What is tokenization in blockchain?
- 1. 1 What is tokenization in Blockchain? Ulf Mattsson Chief Security Strategist www.Protegrity.com
- 2. 2 Cloud Security Alliance (CSA)Tokenization Management and Security Cloud Management and Security Payment Card Industry (PCI) Security Standards Council (SSC): 1. Tokenization Task Force 2. Encryption Task Force, Point to Point Encryption Task Force 3. Risk Assessment SIG 4. eCommerce SIG 5. Cloud SIG, Virtualization SIG 6. Pre-Authorization SIG, Scoping SIG Working Group • Chief Security Strategist at Protegrity, previously Head of Innovation at TokenEx and Chief Technology Officer at Atlantic BT, Compliance Engineering, and IT Architect at IBM Ulf Mattsson • Products and Services: • Data Encryption, Tokenization, Data Discovery, Cloud Application Security Brokers (CASB), Web Application Firewalls (WAF), Robotics, and Applications • Security Operation Center (SOC), Managed Security Services (MSSP) • Inventor of more than 70 issued US Patents and developed Industry Standards with ANSI X9, CSA and PCI DSS Dec 2019 May 2020 May 2020
- 3. 3 Agenda 1. Blockchain • What is Blockchain? • Use cases, trends and risks • Vendors and platforms • Data protection techniques and scalability 1. Tokenization • Digital business • Convert a digital value into a digital token • Local and central models 1. Cloud • Tokenization in Hybrid cloud
- 5. 5Source: Gartner Blockchain Transactions How Does Blockchain Work?
- 6. 6Source: Gartner Blockchain has five elements 1. Distribution: Blockchain participants are located physically apart from each other and are connected on a network 2. Encryption: Blockchain uses technologies such as public and private keys to record the data in the blocks securely and semi- anonymously 3. Immutability: Completed transactions are cryptographically signed, time-stamped and sequentially added to the ledger 4. Tokenization: Transactions and other interactions in a blockchain involve the secure exchange of value 5. Decentralization: Both network information and the rules for how the network operates are maintained by nodes on the distributed network due to a consensus mechanism
- 8. 8 Spectrum of Blockchains Source: Gartner
- 9. 9Source: Gartner Blockchain Provides an Alternative Trust Model
- 10. 10 ComputerworldExample of startups implementing distributed ledger technology software, 2019
- 13. 13 Computerworld Examples of Enterprises focused distributed ledger technology
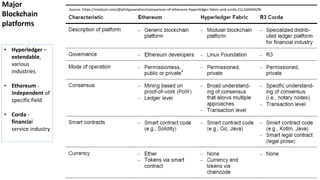
- 14. 14 Enterprise Blockchain platforms Amazon Hyperledger Fabric Ant Financial Ant Blockchain Technology, Hyperledger Anthem Hyperledger Fabric Aon R3 Corda Baidu Hyperledger Fabric— Bitfury Bitcoin, Exonum BMW Hyperledger Fabric, Ethereum, Quorum, Broadridge Hyperledger Fabric, Quorum, Corda, DAM Cargill Hyperledger Sawtooth, Hyperledger Grid China Construction Bank Hyperchain, Hyperledger Fabric Citigroup Axcore, Symbiont Assembly, Quorum Coinbase Bitcoin, ethereum, XRP and 24 others Credit Suisse Corda, Paxos Daimler Hyperledger, Corda, Ethereum De Beers Ethereum Depository Trust & Clearing Corporation (DTCC) Axcore Dole Foods IBM Blockchain, Hyperledger Fabric— Facebook Hotstuff Figure Hyperledger Fabric Foxconn Ethereum General Electric Microsoft Azure, Corda, Quorum, Hyperl Google Chainlink, Bitcoin, Ethereum, Bitcoin Cas Honeywell Hyperledger Fabric HSBC Ethereum, Corda, Hyperledger Fabric Enterprise B IBM ING Group Intercontinental Exchange JPMorgan LVMH Mastercard Microsoft Nasdaq National Settlement Depository Nestlé Optum Overstock Ripple Royal Dutch Shell Samsung Santander Signature Bank Silvergate Bank Square Tencent T-Mobile UBS United Nations Vanguard VMware Walmart Examples Using Blockchain 50 Enterprises: 5 Logistics: Forbes Computerworld
- 15. 15 Major Blockchain platforms used by Enterprises Forbes m Assembly DAML Axcore Stell ar Burr ow Sovri n Trust SQL MS IBM Waves XR P NX T Nextl edger Ravencoi n Flori n XRP Chain link Dash Doge coin Hotstuf f Tezo s Hyperc hain Zcas h Ant Litec oin Other 3 3 2 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 1 45 Platform Hyperledger Ethereum Corda Bitcoin Quorum Assembly DAML Axcore Stell ar Burr ow Sovri n Trust SQL MS IBM Waves XR P Enterprise customers 27 24 9 9 6 3 3 2 1 1 1 1 1 1 1 1 Platform Hyperledger Ethereum Corda Bitcoin Enterprise customers 27 24 9 9 a 1 1 b 1 1 c d e 1 f 1 g 1 1 h 1 1 1 i 1 1 j 1 1 k 1 l 1 1 m n 1 1 1 o 1 p 1 q 1 r 1 s 1 t 1 u 1 1 1 v 1 1 1
