Testing Android Security Codemotion Amsterdam edition
- 1. Testing Android Security José Manuel Ortega @jmortegac AMSTERDAM 11-12 MAY 2016
- 3. AGENDA ▪ Development Cycle ▪ Static and Dynamic Analysis ▪ Components Security ▪ Hybrid Automatic tools ▪ Best Practices & OWASP
- 5. WHITE BOX /BLACK BOX ✓ ✓ ✓ ✓ ✓ ✓
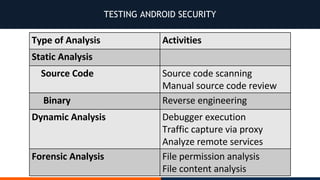
- 7. FORENSICS
- 10. CODE REVIEW / SOURCE CODE ANALYSIS
- 11. ANDROID LINT
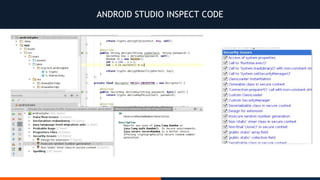
- 12. ANDROID STUDIO INSPECT CODE
- 14. ANDROID SONAR PLUGIN >RULES
- 15. SONAR SECURITY
- 16. ANDROWARN
- 17. QARK ▪ Quick Android Review Kit ▪ https://github.com/linkedin/qark ▪ Static code analysis tool ▪ Look for potential vulnerabilities
- 18. QARK ▪ Identifies permissions and exported components (activities,services..) on Manifest ▪ Looks for WORLD_READABLE and WORLD_WRITABLE files ▪ Looks for X.509 certificates validation issues
- 19. QARK
- 20. QARK REPORT
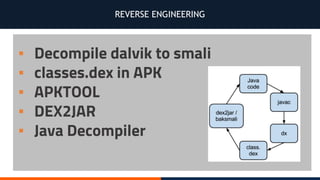
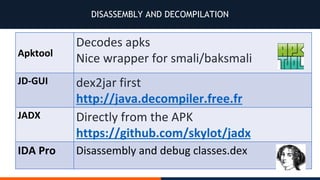
- 21. REVERSE ENGINEERING ▪ Decompile dalvik to smali ▪ classes.dex in APK ▪ APKTOOL ▪ DEX2JAR ▪ Java Decompiler
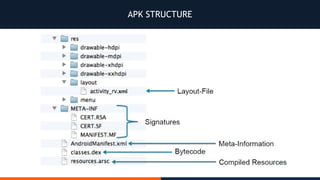
- 22. APK STRUCTURE
- 24. JADX-GUI
- 25. APKTOOL
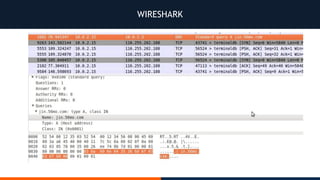
- 27. WIRESHARK
- 28. BURP SUITE ▪ Intercepting network traffic ▪ HTTP proxy tool ▪ Able to intercept layer traffic and allows users to manipulate the HTTP request and response
- 29. DROZER ▪ https://labs.mwrinfosecurity.com/tools/drozer/ ▪ Find vulnerabilities automatically ▪ Automate security testing ▪ Interact with your Apps with debugging disabled
- 30. INSIDE DROZER
- 31. DROZER
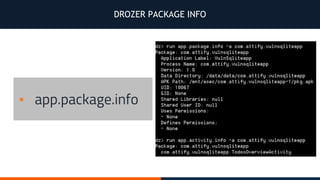
- 32. DROZER PACKAGE INFO ▪ app.package.info
- 33. DROZER COMMANDS
- 35. FINDING SQL INJECTION IN CONTENT PROVIDERS
- 36. EXPLOITING SQL INJECTION VULNERABILITY
- 38. ANDROID MANIFEST EXPORTED ATTRIBUTE … … …
- 39. COMPONENTS SECURITY ▪ AndroidManifest.xml ▪ Activities ▪ Content Providers ▪ Services ▪ Shared Preferences ▪ Webview
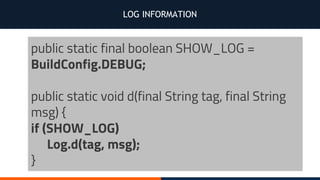
- 40. LOG INFORMATION public static final boolean SHOW_LOG = BuildConfig.DEBUG; public static void d(final String tag, final String msg) { if (SHOW_LOG) Log.d(tag, msg); }
- 42. VULNERABILITIES IN CORDOVA 3.5
- 43. SECURITY IN CONTENT PROVIDERS ▪ Components provide a standardized interface for sharing data between applications ▪ URI addressing scheme ▪ Can perform queries equivalent to SELECT, UPDATE,INSERT, DELETE
- 44. SQLCIPHER ▪ SQLCipher is a SQL extension that provides transparent AES encryption of database files ▪ 256-bit AES Encrypt SQLite database ▪ http://sqlcipher.net/sqlcipher-for-android
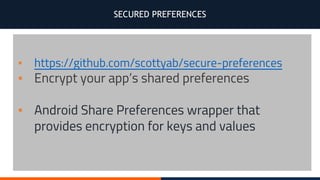
- 45. SECURED PREFERENCES ▪ https://github.com/scottyab/secure-preferences ▪ Encrypt your app’s shared preferences ▪ Android Share Preferences wrapper that provides encryption for keys and values
- 47. DATA STORAGE
- 49. SECURE COMMUNICATIONS ▪ Ensure that all sensitive data is encrypted ▪ Certificate pinning for avoid MITM attacks
- 50. CERTIFICATES SSLSocketFactory.ALLOW_ALLHOSTNAME_VERIFIER TrustManager where checkServerTrusted() always returns true
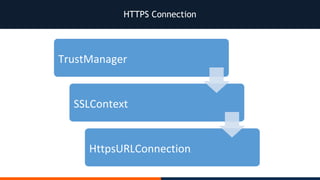
