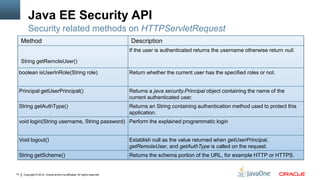
The document provides an overview of Java EE Security, covering key concepts such as authentication, authorization, and security APIs including JSR-196 for authentication and JSR-115 for access control. It details methods for resource protection, authentication mechanisms, and the implementation of security constraints, as well as best practices for data protection and role mapping. Additional guidance is offered on integrating security features within GlassFish and general considerations for secure application development.























![Java Authentication Service Provider Interface
(JSR-196)
2 directly from ServerAuthModule
Class[] getSupportedMessageTypes()
Returns an array of the supported message type class names.
– HttpServletRequest.class
– HttpServletResponse.class
25 Copyright © 2012, Oracle and/or its affiliates. All rights reserved.](https://image.slidesharecdn.com/j12012sfutilizecon3964-121007103710-phpapp02/85/Utilize-the-Full-Power-of-GlassFish-Server-and-Java-EE-Security-25-320.jpg)