- 16. 16 Major Blockchain platforms • Hyperledger – extendable, various industries • Ethereum - independent of specific field • Corda - financial service industry Source: https://medium.com/@philippsandner/comparison-of-ethereum-hyperledger-fabric-and-corda-21c1bb9442f6
- 18. 18 Blockchain Use Cases 1. Asset Tracking. These use cases cover the tracking of physical assets through the supply chain to identify location and ownership accurately. 2. Claims. This category covers automated claims processing in areas such as auto mobile, agriculture, travel, and life and health insurance. 3. Identity Management/Know Your Client (KYC). This category covers uses where records must be securely tied to an individual. 4. Internal Record Keeping. In these use cases, the data to be secured remains within an individual organization. 5. Loyalty and Reward. This category includes use cases for tracking loyalty points 6. Payment/Settlement. Use cases in this category involve a payment between parties, or settlement of a trade. 7. Provenance. Similar to the asset-tracking use case, this covers recording the movement of assets, but the aim is to show the full history and ownership of the asset, rather than its location. 8. Shared Record Keeping. This category includes use cases where data needs to be shared securely between multiple participants. 9. Smart Cities/the IoT. This group includes use cases that use blockchain to provide data tracking and to control functions for smart spaces or IoT solutions. 10. Trade Finance. These use cases aim to streamline the process of financing trades, including managing letters of credit, simplifying trade finance and facilitating cross-border trade. 11. Trading. Use cases in this group aim to improve the process for buying and selling assets, including dealing in derivatives, trading of private equity and sports trading. Gartner
- 19. 19Gartner and springer.com A secure and extensible blockchain-based data provenance framework
- 20. 20Gartner Blockchain has the potential to reshape industries Enabling trust, providing transparency and enabling value exchange across business ecosystems — potentially lowering costs, reducing transaction settlement times and improving cash flow. • Assets can be traced to their origin, significantly reducing the opportunities for substitutions with counterfeit goods. • Asset tracking also has value in other areas, such as tracing food across a supply chain to more easily identify the origin of contamination or tracking individual parts to assist in product recalls. • Another area in which blockchain has potential is identity management. • Smart contracts can be programmed into the blockchain where events can trigger actions; • Example, payment is released when goods are received.
- 25. 25Gartner Gartner highlights seven enterprise blockchain project mistakes, 2020 1. Misusing or misunderstanding blockchain technology Gartner states that the vast majority of projects focus on recording data. Many fail to use major capabilities such as decentralized consensus, smart contracts and tokenization. 2. Assuming technology is more mature than it is Some corporates believe blockchain technology is ready for production use, even though many platforms are still immature for large-scale production. Gartner expects this will change within the next few years. 3. Confusing a protocol with a business solution A protocol is the underlying technology such as Hyperledger Fabric of R3’s Corda and is invariably applicable to several industries. Applications need to be developed on top of these. Much like a website or web application leverages the internet. 4. Viewing blockchain as a database Databases are capable of creating, reading, updating and deleting data. Not so with blockchains. Because of its immutable nature, blockchains are not designed to update and delete data. 5. Assuming that interoperability standards exist Although some platforms talk about interoperability, Gartner finds it challenging to envision interoperability when all the protocols are evolving quickly. 6. Assuming smart contract technology is a solved problem Smart contracts don’t just execute code on a single system. Instead, they are run by all nodes on a blockchain. 7. Ignoring governance issues In private or permissioned blockchain governance is usually by the owner or contractual. While challenging, the problem is far bigger for public blockchains. Governance in public blockchains such as Ethereum and Bitcoin is mostly aimed at technical issues.
