Webinar: Compliance and Data Protection in the Big Data Age: MongoDB Security Architecture
- 1. Compliance & Data Protection in the Big Data Age - MongoDB Security Architecture Mat Keep MongoDB Product Management & Marketing [email protected] @matkeep
- 2. 2 Agenda • Data Security Landscape and Challenges • Best Practices and MongoDB Implementation • Resources to Get Started
- 3. 3 Security Breaches: More Users, More Cost http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
- 4. 4 …and it’s getting worse • $5.4m average cost of a data breach • 10% annual growth in financial impact of cybercrime • 96% of thefts come from database records Source: Symantec
- 5. 5 Security: #2 Spending Increase
- 6. 6 Security: Largest Skills Deficit
- 7. 7 • Data growth: 1.8 trillion gigabytes in 2011 to 7.9 trillion gigabytes by 2015 (IDC) • Technologies Growth: DB-Engines now tracks over 210 data stores • Market Growth: Big data market forecast to reach $50bn by 2017 (Wikibon) More Data, New Data
- 8. 8 • Analytics derived from “big data” becoming as valuable as traditional enterprise data • Big data technologies must evolve to meet compliance standards of industry & government New Reality
- 9. 9 • Multiple standards – PCI-DSS, HIPAA, NIST, STIG, EU Data Protection Directive, APEC data protection standardization • Common requirements – Data access controls – Data protection controls – Data permission – Data audit Regulatory Compliance
- 11. Best Practices & Enforcement in MongoDB
- 12. 12 • Confirming identity for everything accessing the database • Create unique credentials for each entity • Clients, admins/devs, software systems, other cluster nodes • Integrated with the corporate authentication standards Authentication Application Reporting ETL [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected]
- 13. 13 • Integrate with choice of corporate authentication mechanisms • Kerberos protocol, with support for Active Directory • PKI integration with x.509 Certificates, for clients and inter- cluster nodes • IdM integration with LDAP support • Red Hat Identity Management Authentication in MongoDB
- 14. 14 • Defines what an entity can do in the database • Control which actions an entity can perform • Grant access only to the specific data needed Authorization User Identity Resource Commands Responses Authorization
- 15. 15 Authorization in MongoDB • User-defined roles assign fine-grained privileges, applied per collection, delegate across teams
- 16. 16 MongoDB Field Level Redaction User 1 - Confidentia l - Secret { _id: ‘xyz’, field1: { level: [ ‚Confidential‛ ], data: 123 }, field2: { level: [ ‚Top Secret‛ ], data: 456 }, field3: { level: [ ‚Unclassified‛ ], data: 789 } } User 2 - Top Secret - Secret - Confidentia l User 3 - Unclassified FieldLevelAccessControl • Enables a single document to to store data with multiple security levels
- 17. 17 Field Level Redaction User 1 - Confidentia l - Secret { _id: ‘xyz’, field1: { level: [ ‚Confidential‛ ], data: 123 }, field2: { level: [ ‚Top Secret‛ ], data: 456 }, field3: { level: [ ‚Unclassified‛ ], data: 789 } } User 2 - Top Secret - Secret - Confidentia l User 3 - Unclassified FieldLevelAccessControl
- 18. 18 Field Level Redaction User 1 - Confidentia l - Secret { _id: ‘xyz’, field1: { level: [ ‚Confidential‛ ], data: 123 }, field2: { level: [ ‚Top Secret‛ ], data: 456 }, field3: { level: [ ‚Unclassified‛ ], data: 789 } } User 2 - Top Secret - Secret - Confidentia l User 3 - Unclassified FieldLevelAccessControl
- 19. 19 Field Level Redaction User 1 - Confidentia l - Secret { _id: ‘xyz’, field1: { level: [ ‚Confidential‛ ], data: 123 }, field2: { level: [ ‚Top Secret‛ ], data: 456 }, field3: { level: [ ‚Unclassified‛ ], data: 789 } } User 2 - Top Secret - Secret - Confidentia l User 3 - Unclassified FieldLevelAccessControl
- 20. 20 Field Level Redaction: Implementation
- 21. 21 • Capture actions in the database • Access • Data • Database configuration • Used for compliance and forensics Auditing Audit Trail Collection Database
- 22. 22 Auditing in MongoDB • Capture • Schema operations & database configuration changes • Authentication & authorization activities • Configurable filters • Write log to multiple destinations in JSON or BSON • Partner solutions for capture of read / write activity • IBM Guardium
