Understanding the "Intelligence" in AI
- 1. Understanding the "Intelligence" in AI RAFFAEL MARTY VP Research and Intelligence Head of X-Labs, Forcepoint AI 4 Cyber | April 2019 | New York City
- 2. A BRIEF SUMMARY We don’t have artificial intelligence (yet) Algorithms can be dangerous - Understand your data and your algorithms Build systems that capture “expert knowledge” and augment human capabilities Escape the cat and mouse game between attackers and security Copyright © 2019 Raffael Marty. | 2
- 3. RAFFAEL MARTY Sophos PixlCloud Loggly Splunk ArcSight IBM Research Security Visualization Big Data ML & AI SIEM Corp Strategy Leadership Zen Copyright © 2019 Raffael Marty | 3
- 4. BEAT WORLD CHAMPION AT GO DESIGN MORE EFFECTIVE DRUGS MAKE SIRI SMARTER ARTIFICIAL INTELLIGENCE Deep Learning Statistics Unsupervised Machine Learning Natural Language Processing
- 5. THE DANGERS OF AI SECURITY EXAMPLES Fooling Facial Recognition Hack Crash Tweet Blacklisting of Windows Executable Pentagon AI Fail Algorithm Bias NOTIFY_SOCKET=/run/syst emd/notify systemd-notify "" Data Biases
- 6. WHAT MAKES ALGORITHMS DANGEROUS? Algorithms make assumptions about the data. Algorithms are too easy to use. Algorithms do not take domain knowledge into account. History is not a predictor of the future. Copyright © 2019 Raffael Marty. | 6
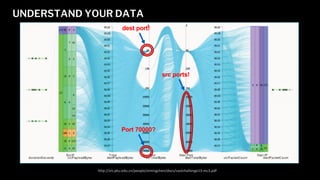
- 7. UNDERSTAND YOUR DATA dest port! Port 70000? src ports! http://vis.pku.edu.cn/people/simingchen/docs/vastchallenge13-mc3.pdf
- 8. CHOOSING THE CORRECT ALGORITHM PARAMETERS The dangers of not understanding algorithmic parameters t-SNE clustering of network traffic from two types of machines perplexity = 3 epsilon = 3 No clear separation perplexity = 3 epsilon = 19 3 clusters instead of 2 perplexity = 93 epsilon = 19 What a mess Copyright © 2019 Raffael Marty. | 8
- 9. INTELLIGENCE Expert KnowledgeSecurity Graph DETECTION COMPONENTS RISK-ADAPTIVE PROTECTION ADDING THE INTELLIGENCE INTO AI CYBER BEHAVIOR CATALOG
- 10. IOCs to Behaviors IOCs / Traditional Threat Intel Behavior ESCAPING THE SECURITY CAT AND MOUSE GAME CnC Bot Bot IOC: Compromised IP addresses • Characterizing machine and human behavior • Leverage risk-based approaches • From reactive to proactive • From detection to protection / automation Behavior: Botnet characteristics Traffic size: 200-350bytes Periodicity: 2 minutes Jitter: 12 seconds IPv4 proto: 6 App protocol: HTTPS
- 11. TAKEAWAYS “Algorithms are getting ‘smarter’, but experts are more important” “Understand your data, your algorithms, and your data science process” “History is not a predictor – but knowledge can be”