Brining Harmony between Dev and Ops and Security Teams using Gauntlt at ISC2 Austin Event
- 1. Bringing Harmony between Dev and Ops and Security Teams using Gauntlt
- 2. Be Mean to your Code with Gauntlt
- 3. @wickett College Startup Web Systems Engineer Media Startup Web Ops Lead DevOps CISSP CISSP, sounds cool
- 5. 1337 tools
- 6. the worms and viruses didn’t stop
- 10. “[RISK ASSESSMENT] INTRODUCES A DANGEROUS FALLACY: THAT STRUCTURED INADEQUACY IS ALMOST AS GOOD AS ADEQUACY AND THAT UNDERFUNDED SECURITY EFFORTS PLUS RISK MANAGEMENT ARE ABOUT AS GOOD AS PROPERLY FUNDED SECURITY WORK”
- 12. devs became cool
- 13. devs became cool agile
- 16. dev and ops now play nice
- 19. culture automation measurement sharing credit to John Willis and Damon Edwards
- 21. Your punch is soft,just like your heart
- 29. enter gauntlt
- 32. gauntlt credits: Creators: Mani Tadayon James Wickett Community Wrangler: Jeremiah Shirk Friends: Jason Chan, Netflix Neil Matatall, Twitter
- 35. fuzzfind inject
- 37. wisdom from a video game
- 39. Find the weakness of your enemy
- 41. sometimes, you face the same enemies again
- 43. Gauntlt helps dev and ops and security to communicate
- 45. Behavior Driven Development BDD is a second-generation, outside–in, pull-based, multiple-stakeholder, multiple-scale, high-automation, agile methodology. It describes a cycle of interactions with well- defined outputs, resulting in the delivery of working, tested software that matters. Dan North , 2009
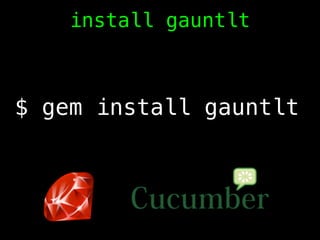
- 47. $ gem install gauntlt install gauntlt
- 48. gauntlt design Simple Extensible UNIX™: stdin, stdout, exit status Minimum features yield maximum utility
- 49. $ gauntlt --list Defined attacks: curl dirb garmr generic nmap sqlmap sslyze
- 50. Attack File Plain Text File Gherkin syntax: Given When Then
- 51. Feature: nmap attacks for example.com Background: Given "nmap" is installed And the following profile: | name | value | | hostname | example.com | Scenario: Verify server is open on expected ports When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should contain: """ 80/tcp open http """ Scenario: Verify that there are no unexpected ports open When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should not contain: """ 25/tcp """ Given When Then When Then
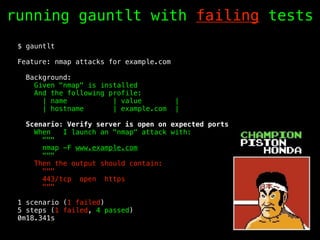
- 52. running gauntlt with failing tests $ gauntlt Feature: nmap attacks for example.com Background: Given "nmap" is installed And the following profile: | name | value | | hostname | example.com | Scenario: Verify server is open on expected ports When I launch an "nmap" attack with: """ nmap -F www.example.com """ Then the output should contain: """ 443/tcp open https """ 1 scenario (1 failed) 5 steps (1 failed, 4 passed) 0m18.341s
- 53. $ gauntlt Feature: nmap attacks for example.com Background: Given "nmap" is installed And the following profile: | name | value | | hostname | example.com | Scenario: Verify server is open on expected ports When I launch an "nmap" attack with: """ nmap -F www.example.com """ Then the output should contain: """ 443/tcp open https """ 1 scenario (1 passed) 4 steps (4 passed) 0m18.341s running gauntlt with passing tests
- 54. $ gauntlt --steps /^"(w+)" is installed in my path$/ /^"curl" is installed$/ /^"dirb" is installed$/ /^"garmr" is installed$/ /^"nmap" is installed$/ /^"sqlmap" is installed$/ /^"sslyze" is installed$/ /^I launch a "curl" attack with:$/ /^I launch a "dirb" attack with:$/ /^I launch a "garmr" attack with:$/ /^I launch a "generic" attack with:$/ /^I launch an "nmap" attack with:$/ /^I launch an "sslyze" attack with:$/ /^I launch an? "sqlmap" attack with:$/ /^the "(.*?)" command line binary is installed$/ /^the file "(.*?)" should contain XML:$/ /^the file "(.*?)" should not contain XML:$/ /^the following cookies should be received:$/ /^the following profile:$/
- 55. $ gauntlt --steps /^"(w+)" is installed in my path$/ /^"sqlmap" is installed$/ /^I launch a "generic" attack with:$/ /^I launch an? "sqlmap" attack with:$/