- 23. 23 • Encoding of data in transit & at rest – Connections to database, and between nodes – Data stored on disk…protected against attacks targeting OS or physical storage – Mechanisms to sign & rotate keys – FIPS-compliant cryptography Encryption
- 24. 24 Encryption in MongoDB • SSL on all connections & utilities – FIPS 140-2 mode – Mix with non-SSL on the same port • On-disk encryption via partner solutions – Gazzang – LUKS – IBM Guardium – Bitlocker & TrueCrypt
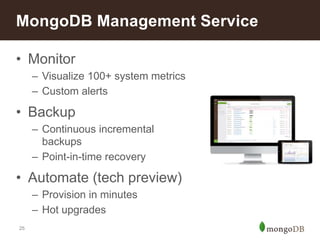
- 25. 25 • Monitor – Visualize 100+ system metrics – Custom alerts • Backup – Continuous incremental backups – Point-in-time recovery • Automate (tech preview) – Provision in minutes – Hot upgrades MongoDB Management Service
- 26. 26 • Network filters: Router ACLs and Firewall • Bind IP Addresses: limits network interfaces • Run in VPN • Dedicated OS user account: don’t run as root • File system permissions: protect data, configuration & keyfiles Environmental Control
- 27. Putting it all Together
- 28. 28 Business Needs Security Features Authentication In Database LDAP* Kerberos* x.509 Certificates Authorization Built-in Roles User-Defined Roles Field Level Redaction Auditing Admin Operations* Queries (via Partner Solutions) Encryption Network: SSL (with FIPS 140-2) Disk: Partner Solutions MongoDB Enterprise-Grade Security *Requires a MongoDB Subscription
- 29. 29 Subscriptions Basic Standard Enterprise Mgt. Tools Cloud On-Prem & Cloud On-Prem & Cloud Advanced Security SSL On-Demand Training SLA 4 hours 1 Hour 30 Minutes Support 9am – 9pm M – F 24x7x365 24x7x365 License AGPL Commercial Commercial
- 30. 30 Try it Out • MongoDB Security Architecture Whitepaper & Security Checklist • Extensive tutorials in the documentation • Download MongoDB Enterprise
- 31. 31 For More Information Resource Location MongoDB Downloads mongodb.com/download Free Online Training education.mongodb.com Webinars and Events mongodb.com/events White Papers mongodb.com/white-papers Case Studies mongodb.com/customers Presentations mongodb.com/presentations Documentation docs.mongodb.org Additional Info [email protected] Resource Location
- 33. 33 7,000,000+ MongoDB Downloads 150,000+ Online Education Registrants 30,000+ MongoDB Management Service (MMS) Users 25,000+ MongoDB User Group Members 20,000+ MongoDB Days Attendees Global Community
- 34. 34 MongoDB Use Cases Big Data Product & Asset Catalogs Security & Fraud Internet of Things Database-as-a- Service Mobile Apps Customer Data Management Data Hub Social & Collaboration Content Management Intelligence Agencies Top Investment and Retail Banks Top US Retailer Top Global Shipping Company Top Industrial Equipment Manufacturer Top Media Company Top Investment and Retail Banks
- 35. 35 MongoDB Products and Services MongoDB University Certification and Training for Developers and Administrators – Online & In-Person MongoDB Management Service (MMS) Cloud-Based Service for Monitoring, Alerts, Backup and Restore Subscriptions Development & Production – On-Prem Monitoring, Advanced Security, Professional Support and Commercial License Consulting Expert Resources for All Phases of MongoDB Implementations
- 36. 36 MongoDB Company Overview 350+ employees 1,000+ customers 13 offices around the world Over $231 million in funding
- 37. 37 • 27 of the Top 100 Organizations • 10 of the Top Financial Services Institutions • 10 of the Top Electronics Companies • 10 of the Top Media and Entertainment Companies • 10 of the Top Retailers • 10 of the Top Telcos • 8 of the Top Technology Companies • 6 of the Top Healthcare Companies Fortune 500 & Global 500
- 38. 38 Costs – Measured in Billions
Editor's Notes
- #2: SurveyRapid adoption – agility, scale, performance. 1 area of immaturity vs RDBMS securityApache Cassandra. Apache AccumuloAdding security features over past couple of releases – Mongo 2.6 takes that to next level – cover those in this session
- #4: Visualisation of some of the latest security breaches – measured by number of usersMost recent high profile breach at Target – within 1st quarter, contributed to 46% drop in net profits and $60m of cost – will increaseMassive american – breach at Heartland Payment Systems, affected 160m users, estimated cost upwards of $7bn
