Web Application Security II - SQL Injection
- 1. Web Application Security Presented by: Md Syed Ahamad Detection and Prevention of SQL Injection 1 Project under: Dr. Ferdous Ahmed
- 2. Project Role Theory Analysis Implementation CS200Detection and Prevention of SQL Injection 2
- 3. Topics Introduction Webgoat and WebScarab Prevention Mechanism and Detection Mechanism Methods Visual Advantage and disadvantage Conclusion CS200Detection and Prevention of SQL Injection 3
- 4. Introduction Thread Agent – Application Specific Attack Vector Exploitability – Easy Security Weakness Prevalence – Common Detectability – Average Technical impacts – severe Business impacts – Business Specific CS200Detection and Prevention of SQL Injection 4
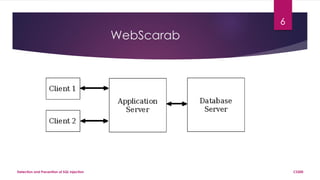
- 5. WebGoat and WebScarab WebGoat – Web based application for demonstration of common Web App. Flaws. Application penetration testing techniques WebScarab – use as proxy in the localhost for WebGoat. Shows Request and Response intercept Parameters can be modified CS200Detection and Prevention of SQL Injection 5
- 6. WebScarab CS200Detection and Prevention of SQL Injection 6
- 7. SQL Injection Serious thread String query = "SELECT * FROM accounts WHERE custID='" + request.getParameter("id") + "'"; Select * from account where username=‘”+a+”’ and PIN=‘”+b+”’; Here, a=998’or’1’=‘1, b may be empty or anything. CS200Detection and Prevention of SQL Injection 7
- 8. Prevention Mechanism Parametrized Query Specific primitive data type CS200Detection and Prevention of SQL Injection 8
- 9. Prevention Mechanism Indirect SQL Query Avoid Direct SQL Query Some tuple similar to the input is taken out and match If match is found go ahead otherwise return false CS200Detection and Prevention of SQL Injection 9
- 10. Detection Mechanism Methods Regular Expression – /w*((%27)|('))((%6F)|o|(%4F))((%72)|r|(%52))/ix @"(;|s)(exec|execute|select|insert|update|delete|create|alter|drop|rename|truncate |backup|restore)s" Parametrized Visual Advantage and disadvantage CS200Detection and Prevention of SQL Injection 10
- 11. Detection Mechanism CS200Detection and Prevention of SQL Injection 11
- 12. Conclusion Its not solving the all injection flaws. Hierarchical structure of Scanner is required. Hashing of user’s input credentials. CS200Detection and Prevention of SQL Injection 12