- 27. 27 If there is a Picasso’s painting valued at $50 million, it can be tokenized. • The same applies to gold and diamonds. Company stocks are more complicated because in most jurisdictions it is prohibited to sell fractional parts of company shares. Bankex — “Bankex provides the universal solution which can transform different asset classes to a digital system/field/economy/area providing it with liquidity, flexibility, and safety for asset owners and investors like never before” Maecenas — “Maecenas is a new online marketplace promises to give art lovers the chance to buy shares in famous paintings.[The Telegraph]” LaToken — “LATOKEN’s mission is to make capital markets and trading available 24/7 T+0, with a broader range of asset classes. We aim to facilitate capital reallocation into promising businesses, which will foster job creation with higher productivity.” Transform different asset classes
- 28. 28 Tokenization in real estate • Suppose there is a $200,000 apartment • Tokenization can transform this apartment into 200,000 tokens • Thus, each token represents a 0.0005% share of the underlying asset • Finally, we issue the token on some sort of a platform supporting smart contracts • For example on Ethereum, • The tokens can be freely bought and sold on different exchanges • Imagine you want to invest in real estate, but your initial investment is modest — say $5,000. • Perhaps you want to start small and increase your investment gradually. You are not becoming a legal owner of the property. However, because Blockchain is a public ledger that is immutable, it ensures that once you buy tokens, nobody can “erase” your ownership even if it is not registered in a government-run registry.
- 29. 29 What happens if a company that handles tokenization sells the property? • Token owners just own tokens. • They have no legal rights on the property and thus are not protected by the law. • Therefore, legal changes are needed to accommodate these new business models. A problem is that this system brings us back some sort of centralization. • The whole idea of Blockchain and especially smart contracts is to create a trustless environment. • While this is possible to achieve when tokenizing digital assets, with real world, physical assets, this is not the case. • Therefore, we have to accept a certain dose of centralization. Legislation and centralization
- 31. 31 Blockchain Business Value, Worldwide Gartner
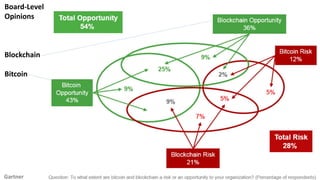
- 32. 32 Blockchain Plans Q: What are your organization’s plans in terms of blockchain? 2019 Gartner CIO Survey: • 60% of CIOs expect some kind of blockchain deployment in the next three years. • Deployed blockchain or plan to deploy it in the next 12 months, 1. financial services (18%) 2. services (17%) 3. transportation (16%)
- 33. 33Gartner 4 Types of Blockchain Business Initiatives
- 34. 34 Blockchain enabling technologies: 2009-2020 This early phase of blockchain-enabled experiments is built on top of existing systems to reduce cost and friction in private, proprietary activities. They have only limited distribution capabilities to a small number of nodes either within or between enterprises. Blockchain-inspired solutions: 2016-2023 The current phase of blockchain-inspired solutions is usually designed to address a specific operational issue – most often in terms of inter-organisational process or record keeping inefficiency. Blockchain complete solutions: 2020s Blockchain complete offerings, starting in the 2020s, will have all five elements, delivering on the full value proposition of blockchain including decentralization and tokenization. Blockchain enhanced solutions: Post- 2025 Blockchain enhanced solutions offer all five elements and combine them with complementary technologies such as AI or IoT. Blockchain technologies Gartner
- 36. 36 Centralized vs. Decentralized Identity YOU ACCOUNT ORG STANDARDS: #2 Third-Party IDP (Federated) Identity YOU ACCOUNT ORGIDP #3 Self-Sovereign Identity (SSI) YOU CONNECTION PEER DISTRIBUTED LEDGER (BLOCKCHAIN) #1 Siloed (Centralized) Identity
- 37. 37 https://royalsociety.org Secure Multi-Party Computing (MPC) Using MPC, different parties send encrypted messages to each other, and obtain the model F(A,B,C) they wanted to compute without revealing their own private input, and without the need for a trusted central authority. Secure Multi-Party machine learningCentral trusted authority A B C F(A, B,C) F(A, B,C) F(A, B,C) Protected data fields U B A C F(A, B,C) U U U
- 40. 40 40Source: IBM Blockchains can be private or public Is Blockchain impossible to hack?
