XPATH, LDAP and Path Traversal Injection
- 1. XPATH, LDAP and Path-Traversal Injection
- 2. XPATH
- 3. XPATH injection • XPATH parsing standard error • XPATH is method available for XML parsing • MS SQL server provides interface and one can get table content in XML format. • Once this is fetched one can run XPATH queries and obtain results. • What if username/password parsing done on using XPATH – XPATH injection
- 4. XPATH injection string fulltext = ""; string coString = "Provider=SQLOLEDB;Server=(local);database=order;User ID=sa;Password=mypass"; SqlXmlCommand co = new SqlXmlCommand(coString); co.RootTag="Credential"; co.CommandType = SqlXmlCommandType.Sql; co.CommandText = "SELECT * FROM users for xml Auto"; XmlReader xr = co.ExecuteXmlReader(); xr.MoveToContent(); fulltext = xr.ReadOuterXml(); XmlDocument doc = new XmlDocument(); doc.LoadXml(fulltext); string credential = "//users[@username='"+user+"' and @password='"+pass+"']"; XmlNodeList xmln = doc.SelectNodes(credential); string temp; if(xmln.Count > 0) { //True } else //false
- 5. XPATH injection string credential = "//users[@username='"+user+"' and @password='"+pass+"']"; • XPATH parsing can be leveraged by passing following string ' or 1=1 or ''=‘ • This will always true on the first node and user can get access as who ever is first user. Bingo!
- 7. Description • LDAP : Lightweight Directory Access Protocol • Runs over TCP/IP • Used for modifying and querying directory services • Object oriented • Stores and organizes information sharing some common attributes
- 8. Attack Anatomy • Normal flow : Expected Input (Good query) Expected results
- 9. Attack Anatomy • Checking for vulnerability : Erroneous Input (Bad query) Server Error/ Unexpected Behavior LDAP Injectable !!!
- 10. Attack Anatomy • Common Injection methods : – AND Injection – OR Injection • Common risks : – Information Disclosure – Role Escalation – Authentication Bypass
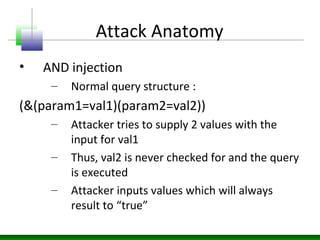
- 11. Attack Anatomy • AND injection – Normal query structure : (&(param1=val1)(param2=val2)) – Attacker tries to supply 2 values with the input for val1 – Thus, val2 is never checked for and the query is executed – Attacker inputs values which will always result to “true”
- 12. Attack Anatomy Login Form Asks username and password
- 13. Attack Anatomy Login Form Asks username and password Uname = abc, pwd = 123 Query : (&(uname=abc)(pwd=123))
- 14. Attack Anatomy Login Form Asks username and password Uname = abc)(&), pwd = Query : (&(uname=abc)(&))(pwd=))
- 15. Attack Anatomy • OR Injection – Similar to AND Injection – Normal query structure : (|(param1=val1)(param2=val2)) – Normally used by attacker for information disclosure
- 16. Attack Anatomy Resource viewer : http://www.something.com/res.cgi?type=1 •Restricted access •Machines accessible to the uid of the user are displayed
- 17. Attack Anatomy Resource viewer : http://www.something.com/res.cgi?type=1)(uid=*)) •Notice the injection •Attacker bypasses the user id check •(S)he can view all machines now
- 18. Path Traversal & Injection
- 19. Description • An application has numerous resources – Images – Sound – Videos – Background and page eye-candies • A normal application would group these in separate directories and put the code in a separate directory
- 20. Description • A poorly developed application would use absolute/relative paths to reach the necessary resources • Even worst done applications would directly use user preferences from URL / cookies and append them to the URI for these resources • A user could modify the URL / cookie values and view files not meant for him/her
- 21. Attack Anatomy • The attacker begins by identifying resources accessed via URIs • Then the attacker looks out for URLs or cookies which contain the resource identifiers • Usually, such applications set the resource names (and possibly even the paths) via URLs and cookies
- 22. Attack Anatomy • Before the attacker begins to browse directories, (s)he tries to find out the operating system type of the server • This is necessary because unix based servers allow forward slash for directory traversal and windows based servers allow backward slash for directory traversal
- 23. Attack Anatomy Attacker URL : http://something.com?pref=page1.html Interesting … pref =page1.html Attacker
- 24. Attack Anatomy URL : http://something.com?pref=page1.html Serves back page1.html Maybe .... path traversal ??? Attacker
- 25. Attack Anatomy Attacker Cookie: PREF=page1.html Interesting … PREF=page1.html Attacker
- 26. Attack Anatomy Cookie: PREF=page1.html Sends back a page with page1.html as the background Maybe .... path traversal ??? Attacker
- 27. Attack Anatomy • Once the attacker has determined that an application is vulnerable to path traversal, (s)he tries out the following, depending on – The operating system of the server – The level of input scanning the application does ...
- 28. Attack Anatomy • Unix based servers – Uses forward slash (/) – Attacker begins with “../” sequences • If the application scans for sequences such as the dot-dot-slash, the attacker will try : – %2e%2e%2f – %2e%2e/ – ..%2f
- 29. Attack Anatomy • Windows based servers – Uses backward slash () – Attacker begins with “..” sequences • If the application scans for sequences such as the dot-dot-slash, the attacker will try : – %2e%2e%5c – %2e%2d – ..%5c
- 30. Conclusion



![XPATH injection
string fulltext = "";
string coString =
"Provider=SQLOLEDB;Server=(local);database=order;User
ID=sa;Password=mypass";
SqlXmlCommand co = new SqlXmlCommand(coString);
co.RootTag="Credential";
co.CommandType = SqlXmlCommandType.Sql;
co.CommandText = "SELECT * FROM users for xml Auto";
XmlReader xr = co.ExecuteXmlReader();
xr.MoveToContent();
fulltext = xr.ReadOuterXml();
XmlDocument doc = new XmlDocument();
doc.LoadXml(fulltext);
string credential = "//users[@username='"+user+"' and
@password='"+pass+"']";
XmlNodeList xmln = doc.SelectNodes(credential);
string temp;
if(xmln.Count > 0)
{
//True
}
else //false](https://image.slidesharecdn.com/other-injections-151026084156-lva1-app6891/85/XPATH-LDAP-and-Path-Traversal-Injection-4-320.jpg)
![XPATH injection
string credential =
"//users[@username='"+user+"' and
@password='"+pass+"']";
• XPATH parsing can be leveraged by
passing following string ' or 1=1 or ''=‘
• This will always true on the first node and
user can get access as who ever is first
user.
Bingo!](https://image.slidesharecdn.com/other-injections-151026084156-lva1-app6891/85/XPATH-LDAP-and-Path-Traversal-Injection-5-320.jpg)