- #5: Cost of data breaches caused by attacks increasing – cost per record approaching $300Avg breach in US costing $5.5mGrowth in cost of cybercrime96% of all breaches come from the database. Might seem obvious, but DBs generally only store about 20% of an organisations data
- #6: Based on research published this year by Ent Strategy Group – IT spending increase 2nd only to cloud
- #7: Based on same research largest skills deficit currently exists – 25% believe they have shortage in skillsNote, closley followed by analytics skills, oft quoted data scientist. But smaller than security
- #8: Why are risks and costs escalatingData growth – more than just GB – value of data increasing – more of our personal info on line, more corp IP and business is run online Market for managing the data is growingTo deal with that growth, more database technologies, which add complexity
- #9: Data collected from social media, mobile devices and sensor networks has become as sensitive as traditional transaction data generated from backoffice systems. For this reason, big data technologies must evolve to meet the regulatory compliance standards demanded by industry and government.
- #10: No talk on security is ever complete without reference to stds and compliance, multiple, across industries and regions – evolve rapidlyNo piece of tech can ever be declared as being compliant on its own, ie MongoDB is PCI or Hipaa compliant, because compliance is based on people, process and the productCommon set of criteraRestrict access to dataProtect against disclosure/lossAppropriate permissions – separation of dutiesCreate audit trails for governance and forensives
- #11: Requirements define security architecture of any databaseNeeds Authentication, authroization, encryption and auditing – talk more about each of those in a momentThese mechanisms need to apply to everything that interacts with the database – from clients, admins, to underlying storage and platformAuthentication: ensuring only registered users and entities can access the dataAuthorization: controlling who can do what to each piece of dataAuditing: recording what actions are taken against the dataEncryption: scrambling data in motion over the network and at rest on diskEnforced across clients, admin/developers and covering database, storage and network
- #23: Schema operations:(create/drop database, index, etc,Config changes: creation of replica sets, shardsAuth: records creation of new users, successful and failed authentication events and attempts to run actions not authorised to commitFilter which actions you want to logThe audit log can be written to multiple destinations in a variety of formats includ- ing to the console and syslog (in JSON format), and to a file (JSON or BSON), which can then be loaded to MongoDB and analyzed to find relevant events.Capture of r/w, use partner solutions, ieGuardium
- #25: Tooling includes mongodump, restore, topLinux Unified Key Setup
- #26: Beyond security controls in DB itself, need to consider how we implement security in the broader environment – monitoring is key part . For exam- ple, sudden peaks in the CPU and memory loads and high operations counters in the database can indicate a Denial of Service attack. Detect and respond in real time, reduces impact of any security breachMMS application that allows montoring, backup and automationMonitoring – visualise 100+ system metrics, create custom alertsBackup – essential part of security policy should intruder corrupt data
- #27: Also important to consider broader environmental control around the databaseThe bind_ip setting for mon- god instances limits the network in- terfaces on which MongoDB processes will listen for incoming connections.Recommend Running in VPNs. Limit MongoDB programs to non- public local networks and virtual private networks.Should configure a Dedicated OS User Account. Which is used to run MongoDB executables. MongoDB should not run as the “root” user.Configure appropriate File System Permissions. The servers running Mon- goDB should use filesystem permissions that prevent users from accessing the data files created by MongoDB. MongoDB configuration files and the cluster keyfile should be protected to prevent ac- cess by unauthorized users.
