. Abstract of the Patent Application for Symmetric Key Encryption Standard The present invention relates to a system and a method for secured transmission of data. The method comprises the steps of providing the data, generating a password or a key by a user, encrypting the data by the password or the key for plural number of times resulting plurality of cipher texts, sending plurality of the cipher texts and the password or key, and decrypting the cipher text by the password or the key. The system comprises input device means for providing the data, input device means for generating a password by a user, processor means encrypting the data by the password or key for plural number of times resulting plurality of cipher texts, means for sending the plurality of cipher texts and the password and means for decrypting the cipher text by the password or key.
- 4. What the Company does:- •Our Company has conceived a Symmetric Key Encryption Standard and has filed for patenting in Indian Patent Office vide application no.0992/KOL/2011 dated. 26.07.2011 in Kolkata Patent Office Entitled as “A SYSTEM AND A METHOD FOR USE IN A SYMMETRIC KEY CRYPTOGRAPHIC COMMUNICATIONS.” And was published in the Indian Patent Office Journal on 2nd December 2011. Moreover we have applied for patenting in USPTO vide application no 13/557112 date 24.07.2012 and was published in USPTO Journal on 31.12.2012 •The Company has also applied for a Asymmetric Key cryptographic Standard and has filed for patenting in Indian Patent Office (I.P.O Kolkata ) vide application no.446/KOL/2012 dated. 19/04/2012 in Kolkata Patent Office Entitled as “METHOD FOR ESTABLISHING SECURE COMMUNICATION IN A NETWORK AND SYSTEM THEREOF” And was published in the Indian Patent Office(IPO) Journal on 24/08/2012
- 5. Technology Every block cipher involves a transformation of a block of plain text into block of cipher text, where the transformation depends on the cipher key. The mechanism of our encryption procedure seeks to make the statistical relationship between the plain text and the cipher text as complex as possible to prevent attempts to derive the cipher key. The technology a basic building block, which encrypts / decrypts a fixed size block of data, however to use these in practice, we usually need to handle arbitrary amount of data , which may be available in advance, (in which case a block mode is appropriate).
- 6. Technology •Block size: with a view to improve security the block size has been increased but without any compromise to the speed of the procedure. •Key Size: increasing size improves security, makes exhaustive key searching harder but without any compromise with the speed of encryption / decryption function. •Number of rounds: increasing number of rounds in our technology shall improve security but without slowing the Cipher Generation Procedure.
- 7. CLAPE CIPHER DESIGN PRINCIPLES : It encrypts 1024 bit blocks of plain text with the Cipher Key having same size of bits, using appropriate iterations of an elaborate combination of table look up and bits rearrange. Through this procedure the password key is being made into a 1024 bit block size and correspondingly a chunk of plain text of same bit size are being put into our own encryption algorithm to generate a chunk of cipher text. It is commonly believed that the strength of the Password much depends on the method how the encryption algorithm is deployed. In practicality, it has been observed that the user doesn't always want to use password as long as needed for effective key generation. As such responsibility of securing the password of the user rests on the Encryption Technology. There is no need for using salts/pass phrases in this technology for strengthening the password what any common user tends to apply to achieve utmost security.
- 8. The Cryptographic community needs to provide the world with a new encryption standard. The few workhorse algorithms for the last few decades are nearing the end of their useful life cycle. Moreover the recent attacks as evident in the following links provided herein:- www.forbes.com/sites/andygreenberg/ 2013/03/13/cryptographers_show_mathematically_crackable_flaw s_in_common_web_encryption/ www.arstechnica.com/security/2013/02/lucky_thirteen_attacks_sn arfs_cookies_protected_by_SSL_encryption/ www.theregister.co.uk/2011/09/19/beast_exploits_paypal_SSL/ www.isg.rhul.ac.uk/tls/TLS timing.pdf on Padding Oracle attack Recent attacks on existing workhorse algorithms
- 9. In this context if the world is to have a secure reliable and easily available encryption algorithm by the turn of the decade the world needs several candidate symmetric Key encryption algorithms now. These algorithms have to be subjected to years of public scrutiny and cryptanalysis. We are confident that our encryption standard will survive this process and shall eventually become a new standard. Mission:-
- 10. Performance Comparison Study: This comparison has been conducted to measure encryption / decryption speed of Clape with other encryption algorithms like Blow fish, AES, DES, 3DES etc. at different settings for each algorithm such as; different sizes of data blocks, different key sizes, encryption / decryption speed / power Consumption etc.
