Topic5 advanced encryption standard (aes)
- 1. ADVANCED ENCRYPTION STANDARD (AES) Name: Md Fazle Rabbi ID:16CSE057
- 2. CONTENTS What is AES? AES features Operation of AES AES security
- 3. WHAT IS AES? The Advanced Encryption Standard (AES) is a symmetric block cipher chosen by the U.S. government to protect classified information. The more popular and widely adopted symmetric encryption algorithm likely to be encountered nowadays is the Advanced Encryption Standard (AES). It is found at least six time faster than triple DES. AES is implemented in software and hardware throughout the world to encrypt sensitive data. It is essential for government computer security, cyber security and electronic data protection
- 4. AES FEATURES AES algorithm must be a block cipher capable of handling 128-bit blocks, using keys sized at 128, 192 and 256 bits. Other criteria for being chosen as the next AES algorithm included the following: Security. Competing algorithms were to be judged on their ability to resist attack -- as compared to other submitted ciphers. Security strength was to be considered the most important factor in the competition. Cost. Intended to be released on a global, nonexclusive and royalty-free basis, the candidate algorithms were to be evaluated on computational and memory efficiency. Implementation. Factors to be considered included the algorithm's flexibility, suitability for hardware or software implementation, and overall simplicity.
- 5. OPERATION OF AES The number of rounds in AES is variable and depends on the length of the key. AES uses 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256- bit keys. Each of these rounds uses a different 128-bit round key, which is calculated from the original AES key.
- 6. THE SCHEMATIC OF AES STRUCTURE IS GIVEN IN THE FOLLOWING ILLUSTRATION −
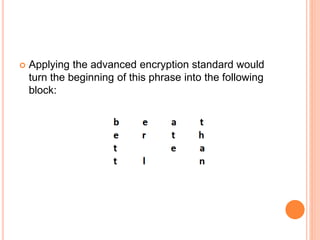
- 7. HOW DOES AES ENCRYPTION WORK? 1. Dividing data into blocks First, we have to keep in mind that AES is a block cipher. Unlike stream ciphers, it encrypts data in blocks of bits instead of bit-by-bit. Each of its blocks contains a column of 16 bytes in a layout of four-by-four. As one byte contains 8 bits, we get 128-bit block size (16×8=128). Thus, the very first step of AES encryption is dividing the plaintext (text that is not written in code) into these blocks. So, let’s choose the text you want to encrypt. For example, it can be “better late than never”.
- 8. Applying the advanced encryption standard would turn the beginning of this phrase into the following block:
- 9. 2.ADDING ROUND KEY This is the very first round of AES encryption. Here, the algorithm adds the initial key to our phrase, which was previously turned into a 4×4 block: + = Adding two blocks of text might seem impossible. However, remember that AES actually uses binary code, and what you now see is just a visual representation of what is actually happening in the binary language.
- 10. ENCRYPTION PROCESS Here, we restrict to description of a typical round of AES encryption. Each round comprise of four sub- processes. The first round process is depicted below −
- 11. I) BYTE SUBSTITUTION The 16 input bytes (128-bit) are substituted based on a predetermined table. The result is a matrix of four rows and four columns where the data is altered in a non-linear way to add confusion
- 12. II) SHIFT ROWS Shift Row is carried out in four parts: First row is not shifted Second row is shifted one (byte) position to the left Third row is shifted two positions to the left Fourth row is shifted three positions to the left In the end, a new matrix is formed based on the same 16 bytes.
- 13. III)) MIX-COLUMNS This operation is the most difficult, both to explain and perform. Each column of the state array is processed separately to produce a new column. The new column replaces the old one. The processing involves a matrix multiplication.
- 14. IV) XOR-ROUND KEY After the Mix-Columns operation, the Xor-Round Key is very simple indeed and hardly needs its own name. This operation simply takes the existing state array, XORs the value of the appropriate round key, and replaces the state array with the result.
- 15. AES SECURITY Security experts maintain that AES is secure when implemented properly. However, AES encryption keys need to be protected. Even the most extensive cryptographic systems can be vulnerable if a hacker gains access to the encryption key. Use of strong passwords, password managers, multifactor authentication (MFA), firewalls and antivirus software is critical to enterprise security. Employees should also be trained in ways to prevent social engineering and phishing attacks.
- 16. THE END