- 53. HTTPS Connection
- 54. HTTPS Connection
- 55. ENCRYPT NETWORK REQUESTS ▪ Best practice is to always encrypt network communications ▪ HTTPS and SSL can protect against MitM attacks and prevent casual sniffing traffic. ▪ Server certificate validity is checked by default
- 56. VALIDATE SERVER CERTIFICATE ▪ https://www.ssllabs.com/ssltest
- 57. CHECK CERTIFICATES TOOLS ▪ OpenSSL ▪ Keytool ▪ Jarsigner
- 58. Runtime Permissions ▪ All permissions granted at install time ▪ Dangerous permissions require user confirmation ▪ Prompt for dangerous permissions at runtime ▪ Granted/revoked by permission group ▪ Managed per app, per user ▪ /data/system/users/0/runtime-permissions.xml
- 59. Group permissions on Android M
- 60. Permissions FLOW on Android M
- 61. Permissions on Android M
- 62. Permissions on Android M
- 63. OBFUSCATION ▪ The obfuscator can use several techniques to protect a Java/Android application: ▪ change names of classes, methods, fields ▪ modify the control flow ▪ code optimization ▪ dynamic code loading ▪ change instructions with metamorphic technique
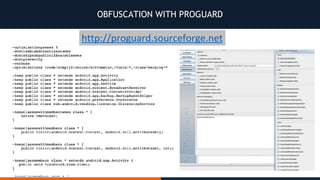
- 64. PROGUARD ▪ File shrinker: detects and removes unused classes, fields, methods,and attributes ▪ Optimizer: optimizes bytecode and removes unused instructions ▪ Obfuscator: renames classes, fields, and methods using short meaningless names
- 67. HYBRID AUTOMATIC ONLINE TOOLS ▪ SandDroid ▪ ApkScan ▪ Visual Threat ▪ TraceDroid ▪ CopperDroid ▪ APK Analyzer ▪ ForeSafe ▪ AndroTotal ▪ NowSecure Lab
- 69. HYBRID AUTOMATIC ONLINE TOOLS ▪ http://sanddroid.xjtu.edu.cn/#home
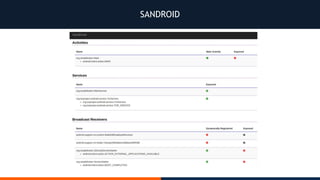
- 70. SANDROID
- 71. SANDROID
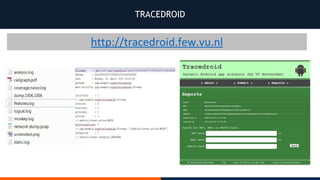
- 72. TRACEDROID
- 73. NOWSECURE LAB
- 74. NOWSECURE LAB
- 75. NOWSECURE LAB
- 76. BEST PRACTICES ▪ Don’t hardcode sensitive information ▪ Don’t store sensitive information ▪ Don’t store at easily readable location like memory card ▪ Encrypt the stored data ▪ Implement SSL
- 77. BEST PRACTICES ▪ Protect the webserver against application layer attacks ▪ Prefer encryption over encoding or obfuscation ▪ Sanitize inputs, use prepared statements (protection against sql injection)
- 78. BEST PRACTICES
- 79. Android Secure Coding Checklist ▪ Use least privilege in request permissions ▪ Don’t unnecessarily export components ▪ Handle intents carefully ▪ Justify any custom permissions ▪ Mutually authenticate services ▪ Use APIs to construct ContentProvider URIs ▪ Use HTTPS ▪ Follow best practices from OWASP project http://owasp. org/index.php/OWASP_Mobile_Security_Project
- 80. OWASP MOBILE TOP 10 RISKS
- 81. OWASP MOBILE TOP 10 RISKS
- 82. Open Android Security Assesment Methodology
- 83. PENTESTING TOOLS / SANTOKU LINUX o o o
- 84. PENTESTING TOOLS / NOWSECURE ▪ https://www.nowsecure.com/resources/freetools/
- 85. REFERENCES ▪ http://proguard.sourceforge.net ▪ http://code.google.com/p/dex2jar ▪ http://code.google.com/p/android-apktool ▪ https://labs.mwrinfosecurity.com/tools/drozer ▪ http://sqlcipher.net/sqlcipher-for-android ▪ https://www.owasp.org/index. php/OWASP_Mobile_Security_Project ▪ https://developer.android. com/training/articles/security-tips.html
- 86. BOOKS
- 87. BOOKS