- 11. THIS STUDY EVALUATES SEVEN DIFFERENT ENCRYPTION ALGORITHMS NAMELY; AES, DES, 3DES, RC6, BLOWFISH, RC2 & CLAPE. THE PERFORMANCE MEASURE OF ENCRYPTION SCHEMES HAS BEEN CONDUCTED IN TERMS OF CHANGING FILE SIZE FOR THE SELECTED CRYPTOGRAPHIC ALGORITHMS.
- 12. Hardware used: i3 processor 2.10 GHz, 3GB RAM and i3 processor, 2.20 GHz, 2GB RAM Energy consumption : It is observed that 600 times of encryption of a 5 MB file utilizes only 20% (approx) of the available Battery power of the laptop. All the tests have been performed on commonly known file formats. Specifications:
- 13. Time Comparison of encryption algorithms Results are based on base 64 encoding
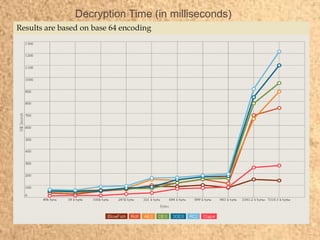
- 14. Decryption Time (in milliseconds) Results are based on base 64 encoding
- 15. Encryption Time (in milliseconds) for Medium Size of file Results are based on base 64 encoding
- 16. Decryption Time (in milliseconds) for Medium Size of file Results are based on base 64 encoding
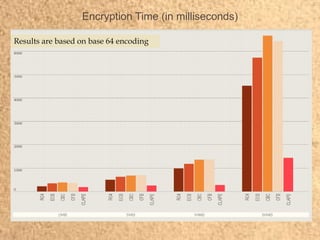
- 17. Encryption Time (in milliseconds) Results are based on base 64 encoding
- 18. Decryption Time (in milliseconds) Results are based on base 64 encoding
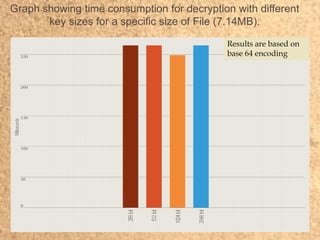
- 19. Graph showing time consumption for encryption with different key sizes for a specific size of File (7.14MB). Results are based on base 64 encoding
- 20. Graph showing time consumption for decryption with different key sizes for a specific size of File (7.14MB). Results are based on base 64 encoding
- 21. Graph showing time consumption for encryption with different key sizes for a specific size of File (694 Kb) Results are based on base 64 encoding
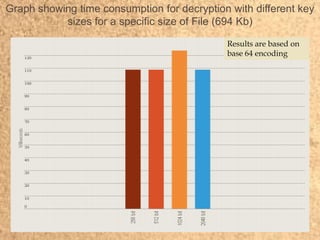
- 22. Graph showing time consumption for decryption with different key sizes for a specific size of File (694 Kb) Results are based on base 64 encoding
- 23. Acknowledgement:- International Journal of Network Security, Vol.10, No.3, PP.213 {219, May 2010} International Business Information Management Association (IBIMA). Looking forward to arranging a presentation to demonstrate the authenticity of our claims through Remote Screen Sharing / visit to our lab /any other conceivable mode of testing. Websites: www.clape.io www.asthaitsolutions.com Contacts: +1 202 642 3323 (USA) +91 341 225 0077 (India) E-mail: [email protected] [email protected]