- #29: Put it all together
- #30: MongoDB available in multiple subscription levelsAdvanced – ldap and auditing
- #31: Download Security Architecture whitepaper
- #35: Customer Data Management (e.g., Customer Relationship Management, Biometrics, User Profile Management)Product and Asset Catalogs (e.g., eCommerce, Inventory Management)Social and Collaboration Apps: (e.g., Social Networks and Feeds, Document and Project Collaboration Tools)Mobile Apps (e.g., for Smartphones and Tablets) Content Management (e.g, Web CMS, Document Management, Digital Asset and Metadata Management)Internet of Things / Machine to Machine (e.g., mHealth, Connected Home, Smart Meters)Security and Fraud Apps (e.g., Fraud Detection, Cyberthreat Analysis)DbaaS (Cloud Database-as-a-Service)Data Hub (Aggregating Data from Multiple Sources for Operational or Analytical Purposes)Big Data (e.g., Genomics, Clickstream Analysis, Customer Sentiment Analysis)
- #38: Customers (not just users)
- #39: Heartland payment systems – credit card processing for 250k business nearly $8bnSony 2011, playstation $4.6bn
















![16
MongoDB Field Level Redaction
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ ‚Confidential‛ ],
data: 123
},
field2: {
level: [ ‚Top Secret‛ ],
data: 456
},
field3: {
level: [ ‚Unclassified‛ ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl
• Enables a single document to to store data with
multiple security levels](https://image.slidesharecdn.com/mongodb2-140501104815-phpapp01/85/Webinar-Compliance-and-Data-Protection-in-the-Big-Data-Age-MongoDB-Security-Architecture-16-320.jpg)
![17
Field Level Redaction
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ ‚Confidential‛ ],
data: 123
},
field2: {
level: [ ‚Top Secret‛ ],
data: 456
},
field3: {
level: [ ‚Unclassified‛ ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl](https://image.slidesharecdn.com/mongodb2-140501104815-phpapp01/85/Webinar-Compliance-and-Data-Protection-in-the-Big-Data-Age-MongoDB-Security-Architecture-17-320.jpg)
![18
Field Level Redaction
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ ‚Confidential‛ ],
data: 123
},
field2: {
level: [ ‚Top Secret‛ ],
data: 456
},
field3: {
level: [ ‚Unclassified‛ ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl](https://image.slidesharecdn.com/mongodb2-140501104815-phpapp01/85/Webinar-Compliance-and-Data-Protection-in-the-Big-Data-Age-MongoDB-Security-Architecture-18-320.jpg)
![19
Field Level Redaction
User 1
- Confidentia
l
- Secret
{ _id: ‘xyz’,
field1: {
level: [ ‚Confidential‛ ],
data: 123
},
field2: {
level: [ ‚Top Secret‛ ],
data: 456
},
field3: {
level: [ ‚Unclassified‛ ],
data: 789
}
}
User 2
- Top Secret
- Secret
- Confidentia
l
User 3
- Unclassified
FieldLevelAccessControl](https://image.slidesharecdn.com/mongodb2-140501104815-phpapp01/85/Webinar-Compliance-and-Data-Protection-in-the-Big-Data-Age-MongoDB-Security-Architecture-19-320.jpg)