Web Socket ASM support lior rotkovitch
- 1. BIG-IP v12.1 Application Security Manager WebSocket Created by , NPIE ASM [email protected] V1.0 March, 2016 @rotkovitch
- 2. © F5 Networks, Inc 2 • Intro to WebSocket • ASM and WebSocket • WebSocket violations • WebSocket URL setting • WebSocket in the request log • WebSocket Learning and policy building • Demo flow Index
- 3. © F5 Networks, Inc 3 Intro to WebSocket http://demo.kaazing.com/forex/ http://www.websocket.org/echo.html
- 4. © F5 Networks, Inc 4 • WebSocket provide simple framing layer on top of HTTP • Key Benefits : • Two-way communication • Connections that are persistent • Full-duplex. • Low HTTP and TCP overhead • WebSocket protocol is RFC 6455 WebSocket intro
- 5. © F5 Networks, Inc 5 WebSocket intro – Handshake and frames exchange CLIENT SERVER GET /chat HTTP/1.1 Host: server.example.com Upgrade: Websocket Connection: Upgrade Sec-WebSocket-Key: dGhlIHNhbXBsZSBub25jZQ== Origin: http://example.com Sec-WebSocket-Protocol: chat, superchat Sec-WebSocket-Version: 13 HTTP/1.1 101 Switching Protocols Upgrade: Websocket Connection: Upgrade Sec-WebSocket-Accept: s3pPLMBiTxaQ9kYGzzhZRbK+xOo= Sec-WebSocket-Protocol: chat Websocket frame Websocket frame Websocket frame Websocket close frame Websocket close frame
- 6. © F5 Networks, Inc 6 WebSocket Demo 1 2 WS filter http://www.websocket.org/echo.html
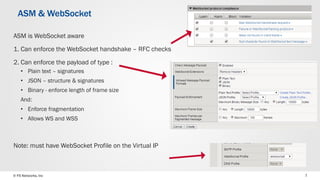
- 7. © F5 Networks, Inc 7 ASM is WebSocket aware 1. Can enforce the WebSocket handshake – RFC checks 2. Can enforce the payload of type : • Plain text – signatures • JSON – structure & signatures • Binary - enforce length of frame size And: • Enforce fragmentation • Allows WS and WSS Note: must have WebSocket Profile on the Virtual IP ASM & WebSocket
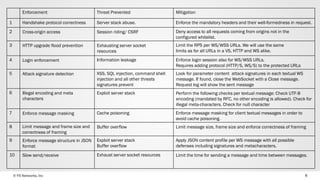
- 8. © F5 Networks, Inc 8 Enforcement Threat Prevented Mitigation 1 Handshake protocol correctness Server stack abuse. Enforce the mandatory headers and their well-formedness in request. 2 Cross-origin access Session riding/ CSRF Deny access to all requests coming from origins not in the configured whitelist. 3 HTTP upgrade flood prevention Exhausting server socket resources Limit the RPS per WS/WSS URLs. We will use the same limits as for all URLs in a VS, HTTP and WS alike. 4 Login enforcement Information leakage Enforce login session also for WS/WSS URLs. Requires adding protocol (HTTP/S, WS/S) to the protected URLs 5 Attack signature detection XSS, SQL injection, command shell injection and all other threats signatures prevent Look for parameter content attack signatures in each textual WS message. If found, close the WebSocket with a Close message. Request log will show the sent message 6 Illegal encoding and meta characters Exploit server stack Perform the following checks per textual message: Check UTF-8 encoding (mandated by RFC, no other encoding is allowed). Check for illegal meta-characters. Check for null character 7 Enforce message masking Cache poisoning Enforce message masking for client textual messages in order to avoid cache poisoning. 8 Limit message and frame size and correctness of framing Buffer overflow Limit message size, frame size and enforce correctness of framing 9 Enforce message structure in JSON format Exploit server stack Buffer overflow Apply JSON content profile per WS message with all possible defenses including signatures and metacharacters. 10 Slow send/receive Exhaust server socket resources Limit the time for sending a message and time between messages.
- 9. © F5 Networks, Inc 9 WebSocket violations – Protocol compliance
- 10. © F5 Networks, Inc 10 WebSocket violations – Protocol compliance Security ›› Application Security ›› Policy Building ›› Learning and Blocking Settings
- 11. © F5 Networks, Inc 11 WebSocket violations – Protocol compliance • Bad WebSocket handshake request • Failure in WebSocket framing protocol • Mask not found in client frame • Null character found in WebSocket text massage
- 12. © F5 Networks, Inc 12 WebSocket violations – Protocol compliance • Bad WebSocket handshake request • HTTP Version is 1.1 • “Upgrade” header appears once • "Sec-WebSocket-Key“ has one occurrence and is base 64 encoded • "Sec-WebSocket-Version“ has once occurrence and value of 13 • Evasion technique
- 13. © F5 Networks, Inc 13 WebSocket violations – Protocol compliance • Failure in WebSocket framing protocol • Continuing frame without start frame. • Start frame without ending the previous message fragmentation (interleaving fragmentation is not allowed!) • Control frame with FIN flag off (i.e. attempt to fragment them). • Control frame payload size is greater than 125.