- 41. 41 41Source: IBM Blockchain offers validation, encryption and potentially tokenization
- 42. 42 Scalability
- 43. 43 • By 2023, blockchain will be scalable technically, and will support trusted private transactions with the necessary data confidentiality. • Over time, permissioned blockchains will integrate with public blockchains. • Blockchain adds little value unless it is part of a network that exchanges information and value. • The network collaboration challenges have initially driven organizations to turn to consortia to derive the most immediate value from blockchain. • Four types of consortia exist: • technology-centric; geographically centric; industry centric and process-centric. Source: Gartner Blockchain Will Be Scalable by 2023 Blockchain remains immature for enterprise deployments due to a range of technical issues including poor scalability and interoperability. Scalability Roadmap
- 44. 44 Shared responsibili ties across cloud service models Data Protection for Multi- cloud Payment Application Payment Network Payment Data Policy, tokenization, encryption and keys Gateway Call Center Application PI* Data Tokenization Salesforce Analytics Application Differential Privacy (DP), K-anonymity model PI* Data Microsoft Election Guard development kit Election Data Homomorphic Encryption (HE) Data Warehouse PI* Data Vault-less tokenization (VLT) Use-cases of some data privacy techniques Voting Application *: PI Data (Personal information) means information that identifies, relates to, describes, is capable of being associated with, or could reasonably be linked, directly or indirectly, with a consumer or household according to CCPA Dev/test Systems Masking PI* Data
- 46. 46 Differential Privacy (DP) 2-way Format Preserving Encryption (FPE) Homomorphic Encryption (HE) K-anonymity modelTokenization MaskingHashing 1-way Analytics and Machine Learning (ML) Algorithmic Random Noise added Computing on encrypted data Format Preserving Fast Slow Very slow Fast Fast Format Preserving Encryption and Privacy Models
- 47. 47 Field Privacy Action (PA) PA Config Variant Twin Output Gender Pseudonymise AD-lks75HF9aLKSa Pseudonymization Generalization Field Privacy Action (PA) PA Config Variant Twin Output Age Integer Range Bin Step 10 + Pseud. Age_KXYC Age Integer Range Bin Custom Steps 18-25 Aggregation/Binning Field Privacy Action (PA) PA Config Variant Twin Output Balance Nearest Unit Value Thousand 94000 Rounding Generalization Source data: Output data: Last name Balance Age Gender Folds 93791 23 m … … … … Generalization Source data: Output data: Patient Age Gender Region Disease 173965429 57 Female Hamburg Gastric ulcer Patient Age Gender Region Disease 173965429 >50 Female Germany Gastric ulcer Generalization Examples of data de-identification Source: INTERNATIONAL STANDARD ISO/IEC 20889, Privitar, Anonos
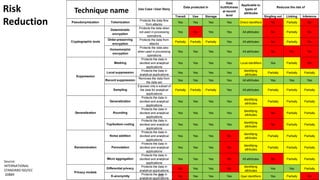
- 48. 48 Risk Reduction Source: INTERNATIONAL STANDARD ISO/IEC 20889 Transit Use Storage Singling out Linking Inference Pseudonymization Tokenization Protects the data flow from attacks Yes Yes Yes Yes Direct identifiers No Partially No Deterministic encryption Protects the data when not used in processing operations Yes No Yes Yes All attributes No Partially No Order-preserving encryption Protects the data from attacks Partially Partially Partially Yes All attributes No Partially No Homomorphic encryption Protects the data also when used in processing operations Yes Yes Yes Yes All attributes No No No Masking Protects the data in dev/test and analytical applications Yes Yes Yes Yes Local identifiers Yes Partially No Local suppression Protects the data in analytical applications Yes Yes Yes Yes Identifying attributes Partially Partially Partially Record suppression Removes the data from the data set Yes Yes Yes Yes All attributes Yes Yes Yes Sampling Exposes only a subset of the data for analytical applications Partially Partially Partially Yes All attributes Partially Partially Partially Generalization Protects the data in dev/test and analytical