Web cryptography javascript
- 1. José Manuel Ortega Candel Web Cryptography with JavaScript The talk would aim to introduce the cryptography from the developer point of view, showing ways to encrypt information with JavaScript in both client and server side for web applications. The talking points could be: Introduction to security in web applications (authentication, authorization, confidentiality, integrity) Browser storage Information encryption and decryption with JavaScript Web Cryptography API and browsers support Libraries let you use encryption algorithms like SHA,AES,RSA(CryptoJS, SJCL) Cipher information in server side with NodeJS Tools and plugins for browsers that allow checking the main algorithms used to encrypt information JavaScript Obfuscation Practical application that uses any of encryption libraries discussed Keywords: Security, Encryption, Libraries, Tools ,Obfuscation, JavaScript
- 2. Introduction to security in web applications (authentication, authorization, confidentiality, integrity) Cryptography The discipline that embodies principles, means, and methods for providing information security, including confidentiality, data integrity, nonrepudiation, and authenticity. Browser storage The actual state is the lack of cryptographic functions that are supported in all browsers. The actual tendency is to use the browser localStorage and a possible attacker could use this information to extract the contents to be keeping With HTTPS the communication is encrypted, but suffered one MITM attack and with the right tools like sniffers it can get to see the data. Further, there are techniques like SSLStrip that allows to convert HTTPS traffic to HTTP through a MITM attack. For these reasons, it would be advisable to add another security layer with a crypto library in JavaScript.
- 3. Comparing local storage clear text with local storage encrypted In clear text version we can see key and value in clear in browser console In encrypted version we can see that notes value are not in clear text. More over, we have other keys like iv and salt variables.
- 4. Information encryption and decryption with JavaScript Introduce to algorithms MD5, SHA-1,SHA-256,SHA-512 (hash functions).Allow check files integrity and document signing AES [Private key cryptography][Used in WPA2] RSA-4096 [Public key cryptography] RC4[Used in SSL] AES The AES algorithm is a symmetric block cipher that can encrypt (encipher) and decrypt (decipher) information. The main features AES algorithm are: Shared secret key algorithm Symmetrical Same key to encrypt and decrypt 128 192 256 bit key sizes Any message encrypted with a public key can be decrypted with a private key and vice versa, but an encrypted message cannot be decrypted by the same key that encrypted it as in symmetric key encryption. In asymmetric key cryptography, each party has two keys, a public key and a private keys The public key is shared to the world, and the private key is kept private The keys are generated in such a way that any message encrypted by the public key in the pair can only be decrypted by the private key, and viceversa It can be identified the following elements: message = the unencrypted, readable data we care about. cipherText = the message after encryption, the data the adversary gets to see. Key = the secret required to encrypt and decrypt the message Encryption: ciphertext = f(key, message) Decryption: cleartext = f(key, cipherText)
- 5. AES algorithm JavaScript implementation Initialization Vector (IV) A vector used in defining the starting point of an encryption process within a cryptographic algorithm.
- 6. RSA The main features RSA algorithm are: Algorithm public / private key Asymmetric It is encrypted with the public key and decrypted with the key private Asymmetric key cryptography works in a similar manner to symmetric key cryptography except that the keys are generated in a special manner that allows them to decrypt only messages encrypted by the other key in the pair While there are many ways to do this, the most common algorithm is known as the RSA keygen algorithm Public key: (n, e); To encrypt: C ≡ Me (mod n) Private key (n, d); To decrypt: M ≡ Ce (mod n) Pub-Key Encryption (PKE) Encrypt message(M) using public-key(pk) Decrypt Cipher text(C) using secret-key(sk) E(pk, M) → C D(sk, C) → M
- 7. RSA algorithm JavaScript implementation
- 8. Web Cryptography API and browsers support This specification describes an API for cryptographic operations like: Hash functions Public and private key algorithms Signature generation and data verification Encryption and decryption In browser support, only Chrome, FireFox and Opera offer total support for Web Crypo API. In this table we can see browser support for different algorithms that offers web crypto API
- 9. Methods and algorithms supported by Web Crypto API
- 10. WebCrypto API RSA Public/Private Key
- 13. Libraries let you use encryption algorithms like SHA,AES,RSA(CryptoJS, SJCL) Stanford Javascript Crypto Library(SJCL) It supports AES,SHA-256,HMAC,PBKDF2 algorithms
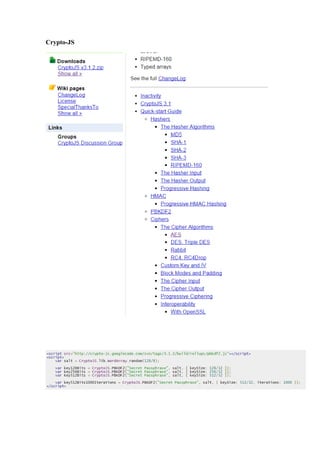
- 14. Crypto-JS
- 15. Cipher information in server side with NodeJS require('crypto') OPENSSL is required install in server o Methods of crypto object Testing crypto object
- 16. Tools Mymail-Crypt for Gmail Plugin for Chrome that allow generate our private key for encrypt messages
- 19. DuckDugGo Cryptography hacks Identifying Hash Algorithm and Finding Plain text from Hashes
- 20. NoScript plugin for Firefox that allows protection for Cross Site Scripting(XSS)
- 21. JavaScript obfuscation Benefits of obfuscating JavaScript o Protect source code o Prevent code theft and reuse o Protect intellectual property o Add an extra security layer Online tools for code obfuscation o https://jscrambler.com/es o http://www.minifyjs.com/javascript-obfuscator o http://www.javascriptobfuscator.com/Javascript-Obfuscator.aspx
- 22. Practical application that uses any of encryption libraries discussed Analysis of security telegram web application AES, SHA-1 implementation https://code.google.com/p/crypto-js RSA implementation http://www-cs-students.stanford.edu/~tjw/jsbn
- 23. We can see the implementation of aesEncrypt and aesDecrypt methods. These methods are using the CryptoJS library
- 24. The main problem with this protocol encryption is the use of SHA-1 algorithm for generating the message key, since SHA-1 is an algorithm cryptographically broken. The security of this protocol is that the key is generated from the contents of the user message.




![Information encryption and decryption with JavaScript
Introduce to algorithms
MD5, SHA-1,SHA-256,SHA-512 (hash functions).Allow check files integrity and
document signing
AES [Private key cryptography][Used in WPA2]
RSA-4096 [Public key cryptography]
RC4[Used in SSL]
AES
The AES algorithm is a symmetric block cipher that can encrypt (encipher) and decrypt
(decipher) information.
The main features AES algorithm are:
Shared secret key algorithm
Symmetrical
Same key to encrypt and decrypt
128 192 256 bit key sizes
Any message encrypted with a public key can be decrypted with a private key and vice versa,
but an encrypted message cannot be decrypted by the same key that encrypted it as in symmetric
key encryption.
In asymmetric key cryptography, each party has two keys, a public key and a private keys
The public key is shared to the world, and the private key is kept private
The keys are generated in such a way that any message encrypted by the public key in the pair
can only be decrypted by the private key, and viceversa
It can be identified the following elements:
message = the unencrypted, readable data we care about.
cipherText = the message after encryption, the data the adversary gets to see.
Key = the secret required to encrypt and decrypt the message
Encryption: ciphertext = f(key, message)
Decryption: cleartext = f(key, cipherText)](https://image.slidesharecdn.com/webcryptographyjavascript-170603105919/85/Web-cryptography-javascript-4-320.jpg)