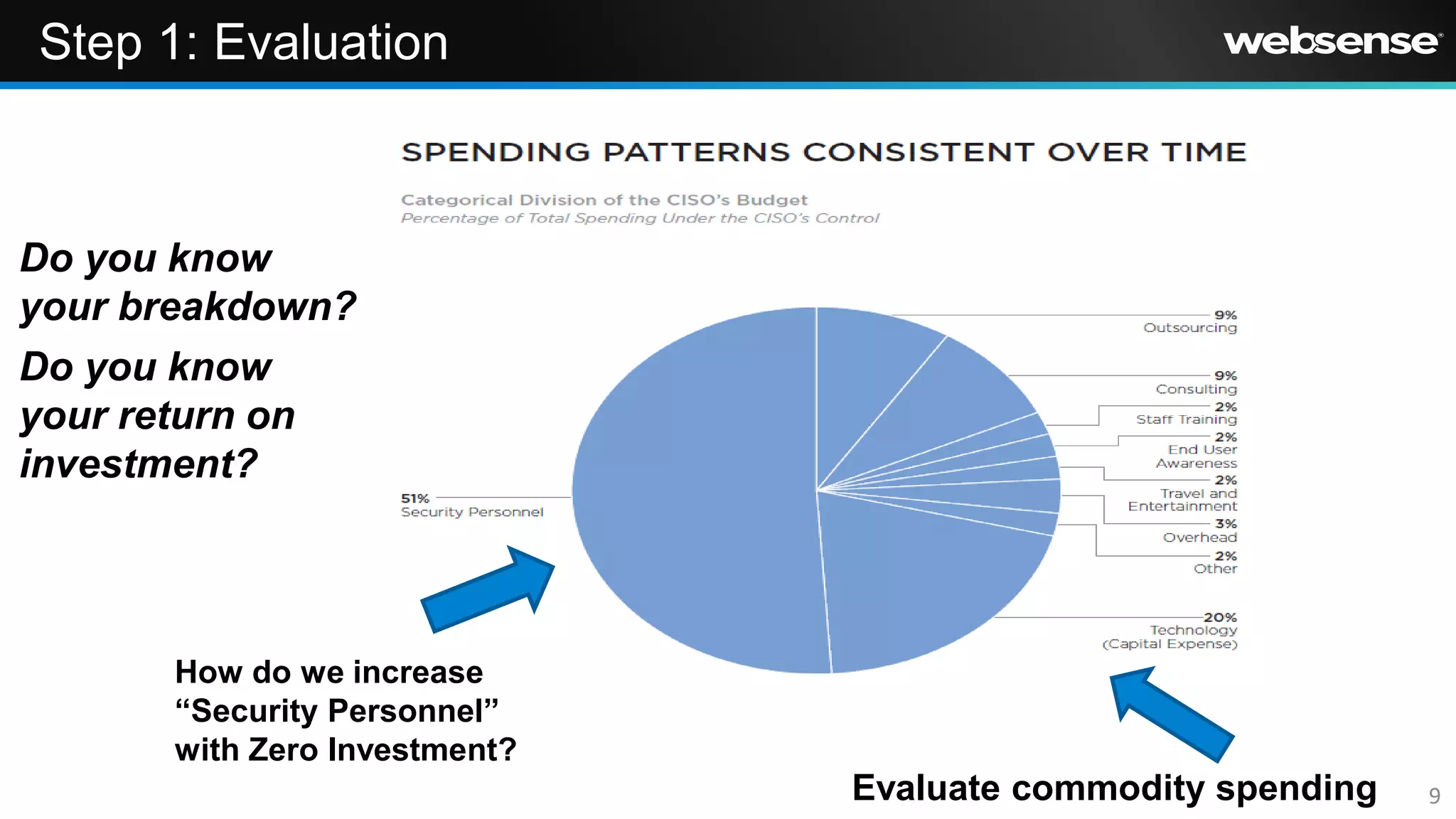
The document discusses the need for a new security strategy that focuses on data protection rather than infrastructure. It recommends evaluating current security spending and redirecting funds to intelligence-led approaches. A next generation security model is proposed that uses context awareness and data-centric policies to identify and contain advanced threats, including insider risks.