applications Yes Yes Yes Yes Identifying attributes Partially Partially Partially Rounding Protects the data in dev/test and analytical applications Yes Yes Yes Yes Identifying attributes No Partially Partially Top/bottom coding Protects the data in dev/test and analytical applications Yes Yes Yes Yes Identifying attributes No Partially Partially Noise addition Protects the data in dev/test and analytical applications Yes Yes Yes No Identifying attributes Partially Partially Partially Permutation Protects the data in dev/test and analytical applications Yes Yes Yes No Identifying attributes Partially Partially Partially Micro aggregation Protects the data in dev/test and analytical applications Yes Yes Yes No All attributes No Partially Partially Differential privacy Protects the data in analytical applications No Yes Yes No Identifying attributes Yes Yes Partially K-anonymity Protects the data in analytical applications No Yes Yes Yes Quai identifiers Yes Partially No Privacy models Applicable to types of attributes Reduces the risk of Cryptographic tools Suppression Generalization Technique name Data truthfulness at record level Use Case / User Story Data protected in Randomization Technique name
- 49. 49 Reduction of Pain with Different Protection Techniques 1970 2000 2005 2010 High Low Pain & TCO Strong Encryption Output: AES, 3DES Format Preserving Encryption DTP, FPE Vault-based Tokenization Vaultless Tokenization Input Value: 3872 3789 1620 3675 !@#$%a^.,mhu7///&*B()_+!@ 8278 2789 2990 2789 8278 2789 2990 2789 Format Preserving Greatly reduced Key Management No Vault 8278 2789 2990 2789 Year
- 50. 50 10 000 000 - 1 000 000 - 100 000 - 10 000 - 1 000 - 100 - Transactions per second* I Format Preserving Encryption Tokenization Speed I Vaultless Data Tokenization I AES CBC Encryption Standard I Vault-based Data Tokenization *: Speed will depend on the configuration
- 51. 51 Different Tokenization Approaches Property Dynamic Pre-generated Vault-based Vaultless
- 52. 52 Minimization Devaluation/Pseudonymisation Data Hashing/Masking Encryption DataUtility Data Protection Max Utility Min Utility Min Protection Max Protection Source:TokenEx Data Security Approaches
- 53. 53 Type of Data Use Case I Structured How Should I Secure Different Types of Data? I Un-structured Simple – Complex – PCI PHI PII Encryption of Files Card Holder Data Tokenization of Fields Protected Health Information Personally Identifiable Information
- 54. 54 Personally Identifiable Information (PII) in compliance with the EU Cross Border Data Protection Laws, specifically • Datenschutzgesetz 2000 (DSG 2000) in Austria, and • Bundesdatenschutzgesetz in Germany. This required access to Austrian and German customer data to be restricted to only requesters in each respective country. • Achieved targeted compliance with EU Cross Border Data Security laws • Implemented country-specific data access restrictions Data sources Case Study A major international bank performed a consolidation of all European operational data sources to Italy
- 55. 55 Examples of Protected Data Field Real Data Tokenized / Pseudonymized Name Joe Smith csu wusoj Address 100 Main Street, Pleasantville, CA 476 srta coetse, cysieondusbak, CA Date of Birth 12/25/1966 01/02/1966 Telephone 760-278-3389 760-389-2289 E-Mail Address [email protected] [email protected] SSN 076-39-2778 076-28-3390 CC Number 3678 2289 3907 3378 3846 2290 3371 3378 Business URL www.surferdude.com www.sheyinctao.com Fingerprint Encrypted Photo Encrypted X-Ray Encrypted Healthcare / Financial Services Dr. visits, prescriptions, hospital stays and discharges, clinical, billing, etc. Financial Services Consumer Products and activities Protection methods can be equally applied to the actual data, but not needed with de- identification
- 56. 56 Access to DataLow High High - Low - I I Lower Risk and Higher Productivity with More Access to More Data User Productivity Risk More Access to Data Low Risk Tokens High Risk Clear Data
