Vulnerable Active Record: A tale of SQL Injection in PHP Framework
- 1. Vulnerable Active Record A tale of SQL Injection in PHP Framework [email protected] fb.com/index.htmli linkedin.com/in/pich4ya Pichaya Morimoto Thailand PHP User Group Meetup January 28, 2015
- 2. ★ What is Active Record ? ★ Secure by Design ? ★ Case Studies ★ Exploitation ★ Input Validation ★ Defence-in-Depth ★ Conclusion Overview
- 3. Active record pattern is an approach to accessing data in a database. A database table or view is wrapped into a class. Thus, an object instance is tied to row(s) in the table. PHP frameworks also bundle their own ORM implementing the active record pattern. For example, Laravel (Eloquent), CakePHP, Symfony (Doctrine), CodeIgniter and Yii. $query = $this->db->select('title, content, date'); $query->from('table1'); $query->where('id', $id); $query->get(); Source: https://en.wikipedia.org/wiki/Active_record_pattern What is Active Record ?
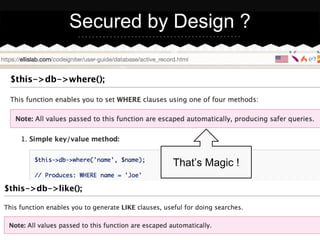
- 4. Secure by Design ? That’s Magic !
- 5. Case Study #1 Get rows from table ‘news’ and order by user input ‘sort’ PHP Framework: CodeIgniter 2.2
- 6. Hacker is here, where is SQLi ? SQLMap == Failed Acunetix == Failed Havij == Failed ‘ or ‘1’=’1 , union all select blah blah blah == Failed
- 7. SQL Injection Pwnage Pwned ! What if error message is turned off, is it still vulnerable? Ads: http://slideshare.net/pichayaa/sql-injection-owaspthailand
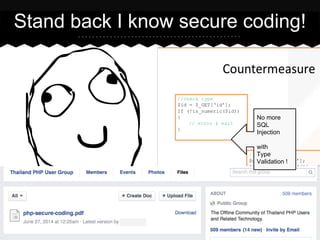
- 8. Stand back I know secure coding! No more SQL Injection with Type Validation !
- 9. Case Study #2 Secure Coding !!
- 10. Keep calm and Think Again Numeric = [Integer, Double, Hex, ...] id value above is hex encoded of “1 and 1>2 union select CHAR(32,58,32),user(),database(),version(),concat_ws (0x3a,username,password) from ci220news_db” + data field is varchar type ***
- 11. A list of security techniques that should be included in every software development project. ★ Parameterize Queries ★ Implement Logging, Error Handling and Intrusion Detection ★ Leverage Security Features of Frameworks and Security Libraries and more.. https://www.owasp.org /index.php/OWASP_Proactive_Controls OWASP Proactive Controls ProTip: PHP is not allowed to parameterize ‘Order By’ clause ;) Because it isn’t data, it is a column name!
- 12. A layered approach to security can be implemented at any level of a complete information security strategy. ★ Secure Coding in software requirement ★ OS Hardening, reduce attack surface ★ Perimeter Security (Network Firewall, IPS/IDS) ★ Centralized Log Server / SIEM ★ Patch / Vulnerability Management System ★ Incident Response Plans ★ Web Application Firewall Source: http://techrepublic.com/blog/it-security/understanding-layered-security-and-defense-in-depth/ Defence-in-Depth







![Keep calm and Think Again
Numeric = [Integer, Double, Hex, ...]
id value above is hex encoded of “1 and 1>2 union select
CHAR(32,58,32),user(),database(),version(),concat_ws
(0x3a,username,password) from ci220news_db” + data
field is varchar type ***](https://image.slidesharecdn.com/s9sk0qosp6pyrvf67ch4-signature-81d70c3f9c3d177b8443900672da69eaa01a3ca613e250eaa1569f38e2adebaa-poli-150128105725-conversion-gate02/85/Vulnerable-Active-Record-A-tale-of-SQL-Injection-in-PHP-Framework-10-320.jpg)