- 14. © F5 Networks, Inc 14 WebSocket violations – Protocol compliance • Mask not found in client frame • Each frame should have a bit mask according to the RFC. • Enforce the continuity of the frames by verifying the bit mask exists • Client side • Null character found in WebSocket text massage • Null character inside message payload of type JSON and Text will be enforce. • Indifferent to “check message payload”
- 15. © F5 Networks, Inc 15 WebSocket URL Entities Security ›› Application Security ›› Policy Building ›› Learning and Blocking Settings Policy Type Learn New WebSocket URL’s Fundamental Never Enhance Selective Comprehensive Add all entities
- 16. © F5 Networks, Inc 16 1. Binary content found in text only WebSocket 2. Illegal WebSocket binary message length 3. Illegal WebSocket extension 4. Illegal WebSocket frame length 5. Illegal number of frame per message 6. Text content found in binary only WebSocket WebSocket Violations - Payload
- 17. © F5 Networks, Inc 17 • Binary content found in text only WebSocket • The WebScoket payload is defined as text but the payload contains binary payload. WebSocket Violations - Payload
- 18. © F5 Networks, Inc 18 • Illegal WebSocket binary message length • Binary message size enforce of 10000 bytes (default) WebSocket Violations - Payload
- 19. © F5 Networks, Inc 19 • Illegal WebSocket extension • Protocol extensions: Per-message compression, Interleaved message fragmentation, etc • ASM can do the following for WebScoket extension : o Remove headers – remove the extension header (default) o Ignore – ignore the extension header (let then pass) o Block – block request with WebSocket extension WebSocket Violations - Payload
- 20. © F5 Networks, Inc 20 • Illegal WebSocket frame length WebSocket Violations - Payload
- 21. © F5 Networks, Inc 21 • Illegal number of frames per message WebSocket Violations - Payload
- 22. © F5 Networks, Inc 22 • Text content found in binary only WebSocket WebSocket Violations - Payload
- 23. © F5 Networks, Inc 23 WebSocket URL configuration
- 24. © F5 Networks, Inc 24 WebSocket URL configuration
- 25. © F5 Networks, Inc 25 WebSocket URL configuration
- 26. © F5 Networks, Inc 26 Reviewing WebSocket message in the request log
- 27. © F5 Networks, Inc 27 Reviewing WebSocket message in the request log Security ›› Event Logs ›› Application ›› Requests 1 2 3
- 28. © F5 Networks, Inc 28 WebSocket - Request log filtering Security ›› Event Logs ›› Application ›› Requests
- 29. © F5 Networks, Inc 29 WebSocket - Request log filtering
- 30. © F5 Networks, Inc 30 WebSocket Handshake
- 31. © F5 Networks, Inc 31 WebSocket Handshake
- 32. © F5 Networks, Inc 32 WebSocket - Ping Pong
- 33. © F5 Networks, Inc 33 WebSocket - Close
- 34. © F5 Networks, Inc 34 WebSocket Demo
- 35. © F5 Networks, Inc 35 Leaning page for WebSocket
- 36. © F5 Networks, Inc 36 WebSocket URL
- 37. © F5 Networks, Inc 37 Leaning page for WebSocket
- 38. © F5 Networks, Inc 38 “Sec-WebSocket-Extensions” WebSocket URL
- 39. © F5 Networks, Inc 39 WebSocket URL
- 40. © F5 Networks, Inc 40 Policy builder classification
- 41. © F5 Networks, Inc 41 JSON facts
- 42. © F5 Networks, Inc 42 Attack signatures on Web Socket
- 43. © F5 Networks, Inc 43 Web Sokcet Learning and attack signature
- 44. © F5 Networks, Inc 44 Override attack signature – false positive
- 45. © F5 Networks, Inc 45 • ASM support WebSocket protocol • Enforce protocol compliance • Enforce payload – • Plane Text – attack signature , null • JSON – structure and attack signature • Binary – length • New violations and setting for Web Scoket • Policy builder can learn the URL and classify the WebSocket payload types. • Request log display the communication between client and server Summary