- 58. 58 Data protection techniques: Deployment on-premises, and clouds Data Warehouse Centralized Distributed On- premises Public Cloud Private Cloud Vault-based tokenization y y Vault-less tokenization y y y y y y Format preserving encryption y y y y y Homomorphic encryption y y Masking y y y y y y Hashing y y y y y y Server model y y y y y y Local model y y y y y y L-diversity y y y y y y T-closeness y y y y y y Privacy enhancing data de-identification terminology and classification of techniques De- identification techniques Tokenization Cryptographic tools Suppression techniques Formal privacy measurement models Differential Privacy K-anonymity model
- 59. 59
- 60. 60Source: Gartner Source: Netskope Current use or plan to use: Spending by Deployment Model, Digital Commerce Platforms, Worldwide
- 61. 61 A Data Security Gateway can protect sensitive data in Cloud and On-premise • Policy Enforcement Protected data U • Encryption Key On-premise
- 62. 62 Protection throughout the lifecycle of data in Hadoop Tokenizes or encrypts sensitive data fields Enterprise Policies Privacy policies may be managed on-prem or Cloud Platform • Policy Enforcement Point (PEP) Protected data fields U Separation of Duties • Encryption Key Management Big Data Analytics Data Producers Data Users Google Cloud UU Big Data Protection with Granular Field Level Protection for Google Cloud
- 63. 63 Protect data before landing Enterprise Policies Apps using de-identified data Sensitive data streams Enterprise on- prem Data lifted to S3 is protected before use S3 • Applications can use de- identified data or data in the clear based on policies • Protection of data in AWS S3 before landing in a S3 bucket Protection of data in AWS S3 with Separation of Duties • Policy Enforcement Point (PEP) Separation of Duties • Encryption Key Management
- 64. 64 Legal Compliance and Nation-State Attacks • Many companies have information that is attractive to governments and intelligence services. • Others worry that litigation may result in a subpoena for all their data. Securosis, 2019 Multi-Cloud Data Privacy considerations Jurisdiction • Cloud service providers redundancy is great for resilience, but regulatory concerns arises when moving data across regions which may have different laws and jurisdictions. SecuPi
- 65. 65Securosis, 2019 Consistency • Most firms are quite familiar with their on-premises encryption and key management systems, so they often prefer to leverage the same tool and skills across multiple clouds. • Firms often adopt a “best of breed” cloud approach. Examples of Hybrid Cloud considerations Trust • Some customers simply do not trust their vendors. Vendor Lock-in and Migration • A common concern is vendor lock-in, and an inability to migrate to another cloud service provider. Cloud Gateway Google Cloud AWS Cloud Azure Cloud S3 Salesforce
- 66. 66 THANK YOU! Ulf Mattsson Chief Security Strategist www.Protegrity.com
Editor's Notes
- #3: The 2014 Verizon Data Breach Investigations Report concluded that enterprises are losing ground in the fight against persistent cyber-attacks. We simply cannot catch the bad guys until it is too late. This picture is not improving. Verizon concluded that less than 14% of breaches are detected by internal security tools. Detection by third party entities increased from approximately 10% to 25% during the last three years. Specifically theft of payment card information 99% of the cases that someone else told the victim they had suffered a breach. One reason is that our current approach with monitoring and intrusion detection products can't tell you what normal looks like in your own systems and SIEM technology is simply too slowly to be useful for security analytics. Big Data security analytics may help over time, but we don't have time to wait. Biggest hacks and security breaches of 2014 include eBay, Target, Sony and Microsoft, Celebrity iCloud, NSA, Heartbleed, Sony The successful attack on JP Morgan Chase surprised me most as the largest US bank lost personal information of 76 million households and it took several months to detect.