- 56. Feature: nmap attacks for example.com Background: Given "nmap" is installed And the following profile: | name | value | | hostname | example.com | Scenario: Verify server is open on expected ports When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should contain: """ 80/tcp open http """ Scenario: Verify that there are no unexpected ports open When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should not contain: """ 25/tcp """ setup steps verify tool set config
- 57. Feature: nmap attacks for example.com Background: Given "nmap" is installed And the following profile: | name | value | | hostname | example.com | Scenario: Verify server is open on expected ports When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should contain: """ 80/tcp open http """ Scenario: Verify that there are no unexpected ports open When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should not contain: """ 25/tcp """ attack get config
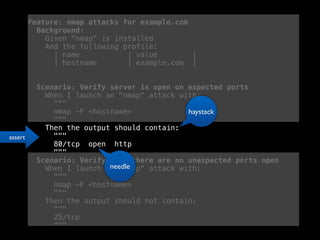
- 58. Feature: nmap attacks for example.com Background: Given "nmap" is installed And the following profile: | name | value | | hostname | example.com | Scenario: Verify server is open on expected ports When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should contain: """ 80/tcp open http """ Scenario: Verify that there are no unexpected ports open When I launch an "nmap" attack with: """ nmap -F <hostname> """ Then the output should not contain: """ 25/tcp """ assert needle haystack
- 60. Netflix Use Case Real World Cloud Application Security, Jason Chan https://vimeo.com/54157394
- 61. Check your ssl certs
- 62. cookie tampering
- 63. curl hacking
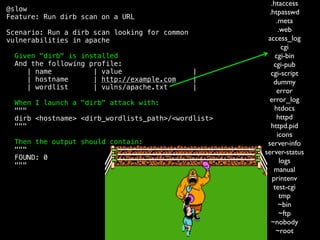
- 65. @slow Feature: Run dirb scan on a URL Scenario: Run a dirb scan looking for common vulnerabilities in apache Given "dirb" is installed And the following profile: | name | value | | hostname | http://example.com | | wordlist | vulns/apache.txt | When I launch a "dirb" attack with: """ dirb <hostname> <dirb_wordlists_path>/<wordlist> """ Then the output should contain: """ FOUND: 0 """ .htaccess .htpasswd .meta .web access_log cgi cgi-bin cgi-pub cgi-script dummy error error_log htdocs httpd httpd.pid icons server-info server-status logs manual printenv test-cgi tmp ~bin ~ftp ~nobody ~root
- 66. I have my weakness. But I won't tell you! Ha Ha Ha!
- 68. @slow @announce Feature: Run sqlmap against a target Scenario: Identify SQL injection vulnerabilities Given "sqlmap" is installed And the following profile: | name | value | | target_url | http://example.com?x=1 | When I launch a "sqlmap" attack with: """ python <sqlmap_path> -u <target_url> --dbms sqlite --batch -v 0 --tables """
- 70. my_first.attack See ‘GET STARTED’ on project repo Start here > https:// github.com/gauntlt/ gauntlt/tree/master/ examples Find examples for the attacks Add your config (hostname, login url, user) Repeat
- 71. Starter Kit on GitHub The starter kit is on GitHub: github.com/gauntlt/gauntlt-starter-kit Or, download a copy from: www.gauntlt.org/
- 73. Next Features More output parsers More attack adapters JRuby & Java Support Front end UI / web reports
- 75. Contribute to gauntlt See ‘FOR DEVELOPERS’ in the README Get started in 7 steps
- 76. If you get stuck Check the README IRC Channel: #gauntlt on freenode @gauntlt on twitter Mailing List (https:// groups.google.com/forum/#!forum/gauntlt) Office hours with weekly google hangout
- 77. get started with gauntlt github/gauntlt gauntlt.org videos tutorials google group @gauntlt IRC #gauntlt we help! start here cool vids!










![“[RISK ASSESSMENT]
INTRODUCES A DANGEROUS
FALLACY: THAT
STRUCTURED INADEQUACY
IS ALMOST AS GOOD AS
ADEQUACY AND THAT
UNDERFUNDED SECURITY
EFFORTS PLUS RISK
MANAGEMENT ARE ABOUT
AS GOOD AS PROPERLY
FUNDED SECURITY WORK”](https://image.slidesharecdn.com/isc2-gauntlt-2013-130606093028-phpapp02/85/Brining-Harmony-between-Dev-and-Ops-and-Security-Teams-using-Gauntlt-at-ISC2-Austin-Event-10-320.jpg)