- #41: A framework for GDPR readiness GDPR compliance is complex, because the regulation itself is complex. It outlines obligations for data holders that can affect all parts of a business, from data collection to customer communication practices. However, GDPR is also open-ended: it doesn’t tell you in detail how to meet those obligations, or that any given technological approach will suffice. That’s why IBM has developed a straightforward approach to help simplify the ways you think about conformance. The IBM GDPR framework offers an actionable five-phase approach to GDPR readiness, which recognizes that readiness is a continuum: every organization will have a unique place on the journey to readiness. In Phase 1, you assess your situation. You figure out which of the data you collect and store is covered by GDPR regulations, and then you plot a course to discover it. Phase 2 is where you design your approach. You need to come up with a solid plan for data collection, use and storage. And you need to develop an architecture and strategy that will balance risks and business objectives. Your goal in Phase 3 is to transform your practices, understanding that the data you deem valuable to your organization is equally valuable to the people it represents. This is where you need to develop a sustainable privacy compliance program, implement security and governance controls (TOMs — Technical and Organizational Measures) and potentially appoint a Data Protection Officer. By the time you get to Phase 4, you’re ready to operate your program. Now you’re continually inspecting your data, monitoring personal data access, testing your security, using privacy and security by design principles and purging unneeded data. And Phase 5 — the final phase — is where you’re ready to conform with the necessary GDPR requirements. Now you’re fulfilling data subject requests for access, correction, erasure and transfer. You’re also prepared for audits with documentation of your activities and ready to inform regulators and data subjects in the event of a data breach.
- #42: A framework for GDPR readiness GDPR compliance is complex, because the regulation itself is complex. It outlines obligations for data holders that can affect all parts of a business, from data collection to customer communication practices. However, GDPR is also open-ended: it doesn’t tell you in detail how to meet those obligations, or that any given technological approach will suffice. That’s why IBM has developed a straightforward approach to help simplify the ways you think about conformance. The IBM GDPR framework offers an actionable five-phase approach to GDPR readiness, which recognizes that readiness is a continuum: every organization will have a unique place on the journey to readiness. In Phase 1, you assess your situation. You figure out which of the data you collect and store is covered by GDPR regulations, and then you plot a course to discover it. Phase 2 is where you design your approach. You need to come up with a solid plan for data collection, use and storage. And you need to develop an architecture and strategy that will balance risks and business objectives. Your goal in Phase 3 is to transform your practices, understanding that the data you deem valuable to your organization is equally valuable to the people it represents. This is where you need to develop a sustainable privacy compliance program, implement security and governance controls (TOMs — Technical and Organizational Measures) and potentially appoint a Data Protection Officer. By the time you get to Phase 4, you’re ready to operate your program. Now you’re continually inspecting your data, monitoring personal data access, testing your security, using privacy and security by design principles and purging unneeded data. And Phase 5 — the final phase — is where you’re ready to conform with the necessary GDPR requirements. Now you’re fulfilling data subject requests for access, correction, erasure and transfer. You’re also prepared for audits with documentation of your activities and ready to inform regulators and data subjects in the event of a data breach.
- #49: Simply minimizing the data you collect doesn’t do anything to protect the information that’s left. This is something you should be doing no matter what, however…
- #50: Reduction of Pain with New Protection Techniques. Some security approach products might restricting functionality, or compromise essential big data characteristics, like search and analytics. A good solution should address a security threat to big data environments or data stored within the cluster
- #53: Simply minimizing the data you collect doesn’t do anything to protect the information that’s left. This is something you should be doing no matter what, however…
- #56: De-identification or Anonymization can be a cost effective approach to protect data























![27
If there is a Picasso’s painting
valued at $50 million, it can be
tokenized.
• The same applies to gold
and diamonds.
Company stocks are more
complicated because in most
jurisdictions it is prohibited to sell
fractional parts of company shares.
Bankex — “Bankex provides the universal solution which can transform different asset classes to a digital
system/field/economy/area providing it with liquidity, flexibility, and safety for asset owners and investors like never
before”
Maecenas — “Maecenas is a new online marketplace promises to give art lovers the chance to buy shares in famous
paintings.[The Telegraph]”
LaToken — “LATOKEN’s mission is to make capital markets and trading available 24/7 T+0, with a broader range of asset
classes. We aim to facilitate capital reallocation into promising businesses, which will foster job creation with higher
productivity.”
Transform different asset classes](https://image.slidesharecdn.com/oct28whatistokenizationinblockchain-ulfmattsson2020oct27c-201028232648/85/What-is-tokenization-in-blockchain-27-320.jpg)